Ransomware is one of the prominent malware threats that many online businesses face with outdated updates and fewer security tools. Over the past few years, the number of ransomware attacks has increased by 148%. As per the Business Insiders report, the largest ransomware payout was made by an insurance company in 2021.
Ransomware security is crucial for every small and big organization. With our prior experience and expertise, we have listed the top-notch security tools that can be a great addition to your organization.
Here is our list of the best tools to protect backups from ransomware:
- Acronis Cyber Protect – EDITOR’S CHOICE This package combines anti-virus with data backup and includes application-aware recovery for systems such as databases and VMs. Available for workstations, servers, mobile devices, and cloud platforms. Start a 30-day free trial.
- CrowdStrike Falcon Prevent Follows a modern approach by showing a malicious component in the detections dashboard to provide end-to-end visibility and protection.
- ManageEngine DataSecurity Plus Features real-time monitoring, which allows you to detect and take instant actions on disruptive and sensitive data leaks via USB devices, email, or printers.
- NinjaOne Backup Offers customized, cloud-based, hybrid plans that give instant alerts when data is tampered with or misconfigured across the cloud platform.
These attackers give threat calls to victim companies of leaking exfiltrated data if their demands are not fulfilled. They cause not only financial damage to the company, but also ruin their reputation and brand value. Sophisticated cyber attackers know different ways through which they can enter your system. Once they gain access they infect and encrypt all computer files, and systems. Later, they demand a large ransom after activation.
Ransomware attacks can lead to both financial and data loss, and reputational damage. Here, we will discuss ransomware in detail and tips to help protect backup systems from such attacks. Furthermore, we have listed a few tools that can work in your favor and protect your business from ransomware attacks.
What is Ransomware?
Ransomware is a form of malware that blocks authorized users from accessing their computer files, systems, or networks and demands them to pay a ransom to unlock and decrypt the data. The attackers take advantage of software vulnerabilities to infect, access, lock, and encrypt the computer or device entirely, making it impossible for organizations to access any of its files or applications.
Ransomware is one of the most prominent types of malware that keeps all of your companies’ files and data hostage unless you fulfill their demand. It can infect any computer or mobile device connected to the internet, and commonly targets the one running outdated software. It is imperative you make sure your organization regularly updates its systems and apps to protect from such attacks in the future.
The reason why this type of ransomware is so dangerous is that once the cybercriminals get hold of your files, there is no way for security software or a system reset to retrieve them. If a ransom demand is not met in a cybercriminal’s timeframe, then your system or encrypted data remains unavailable. Also, your data can be deleted by ransomware, with its decryption keys being erased.
Cybercriminals can encrypt files on your system via email attachments, add extensions to your attacked data, and hold it hostage until you pay the requested ransom. Another technique that most attackers practice is to send notifications from malicious websites, informing users that their device is infected and must click on a download link to activate the tool and remove the virus.
The cybercriminal behind the attack will then contact you with their demands, promising to unlock your computer or decrypt your files after you have paid a ransom (usually in bitcoin).
Let us discuss a few tips that will help protect your backups from ransomware attacks.
Tips to Protect Backups from Ransomware
Do you know there are sophisticated ransomware packages that can be uploaded onto shared drives via syncing and travel across a network? These network-connected infections can also pass onto your backup systems and put the business into serious trouble. To avoid such mishaps and protect your backups from ransomware, we have listed a few tips that can work wonders for your business.
1. Secure Your Windows System
An uptick in remote work since the pandemic has seen ransomware attacks increase by 148%. It has also been found that most of these attacks are against Windows hosts and spread faster across other hosts after being infected by a single host.
In these cases, most of the attacker encrypts the files and devices once the infected ransomware spreads to enough hosts in your computing environment and shuts multiple systems altogether. Hence, the best tip for organizations would be to use other platforms for their backup server instead of Windows.
Unknown of the attacker’s possibility, many companies primarily use Windows to run their backup. As an alternative, you could switch to Linux media servers. However, if you want to still run the main backup software on Windows, try running a copy of your backup on Linux as well.
But if your backup is accessible only via Linux media servers, chances are that the ransomware attackers attempting to infect Windows-based servers will not be able to access your backup files.
