Varonis is a company that specializes in bringing data security for file access and permissions. DatAdvantage is a product developed by Varonis to map who can access data and who actually accesses it across the entire email and file system.
Here is our list of the best Varonis alternatives:
- SolarWinds Access Rights Manager – FREE TRIAL This on-premises system acts as a front-end for Active Directory enabling unified control of multiple instances. Installs on Windows Server. Start a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL This on-premises package refers to Active Directory to track user activities and log all actions for compliance reporting. Available for Windows Server. Start a 30-day free trial.
- ManageEngine Endpoint DLP Plus – FREE TRIAL An advanced security solution that helps organizations to safeguard sensitive information from being accessed, stolen, or lost by unauthorized parties. Start a 30-day free trial.
- Netwrix Auditor An auditing package that assesses your system for security weaknesses and recommends improvements. Runs on Windows and Windows Server.
- STEALTHbits StealthAUDIT This package combines a credentials clean-up service with a sensitive data detection and protection system. Installs on Windows Server.
- LepideAuditor A data security system that is particularly strong at protecting databases. Runs on site as a virtual appliance.
Some of Varonis’ important features and capabilities are:
- Provides a visual look into who can access sensitive and regulated information.
- Audits the touch of every single file and email, regardless of whether it is in the cloud or on-premises.
- Allows you to simulate changes in a sandbox environment before you commit changes to the live system.
- Eliminates repetitive clean-ups.
- Automates manual data protection tasks.
- Dashboards give a bird’s eye view of your risks and the progress you make to improve security.
- Provides a panoramic view of data access
- You can remove access permissions for many users with a single click
- Its Automation Engine finds and fixes inconsistent permissions.
- A unified audit trail gives you a snapshot of your security at any time.
Though these are great features, the downside is that Varonis is expensive. The exact pricing information depends on your needs, but you can expect anywhere around $8,000 for every 100 users. In addition, Varonis requires a lot of manual intervention unlike a few other tools that are completely automated. For these reasons, let us look at some competitors, replacements and alternatives to Varonis for access management and file/permission analysis.
Our methodology for selecting the best Varonis alternatives:
We reviewed the market for Varonis alterntaives and analyzed tools based on the following criteria:
- Running in-depth audits for all platforms
- Allows admins to visualize the file server permissions to get a better understanding
- Automated alert systems and in-depth reporting capabilities
- Monitors live changes and modifications made to permission settings
- Free demo session or trial offer for product testing
The Best Varonis Alternatives & Competitors
Let’s briefly look into each of these products to see what they offer, as well as some of their features and some screenshots of them in action.
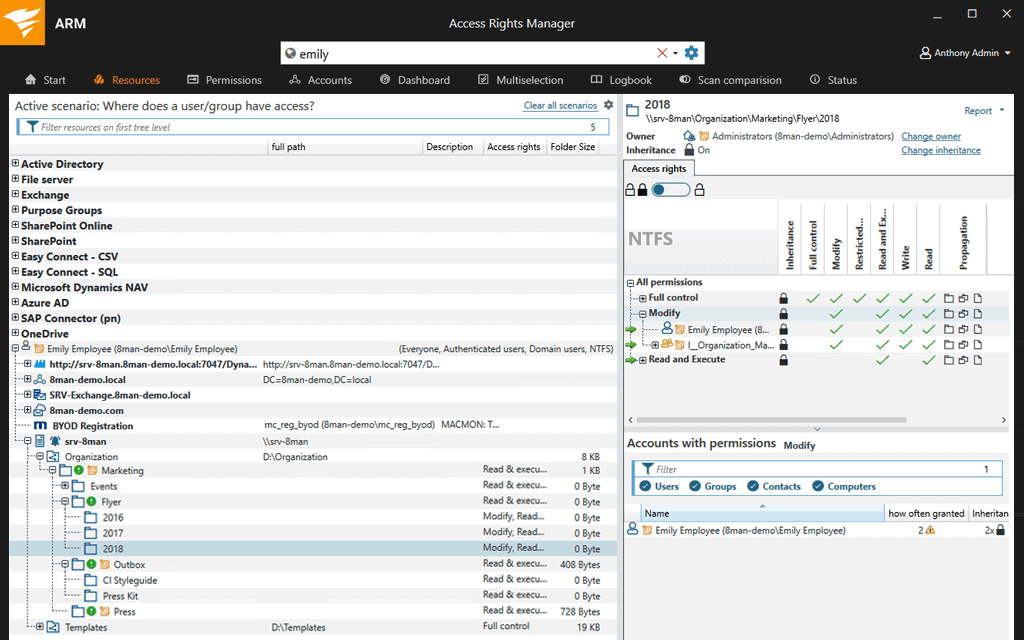
1. SolarWinds Access Rights Manager – FREE TRIAL
Access Rights Manager from SolarWinds makes it easy to manage and audit user access rights across your entire IT infrastructure. If you know much about SolarWinds products, you know that you can’t really go wrong with them as they have a solid reputation.
