Wireshark is a handy tool for analyzing your network traffic and gathering a ton of useful information from it, such as the performance of your network, the health of devices, and possibly even a cyber attack.
So, how does this work?
Data Packets
Every time you open your browser and type a URL, what happens is your computer takes the URL to a server called the Domain Naming Server. This server has a table where it maps each URL with its corresponding IP address.
An IP address is a unique set of numbers and possibly hexadecimal values depending on the version you’re using. These numbers help identify a specific device on the network. Every device that’s connected to the Internet has a unique IP address.
The URL that you enter is mapped to this IP address. With it, your request for information is routed to that specific device through a series of routers and gateways, depending on the location of the device that requested it and the device that contains it.
Once the device is identified, it responds with all the information your device had requested, and it passes through routers and gateways and reaches your device. Finally, your browser renders this data and displays it for you.
Though this may seem like a lengthy process, technological advancements have reduced the entire process to about 50 milliseconds, which is less than the time it takes for you to blink!
You might wonder how this process ties in with Wireshark.
The data transmitted between devices is divided into small packets and sent across the network. The device receiving these packets is responsible for ordering them correctly before responding or displaying as the case may be. All data within a network is sent through these data packets.
Wireshark is a tool that analyzes these network packets to identify their speed of transfer, any repetitive loss of packets that can point to a faulty device, excess traffic that could raise the alarms of an imminent attack, and more.
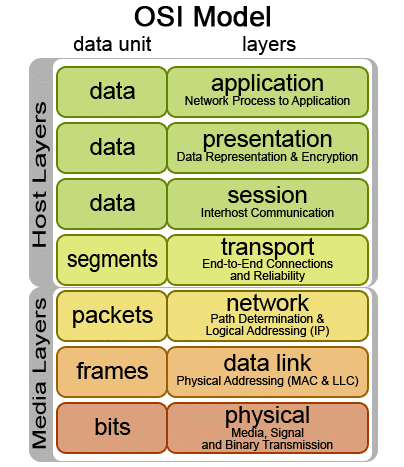
OSI Model and Encryption
Before we move on to Wireshark, let’s talk a bit about the OSI model and encryption. The OSI model consists of seven layers, and each has a specific role in transporting the packets from one device to another.
Source: Wikimedia
The third layer, called The Transport Layer, is responsible for encrypting and decrypting the packages to ensure that the contents of a data packet are not easily viewable as it traverses through a public network like the Internet. This layer was earlier called the Secure Sockets Layer, and hence the name SSL encryption.
What is Wireshark?
Wireshark is a tool that analyzes all the live data packets that pass through a network.
Wireshark analyzes the packets and describes their contents in two panes, right on the interface as the packets pass. The first pane contains data that is in human-readable form, so we can understand the kind of traffic that passes through along with any flags for abnormal transmission. The other pane contains the data in binary format (0s and 1s), which may look gibberish for the untrained eye.
Using Wireshark
Wireshark is a free tool that you can download and install.
Head to www.wireshark.org and click on “Download”. You’ll be presented with a few versions, so choose the one that fits your operating system.
Next, open Wireshark, and you can see the different networks connected to your machine. First, choose the network whose packets you want to analyze. Once you do that, Wireshark automatically goes into the capture mode and displays packets as they transpire within your chosen network. You can decide to stop the capture at any time and restart it.
You also have the option to filter these packets if you’re looking for something specific, like, for example, packets from a particular IP address or packets of a certain length.
Wireshark and Encryption
We saw earlier that SSL encryption protects the contents of the data packets, thereby making it difficult for anyone to intercept them and glean their contents.
Due to this encryption, it’s not directly possible for Wireshark to display the contents of the data packets that it captures. Instead, it requires a few extra steps to decrypt the SSL packets before they can be displayed.
Decrypting SSL with Wireshark
Now comes the question that we set out to answer in the first place – how can you decrypt SSL using Wireshark.
Here’s a step-by-step guide for the same.
Identifying the Encrypted Packets
The first step is to identify which data packets are encrypted because not all of them may be encrypted.
Some websites have what is called the SSL certificate. You buy extra when you buy a domain or even later to ensure that the packets to and from are encrypted at the Transport layer.
If you are requesting data from a website that doesn’t have an SSL certificate, Wireshark will automatically display the header in the middle pane and the contents of the packet in the lowest pane. But suppose your web server that’s sending the packets has an SSL certificate. In that case, you’ll notice the words “Transport Layer Security” in the middle pane and obviously, no data contents in a human-readable form.
This is also an excellent opportunity to understand the handshake protocol between the client and the server. If you look in the uppermost pane, you’ll see something called “Client Hello” and this will be followed by “Server hello”. This is the beginning of the handshake protocol, where both the client and the server establish a secure connection for communication.
Secret Key
An essential aspect of the handshake protocol is a secret key shared between a client and a server to establish a secure connection. This key is used to encrypt the contents of the communication between the two devices.
Often, this key is stored in a temporary memory, but you can ask Windows to store this secret key in a file, so you can access it later for decrypting the contents of the package.
So, how do you store this secret key in a file?
