Cisco switches provide outstanding performance, security, scalability, and cost-efficiency for any network type. They are not ordinary plug-and-play devices that do not need configuration or involvement when resolving issues. However, Cisco switches do require an initial setup, ongoing monitoring, and maintenance.
How to configure a Cisco switch? In this step-by-step guide, we’ll configure a Cisco Catalyst Switch. Catalyst series is a well-known family of enterprise-grade network equipment, which varies from wireless controllers, switches, and wireless access points. Catalyst switches use the IOS as their operating system. There are two different interfaces to configure a Cisco switch, via the modern Web Console or through the more versatile Cisco IOS Command-Line Interface.
In this step-by-step guide on configuring a Cisco switch:
- Inspecting and connecting to your hardware
- Establishing a serial connection
- Moving through command modes
- Initial configuration commands
- Restrict access to your switch
- Configure your switch ports and VLANs
- Useful additional commands
1. Inspecting and connecting to your hardware
Before configuring your Cisco switch, you’ll need to be able to identify the power cable, switch ports, console ports. In addition, all Cisco switches come with LEDs that let you know the current state of your switch.
- Connect the switch’s power cable to the power source, and wait for the lights to come up.
- Check the front side of the switch. The switch’s (SYST) System’s LEDs are as follow:
- Off: The system is not powered. If power cables are connected but LEDs are off, check the power source or switch’s power cable.
- Green: The switch is operational.
- Blinking green: The system’s software is loading.
- Amber: Power is ok, but the system is not functional.
- Blinking amber: Fault with either: network module, power supply, or fan.
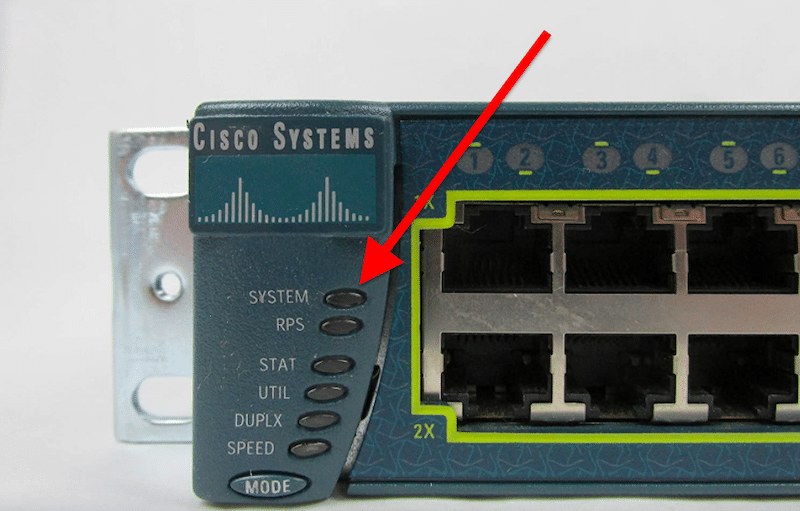
- Check the lights. They vary according to the Cisco Switch series, but generally, you should see the System light (as displayed above), along with other lights like Console, Active, RPS, Stack, PoE, Duplex, Speed, etc.
- Check the backside of the switch. Behind the switch, you should be able to see the power supply and console port. The console port of switches can be either, Serial or Mini USB. You should also see the IOS label on the backside, which shows the operating system version that comes by default.

How to connect to a Cisco Switch?
Connect to the console (management) port using a console cable.
- Depending on the console port of the Cisco Switch, you should use different adapters. Generally, there are two types of cable adapters: a Serial DB-9/Ethernet RJ45 Console cable (as shown below) and a USB/Serial DB-9 adapter (if your computer does not have a serial port).

- How to physically connect your laptop or PC to the console port? Plug the serial DB9 end of the console cable into your computer’s serial port and connect the RJ45 end on the Cisco Switch. But if your computer does not have a serial DB-9 port, connect the serial DB9 console cable end into the Serial-to-USB adapter and then plug it into your laptop. Bear in mind that these adapters work with a software driver.
2. Establishing a serial connection
To establish a serial connection to your computer, you’ll need to use software that controls serial lines. A well-known software that can do this is PuTTy. This software is a free SSH, Telnet, rlogin, and TCP client. Unfortunately, PuTTy is only supported by Windows. So if you are running Linux or macOS, there are some alternatives such as SecureCRT and MobaXTerm.
- Ensure you are connected to the console port of the Cisco switch using the correct cable, as shown in the previous section.
