A network security audit is an integral part of every organization’s IT and security management, and over the last few years, this process has shot to prominence due to the many attacks and data breaches on organizations.
At the heart of it all, network security auditing is the process of mapping your network’s hardware and software, so you can stay on top of their health, performance, security vulnerabilities, and more. These audits, when done at regular intervals, can quickly resolve the underlying network security issues and at the same time, can report the gaps and vulnerabilities that increase the chances of a cyberattack.
This also explains why a network security audit is an integral part of any operations system audit or even a business audit for that matter.
Here are the top network security auditing tools:
- SolarWinds Network Configuration Manager – FREE TRIAL A comprehensive platform that handles all aspects of network security and audit and generates insightful reports for a positive outcome in your organization.
- N-able N-sight – FREE TRIAL It is a cloud-based solution consisting of a bunch of remote monitoring and management tools to protect your business assets.
- ManageEngine Log360 – FREE TRIAL A log manager and SIEM system bundle that gathers operating system and software logs for security monitoring. Runs on Windows Server.
- ManageEngine EventLog Analyzer – FREE TRIAL A log management system that is useful for security analysis and compliance reporting. Available for Windows Server and Linux.
- Intruder An online vulnerability scanner that scans your network for vulnerabilities, so you can fix them right away. It also works well across different devices and endpoints.
- ITarian Network Assessment Tool Monitors all the hardware and software components of your network to provide actionable intelligence
- Nagios An open-source framework that works well on Windows, Linux, and Unix systems
- Splunk is a platform well-known for not just its monitoring, but also for its visually appealing reports and graphs.
- Nessus is a simple monitoring solution that continuously monitors your network and raises alerts if any value goes beyond the threshold limits.
- Nmap A popular free tool that specializes in vulnerability scanning, device discovery, and reporting.
The top network security auditing tools
So, how do you do this network security audit? Given the size and complexity of organizational networks today, it’s almost impossible to do this audit manually. Hence, it’s a good idea to choose from the many automated tools to handle this job for you.
Methodology for Selecting the Best Network Security Auditing Tools
- Does it offer automated asset discovery?
- Does it offer vulnerability assessors and testing tools?
- Supports activity logging to comply with data security standards?
Let’s take a detailed look into each of these tools, including their features and cost, to help you make an informed decision.
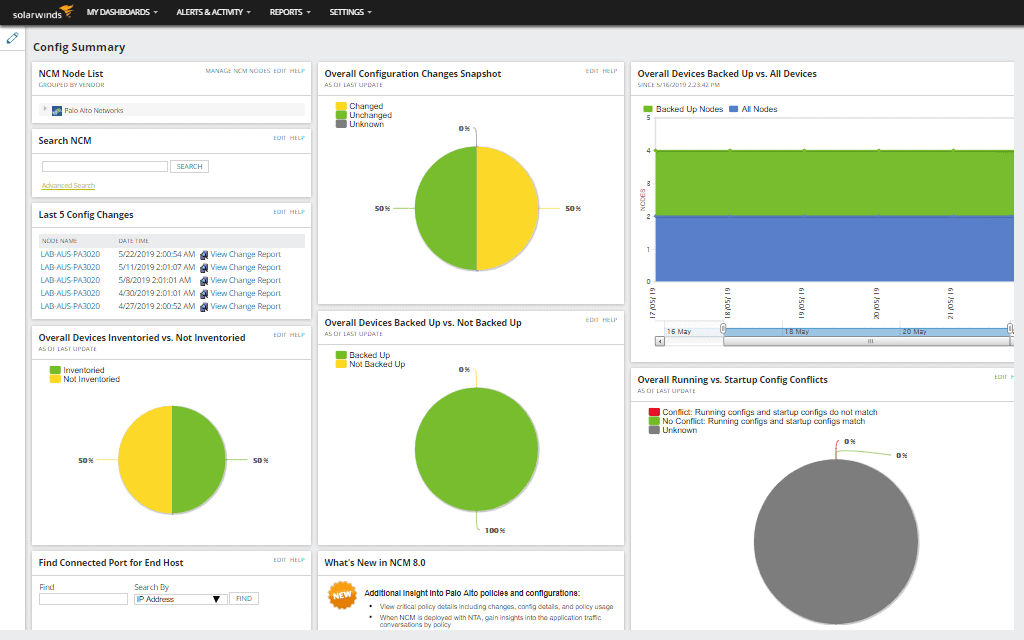
1. SolarWinds Network Configuration Manager – FREE TRIAL
The SolarWinds Network Configuration Manager is an automated platform that handles all aspects of your network security and audit. Coming from a world-leader in network management and audit, this platform has all the features you need to stay on top of what’s happening in your network.