Also, try to store the main backup behind a Linux-based media server to avoid any mishaps. Furthermore, work on the security of your Windows-based backup servers and turn off maximum services ransomware used to attack servers. Focus more on tightening your security and less on convenience.
2. Remove File-System Access to Backups
Avoid placing your backup data in a standard file-system directory. For example, E:\backups or C:\ProgramFiles. The attackers often target these directories with names to infect and encrypt files. You must always look for a different folder or destination to store backups on disk.
If you are using a backup server, try looking for new ways to write a backup product to your target deduplication array without server message block (SMB) or network file system (NFS). If the attacker can infect the server, it will encrypt all the stored backups as they are easily accessible via a directory.
3. Store Backups Out of Data Center
No matter which location you choose to store your backup data, make sure that its copy is stored in a different location. For example, in the case ransomware tries to attack your data center, your copies stored in the cloud must remain safe. Using firewall rules or changing operating systems and storage protocols, you can ensure your copies remain separate in the case of an attack.
Ransomware attackers indeed know different techniques to infect victims’ files but, they still don’t know how to attack backups stored in object-based storage. Further, there are a few backup services that can write backups to the storage but are not accessible except via their user interface. As a result, neither the administrator nor the ransomware can directly see the stored backups.
Use cloud platforms to store the backup copy and protect them by firewall rules or write it in different storage for security purposes.
4. Follow the 3-2-1-1-0 Golden Rule for Backups
The 3-2-1-1-0 Golden Rule is highly effective and provides the best protection from ransomware. As per this rule, you must meet five important conditions, including:
- Enterprises must create three data copies, including the production copy.
- Use at least two different storage media, such as tape and cloud storage.
- Out of the three, one copy must be stored off-site, in case the supporting machines are physically damaged.
- Out of the three, another copy must be stored offline or in the cloud (Immutable, i.e., it cannot be modified).
- The backups must have zero errors.
5. Automate Response
Another way to prevent contamination spread is to detect and respond immediately to the ransomware attack. In most cases, ransomware takes a minimum of 90+ days before activating and making a ransom demand. If your organization has a strong security posture, there are high chances that you can timely detect and prevent ransomware.
