Today, data is not secure in any place; websites, cloud apps, or private apps. Even the application used by employees for collaboration or communication is risky. Cyberattackers are always on the move and look for entry points to get into your devices and steal data. Therefore it has become essential for organizations to depend on trusted and efficient security tools.
Here is our list of the best Forcepoint One alternatives:
- ManageEngine Endpoint DLP Plus – FREE TRIAL Dedicated vulnerability management solution that uses advanced data loss prevention strategies to monitor ongoing security processes and immediately stop any attempts at data theft. Get a 30-day free trial.
- CrowdStrike Falcon Endpoint Protection Prominent cybersecurity provider that offers endpoint protection, quick deployments, and detects fileless attacks and other threats in real time.
- Barracuda CloudGen Firewall Advanced SaaS security system that provides backup and detection capabilities, perfect for safeguarding complex distributed network systems.
- zScaler Cloud Protection Collection of cloud-based security solutions that is perfect for safeguarding on-demand software users
- Trend Micro Cloud One In addition to acting as an antivirus, the cloud-based system guards workloads, network layers, and storage services with the vulnerability management system.
- Sophos XG Firewall: Next-generation firewall protection solution that uses intelligent TLS inspection features to detect and protect the network from threats
The high rate of adoption of public cloud services has led businesses to be dependent on cloud security to guard their data and assets. To tighten security, organizations must adopt a new approach and use sophisticated cloud security tools that will protect sensitive information at all times against known and unknown threats.
Forcepoint ONE is one of the popular cloud security tools available in the market that routes traffic locally and supports unified policies to prevent data loss. Similarly, other cloud security platforms provide similar features. Let’s review Forcepoint One and check out its alternatives.
Forcepoint One Product Overview
Forcepoint ONE is an all-in-one cloud platform that secures remote workforces and enterprises with hybrid workforces. It allows users to gain better visibility and control over the data stored on the web, in the cloud, or private applications.
Key Features:
- Better data security
- Single console support
- Centralized cloud management
- Unified on-device agent
- Zero Trust and Security Service Edge
- Secure Web Gateway (SWG)
- Content Disarm and Reconstruction (CDR)
- SaaS Security Posture Management (SSPM)
- Remote Browser Isolation
- Supports two-way integration
- Provides Data Loss Protection (DLP)
- Supports Windows and macOS devices
- Zero-day sandboxing
- Supports better integration features
- Reduces agent bloat
- Cloud Security Posture Management (CSPM)
- Cloud Access Security Broker (CASB)
- Better visibility and identity-based access control
- BYOD security support
- Advanced threat protection
- Dynamic scalability
- Blocks malware and other threats
- Malware scanning
Why do we recommend it?
We recommend Forcepoint ONE for its comprehensive cloud-native security capabilities, especially its focus on securing remote and hybrid workforces. The platform not only simplifies security but also offers centralized management and advanced threat protection.
The cloud-native security platform routes traffic locally and enables businesses to secure workload from any device. Its launch has helped reduce the management burden and costs significantly. Further, it helps keep malware away from your sensitive data and devices.
Forcepoint One is a comprehensive and secure cloud-native security platform that monitors real-time traffic and prevents sensitive data from cyber attackers. Using this popular tool, you and your team can consistently secure all its BYO devices, private applications, or web data from any location.
To deploy, you require no additional agent or software as it is an all-in-one cloud solution. It is a trusted platform that makes security simple and protects all your sensitive data across business applications and BYOD devices at all times.
Forcepoint ONE is easily available and offers centralized cloud management and unified policies to prevent data loss.
Who is it recommended for?
Forcepoint ONE is ideal for enterprises with remote or hybrid workforces who need a single, unified solution for data loss prevention, advanced threat protection, and identity-based access control. Its all-in-one cloud architecture makes it particularly well-suited for businesses looking to reduce the complexity and costs of security management.
Pros:
- Simplifies security for remote and hybrid workforces.