Key Features:
- Monitors all devices including network switches and routers, and works well even in complex networks
- Gives a unified view of all the information you need through its centralized dashboard
- You can monitor configurations, changes, and backups to every device on the network
- Helps to quickly identify unauthorized changes in the devices, so you can address them right away
- Provides continuous updates about the health of devices, performance, failed backups, noncompliance to established standards, vulnerable gaps in confirmation, and more
- The inventory reports are designed to give you quick information about the health of devices. Also, these reports are compliant with the industry standards
- Gathers key information about devices such as the serial numbers, ports, IP addresses, end-of-life dates, and more
- Keeps devices current by giving you updated information
- The alerts can be customized to meet your preferences
- Streamlines change management
- Uses network automation to handle backups
Why do we recommend it?
We recommend SolarWinds Network Configuration Manager for its comprehensive, automated approach to network management and security. It excels in real-time monitoring and alerts, offering a centralized dashboard for a unified view of your network.
Who is it recommended for?
This tool is recommended for network administrators and IT professionals tasked with maintaining a secure, efficient, and compliant network. It’s especially useful for large or complex networks where automated monitoring and updates are crucial.
Pros:
- Easier to track network switches and routers
- Network scanning and discovery features help gather all data essential to create an accurate inventory of network devices
- Deploys firmware updates to outdated devices automatically
- Create audit reports on all network devices
- Notifies about configuration changes and other details
Cons:
- Designed for corporate environments run by network professionals; it was not created for home users.
The pricing starts at $1,687. Click here for a fully functional 30-day free trial.
EDITOR'S CHOICE
SolarWinds Network Configuration Manager is our top network monitor because it seamlessly blends comprehensive network management with robust security features. Its automated approach is especially effective in large and complex network environments, ensuring every aspect of network configuration is monitored and managed efficiently. The centralized dashboard is a standout feature, providing a unified view of all network activities, which is invaluable for IT professionals.
Its capability to identify and address unauthorized changes swiftly enhances network security. SolarWinds Network Configuration Manager’s consistent updates on device health and compliance keep the network running smoothly, making it an indispensable tool for network administrators.
Download: Download a 30-Day Free Trial
Official Site: https://www.solarwinds.com/network-configuration-manager
OS: Windows
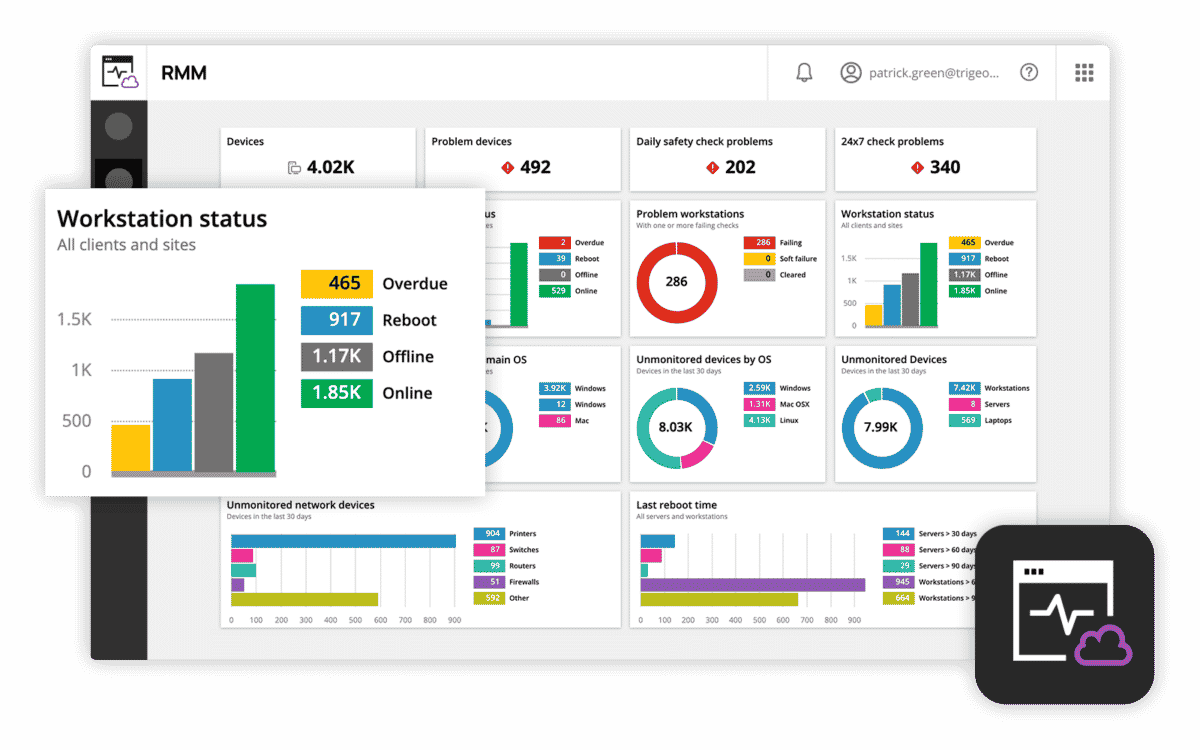
2. N-able N-sight – FREE TRIAL
N-able N-sight consists of a bunch of remote management and monitoring tools to secure and maintain your remote computers. This cloud-based IT solution is designed to keep your business safe and at the same time, allow your employees to access the applications from anywhere.