Various built-in monitoring systems can detect and alert your team to possible ransomware attacks. Also, integrate SIEM and SOAR platforms that help automate the response process.
Our methodology for selecting the best tools to protect backups from ransomware
You must follow this simple methodology to pick the right security tool to protect your organization from ransomware malware:
- Go through risk assessment according to your organization’s size.
- Consider implementing a comprehensive security strategy
- Look for features like anti-malware, anti-ransomware, and behavior-based analysis.
- Must have email and network security
- Regularly backup critical data in an isolated environment
- Consider a comprehensive incident response plan
- Consider tools compliance with relevant regulations and industry standards.
- Testing and evaluation
Tools to Protect Backups from Ransomware
Take a look at some of the trusted tools that will block and protect your backups from ransomware before they get inside your backup storage.
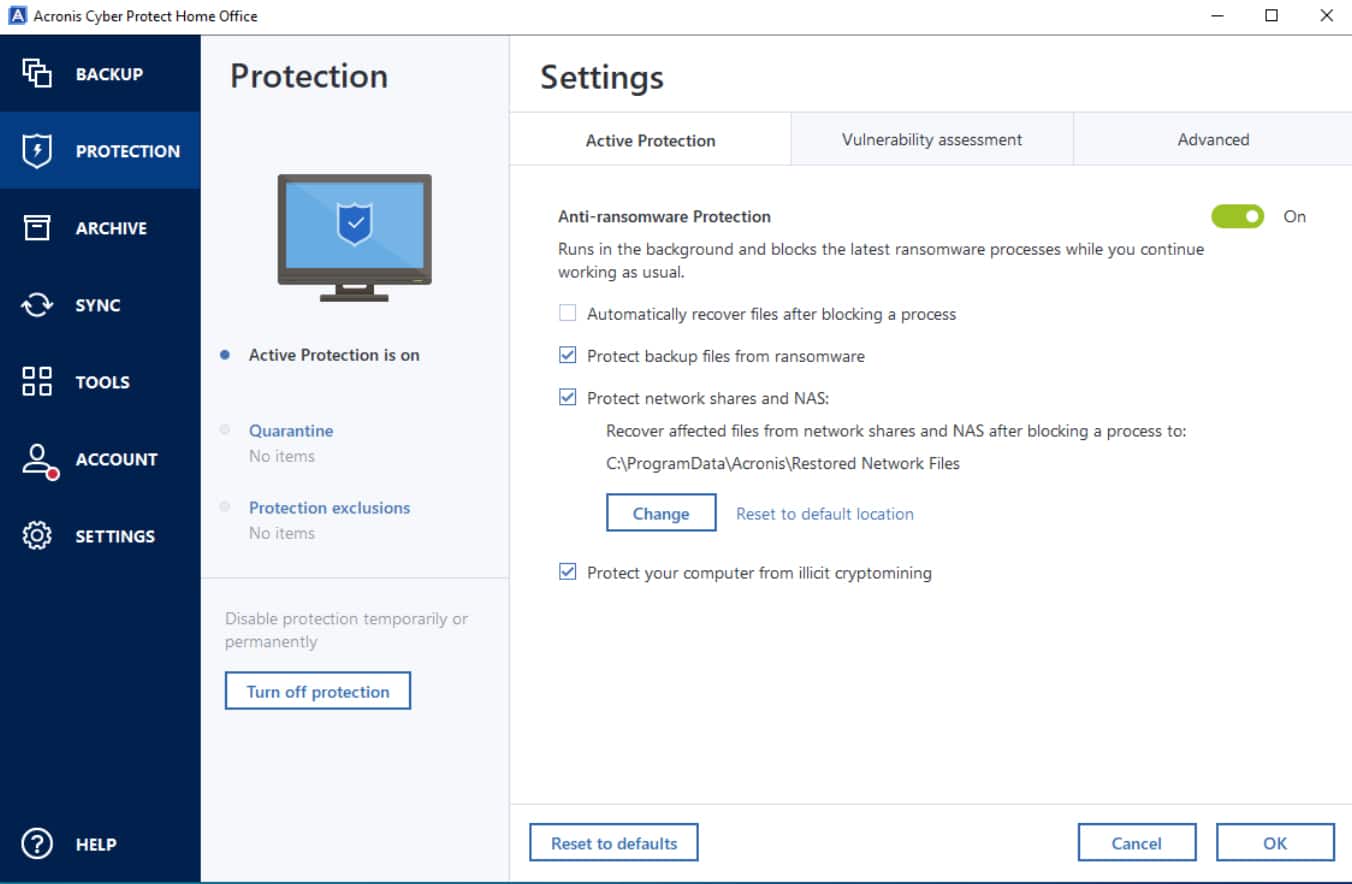
1. Acronis Cyber Protect – FREE TRIAL
Acronis Cyber Protect helps businesses manage, protect, and create a backup of multiple endpoints. It is a package of modules that safeguards your information and devices from threats and ransomware. It uses advanced MI-based protection against malware to protect every data and evolving threat.
Key Features:
- Active protection with foreign backup
- Anti-Malware and web protection
- Supports remote management and assistance
- Disk health monitoring
- Application-aware backup and recovery
Why do we recommend it?
Acronis Cyber Protect is the perfect security tool for advanced protection against ransomware. With its multi-layered security approach and AI assistance, it detects and mitigates ransomware attacks, keeping your data safe. You can always stay ahead of threats to ensure your organization’s security integrity and valuable information with this reliable backup solution.
Furthermore, it also supports various anti-ransomware technologies that help protect backup systems and eliminates the gap in the defenses. Organizations can easily scan all infections using its advanced features before getting added to the backup.
The backup restoration process also involves the use of malware scans. It is one of the best cyber protection solutions that offer a high level of efficiency and unmatched protection. Users can easily manage the tool and protect backup systems from ransomware via a single console.
Who is it recommended for?
Acronis Cyber Protect is ideal for IT experts who want a complete solution. It automatically finds new devices, making management easy. With built-in vulnerability assessments, experts can identify and fix weaknesses. The data protection map provides a clear picture of data activities, aiding strategic decision-making. It’s a must-have for efficient, secure data management.