- Security policies aid in protecting all managed and unmanaged apps/devices.
- Offers better visibility and control access.
- Keeps attackers at a distance with its integrated advanced threat protection.
- Maintains data security by stopping hackers from getting in.
- Monitors and controls interactions with different platforms.
- Blocks malware uploads in real-time.
- Protects all sensitive information from one set of security policies.
- Scans all files when uploading or downloading.
- Manages configuration, monitoring, and reporting from a single console.
- Offers comprehensive reporting and automated access through a unified endpoint agent.
- Allows use of a single set of login policies to prevent account takeovers.
Cons:
- Does not support the OCR feature.
- Users find it difficult to interpret reports.
- Only a few database servers are supported by the platform.
Forcepoint One Pricing
Licensed for Dynamic Data Protection (DDP), Forcepoint One is a combination of DLP Forcepoint One Endpoint and UEBA with excellent capabilities and features, making it a great solution for understanding risky behavior and blocking malware.
For quotes and other pricing details, make a direct request to the sales team.
Platform Support
Forcepoint ONE solution supports Windows and macOS platforms.
Software Download Link
Mitigate risk to business information available on the web, BYO devices, in the cloud, or in private applications with Forcepoint ONE security product. It has a single console that manages, monitors, and controls interactions with different platforms. Further, it provides protection to remote and hybrid workflows with its advanced threat protection features.
If you are looking for cloud-based security solutions that manage one set of policies to detect threats and respond faster, download the product here.
Top Forcepoint One Alternatives
Forcepoint ONE makes security simple and is one of the trusted cloud-native security platforms available in the market with advanced features and monitoring capabilities. But still, many companies look for similar alternatives. So, we have shortlisted a few top alternatives to Forcepoint One with similar features and functionalities.
The below-listed tools also provide comprehensive protection to your cloud platforms and data on the web or private applications. Using some of these tools, you can instantly detect threats, block them before they compromise the environment, and respond faster.