Key Features:
- Comes with out-of-the-box monitoring templates
- Provides fast and remote access
- Handles patch management automatically
- Takes care of backup and recovery
- Gives intelligent insights into the possible risks and vulnerabilities
- Manages the antivirus updates automatically
- Protects web resources from cyberattacks
- Remotely monitors both Mac and Windows devices
- Leverages integrated endpoint protection to respond to ever-changing threats
- Monitors a wide range of devices such as switches, routers, firewalls, and more
- Automatically discovers devices on the network
- Provides detailed network visibility including node or hop information, QoS monitoring, history, and performance
- Advanced reporting module generates reports for meeting the compliance of different standards
- All the pertinent information can be viewed from a single dashboard
Why do we recommend it?
We recommend N-able N-sight for its all-encompassing cloud-based IT solution that caters to both remote management and monitoring needs. Its capabilities range from automatic patch management to integrated endpoint protection, making it a versatile tool for maintaining business security.
Who is it recommended for?
This platform is highly recommended for IT managers and administrators who oversee remote teams and need a robust, cloud-based solution to secure and maintain remote computers. Its detailed network visibility and advanced reporting also make it suitable for compliance managers.
Pros:
- Automatically manages all the antivirus upgrades
- Supports QoS monitoring and automated patch management
- Provides detailed visibility into history, performance, as well as node information
- Uses integrated endpoint protection to react to threats that are constantly changing
- Creates backup and prevents web resources from cyberattacks
Cons:
- Not a great option for small networks and home users as it was created for large enterprises
Click here to get a quote. Click here for a fully functional 30-day free trial.
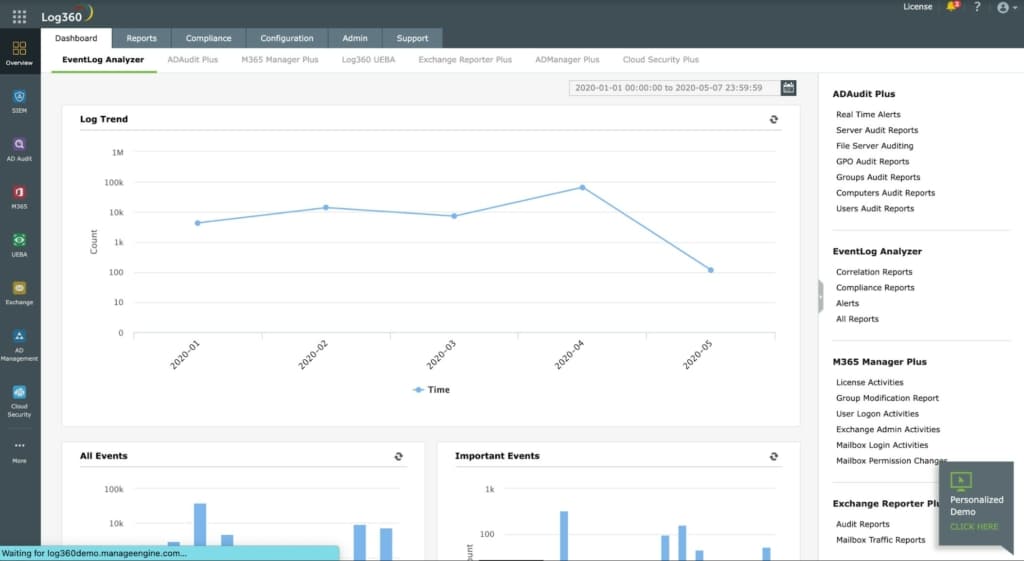
3. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a software package for installation on Windows Server that implements security monitoring through log scanning. This is a SIEM tool and it relies on the completeness of the log collection process and so the package includes a competent log management service. Logs are at the heart of compliance auditing.
Key Features:
- Collection of Windows Events and Syslog from operating systems
- Integration with more than 700 software packages
- Converts log formats into a common layout to allow them to be searched and stored together
- Management of a log file directory structure for ease of auditing
- A data viewer for live tail records and log files
- Spots network threats
- Compliance reporting templates for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA
- File integrity monitoring
- A SIEM
- Anomaly detection
- User and entity behavior analytics (UEBA) for standard activity baselining
- Alerts and notifications are sent through ManageEngine ServiceDesk Plus, Jira, and Kayoko ticketing systems
Why do we recommend it?
