Today, intrusion is a bigger concern than viruses as hackers are targeting even the most basic computer systems as a resource for malicious purposes. Identity cloaking, botnets, and crypto mining are a few examples. It has become crucial for companies to have protections in place that will protect systems from such malicious activities and attempts at all times.
Here is our list of the best ESET Endpoint Security alternatives:
- ManageEngine Endpoint Central – FREE TRIAL Offers centralized endpoint management with features like asset detection and patching. Ideal for medium to large-scale networks.
- CrowdStrike Falcon – Cloud-based solution utilizing AI for threat detection. Best for organizations needing high-level endpoint protection with scalable pricing plans.
- Syxsense Secure – Combines patch management, endpoint security, and vulnerability scanning. Suitable for businesses requiring a comprehensive, cloud-based solution.
- Symantec End-user Endpoint Security – Provides comprehensive cloud-based protection with AI methods. Ideal for businesses with diverse IT infrastructures needing flexible security solutions.
- Sophos SafeGuard Encryption – Offers full disk encryption with real-time threat protection. A great choice for securing data across various platforms without impacting performance.
- Panda Endpoint Protection – Perfect for small to medium-sized networks, providing centralized cloud-based management and Collective Intelligence technology.
The data any company holds is highly a significant resource that must be protected at any cost and given the utmost attention. Data theft, or even a security breach, on your endpoints can ruin goodwill with your customers or harm the company. As a result, the company can be fined or even sued. This is why most companies follow data security standards compliance for doing business as it builds trust among clients and potential partners.
You can also discover and invest in different antivirus solutions online, but we recommend ESET Endpoint Security as it is a reliable solution. ESET Endpoint Security is a solution that can act as a defense system against theft, misappropriation, tampering, or blackmail.
Here, we will discuss the ESET Endpoint Security solution, its features, benefits, and drawbacks. We have also shortlisted a few alternate solutions for ESET Endpoint Security. Learn about the different endpoint protection systems, compare them, and select the one that suits your requirements and budget.
What is ESET Endpoint Security?
ESET Endpoint Security is an antivirus software system launched to protect equipment attached to your network. Began trading in 1992, ESET has evolved to be one of the pioneers of cybersecurity with various security products available on the market.
It is a unified management tool responsible for protecting business devices (PCs or mobile devices), endpoints, business data, and users with multi-layered technology. Available as a series of modules, the package will need to be installed on every device that requires protection for better results.
An Endpoint Protection Platform (EPP) is a trusted security solution deployed to detect malicious activity, prevent data and systems from cyberattacks or intrusion attempts, and provide remediation solutions instantly. It is highly compatible with modern browsers, Windows, macOS, Microsoft Azure servers, iOS, Linux, and VMWare virtualizations. One can easily download the solution or use it on-premises for Windows or Linux.
The EPP solution is highly beneficial for any company, and focuses on three main areas of protection; endpoint protection, cloud security, and company data protection. It is one of the most easy-to-set-up and lightweight antivirus solutions that enable businesses to detect malware pre-execution, during execution, and post-execution.
Other notable features of ESET Endpoint Security include full disk encryption, cloud-based application protection, identification of ransomware files, Network Attack Protection, and more.
Key Features:
Here are a few advanced features of ESET Endpoint Security that make it a great option for your business data and system protection:
- Unified Console Management Cloud-based and on-premises unified management console ESET PROTECT that provides a real-time overview of all endpoints. The console also supports flexible reporting, offers network visibility, and manages security.
- Blocks Targeted Attacks Prioritize and block the latest threats before their delivery using the threat intelligence data. Also, it supports cloud-based updating features that quickly respond to missed detections.
- Prevents Fileless Attacks Uses scanners to constantly check memory, detect hijacked applications, and protect against fileless attacks.
- Safeguard Web Browsers Provides a special layer of protection for browsers coupled with memory and keyboard protection.
- Protects Against Network Attacks Helps in the quick detection of known vulnerabilities available on the network and stops the damage.