Also, most of the products can be deployed across multiple locations. So, have a look at each cloud security platform, compare and then come to a conclusion.
Our methodology for selecting the best Forcepoint One alternatives
We analyzed the market for top Forcepoint One alternatives and assessed different options based on the following criteria:
- Make sure your selected tool also covers hybrid systems and virtual servers
- Ability to automatically new devices or threats in real-time
- Instantly alerts or notifies using different channels on detecting security issues
- Centralized management and integration support for smooth operations
- Assessment opportunity or free trial options for tool testing
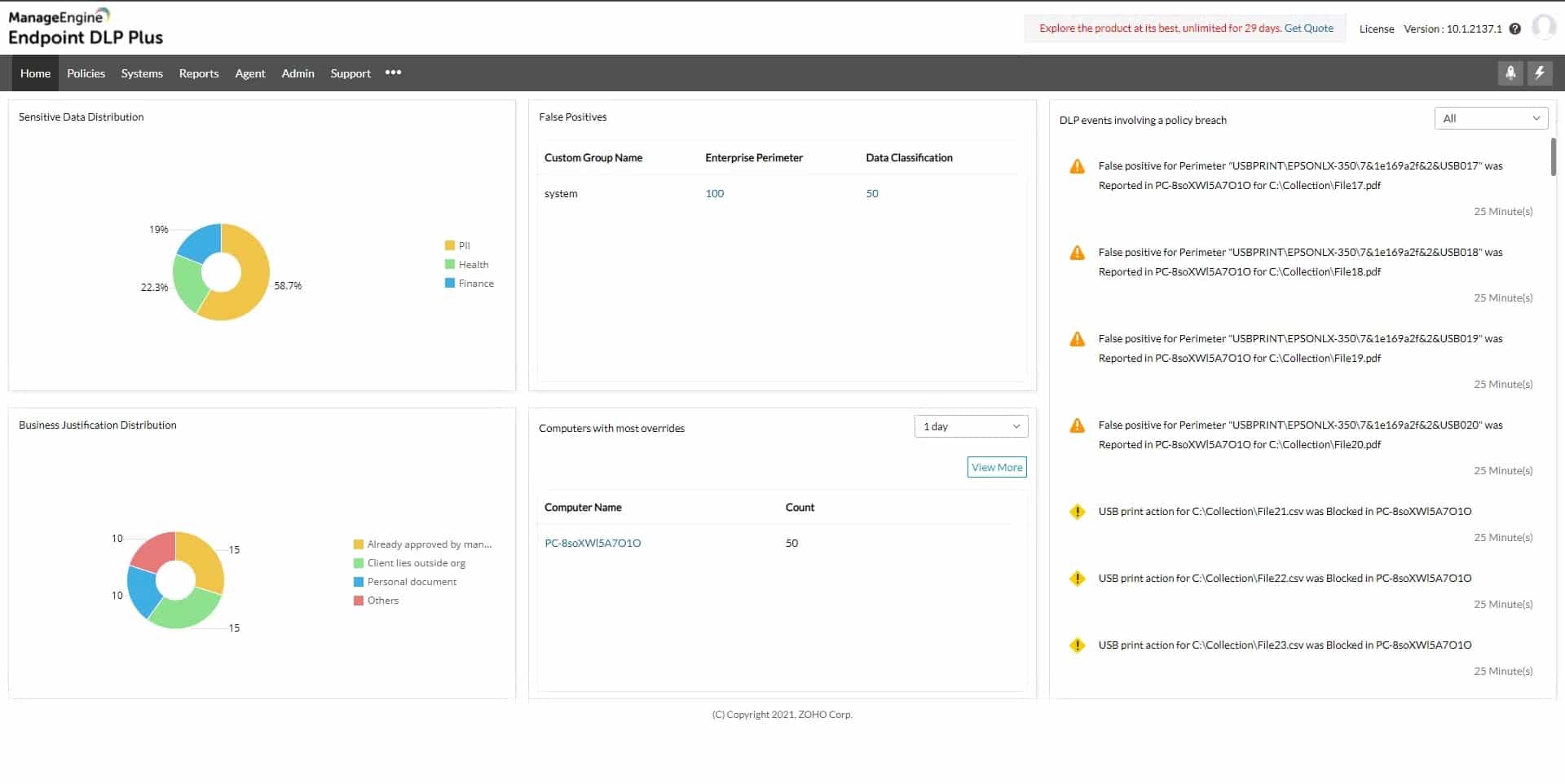
1. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP (Data Loss Prevention) Plus is a security solution from ManageEngine that assists organizations in protecting their sensitive data from loss, theft, or unauthorized access. It employs various techniques such as device control, data encryption, and monitoring to prevent data breaches and comply with regulations such as HIPAA, PCI-DSS, and others.
Key Features:
- Advanced Data Discovery: Runs an in-depth content inspection to discover all structured and unstructured data
- Data Containerisation: Limit the sharing of sensitive data to apps you can trust
- Device Control: Limits USB and other auxiliary devices from viewing or copying data for security purposes
- Quick Remediation: Takes quick actions for issues that might impact your cloud data
- Secure Email Collaboration: Monitors sensitive emails and ensures transmission takes place only via trusted domains
- Compliance Reporting: Generates an extensive audit report that complies with industry standards and regulations
- Centralized Management: Manages a variety of DLP tools from a single console
Why do we recommend it?
ManageEngine Endpoint DLP Plus stands out for its advanced features like full device control, strict security features, and robust reporting options. The tool is user-friendly and leverages data loss protection strategies to identify suspicious behavior and protect data on managed endpoint devices.
The platform allows administrators to establish policies restricting access to sensitive data on endpoints such as laptops and desktops. It also has the ability to encrypt sensitive data and monitor user activity to detect and prevent data breaches. Additionally, it offers detailed reporting and alerts to notify administrators of any suspicious or unauthorized access attempts.