- Look for the COM (communication port) established by your computer. A COM port is the name of the serial port interface on PCs. It refers to physical ports and emulated ports like those of USB adapters. So, if you are using a USB/RJ45 adapter, you’ll need to find the COM port. To do this, go to Windows Device Manager and check your Ports. Then, locate the cable (with driver) that you are using and record the COM number (in this case, COM 1).
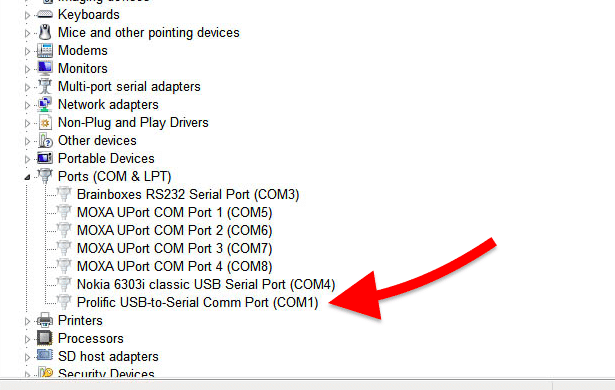
- Let’s configure the serial connection lines in your computer. Open PuTTY. Go to Configuration > Connection > Serial. Set the following parameters.
- The serial line to connect to The COM # you found in the previous section.
- Speed: varies according to your hardware — 9600 to 115200 (bps).
- Data Bits: 8
- Stop Bits: 1
- Parity: None
- Flow Control: None
- Save your connection and click on Open. You’ll be instantly connected to the switch.
3. Moving through command modes
Once connected to the switch, you’ll be greeted with the prompt:
Switch>
The hostname “Switch” is the current name of the switch, and the “>” means you are in “unprivileged” command mode. In this mode, you’ll only be able to display information but not change any configuration. To start configuring your Cisco switch, you’ll need to scale your user privileges.
Navigate through Cisco’s command modes
There are two privilege level modes:
- The “Unprivileged” User EXEC: “>” is the default mode. Here you can only display and see certain debug information.
- The “Privileged” User EXEC: “#” configuration mode. There are other modes within the privilege mode, including global, interface, subinterface, router, and line configuration modes.
To move across these modes, you can use the following commands
- enable. Change from unprivileged (>) to privileged (#)
- disable. Switch from privileged (#) to unprivileged (>).
- Configure terminal. Enter global configuration mode.
- exit. Revert one mode.
- end. Revert to the privilege enable mode.
4. Initial Configuration Commands
Although switching configuration will vary according to the topology, the primary and security design depends on the topology. For example, you can change the hostname, console port, vty ports, etc.
a. Configure an appropriate hostname
Enter to the privilege mode (enable) and then configuration mode (config terminal). Then, issue the following command:
Switch(config)# hostname <name>
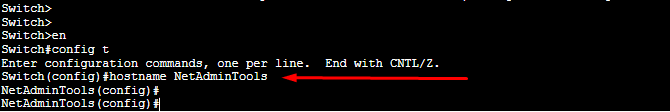
You’ll notice that the switch changed its name from “Switch” to whatever name you gave it.
b. Protect the privilege EXEC mode with an “encrypted” password
Protect the privilege EXEC mode and all sub-modes, including global, interface, subinterface, router, and line configuration modes. Enter global configuration mode and issue:
enable secret <your password>
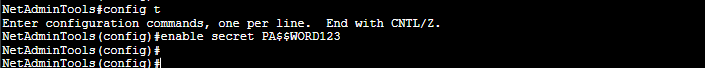
To test the new configuration, exit privilege EXEC mode and try to reaccess it. First, use the “exit” command and then “enable” (as shown in the picture below).
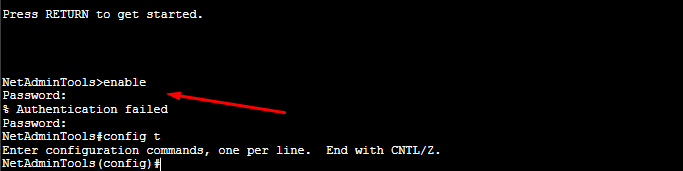
Notice that under unprivileged User EXEC mode, if you attempt to enter privileged User EXEC mode, the console will ask you for a password. If you type the incorrect password, you’ll not be able to move to the Privileged User EXEC mode.