Pros:
- AI-assisted threat detection
- Great GUI Backup
- Two-way data encryption
- Seamless cloud and local backup
- Customizable and faster recovery
Cons:
- Trouble in backup replication
EDITOR'S CHOICE
Acronis Cyber Protect is our top pick for a tool to protect backups from ransomware because it offers a comprehensive, all-in-one solution that combines backup, anti-malware, and endpoint protection. Unlike traditional backup tools, Acronis integrates AI-based behavioral detection to identify and block ransomware attacks in real time, ensuring that backups remain secure and uncorrupted. The Acronis package monitors system processes for ransomware-like behavior, instantly stopping unauthorized encryption attempts. Additionally, it creates immutable, tamper-proof backups stored locally or in the cloud, preventing attackers from deleting or altering them. Acronis also provides secure blockchain-based authentication, ensuring backup integrity by detecting unauthorized changes. Its automated recovery options allow businesses to quickly restore systems to a clean state, minimizing downtime after an attack. Another advantage is its ease of use, making it accessible for both IT professionals and small businesses. With features like vulnerability assessments and patch management, Acronis Cyber Protect doesn’t just defend against ransomware—it proactively strengthens security.
Download: Start a 30-day FREE Trial
Official Site: https://www.acronis.com/en-us/products/cyber-protect/trial/
OS: Windows, Windows Server, macOS, Linux, iOS, Android, and cloud
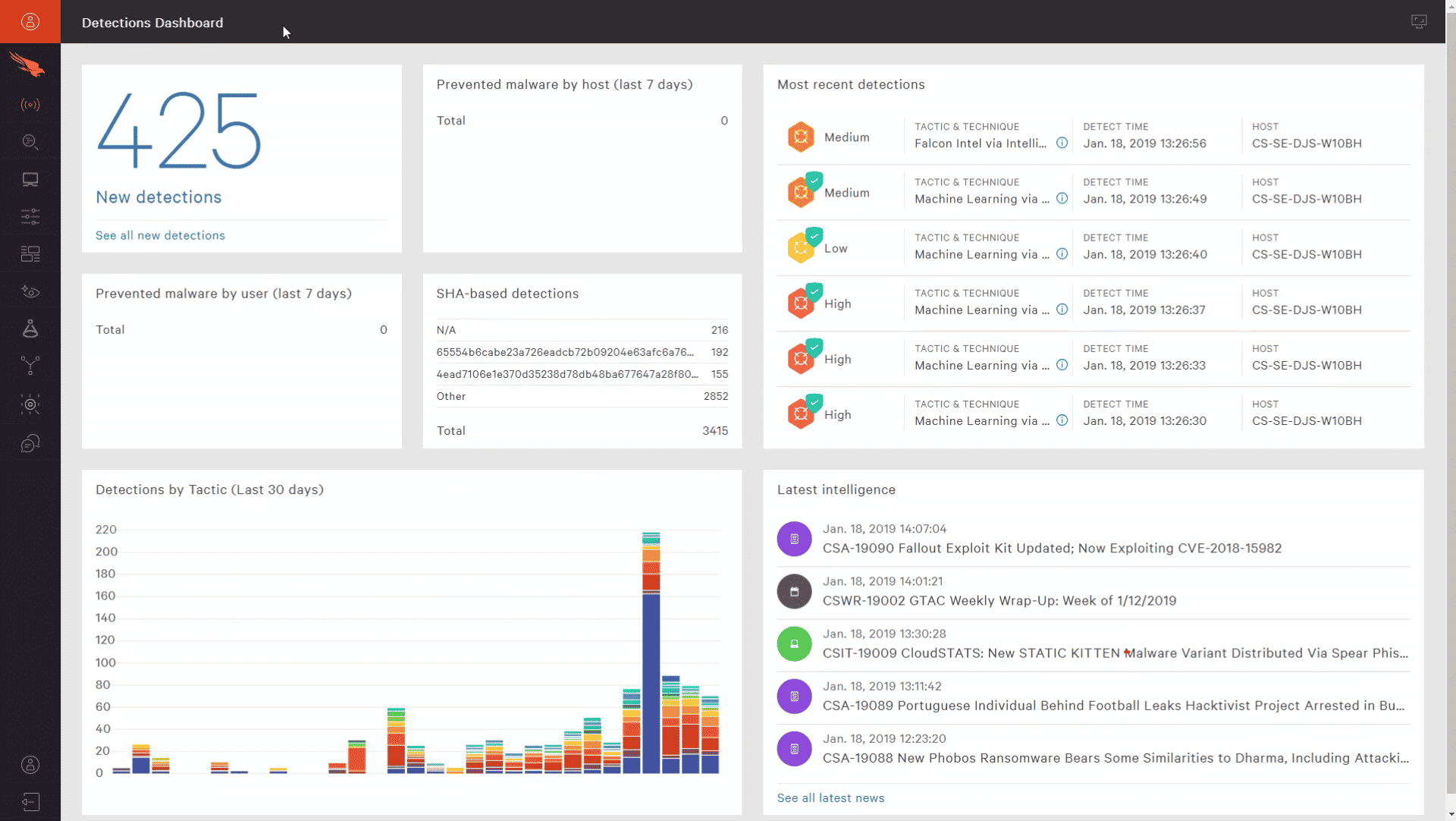
2. CrowdStrike Falcon Prevent
CrowdStrike Falcon Prevent is one of the best security tools available in the market to protect devices from ransomware infection. It is a fully operational tool that offers quick and easy deployment. Further, it protects your devices and backup files without impacting resources or productivity.