We recommend ManageEngine Log360 for its comprehensive security monitoring capabilities, from log scanning to compliance reporting. The tool integrates with over 700 software packages and offers tailored reports for multiple compliance standards, making it a go-to solution for any auditing needs.
Who is it recommended for?
This tool is ideal for security professionals, compliance officers, and IT administrators who require a robust SIEM solution with compliance reporting. Its extensive integration and alerting options also make it suitable for teams using a diverse range of software tools and ticketing systems.
Pros:
- Provides HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA compliance monitoring and reporting services
- It has agents that collect and forward log messages to the server
- Allows integration with 700+ software packages
- Makes auditing easier by managing a log file directory structure
- Monitors File integrity and detect network threats faster
Cons:
- The server does not support Linux systems
ManageEngine doesn’t publish a price list for Log360, so you should contact the Sales Department and request a quote. Start a 30-day free trial.
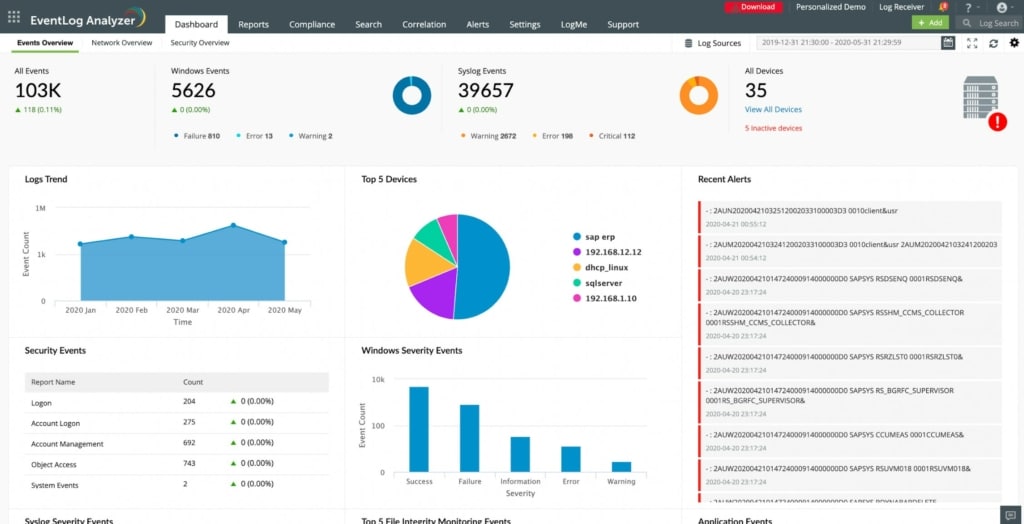
4. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer is a log management package that collects, collates, and parses log messages from all over the network. The system includes an analysis screen that provides tools for manual data searching. It is also a good package for compliance reporting.
Key Features:
- Collects Windows Events and Syslog messages
- More than 700 log sources
- Consolidates logs into a common format
- Displays arriving log messages in a data viewer
- Provides log message throughput statistics
- Tools for manual data analysis
- Includes a library of threat analysis templates
- Stores log messages in files plus creates a meaningful log file directory structure
- Database activity monitoring
- Monitores Web servers
- Monitors DHCP and DNS servers
- File integrity monitoring
- Event correlation
- Allows the creation of custom alert rules
- Forwards alerts as notifications through PagerDuty, Slack, SMS, and email
- Compliance reporting templates for PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001
- Available for Windows Server and Linux
Why do we recommend it?
We recommend ManageEngine EventLog Analyzer for its extensive log management capabilities and compatibility with over 700 log sources. The package not only collects and parses log messages but also provides threat analysis templates and compliance reporting, making it an all-in-one solution for network security.
Who is it recommended for?
This tool is highly recommended for IT administrators, cybersecurity analysts, and compliance officers who need a comprehensive log management system that supports a wide variety of log sources. Its alerting functionalities via PagerDuty, SMS, and email also make it suitable for teams that require immediate notifications for security incidents.
Pros:
- Users can access 700 log sources and combine records into a single, standard format
- Offers several tools to run manual data analysis
- Notifies admins using PagerDuty, SMS, and email
- Users can access several threat analysis templates
- Monitor web, DHCP, as well as DNS servers
Cons:
- Limited scalability and report customization requires improvement
There are three editions of EventLog Analyzer:
- Free – $0
- Premium – from $595 per year
- Distributed – from $2,495 per year
Start a 30-day free trial of the Standard edition.