- Brute Force Attack Protection Discovers and blocks automated attacks that exercise password-guessing techniques to get entry into your network.
- Advanced Memory Scanner Monitors and scans the behavior of a malicious process once decloaks in memory and stops further damage.
- Provides Ransomware Shield Monitors all applications based on their behavior and reputation. Using the EPP, you get access to full protection against ransomware. Also, the feature enables the system to block any activity that resembles ransomware behavior.
- UEFI Scanner Adds a shield to your systems that protects the Unified Extensible Firmware Interface (UEFI). The UEFI Scanner was implemented to monitor firmware’s integrity and enforce the preboot environment’s security. On noticing any changes, it immediately alerts the user.
- Exploit Blocker Monitors exploitable applications, such as document readers, browsers, Java, Flash, etc. It enables businesses to focus on exploitation techniques and block threats immediately as it gets triggered.
- Behavioral Detection – HIPS The Host-based Intrusion Prevention System (HIPS) uses a predefined set of rules to identify, monitor system behavior, and prevent the system from suspicious activities.
- Botnet Protection Helps detect, block, and report malicious communication used by botnets to the users. Furthermore, it helps identify the offending processes.
- In-Product Sandbox Enables businesses to identify the real behavior behind obfuscated malware programs.
Why do we recommend it?
After installing ESET Endpoint Security and navigating its unified management console, we found that its multi-layered technology offers robust protection against a wide array of threats, from ransomware to fileless attacks. Its compatibility across multiple platforms further demonstrates its utility in diverse IT environments.
Who is it recommended for?
ESET Endpoint Security is an ideal solution for businesses that prioritize a multi-faceted approach to cybersecurity. Its suitability for various operating systems makes it highly adaptable, making it perfect for organizations that utilize a mix of Windows, macOS, and Linux.
Pros:
- Highly customizable dashboard that offers real-time overviews of all endpoints and network visibility
- Supports HIPS techniques to discover threats based on their behavior
- Prevents businesses from bot attacks and other threats
- Available as both cloud-based SaaS or on-premise
- Uses scanners to check memory and discover anything suspicious
- Compatible with modern browsers, Windows, Linux, Android, iOS, and other platforms
- Monitors system activity and provides remediation instantly
- Protects users from ransomware attacks
Cons:
- Small networks might fail to use all its features as they are more tailored for medium to large-size networks
- Admin console accessible on-premises only
Pricing and Plans
ESET Endpoint Security solution is available in different pricing plans, each supporting a different set of features:
The Protect Entry plan (first tier), supports five devices, offers strong machine learning, and endpoint protection starting at $239 per year. It also offers full protection to Linux and Windows servers.
ESET Protect Advanced is the next tier that offers endpoint protection to five devices with additional features like file server security, full disk encryption, and advanced threat defense.
ESET Protect Complete, the final tier on the list, along with the features of ESET Protect Advanced, offers mail security and cloud app protection.
Similarly, there are a few more plans supported by the ESET’s endpoint protection platform (EPP) that deliver enterprise-grade visibility, cyber risk management, expertise call support services, threat hunting, and more.
Website Link: https://www.eset.com/in/business/advanced-protection-bundle
The Best ESET Endpoint Security Alternatives
Investing in a plan that protects your endpoints has become crucial for all businesses. No doubt, the ESET Endpoint security solution is one of the popular products available in the market to protect against ransomware, balance performance, detect and false positives. But, it can be expensive for a few networks.
Our methodology for selecting the best ESET Endpoint Security alternatives
We picked the picked the tools below based on the following criteria:
- Comprehensive threat detection capabilities, especially against ransomware
- Flexibility in supporting various operating systems and devices
- User-friendly interface and ease of management, particularly for businesses with multiple branches
- Robust patch management and vulnerability scanning features
- Advanced AI-driven threat intelligence and monitoring
Here are a few alternate solutions and products available in the market that carry excellent properties and will deliver better results.