Key Features:
- Active Directory Auditing: Performs active directory audits to identify and mitigate risks in real time
- Automated User Account Provisioning and De-Provisioning: Simplifies the onboarding of new users and permits quick handling of requests to terminate accounts.
- Role-Based Access Control: Create roles and provide users access with specific rights and permissions
- Change Detection: Identifies unauthorized Microsoft Exchange modifications that help improve compliance
- Visualizations: Prevents sensitive data from threats by visualizing all file server permissions
- Reporting Capabilities: Provides detailed insights into user activities, access rights, and file permissions
Why do we recommend it?
With SolarWinds Access Rights Manager, admins can better manage and audit user access and file permissions across multiple platforms. It has a user-friendly interface and robust reporting features that help visualize all the modifications detected in user accounts and permissions in a simple manner, thus improving compliance and ensuring data security.
Who is it recommended for?
Since the SolarWinds system handles compliance auditing and reporting automatically, this solution is very helpful for IT managers, security analysts, and companies that have compliance requirements. It is also appropriate for both small and large enterprises due to its scalability but works only on Windows Server.
Pros:
- Better Visibility: Shows the permissions for SharePoint in a tree structure for better viewing and understanding.
- Quick Setup: Takes only a few minutes to set up an account, making user provisioning and maintenance simple.
- Prevents Data Breaches and Insider Attacks: Monitors file permissions and audits Microsoft Exchange to identify threats at an initial stage.
- Pre-Built Templates: Generates reports using numerous templates to assist with analysis and auditing.
- Self-Service Permissions Portal: Owner bears the responsibility of providing permissions through a web-based self-service permissions portal.
Cons:
- Uses Windows Server: Does not offer support for Linux and macOS versions
System Requirements
- CPU – Dual core processor or better
- Databases – Microsoft Windows Server 2008 SP1, 2008 R2, 2012, 2012 R2 and 2016.
- .NET Framework – .NET 3.5 SP1 and .NET 4.5.2
- Hard Drive – 30GB up to 1000 users and 40 GB for more than 1000 users.
- Memory – 4GB for up to 1000 users, 8GB for 1000 to 4000 users and 16GB for more than 4000 users.
Starts from $2,995. Download a 30-day free trial.
EDITOR'S CHOICE
SolarWinds Access Rights Manager is our top pick for it helps admins create, monitor, and audit user accounts across the entire IT infrastructure. It further helps IT teams build safe accounts at scale by standardizing user credentials using role-specific templates.
You can even create custom reports that highlight your access rights management efforts using this robust tool. Further, to meet the requirements of GDPR, PCI, HIPAA, and other compliance regulations, users have access to schedule comprehensive user activity reports, detect changes, and forward them straight to your auditor.
Download: Download a 30-Day Free Trial
Official Site: https://www.solarwinds.com/access-rights-manager
OS: Windows Server
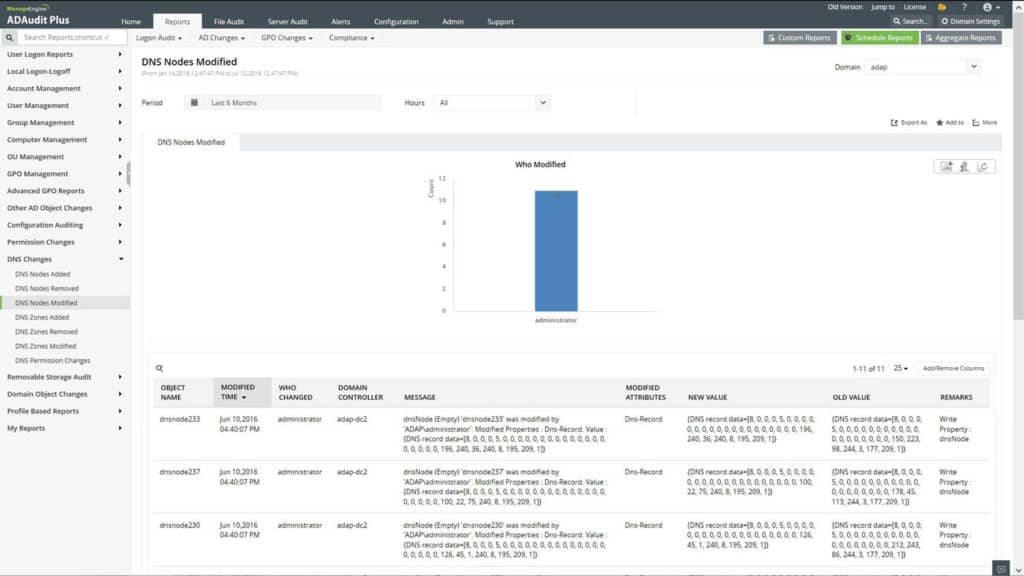
2. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAuditPlus reports Active Directory change auditing in real-time and can be accessed through a web browser as well.