Endpoint DLP Plus is a potent solution that can be employed to secure data and devices in any organization, particularly in the healthcare, finance, and government sector where sensitive data needs to be protected. It can be integrated with other ManageEngine solutions to provide a comprehensive security solution.
Who is it recommended for?
Businesses of all sizes and data security experts might find it a top solution for it comes with various advanced features that help protect their sensitive data across both LAN and cloud environments. Also, the user-friendly setup procedure allows even beginners to use and configure tools with ease.
Pros:
- Encryption Support: Prevents data leakage by encrypting all your sensitive files and data across the system
- Insider Threat Monitoring: Identifies suspicious behavior or threats in real-time by keeping a close watch over user interactions and data transmissions
- Backup and Recovery: Keeps a detailed backup of your data for uncertain events and offers quick recovery options
- Intuitive User Interface: User-friendly dashboard that helps view all the insights and visuals in an easy manner
- Advanced Reporting: Allows generating automated audit reports or schedule as per the preference
- Pre-Defined Templates: Comes with various predefined templates that can be used for sensitive data discovery
Cons:
- Limited Evaluation Option: The trial is not as long as a full-featured trial, which would allow you to thoroughly assess the tool’s functionalities.
Click here to download your ManageEngine Endpoint DLP Plus fully functional 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our editor’s top choice for it helps identify suspicious behavior, hijacking attempts, and data leakages at an initial stage. The tool comes with a wide range of features that make the whole process of threat detection and remediation easy and simple. Using it, you can scan all the endpoints and discover both structured and unstructured data across the system. Additionally, the tool detects all areas where data is exfiltrated and controls the flow according to the permissions granted to each user. In order to stop data theft, administrators can even closely monitor certain user activity.
You can even schedule your reports, get notifications in real time, and have access to obtain quick alternatives for fixing false positives. Furthermore, ensuring security even when the system is offline can be accomplished by remotely distributing these policies using lightweight agents.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/endpoint-dlp/
OS: Windows Server
2. CrowdStrike Falcon Endpoint Protection
CrowdStrike Falcon Endpoint Protection is a security framework that uses the latest technology to stop breaches and improve productivity. The unified cloud-based endpoint protection solution enables organizations to consolidate security solutions and instantly detect threats.
Key Features:
- USB Device Control: Offers visibility and control essential for companies to ensure that USB devices are used safely
- Firewall Management: Allows easy administration and control over host firewall policies with centralized management
- Threat Hunting and Intelligence: Uses AI-powered threat intelligence to detect suspicious behavior and stop breaches
- Identify Protection: Uses behavior analytics and flexible policies to prevent identity-based attacks
- Detection and Response: Detect threats and respond to them in real time
Why do we recommend it?
CrowdStrike Falcon Endpoint Protection allows users to simultaneously deploy hundreds of thousands of agents to protect cloud resources and gain insights into attackers’ moves. It comes with various advanced features like identity protection and threat intelligence that help detect malware and other threats in real-time.
Customers can deploy hundreds and thousands of agents at once using this powerful tool. It helps manage threat hunting and supports Endpoint Detection and Response (EDR) with deep visibility. Additionally, the product ensures that the attackers are blocked before they launch or compromise the environment.
No doubt you can find many tools online for endpoint protection, but what makes CrowdStrike Falcon Endpoint Protection stand out from the rest is its advanced features. Its monitoring capabilities and alert system enable businesses to gain quick insights into attackers’ moves. Using its excellent features, an organization can detect fileless attacks, malware, and other threats.
You can also generate insightful reports using the tool and make better decisions for your endpoint security. Furthermore, it supports several behavioral analysis techniques that help detect attackers faster.
If you are looking for a tool that provides continuous detection, prevention, and response, look no further. CrowdStrike Falcon Endpoint Protection is the perfect match as it provides visibility across all endpoints and prevents threats in real-time. It also records activities on a continuous basis and scrutinizes data for quick analysis.
Who is it recommended for?