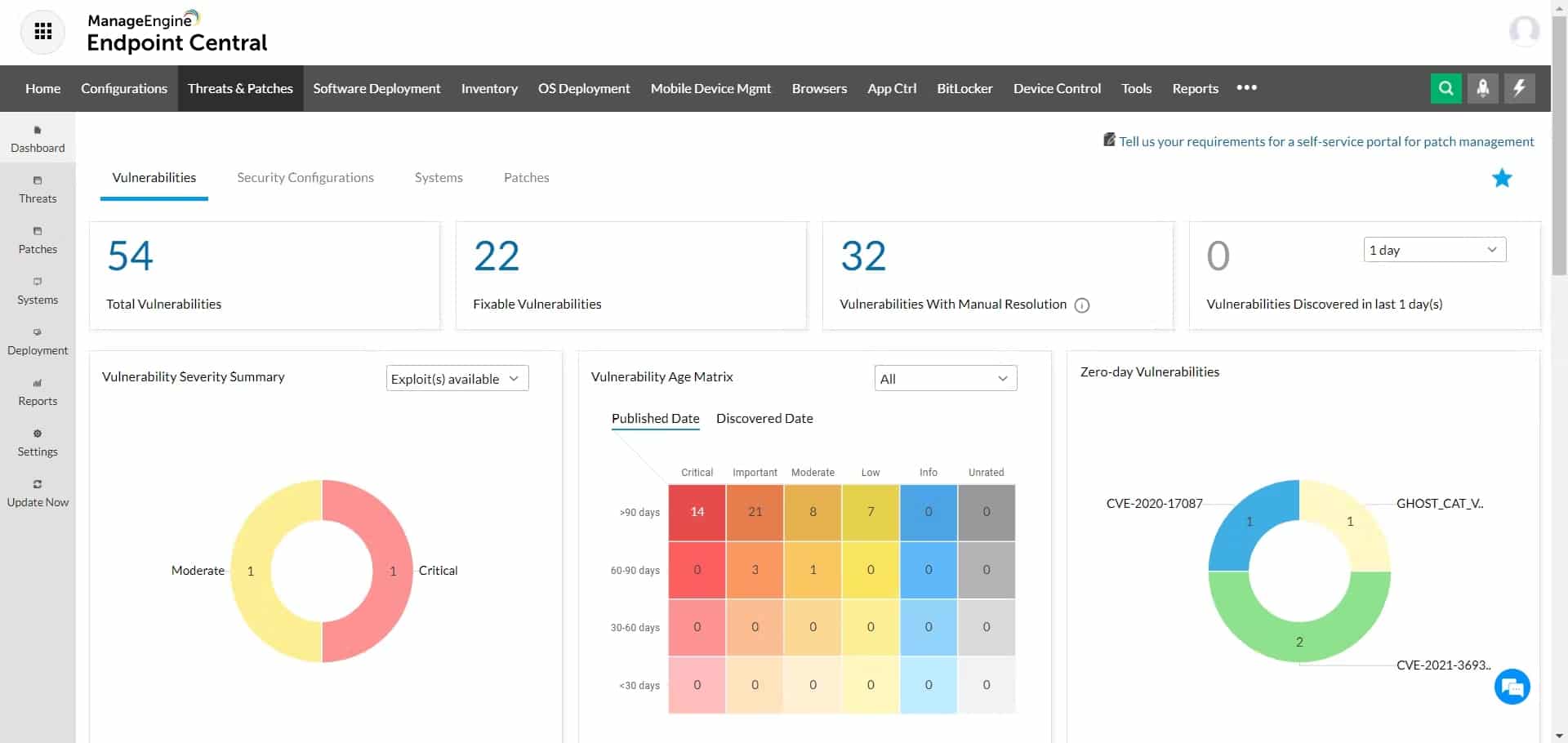
1. ManageEngine Endpoint Central – FREE TRIAL
ManageEngine Endpoint Central is an all-in-one management solution that combines endpoint management and security by offering features such as asset detection, patching and remote control in a unified platform. This allows IT professionals to supervise and administer multiple instances of ManageEngine Endpoint DLP (Data Loss Prevention) from a centralized location, making it an ideal solution for organizations with various branches or managed service providers managing multiple clients.