Key Features:
- Change Notifications: Instantly triggers an alert notifying about the changes made to the account.
- Windows Login Monitoring: Audits login history and failure as well as monitors user login activities on a constant basis.
- Account Lockout Analysis: Identifies the cause of authentication failures to investigate the lockouts.
- Security Features: Utilizes real-time warnings and user behavior analytics (UBA) to reduce threats.
- Compliance Auditing: Generates GDPR compliant reports and other IT mandates for quick audits.
Why do we recommend it?
ManageEngine ADAudit Plus stands out for its ability to streamline audits, detect threats, and ensure compliance with a few clicks. It offers detailed reports for folder activities and compliance and real-time email alerts notifying you about Active Directory changes, making it a robust tool for security and compliance.
Who is it recommended for?
For IT security experts, compliance officials, and administrators who need real-time monitoring and auditing of Active Directory activity, ADAudit Plus comes highly recommended. It is especially helpful for firms that have regulatory norms to follow because of its compliance capabilities.
Pros:
- Monitoring Capabilities: Monitors and audits important resources such as domain controllers
- Reporting and Alerts: Provides real-time email alerts and access to 200+ built-in event specific reports
- Prevents Insider Threats: Uses UBA practices to detect and prevent insider threats
- Employee Time Tracking: Monitors the log on off time of employees in a Windows workstation on a constant basis
- File Integrity Monitoring: Ensures system integrity by watching over all the changes made to the local files and operating systems
Cons:
- Limitations in the Free Version: Admins gain access to collect activity details only from 25 workstations
Contact the sales team to get a custom quote. Download a 30-day free trial!
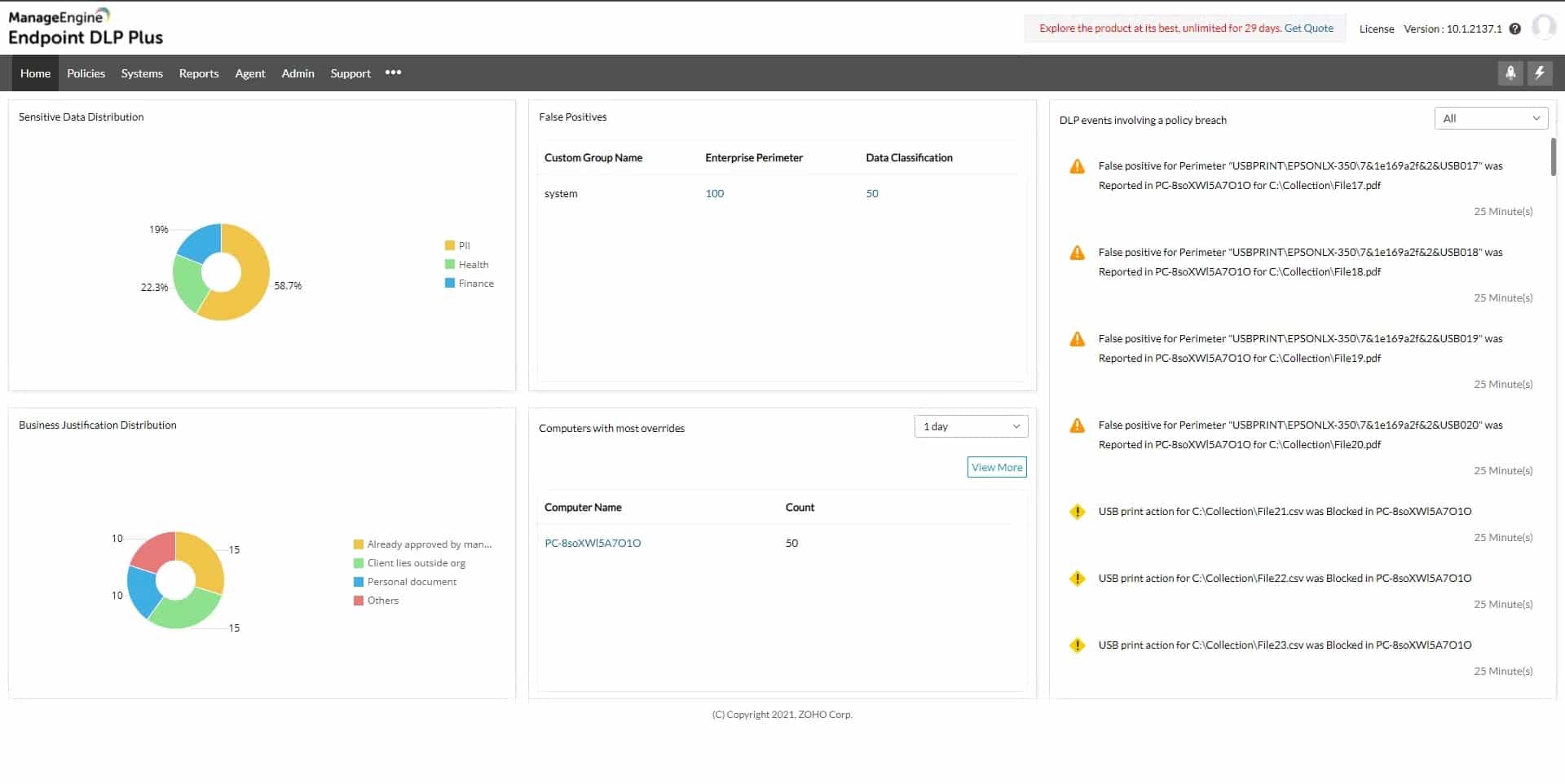
3. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP Plus utilizes a wide range of techniques, such as device control, encryption, and monitoring to comply with regulations and prevent data breaches.
Key Features:
- Encryption: Uses encryption techniques to secure all files across the system and prevents data breaches.