5. Intruder
The Intruder is an online vulnerability scanner that constantly scans your network to identify vulnerabilities, so you can fix them before hackers get to them. This tool provides enterprise-grade security for critical systems, network infrastructure, websites, cloud systems, and endpoint devices.
Key Features:
- Sends intelligent results that are most relevant for your business
- Reduces false positives and reports only actionable issues that impact your business
- Monitors applications on the cloud and on-premise
- Comes with APIs that make it easy to integrate it with your CI/CD pipeline.
- Creates regular reports in PDF for easy tracking and understanding
- Automatically scans your systems for the latest vulnerabilities
- Identifies gaps and vulnerabilities in your network, so you can eliminate the associated risks
- Provides enterprise-grade security without the unnecessary complexity
- Scans for flaws like SQL injection and cross-site scripting
- Identifies common security exposures in your cloud environments
Why do we recommend it?
We recommend Intruder for its intelligent vulnerability scanning that minimizes false positives and focuses on actionable issues. With capabilities for on-premise and cloud application monitoring, along with seamless CI/CD pipeline integration, it offers a comprehensive security solution.
Who is it recommended for?
Intruder is ideal for businesses of all sizes that require a proactive approach to cybersecurity. It is particularly useful for DevOps teams due to its API integrations for CI/CD workflows, and for security analysts who need an efficient and automated way to identify and track vulnerabilities.
Pros:
- Allows keeping track of both on-premises and cloud-based apps
- Enterprise-grade protection is available
- Makes integration with CI/CD workflow simple using APIs
- Track the performance by generating reports in PDF format
- Discover the latest vulnerabilities by running automated scans
Cons:
- Users may take time to explore all of the platform’s features as it is highly intuitive
- Lacks generating detailed reports
Intruder offers three plans and they are:
- Essential ($97/month) – Checks for over 9000 security vulnerabilities across the entire infrastructure
- Pro ($161/month) – Unlimited scans on demand, monitors cloud integrators, offers API and developer integrators, and sends emerging threat notifications.
- Verified ($1,195/month) – Enterprise-grade scanning, reduces false positives, reviews impact, and offers freeform bug hunting.
Click here for a 30-day free trial.
6. ITarian Network Assessment Tool
ITarian Network Assessment Tool that monitors all the hardware and software components to ensure that the entire network is safe from threats.
Key Features:
- Creates customized reports with some of the report types being full detail, client risk summary, asset detail, excel export, XP migration readiness, and change management
- Identifies the hardware and software components that need an upgrade, repair, maintenance, and replacement
- Generates an IT checklist to ensure that there are standard IT assessment procedures in place for the entire team
- Creates a site interview guideline to ask the right questions during a network security assessment
- Highlights the security issues and risks and recommends the appropriate solutions
- Reports the new devices that were added to the network after the last assessment
- Allows administrators to perform in-depth scans
- Comes with a wizard to allow users to import via Active Directory, Workgroup, or IP range
- Does SWOT analysis and provides new opportunities
Why do we recommend it?
We recommend ITarian Network Assessment Tool for its comprehensive monitoring capabilities that cover both hardware and software components. With features like custom reporting, SWOT analysis, and actionable security recommendations, it offers a well-rounded solution for network security.
Who is it recommended for?
This tool is recommended for IT administrators and security professionals who are responsible for ensuring network security across an organization. Its ability to create standard assessment procedures and checklists also makes it ideal for compliance officers.
Pros:
- Generate and export customized reports
- Discover hardware and software components that require repair or replacement
- Identifies security issues and risks in real-time
- Run in-depth scans
- Allows importing via Active Directory
Cons:
- Does not work well with all types of networks
- At times generates false positives
The cost depends on the number of endpoints. Click here to get a custom quote. Click here to enroll up to 50 devices for free.