Key Features:
- Over 25 pre-configured options available for immediate deployment
- Remote asset control with team collaboration tools
- Provides thorough endpoint monitoring and security
Why do we recommend it?
After testing ManageEngine Endpoint Central in a sandbox environment, we were impressed by its extensive asset detection, and patch management features. We found the centralized platform not only easy to navigate but also efficient for managing multiple Endpoint DLP instances.
With Endpoint Central, IT professionals can access and control all their Endpoint DLP instances through a single console, making it more effortless to keep track of their network and devices. It also provides supplementary features such as consolidated reporting and advanced alerting to improve IT professionals’ management efficiency. In short, ManageEngine Endpoint Central empowers organizations to more efficiently prevent the unauthorized transmission of sensitive data from their network.
Who is it recommended for?
This tool is highly recommended for IT professionals and managed service providers who oversee medium to large-scale networks. Its robust reporting and advanced alerting features also make it a good fit for organizations with multiple branches that require centralized control and management.
Pros:
- Ideal choice for administrators who prefer on-premise solutions
- Compatible with both Windows and Linux platforms, making it more versatile than some alternatives
- Offers extensive reporting and inventory management – ideal for managed service providers
- Includes vulnerability scanning and patch management
- Supports mobile device management
Cons:
- Better suited for medium to large-scale networks
Click here to download your ManageEngine Endpoint Central fully functional 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint Central is our top pick for an ESET Endpoint Security alternative due to its comprehensive endpoint management and security features. It offers over 25 pre-configured options for immediate deployment, remote asset control with collaborative tools, and thorough endpoint monitoring and security. We found its centralized platform efficient for managing multiple Endpoint DLP instances, making it a great choice for organizations with various branches or managed service providers.
This tool stood out in our testing, particularly for its asset detection, patch management, and ease of use. ManageEngine Endpoint Central is ideal for IT professionals overseeing medium to large-scale networks, offering extensive reporting, inventory management, and compatibility with both Windows and Linux platforms.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/products/desktop-central/
OS: Windows Server
2. CrowdStrike Falcon
CrowdStrike Falcon is a cloud-based solution that deploys AI techniques and threat intelligence to detect and block attackers. It comprises various modules that operate both in clouds and on-site. Further, it has a console with an agent, the installed software that performs the real job of providing protection and monitoring activities.
Key Features:
- AI-driven threat detection
- Cloud-based architecture
- Modules operate both on-site and in clouds
- Console with agent for real-time protection and monitoring
Why do we recommend it?
We downloaded the free trial of CrowdStrike Falcon and immediately appreciated its AI-driven threat detection capabilities. After putting it through its paces, we can attest that its process scanning and alerting features are effective in identifying and blocking threats.
Falcon is quite similar to the ESET system as it also uses process scanning to discover and identify threats. One can easily track and alert users on noticing anomalous behavior over time.
Who is it recommended for?
CrowdStrike Falcon is best suited for organizations that require high-level endpoint protection without the complexity of managing on-premise hardware. Its cloud-based architecture and scalable pricing plans make it an excellent choice for businesses looking for flexibility and robust security features.
Pros:
- Advanced AI techniques for threat detection
- Flexible and scalable for various business sizes
- Cloud-based, eliminating the need for on-premise hardware
- Effective process scanning and alerting features
Cons:
- May require some technical knowledge for optimal utilization
- Pricing can be higher compared to some other alternatives
The CrowdStrike Falcon platform is available in different pricing plans. Thus, users can choose features as per their requirements and budget.