- Device Control: Minimizes potential risk points connected to devices by restricting their capacity to retrieve or duplicate confidential information.
- Backup and Recovery: Creates detailed backup for all files and systems and recovers whenever necessary.
- Centralized Management: Manages, monitors, and audits all data from a single console for quick analysis.
- Data Discovery: Identifies all structured and unstructured sensitive data by automatically conducting content analysis.
Why do we recommend it?
ManageEngine Endpoint DLP Plus is highly recommended as data theft may be avoided, and suspicious activity can be quickly identified with the extensive reporting and security tools included. Furthermore, it helps create access policies for sensitive data and uses pre-defined templates that are quick to set up and get started.
ManageEngine Endpoint DLP Plus empowers administrators with the ability to create access policies for sensitive data on endpoints such as laptops and desktops, and also has the capability to encrypt sensitive data and monitor user activity to detect and prevent data breaches. Endpoint DLP also offers detailed reporting and alerts to notify administrators of any suspicious or unauthorized access attempts. Endpoint DLP is a robust solution that can aid organizations in effectively securing their data and devices.
Who is it recommended for?
Businesses of all sizes, compliance officers, managed service providers, and even IT administrators can invest in the tool if they are looking for a solution that prevents data loss. It works well with all platforms as well as generates compliance reports, making it highly suitable for organizations that need to adhere to regulatory standards.
Pros:
- Intuitive User Interface: Strikes a balance between information and visuals for effective management
- Secure Email Communications: Verifies and ensures that data transfer takes place only on reputable domains.
- Pre-Defined Templates: Users can find sensitive information by creating new templates or by using pre-made ones that already exist.
- Insider Threat Monitoring: Closely observes user behavior to spot unusual activity and potential threats.
Cons:
- Comprehensive Tool: Wide range of features that may take time for new users to fully explore and understand their functionalities
Download a 30-day free trial.