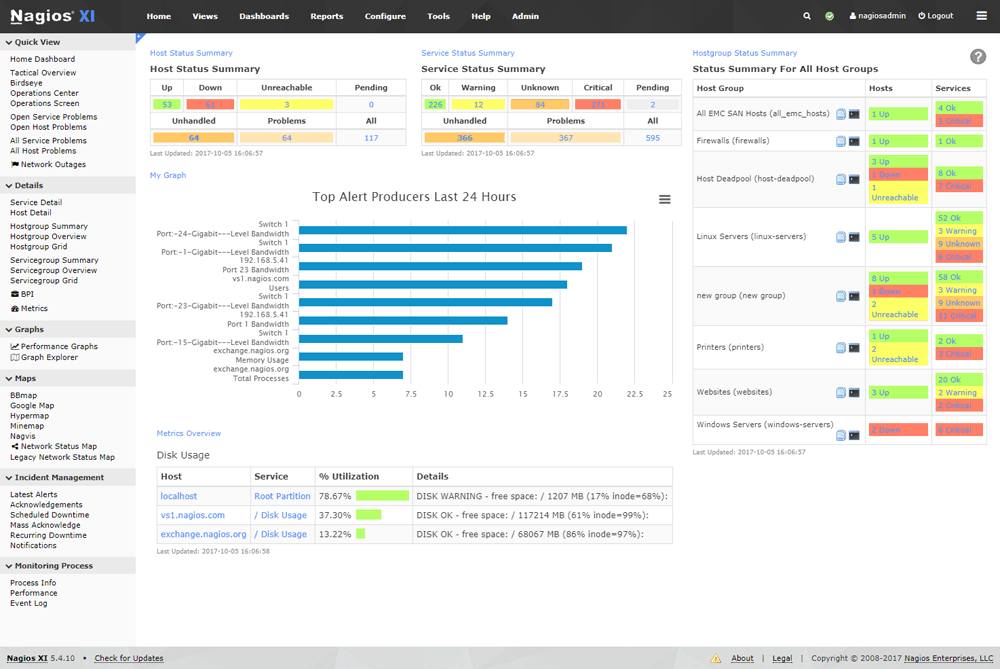
7. Nagios
Nagios is a free and open-source application for monitoring systems, networks, and infrastructure. Though it was designed to run on Linux servers, it also works well on Windows and Unix systems.
Key Features:
- Generates reports on a wide range of parameters such as disk usage, CPU utilization, and memory consumption.
- Sends alerts if values are beyond a threshold limit.
- Comes with performance counters that allow you to customize the metrics and their values.
- Monitors specific processes that you deem are essential for your systems
- You have the flexibility to decide on the processes and applications that need monitoring
- Ensures the availability of different devices
- Quickly detects network outages, protocol failures, and failed services, processes, and batch jobs.
- Offers a high degree of visibility into the health of different devices on your network
- Easily scalable and is adept at solving problems that come up in a global network.
- Its centralized dashboard gives a complete view of the status and availability of all the devices on your network.
Why do we recommend it?
We recommend Nagios for its robust and customizable monitoring capabilities, including alerts for system values beyond set thresholds and detailed reporting on various performance parameters. Its scalability and open-source nature make it a versatile solution for different environments.
Who is it recommended for?
Nagios is ideal for IT managers and network administrators who require a scalable and customizable tool for monitoring a wide range of metrics. Given its open-source foundation, it’s also a good fit for organizations that prefer to tailor the software to meet their specific monitoring needs.
Pros:
- Track and report CPU and memory utilization
- Configure threshold alert settings
- Identifies network outages and failed services
- Better visibility into the health of each device
- Quick insights into device status and availability
Cons:
- Offers minimal support
- Lacks access governance
The Nagios framework is 100% FREE, but you may have to pay for the plugins and monitoring applications such as Nagios XI.
Click here to download Nagios.
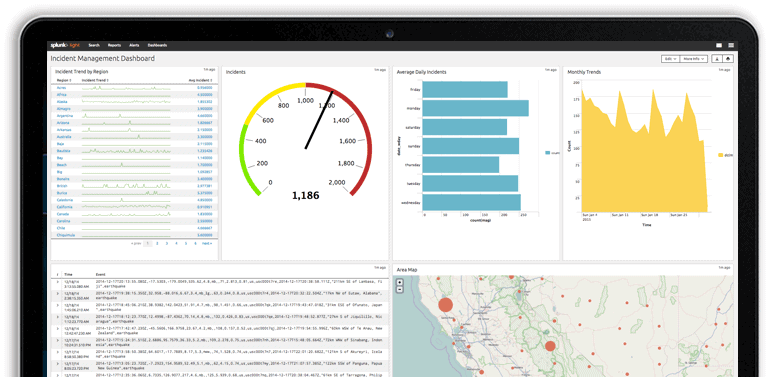
8. Splunk
Splunk is a platform used for monitoring and analyzing the data in real-time and accordingly, provides actionable insights. It also creates graphs, charts, and other tools for visual representation.
Key Features:
- Monitors hybrid and multi-cloud environments
- Consolidates actionable data and eliminates a siloed architecture
- Shortens MTTD and MTTR by providing complete visibility into the problem.
- Has AI-driven streamlining analytics for cloud-based services and infrastructure to analyze them in real-time
- Comes with more than 250 out-of-the-box integrations
- Has an advanced alerting system that reduces the chances for false positives
- Combines different data to give you a centralized view
- Generates reports that meet the compliance requirements of many standards.
- Creates visually appealing graphs and charts for quick reading and understandability
- Offers transparent pricing, so you can stay on top of your usage and budgets
- Auto discovers devices on the network
- Streamlines workflows
- Predicts future performance degradation and outages
Why do we recommend it?