You could have also used:
enable password <password>
But the main difference between “enable secret” vs. “enable password” is encryption. If someone gets their hands on the configuration file (either a printed version or TXT), they could easily find the password in plain text. With “enable secret,” the password is encrypted with MD5.
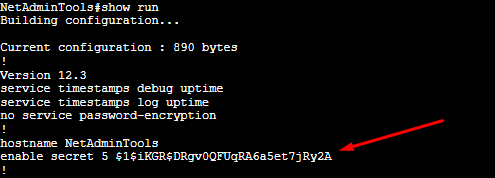
c. Configure a management interface IP
Logging to a switch for management can be challenging. First, using the console port requires you to be on-site and next to the switch. Second, you can’t log in remotely to an L2 switch via Telnet or SSH by default. Third, layer two switches won’t take IP configuration on their physical interfaces. So, the only solution is to create a Switched Virtual Interface (SVI) and assign it an IP.
Enter global configuration mode and issue the following set of commands:
Switch(config)# interface vlan 1
Switch(config-if)# ip address <ip address> <mask>
Switch(config-if)# exit
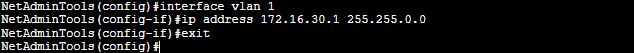
d. Configure a default gateway
To make your switch accessible from a remote network using Telnet or SSH, you’ll need to configure it with a default router. For example, L2 switches would only need a Default Gateway (DG) with L3 capabilities when they need management from external networks.
To configure a DG on your Cisco switch:
- First, make sure the DG is on the same network.
- DG must have the proper routes to route such packets.
- Then, enter global configuration mode and issue the following command.
Switch(config)#ip default-gateway <ip address>
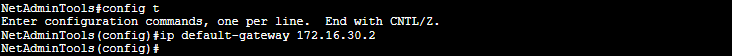
- Use the “ping” command to test connectivity.
- Always at the end of your remember to save your configuration with:
Switch# wr
5. Restrict access to the switch
Security is one of the essential tasks when configuring your switch.
a. Protect console, telnet, and aux ports
When you accessed the switch via the console for the first time, it didn’t request a password. To protect your switch from unauthorized access, you’ll need to establish authentication for all kinds of input connections. Aside from restricting console ports, you’ll also need to consider Telnet and Aux ports.
Issue the following commands:
- To find the current connection lines on your switch.
Switch>show running-config.
- To determine the current connection lines and their numbers.
Switch>show line.
- Configure line console password.
Switch(config)# line con 0
Switch(config-line)# password $$ECRETCONSOLE
Switch(config-line)# login
Switch(config-line)# exit
- Configure line vty password.
Switch(config)# line vty 0 4
Switch(config-line)# password $$ECRETVTY
Switch(config-line)# login
Switch(config-line)# exit
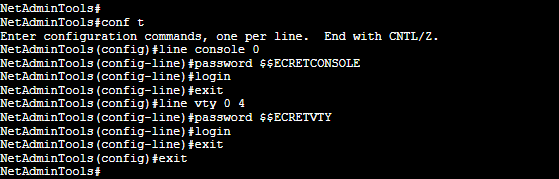
- Once configured, issue the “show running-config” again to verify your configuration.
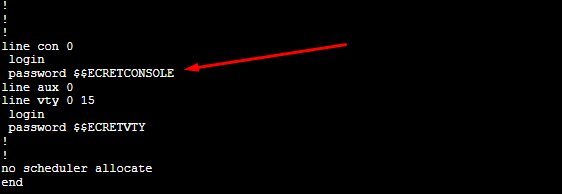
b. Restrict access at the IP level with an ACL
Create an Access Control List (ACL) to deny (or permit) access to the switch based on IP addresses. You can permit access to a single IP or deny access to an entire network with an ACL. Once created, you can assign the new ACL to the VTY line and protect Telnet access.
Issue the following commands:
- Create an ACL.
Switch(config)# ip access-list <number> <permit|deny> <ip address><wildcard>
- You can also create standard ACLs with the following set of commands.
Switch(config)# ip access-list standard TELNET
Switch(config-std-nacl)# permit <IP-1>
Switch(config-std-nacl)# permit <IP-2>
Switch(config-std-nacl)# exit
- Assign the new ACL to the VTY line.