Key Features:
- Comprehensive application control
- Proactive threat hunting
- Gives rapid response
- Dynamic/code analysis
- Endpoint intelligence and malware detection
Why do we recommend it?
CrowdStrike is loved by professionals for its exceptional Endpoint Protection capabilities. It has advanced security measures, which reduces the time spent on manual issue remediation. In addition, it offers proactive defense to ensure overall cybersecurity posture and minimize potential risks to systems and data.
Falcon Prevent is an endpoint detection and response system that monitors each endpoint and detects and blocks ransomware as it hits the device. Its Automated IOA remediation feature further helps clean and eliminate artifacts left behind from blocked malicious activity.
It protects Windows, Windows Server, macOS, and Linux platforms and supports behavior-based indicators of attacks that go out of the way to prevent sophisticated malware-free attacks.
Who is it recommended for?
CrowdStrike is used by a broader range of cybersecurity experts and organizations seeking advanced threat protection. This tool helps in continuous monitoring of user behavior, which involves comparing real-time activity to benchmarked patterns and known fraud indicators. It helps in swift detection and response to anomalous activities, enhancing the overall security posture. Its proficiency in proactively identifying and mitigating potential threats makes it an invaluable tool for cybersecurity professionals tasked with safeguarding sensitive data and networks.
Pros:
- Supports End-Point Detection and Response (EDR)
- 24/7 threat hunting
- Regular follow and robust ability of detection
- Vulnerability management
Cons:
- Console menus are a little bit complex and unclear
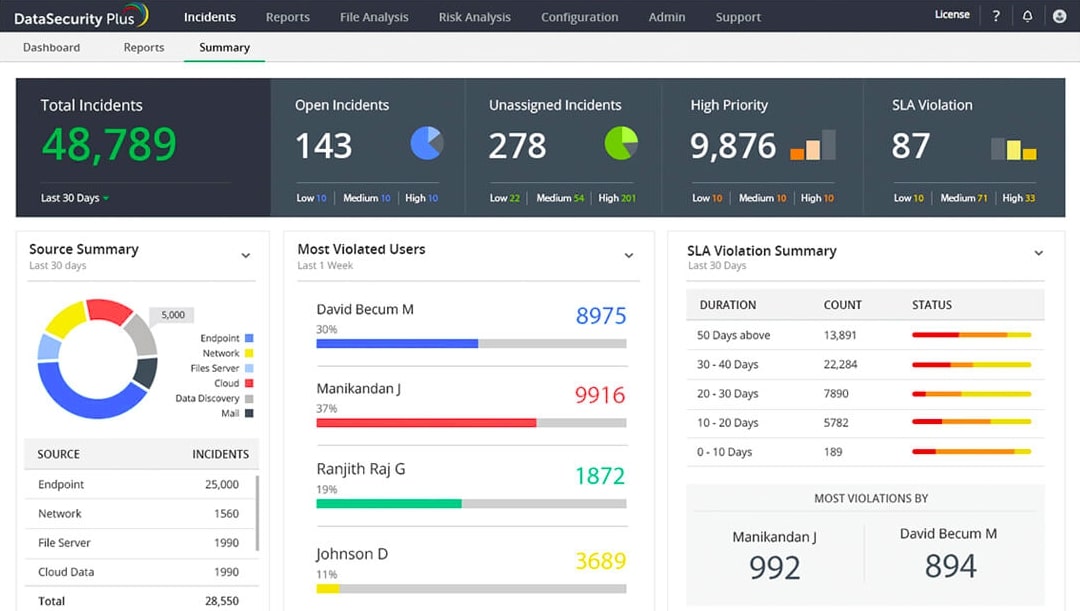
3. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus is another popular tool businesses can invest in to protect files from tampering. Using this tool, organizations can detect potential ransomware intrusions and spot any unauthorized change implemented by the attackers. It is compatible with the Windows platform, one of the most targeted platforms by ransomware attackers.