We recommend Splunk for its real-time data monitoring and analytics capabilities. It excels in reducing both Mean Time to Detect (MTTD) and Mean Time to Resolve (MTTR), thanks to its advanced alerting system and wide array of integrations.
Who is it recommended for?
Splunk is particularly well-suited for organizations that operate in hybrid or multi-cloud environments and need to consolidate data from diverse sources. It’s also ideal for compliance-focused businesses, given its ability to generate reports that meet various regulatory standards.
Pros:
- Generates actionable insights
- Reduces MTTD and MTTR
- Offers 250+ integrations
- Reduces false positives with an advanced alerting system
- Supports auto-discovery feature
Cons:
- At times integration with other tools is difficult
- Setup and management requires expertise
The cost depends on the workload and package. So, contact the sales team for an accurate quote. Click here to get started. You can choose to try the cloud version or download the software to your computer.
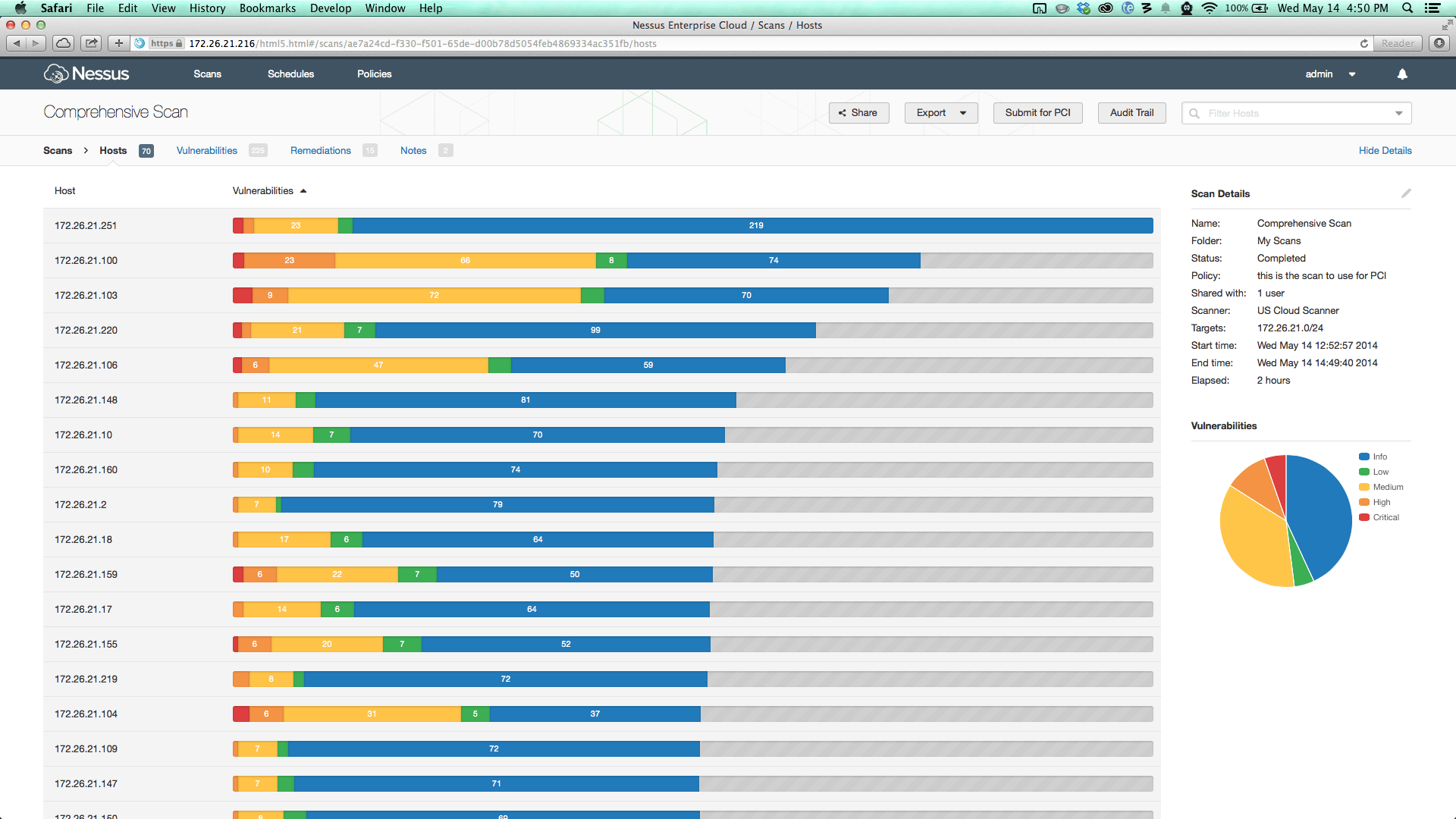
9. Nessus
Nessus is a simple remote scanning tool that scans a network and raises an alert if it detects any suspicious behavior. However, it merits to note that Nessus is not a complete monitoring tool by itself as it only raises alerts and doesn’t proactively fix them.