You don’t need to search much further if you’re seeking a tool that offers continuous detection, prevention, and response. Businesses of all sizes can use the service to fix the security flaws in cloud systems.
Pros:
- Protection Package: Extensive range of solutions offering complete network and cloud resource protection
- Easy-to-Use Console: Easily access the console using a web browser
- Attack Intelligence: Tackles the risk of viruses or hackers hopping from one endpoint to another across the network.
- IT Hygiene: Offers real-time identification of unauthorized accounts and quick remediation for improving security posture
- Antivirus Protection: Protects endpoints by safeguarding against malware and ransomware attacks
Cons:
- Automated Bots for Support: Support is slow to address issues and relies heavily on automated bots.
3. Barracuda CloudGen Firewall
Barracuda CloudGen Firewall is a great product for cloud and hybrid network security. It supports VPN load balancing and comprises various other features that make it a great alternative to Forcepoint One. Using the popular product, organizations can run scans on incoming connections and files that help detect malicious behavior and malware faster.
Key Features:
- Multi-Layered Security: Uses advanced threat protection to detect and block threats
- Global Intelligence: Uses global threat intelligence network to quickly defend and protect against the most recent threats
- Integration Support: Allows for extensive integration with cloud-native features
- Cutting-Edge Firewall Technologies: Offers real-time network defense against a range of network threats
Why do we recommend it?
The Barracuda CloudGen Firewall has a traffic scanner to stop incoming malware, WAN optimization functionalities, email protection, and more in addition to an intrusion detection system. Furthermore, the service can be paired with other Barracuda Edge services and is hosted in the cloud.
The tool’s advanced threat protection capabilities and Intrusion Detection and Prevention System enables administrators to detect known and zero-day threats in real-time. Be it DoS, SQL injections, viruses, or spyware, Barracuda CloudGen Firewall ensures that none of the threats are left unnoticed with its multi-layered security.
Today, in order to combat zero-day threats and other threats, it is vital to adapt sophisticated defense techniques. Barracuda CloudGen Firewall uses a set of next-generation firewall technologies to protect your data, users, and workloads. Also, the product can be deployed across multiple locations, including Google Cloud Platform, AWS, Azure, etc.
Barracuda CloudGen Firewall has an easy-to-use interface and scales well when you need to monitor multiple networks. Another good feature of the Barracuda CloudGen Firewall is its NexGen Admin dashboard which allows users to get an overview of network activity. Also, it is customizable, helps generate reports in different formats and visualize firewall insights.
Who is it recommended for?
Businesses who want to safeguard websites with multiple networks and cloud services might find it suitable. Large companies, especially those who have to handle inbound requests for web servers, can use this tool.
Pros:
- Prevent Zero-Day Threats: Safeguards your resources against zero-day and ransomware attacks with multi-layered security
- Quick Deployment: Enables rapid deployments among various physical locations
- Data Security Monitoring: Watches over user access, workloads, and data security from any location.
- DoS Attacks: Prevents DoS attacks by configuring IDS/IPS
Cons:
- Area of Improvement: Configuring Barracuda CloudGen Firewall could be more intuitive
- No Pricing: There is no price listed for the platform. You need to contact the sales department directly for the product pricing.
4. zScaler Cloud Protection
zScaler Cloud Protection, powered by zero trust, is a security tool that provides comprehensive protection to your public cloud assets. As the demand for cloud services is rising, so are the chances of threats and business risks.
Key Features:
- Business Analytics: Provides insights into the business performance and helps optimize risk
- Cyber Threat Protection: Uses a comprehensive approach to secure workload and devices against cyber threats
- Data Protection: Ensures total data protection throughout the SSE platform by utilizing comprehensive TLS/SSL inspection at scale.
- Zero Trust Networking: Ensures that your remote workforce has direct, quick, and secure access to applications.
Why do we recommend it?
Using the Zscaler Security Cloud, which is spread over more than 100 data centers globally, businesses may safeguard their consumers by rerouting internet traffic through it. The fact that their clients don’t have to buy and maintain their own network security hardware or software reduces costs for them as well.