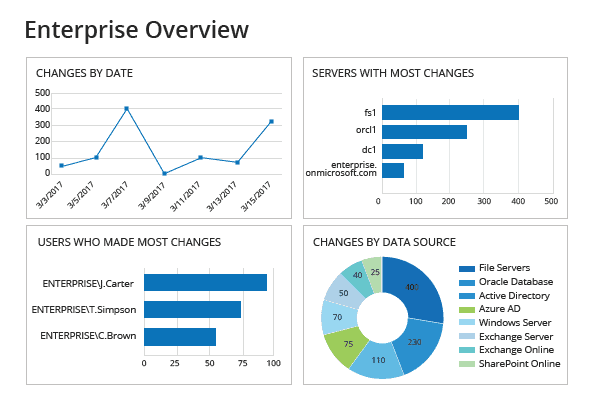
4. Netwrix Auditor
Netwrix Auditor gives you complete visibility and control over your IT infrastructure to protect data from unauthorized users.
Key Features:
- Threat Detection: Identifies security threats across all environments, including on-premises and cloud
- Compliance Software: Uses pre-defined reports aligned with industry standards for auditing
- Clear Visibility: Comprehensive view of their permissions on file servers and Active Directory
- Alert System: Prevents security breaches by sending alerts about unauthorized activities
Why do we recommend it?
With Netwrix Auditor, you can improve your IT team efficiency as it provides a comprehensive overview of your entire IT infrastructure and detects security risks posed by on-premises and cloud systems in real time. Additionally, it sends instant alerts on noticing anything suspicious, making it an effective solution for stopping data breaches and privilege misuse.
Who is it recommended for?
IT security experts and organizations that demand a detailed view of their IT environment and want to ease the auditing burden might find Netwrix Auditor highly suitable. In addition, organizations that have complex, hybrid IT setups that often worry about long-term data storage and compliance will find it helpful thanks to its capabilities.
Pros:
- Reduces Risk: Identifies security gaps and loose permissions early and responds to threats in real time
- Two-Tiered Storage: Helps keep your data safe for several years
- Behavior Monitoring: Reduces the chances of insider threats by assisting in identifying odd user behavior
Cons:
- Filter Option: Filter settings are difficult to figure out when using the product for the first time
There are three editions:
- Small Business Edition for up to 150 AD users
- Standard Edition for 150 AD users
- Data Discovery and Classification Edition for more than 150 users
Contact the sales team for pricing. Download a free trial.
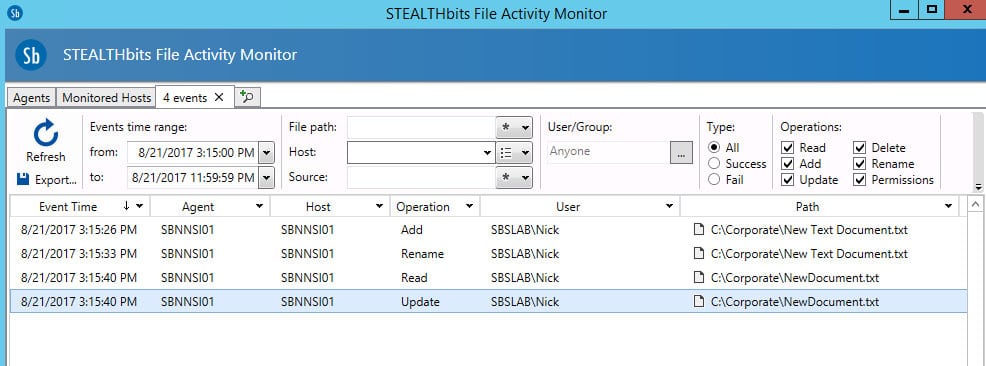
5. STEALTHbits
STEALTHbits is a scalable and automated system that maximizes security and governance.
Key Features:
- Data Access Governance: Limit rights and data access to what is necessary
- Active Directory Security: Manages and keeps Active Directory secure for it has access to all of your data
- Privileged Access Management: Regulates privileged actions and securely assign administrative access
Why do we recommend it?
STEALTHbits comes with various products to help in threat detection, enforcing strict security policies, monitoring, and auditing. It further offers access to extensive threat modeling and privileged account discovery features that help identify and remediate risks and reduce operational costs.
Who is it recommended for?
Organizations that rely on multiple operating systems or have a complex IT environment might find it an ideal option for their business. Furthermore, cybersecurity teams can even use the robust tool for identifying and mitigating security risks thanks to its auditing features and threat models.
Pros:
- Automation: Automatically completes the identification, verification, and decision-making process for various remedial tasks
- Risk Reduction: Uses different threat models to identify and respond to security breaches and insider attacks in real time
- Real-Time Monitoring: Detects threats in real time by monitoring the entire IT infrastructure and proactively blocks critical events
Cons:
- Reporting System: Web-based reporting console is not so user friendly.