Key Features:
- Has one of the lowest false positive rate
- Comes with more than 156,000 plugins
- Saves a ton of time and money
- Simple to use and requires no advanced training
- Identifies vulnerabilities across the entire network
- It comes with many pre-configured templates, including 450 templates for compliance
- Reports can be customized to meet your preferences
- Provides a grouped view so you know which broad divisions need your attention.
- It is highly extensible
- Highly cost-effective for companies of all sizes
- Works well with other solutions from Tenable.io
Why do we recommend it?
We recommend Nessus for its exceptionally low false positive rate and its library of over 156,000 plugins. Its ease of use and pre-configured templates make it a versatile tool for identifying vulnerabilities across a network.
Who is it recommended for?
Nessus is ideal for businesses of all sizes that prioritize vulnerability detection and compliance. With its ability to integrate seamlessly with other Tenable.io solutions, it’s particularly useful for organizations that are already invested in the Tenable ecosystem.
Pros:
- Offers access to 156,000+ plugins
- Generate custom reports as per preference
- No advanced training is needed
- Minimum false positive rate
- 450 templates for compliance are available
Cons:
- Fewer integration options are available
- Scan operations can consume a lot of resources and slow down the system
Nessus comes in three plans and they are:
- Nessus Essentials (FREE) – Scans 16 IPs
- Nessus Professional ($3390 per year) – Scans unlimited IPs
- Tenable.io ($2,275 per year) – Allows you to deploy unlimited scanners and works on a subscription-based model
Click here to download Nessus Essentials.
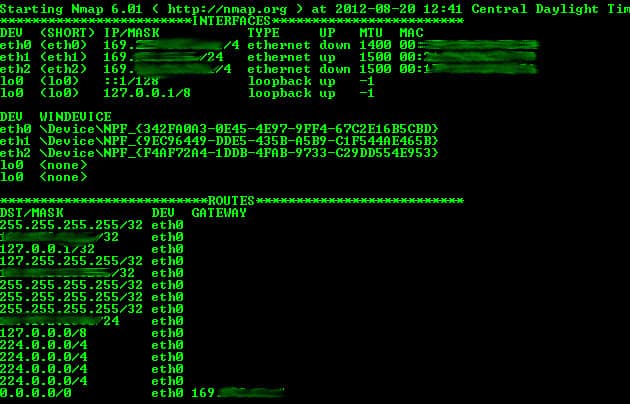
10. Nmap
If you’re looking for a free and open-source network scanner, Nmap is a good choice. It’s an acronym for Network Mapper and specializes in vulnerability scanning and network discovery. It can be used to monitor a single host or a large network with thousands of devices.
Key Features:
- Supports many advanced techniques for monitoring IP filters, firewalls, and routers
- Scans both TCP and UDP ports
- Offers OS detection, ping sweeps, version detection, and more.
- Simple to use and come with both a command-line and graphical user interface
- It is well-documented, so you can find answers to most questions on its manuals
- Backed by a vibrant community of developers and users
- Though it was first written in C++, it has been extended to C, Perl, and Python, and over the years, has received tons of contributions from developers worldwide
Why do we recommend it?
We recommend Nmap for its versatility in network scanning and its support for both TCP and UDP ports. Its strong community backing and extensive documentation make it a reliable choice for a wide range of network monitoring tasks.
Who is it recommended for?
Nmap is suitable for both beginners and advanced users due to its dual interface options (command-line and GUI). It’s ideal for organizations of all sizes looking to perform vulnerability scanning, network discovery, and monitoring firewalls and routers.
Pros:
- Monitor firewall and routers
- Nmap has a strong community for guidance and discussions
- Supports command-line as well as GUI
- Provides access to OS detection
- Proper documentation is available
Cons:
- Does not offer GUI, as a result, it requires using Zenmap for all interface features
- Lacks behavioral analysis and proactive security features
Nmap 100% FREE. Click here to download Nmap.
Conclusion
So far, we have looked at some of the best network security auditing tools available in the market today to scan websites, servers, ports, network devices, cloud applications, and just about every other device in your network. While some devices are more suited for smaller networks, most of the choices we have discussed above are highly scalable, so you can easily extend their use as your business grows. Make your pick based on the size of your network, available budget, and the specific features you’re looking for.
So, how important is network security auditing for you? Which tool do you prefer and why?