Key Features:
- Response to ransomware
- File server auditing
- Comes with data protection software
- Cloud protection and file integrity monitoring
Why do we recommend it?
ManageEngine DataSecurity Plus provides alerts on storage policy violations, including employees hoarding large or non-essential files. This proactive monitoring ensures compliance with storage policies and helps prevent data hoarding. Additionally, DataSecurity Plus specializes in optimizing storage space by identifying and removing files with no business value, such as temporary files. This helps in effective data organization and reduces the need for purchasing additional storage resources.
It also supports automated responses and alerting features that inform users about ransomware actions on time and prevent them from spreading across the network. Further, ManageEngine DataSecurity Plus has a built-in threat library that helps detect attacks by unknown ransomware variants, including Locky, Petya, etc.
Another feature that makes it a top choice is its ransomware detection and response capabilities that help businesses discover threats before they launch and cause damage. It also allows businesses to track and alert on noticing critical changes made to sensitive files.
Who is it recommended for?
IT professionals and organizations who need to better control their unstructured data, ManageEngine DataSecurity Plus is the best tool. The tool’s file analysis solution benefits data management experts, offering them insights and analytics. This enables them to handle scrap files properly, organize storage space intelligently, and secure the files effectively. It helps to make smart decisions with the help of clear and detailed insights and secure sensitive information within securely organized environments.
Pros:
- Automated responses and alerting features
- Keep track of changes in sensitive files
- Allows searching for PII buried files
- Junk file detection
Cons:
- Might not scan password-protected files
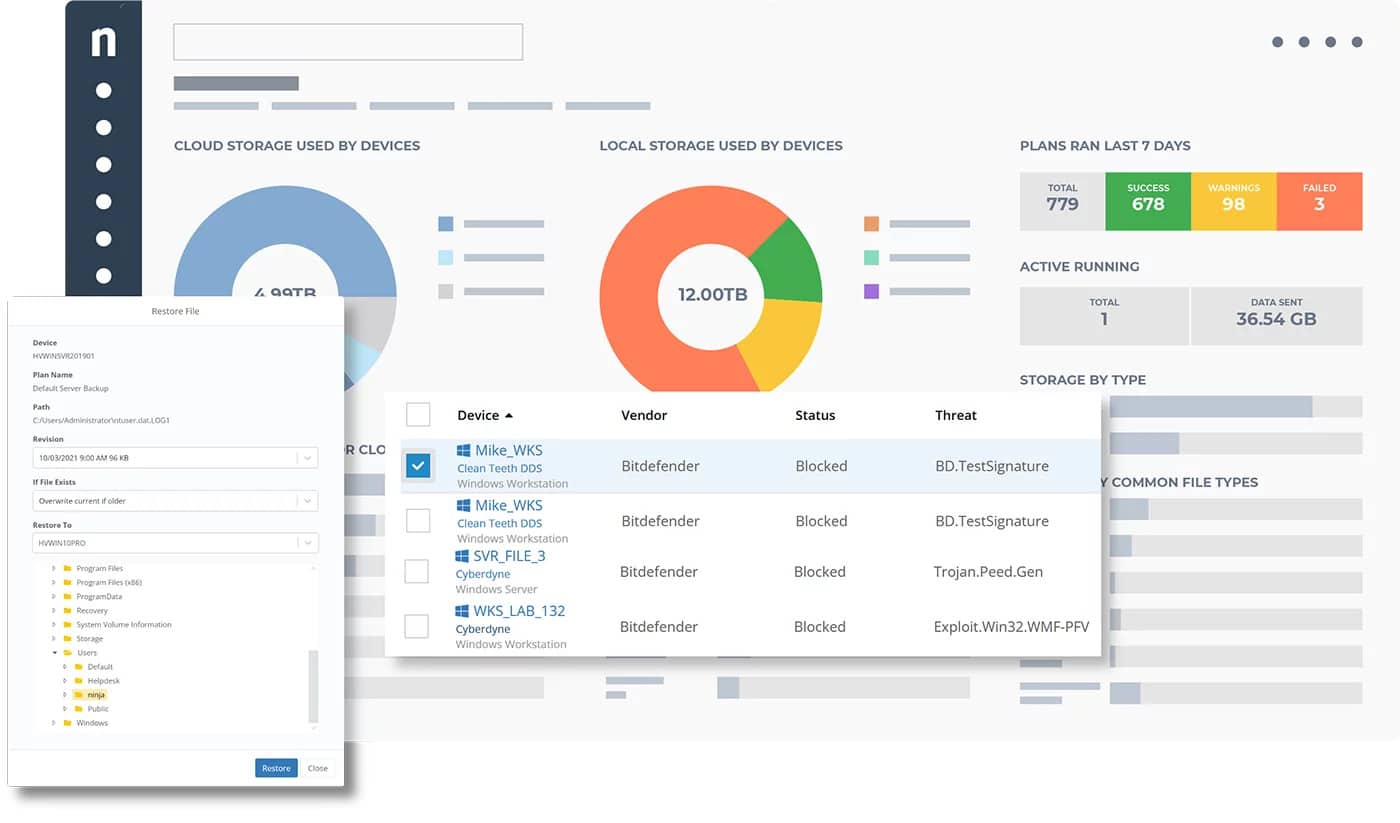
4. NinjaOne Backup – FREE TRIAL
NinjaOne Backup tool is best-suited for managed service providers (MSPs). It is a fast and flexible security tool that protects all your critical business information and data stored on end-user devices from known and unknown threats. It has a cloud storage space protected by 256-bit AES encryption that ensures all the data is safe from malicious actors.
Key Features:
- 360 degree control and visibility
- Bit defender integration
- Proactive alerting
- Remote backup management
Why do we recommend it?