Clouds being dynamic and distributed require better protection and security features. zScaler Cloud Protection allows the organization to leverage intelligent automation and supports an architecture that helps reduce lateral threat movement within VPCs and secures web/app traffic across cloud environments.
It is one of the best tools if you want to eliminate operational complexities out of cloud workload security. Another benefit of choosing zScaler Cloud Protection over other tools is it secures your workload configurations and permissions.
Most cloud security incidents occur due to customers’ fault. However, if you implement CSPM, there are high chances that cloud-related security incidents will reduce and improve performance. Expanding your network to distributed public clouds using VPN can be expensive and risky. But, by investing in Zscaler Workload Communications, you can secure your workload communications across the internet or data centers.
Additionally, data exposure among cloud apps can occur due to misconfigurations. However, the zScaler Cloud Protection tool ensures proper configuration and compliance of cloud platforms. It helps identify, prioritize, and remediate misconfigurations which further aids in protecting sensitive data and restoring compliance.
Who is it recommended for?
For users who use cloud apps, such as those who are clients of an on-demand software service provider, Zscaler is the perfect tool. It is an affordable tool suitable for businesses of all sizes.
Pros:
- Consistent Data Protection: Constantly provides protection to your sensitive data
- Eliminate Lateral Movement: Limits unauthorized movement between systems to prevent the spread of threats
- Reduce Operational Cost: Put security policies in place to reduce operating costs for your business.
Cons:
- Complicated: Works best with multi-site hybrid networks that employ many workers.
5. Trend Micro Cloud One
Trend Micro Cloud One is a unified cybersecurity platform that provides comprehensive security to all applications built in the cloud. With Trend Micro Cloud One, you gain access to increased visibility and consistent security throughout the cloud environment.
Key Features:
- Application Discovery: Automatically discovers added resources and new applications
- Detection and Response: Detect threats and respond to security incidents before they impacts the system and performance
- Remediation: Quickly takes corrective measures to address the identified security issues
Why do we recommend it?
Trend Cloud One offers workload security in addition to other security capabilities. This service is a collection of modules for a cloud platform that assesses the security of various cloud assets, including storage, containers, and apps.
It is a highly flexible cloud security tool that supports integration with existing AWS, Microsoft Azure, and Google Cloud toolsets. Further, it also ensures that the cloud remains secure throughout the migration and expansion process.
Your organization has to no longer compromise on its performance or security with the unified SaaS solution. It is an automated security tool that covers all the cloud security services in a single platform and secures your data center, cloud, and containers. The hybrid cloud security capabilities of the tool help users detect and protect their cloud information against vulnerabilities and malware. Using its machine learning techniques and virtual patching features, organizations can automatically protect their new and existing cloud workload.
Trend Micro Cloud One is a great option if you have been looking for a workload security tool that minimizes business disruptions and delivers 24/7 threat prevention for the cloud. It helps businesses secure their cloud infrastructure.
Who is it recommended for?
This package works well with systems that are hybrid and has no compulsion to subscribe to the full platform. Each module has a monthly consumption limit that is waived for small firms, meaning they might avoid paying for the service altogether.