Switch(config)# line vty 0 4
Switch(config-line)# access-class <access-list number> in
Switch(config-line)# exit
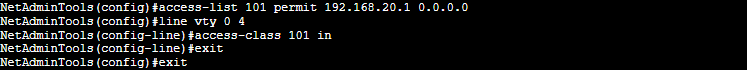
The example set of commands on the screenshot will do the following: The Access list number 101 defines “permit” to the IP address 192.168.20.1. Although no “deny” has been described in the ACL 101, all access lists end with an implicit “deny all.” If the traffic going through the ACL 101 does not match the rules (if IP is not 192.168.20.1), all traffic is ultimately dropped. Finally, this ACL is attached to the VTY (Telnet connections) 0 4, so nobody except 192.168.20.1 can connect to the switch via Telnet.
c. Disable unnecessary switch ports (or assign them to a Blackhole VLAN)
Although this step is not mandatory, it is highly recommended. As a best security practice, disable all unused ports using the “shutdown” command. Let’s suppose our switch has 48 switch ports and that we are not using ports from 18 to 48.
Switch(config)# interface range fa 0/18-48
Switch(config-if-range)# shutdown
Switch(config-if-range)# exit
Switch(config)#
An alternative to shutting down ports is creating a “black hole VLAN” and assigning them all unnecessary switch ports. As a general rule of thumb, it is recommended to assign switch ports (used or unused) to any VLAN, except VLAN 1. If any of these ports are still on the default VLAN 1, and the port is enabled, it might expose user broadcast or multicast traffic.
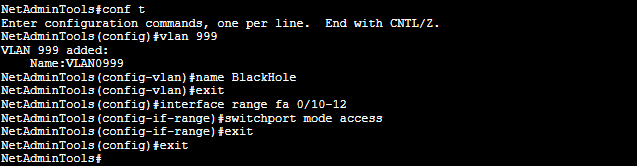
Create a black hole VLAN and assign all unused ports to it
Switch(config)#vlan 999
Switch(config-vlan)#name BlackHole
Switch(config-vlan)#exit
Switch(config)#interface range fa 0/18-48
Switch(config-if-range)#switchport access vlan 999
Switch(config-if-range)#switchport mode access
Switch(config-if-range)#exit
Remember to save your configuration with:
Switch# wr
Configure your switch ports and VLANs
One of the most critical functions of a Layer 2 Cisco Switch is to segment the network into different L2 VLANs, where each of these VLANs belongs to a separate L3 subnet.
Switch ports are by default assigned to VLAN 1, so you’ll need to create additional VLANs and assign the physical switch ports accordingly. As mentioned in the previous section, avoid using the VLAN 1 for user traffic.
Let’s create two VLANs and assign the physical switch ports to each of them. Remember that we have already disabled (or sent to blackhole VLAN) some portion of our switch ports.
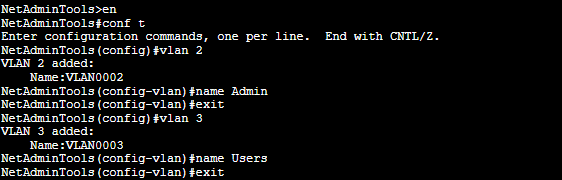
Use the following commands to create VLANs:
Switch(config)# vlan 2
Switch(config-vlan)# name Admin
Switch(config-vlan)# exit
Switch(config)# vlan 3
Switch(config-vlan)# name Users
Switch(config-vlan)# exit
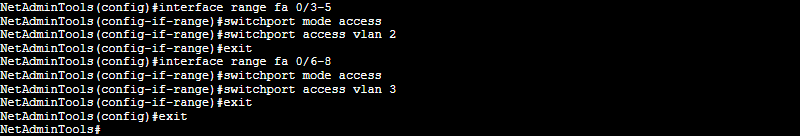
Assign the physical switch ports to each VLAN
Switch(config)# interface range fa 0/1-3
Switch(config-if-range)# switchport mode access
Switch(config-if-range)# switchport access vlan 2
Switch(config-if-range)# exit
Switch(config)# interface range fa 0/4-17
Switch(config-if-range)# switchport mode access
Switch(config-if-range)# switchport access vlan 3
Switch(config-if-range)# exit
Save your configuration with:
Switch# wr
7. Useful Additional Commands
After following the basic Cisco switch configuration shown in the previous sections, you can use the additional commands to monitor and troubleshoot your configuration.
a. Displays the current configuration
Switch# show run
b. Show the current MAC address table.
Switch# show mac address-table
c. Shows all interfaces, their configuration, and the status.
Switch# show interfaces
d. Displays the condition of all interfaces, including parameters like speed, duplex, and more.
Switch# show interface status
e. Shows all the VLAN numbers, names, and their associated switch ports.
Switch# show vlan