NinjaOne Backup is well-known for its user-friendly features. It provides customizable file/folder and image backup plans along with multiple restore options. Other than this, it has plenty of great features like proactive alerting, remediation tools, and ransomware disaster recovery to ensure robust protection for all your endpoints.
Further, organizations can deploy data protection to the workflows and all Windows and Mac endpoints using this powerful tool. In case of a successful ransomware attack, the Ninja Data Protection tool helps faster restore all files stored locally or in the cloud to start operations.
Who is it recommended for?
Ninja Protect is recommended for cybersecurity experts seeking advanced threat protection. This tool is powered by Bitdefender’s next-gen antivirus and has HyberDetect machine-learning models and sandboxing capabilities. It helps experts by identifying suspicious attributes and behaviors to ensure effective and proactive defense against evolving cybersecurity threats.
Pros:
- Windows patching with granular management
- Allows to disable and hide new features
- It comes with various built-in tools
- MFA protection
Cons:
- Lacks extra integrations
You can inquire about custom pricing once you have registered for a 14-day free trial.
Conclusion
Ransomware can get into your systems via mail attachments in PDF format, images, ZIP files, or RAR files. They can also make their way through your device by manipulating an employee or tricking them with fake information. Once the attackers make their way to your systems, they can access and encrypt all your files.
In some cases, they travel across a network and upload into shared drives to cause severe damage. Ransomware attackers are the main cause of concern for many online businesses as they can lead to financial loss, data loss, and reputational damage.
They can also infect your backup systems if not protected beforehand. Sophisticated ransomware attackers know different techniques to enter your space and infect files and systems. Therefore companies need to invest in the best cyber protection solutions that offer security to data, devices, and backup.
Make sure to secure your Windows system and store backup files in Linux media servers for better protection. Furthermore, avoid storing backup data in a standard file-system directory. Another way to protect your backup from ransomware is to store backups out of the data center in the cloud.
Lastly, follow the 3-2-1-1-0 Golden Rule and maintain a strong security posture to detect and prevent ransomware in real-time.
We have also listed a few security tools that will protect your backups from ransomware and block threats before they launch or cause any damage. Compare each above-listed security tool before selecting one for your backup and data protection.