STEALTHbits is offering Varonis customers a one-on-one license swap at no extra cost. For others, pricing starts at $12 per network user for Active Directory. You can download a free trial.
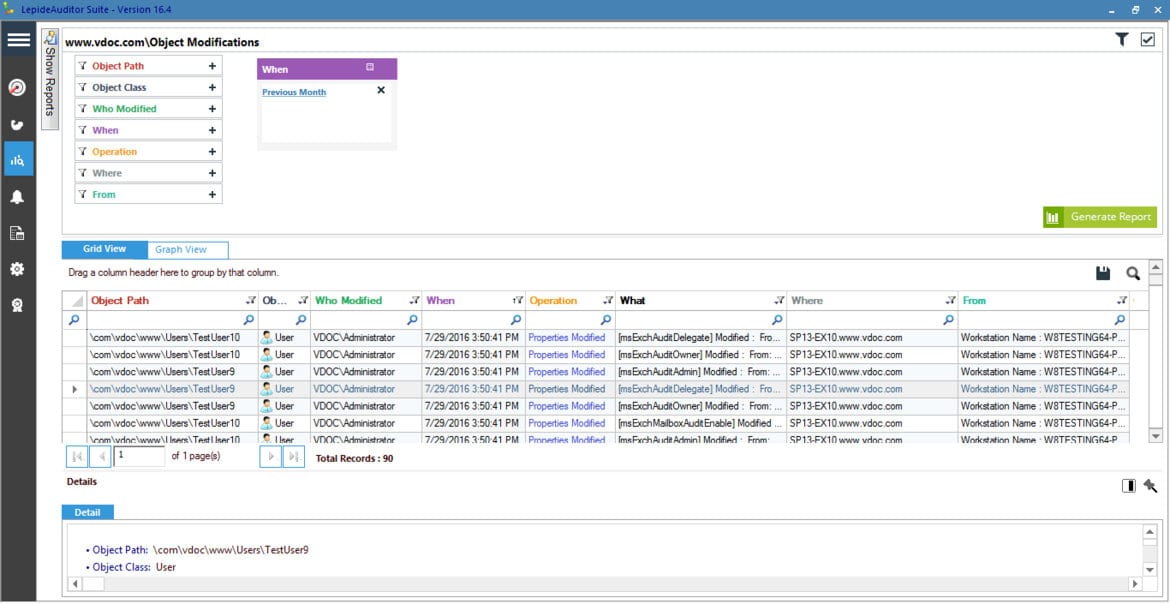
6. LepideAuditor
LepideAuditor is a powerful auditing and monitoring solution that provides security for your data and at the same time, makes compliance a breeze for you.
Key Features:
- Threat Detection and Risk Assessment: Monitors audit changes on multiple platforms to detect threats and assess risk before it escalates
- Compliance Management: Offers access to hundreds of pre-defined reports to assist your company in fulfilling compliance standards’ audit needs
- Log Analysis: Maintains and stores logs on a different SQL server for future reference
Why do we recommend it?
LepideAuditor is an excellent tool for thorough auditing and real-time alerting. It simplifies administration by centralizing all audit records in one location. What distinguishes it in terms of continuous security is its capacity to audit systems even in the absence of logs.
Who is it recommended for?
For IT departments and compliance-focused enterprises, this product could be highly useful because it provides centralized management, real-time audits, and reporting capabilities. Teams aiming to fine-tune their security and compliance policies will find it suited due to its customizable alerts and reporting templates.
- Simplifies IT Management Tasks: Automatically sends reminders for password resetting and easily restores unwanted changes
- Tracks Changes: Lets you know who updated the data and when, so you can keep track of all changes made to sensitive data
- Reporting: Users can customize their reports or use pre-defined audit reports to get the right information
Cons
- Limited Customization: Although LepideAuditor comes with several pre-made reports, some users feel there are fewer customization options
LepideAuditor starts at $499. Get a 14-day free trial is available.
Conclusion
To conclude, auditing file access and permissions is absolutely vital in preventing both insider and outsider security threats, and also to remove all the possible vulnerabilities in your network. Though Varonis is a popular software and comes with a host of features, there are some limitations to it, especially in terms of cost.
But there are many lower-priced alternatives that come with a great set of features as well. We suggest you download some of the software suites from above, as most of them offer you a 30-day trial to test in your environment and see how they do in terms of features and how they perform for the tasks at hand.