Here’s how you can do it
- Go to the Control Panel and click “Advanced System Settings”. If you’re using Windows 10, you’ll see this option on the left-hand pane.
- A new dialog box pops up, and on this, navigate to a button called “Environment Variables” at the bottom right. Click this button, and another dialog box pops up.
- Create a new environment variable and call it “SSIKEYLOGFILE” while the Variable value is the file path. For example, it can be “C:\Documents\Logfiles\SSL_key.log” . Later, you can navigate through this URL to find this file. Click OK to exit all the dialog boxes.
Decrypting on Wireshark
Now that you have created a file to store the secret key on Windows, it’s time to feed this information to Wireshark to help it decrypt the data packets.
To do this, open Chrome and visit a website that has an SSL certificate. Most prominent websites like ESPN, The New York Times, etc., have SSL certificates. An excellent way to check is to see if the URL has HTTP or HTTPS at the beginning. If the URL starts with HTTP, it indicates that the site is not secure. If you’re using Chrome, this lack of security will be shown in red.
Next, open the file where you stored the secret key, and you’ll see that it contains plenty of keys, which will look like a random collection of numbers, alphabets, and characters. So, again, this is proof that session keys are getting stored in the right place.
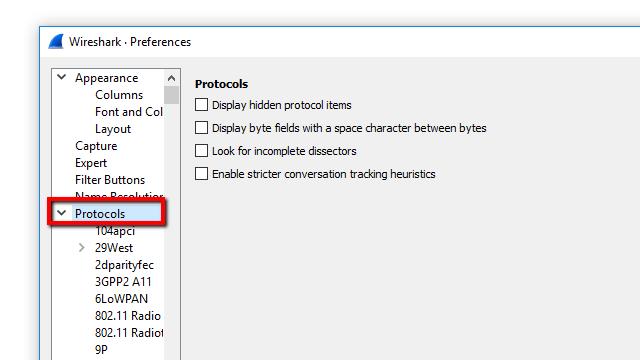
Open Wireshark and navigate to Edit > Preferences. Look for “Protocol” on the left-hand pane and from the list, choose “SSL”.
Look for “(Pre)-Master-Secret logs filename” and choose the file containing the session keys on the right-hand pane. Finally, click Apply and exit the dialog box.
Test the Decrypted Values
Lastly, you have to test if this is working.
Open Wireshark and look for the “Server Hello” packet. After this, you’ll notice that the packets have a description called “[SSL Segment of a reassembled PDU]”. Click on any of these packets, and in the lowest pane, you’ll notice a few extra tabs at the bottom.
Look for the “decrypted SSL data” tab and click it. Now, you’ll be able to read the contents of the data packets.
Thus, this is how you decrypt SSL with Wireshark.
As you can see, it’s not the most intuitive way to decrypt the contents and requires a good grasp of SSL working and the technical expertise to decrypt them. A better alternative is to use third-party tools like SolarWinds Deep Packet Inspection and Analysis.
Let’s learn a bit about this tool.
SolarWinds Deep Packet Inspection and Analysis – FREE TRIAL
The SolarWinds Deep Packet Inspection and Analysis tool is a part of the flagship Network Performance Monitor, and it gives all the insights you need into the health and performance of your network.
Key Features
The features of SolarWinds Deep Packet Inspection and Analysis are:
- Identifies the root cause for network latency
- Can calculate the response time for more than 1,200 applications
- Determines the impact on user experience
- Classifies risk levels
- Restricts network traffic as needed
- It comes with deep packet analysis
- Sends automated alerts when there is a drop in response times
- Provides a well-developed and intuitive dashboard to find all the information you need quickly.
- It doesn’t take up space in the database
- Quickly identifies excess levels of non-business traffic
- Facilitates proactive network troubleshooting
- Allows you to use NPM’s step-by-step wizard to deploy sensors
- Provides the option to choose custom applications for monitoring
Why do we recommend it?
This tool is an essential addition for network administrators seeking in-depth insights into their networks. The ability to identify the root cause of latency and calculate the response time for over 1,200 applications is unparalleled, ensuring that any network issues are promptly identified and resolved.
Who is it recommended for?
Given its extensive features and in-depth analysis capabilities, it is best suited for medium to large-scale enterprises. This tool will greatly benefit IT teams that rely heavily on maintaining optimal network performance.
This deep packet inspection comes with SolarWinds Network Performance Monitor. This NPM starts at $1,638. Click here for a fully functional 30-day free trial.
Conclusion
To conclude, all data transmitted across networks are divided into packets, with each packet has a unique header that describes its sequences and other pertinent information. Furthermore, the contents of every packet are encrypted at the transport layer of the OSI model before it is transmitted through the network.
This encryption aims to provide man-in-the-middle attacks. However, from a network administrator standpoint, it becomes difficult to decrypt the data to know if any malicious content is transmitted. Even advanced tools like Wireshark that support deep packet inspection don’t support decryption directly.
You will have to take some extra steps to decrypt the contents in Wireshark, or you can use powerful tools like SolarWinds Deep Packet Inspection and Analysis that come as a part of the Network Performance Monitor.
We hope this is useful when you want to read through the contents of data packets.