Pros:
- Better Visibility: Offers clear visibility into the entire cloud environment for better analysis
- Ensure Compliance: Monitors security settings and ensures they adhere to regulatory standards
- Centralized Management: Ensures all applications across the hybrid cloud environment are secure from a single platform
Cons:
- Adds Value for Businesses Using a Variety of Cloud Services: Small companies using just a single cloud platform wouldn’t benefit much from the package
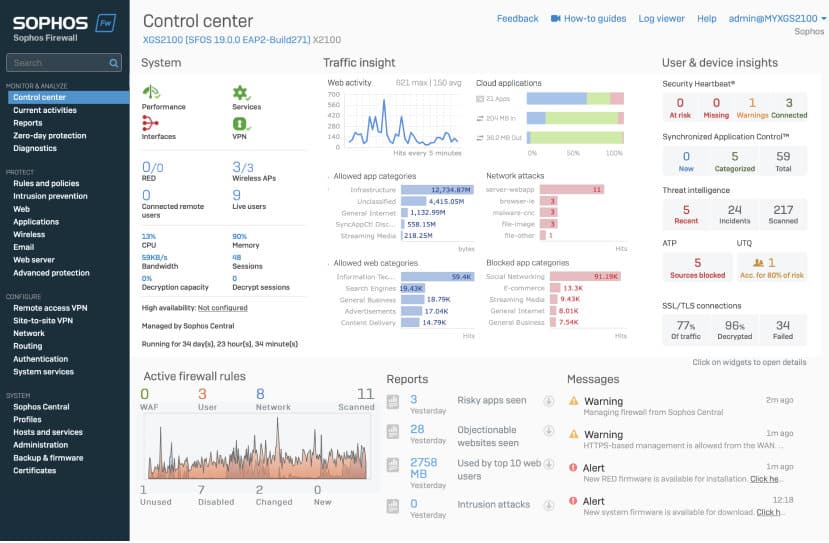
6. Sophos XG Firewall
Sophos XG Firewall is a next-generation firewall protection solution that detects and protects your network from the latest threats. Using the intelligent TLS inspection feature, the platform helps eliminate blind spots caused by encrypted traffic.
Key Features:
- Centralized Management: Manage all the cloud resources and their security from a single console
- Integration Support: Integrates well with Synchronized Security and Automated Threat Response from Sophos MDR and Sophos XDR to stop threats before they impact
- Automated Response: Automatically responds to detected threats and prevents escalation
Why do we recommend it?
Sophos XG Firewall is a great option due to its strong security features, which includes web filtering and threat protection. Even for businesses with limited IT resources, it is simple to deploy and administer thanks to its extensive policy controls, centralized management, and user-friendly interface.
Furthermore, it uses Deep Packet Inspection techniques to prevent your network from the latest ransomware and breaches. They are a series of next-gen firewalls designed to provide better visibility, flexibility, and performance. If you are looking for a security tool that is easy to manage, detects threats in real-time, and provides automatic responses, go for Sophos XG Firewall.
With the help of Sophos XG Firewall, organizations can better manage their firewall, detect and respond to threats faster, and monitor every activity of their network. They also provide unrivaled visibility which enables businesses to identify threats and accelerate their SaaS, SD-WAN, and cloud traffic.
One can access the trusted cloud-based platform from any location and provide immediate notification to administrators on detecting any suspicious activity on their network. Expose all the hidden risks and stop the latest attacks with high-performance IPS and ATP.
You can also perform an in-depth analysis of all network files, monitor the health status, and identify and block various zero-day file-based threats. Web Protection, sandboxing, Synchronized Security, and email filtering are a few features that make it a great alternate option.
Who is it recommended for?
Any size enterprise looking to protect its network infrastructure from a variety of cyber threats should consider the Sophos XG Firewall. Small and medium-sized enterprises who need enterprise-grade security features will find it very useful.
Pros:
- Powerful Protection: Offers complete protection against threats and attacks
- Work from Anywhere: Users can safely and securely access the tool from any location
- Detailed Insights: Provides quick insights about hacked users, devices, and apps
Cons:
- Documentation: Few resources or documents are available for support.
Conclusion
With more people using cloud computing services, the risk of exposure and threat is high. Thus, to protect highly sensitive business information and intellectual property, organizations must purchase or download trusted cloud security platforms.
Here, we have listed some of the best and most trusted cloud security platforms that provide advanced threat protection and data security. Forcepoint ONE is one of the most popular cloud-native security platforms used by some high-profile companies, such as Slack, Office365, AWS, etc.
We have also shared some of Forcepoint One alternatives that will lie within your budget and deliver better visibility, control, protection, and better performance.