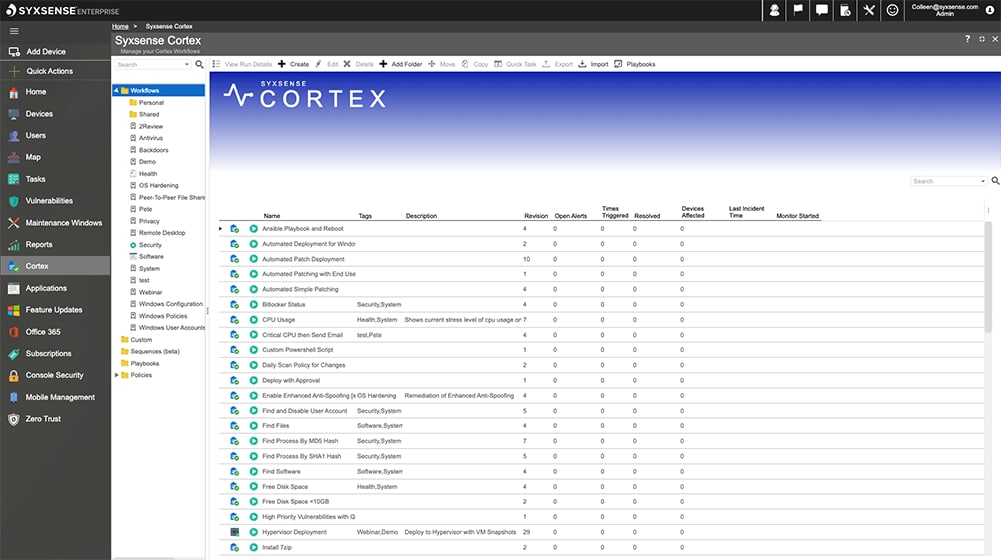
3. Syxsense Secure
Syxsense Secure is another excellent security solution that comprises patch management, endpoint security, and vulnerability scanning features in a single cloud console. It helps prevent your business data and systems from cyber attacks by scanning authorization issues and other aspects. Further, the platform supports all major operating systems, real-time data, and live device monitoring features.
Key Features:
- Patch management
- Endpoint security
- Vulnerability scanning
- Supports all major operating systems
- Real-time data and live device monitoring
Why do we recommend it?
We installed Syxsense Secure and tested its vulnerability scanning and patch management features in a controlled environment. The tool excels in identifying authorization issues and effectively locking down insecure passwords, making it a reliable choice for endpoint security.
Syxsense Secure is easy to set up and has an intuitive dashboard. With the help of this platform, users can lock down insecure passwords and any ineffective user account policy.
Who is it recommended for?
Syxsense Secure is ideal for businesses that need a comprehensive, cloud-based endpoint security solution. It’s particularly well-suited for organizations that operate on multiple operating systems and require real-time data and live device monitoring.
Pros:
- Comprehensive cloud-based security solution
- Effective vulnerability scanning and patch management
- Supports a wide range of operating systems
Cons:
- Could be complex for smaller organizations with limited IT resources
- May not be as cost-effective for smaller networks
4. Symantec End-user Endpoint Security
Symantec End-user Endpoint Security is one of the most integrated platforms that deliver comprehensive cloud-based protection to all mobile devices. Symantec End-user Endpoint Security solution uses AI methods to monitor and track malicious activity and protect your endpoints.
Key Features:
- AI-driven monitoring
- Cloud-based protection for mobile devices
- Active Directory security
- Behavioral isolation and memory scanning
Why do we recommend it?
We downloaded and installed Symantec End-user Endpoint Security to assess its various security layers, including Active Directory security and memory scanning. The tool lived up to its promise, offering effective and comprehensive protection with its AI-driven monitoring capabilities.
It has a single-agent or console architecture with various innovative security layers and features like behavioral isolation, Active Directory security, threat hunting, and memory scanning. Another benefit of Symantec End-user Endpoint Security is it is easy to run on Windows, Mac OS, Windows Server, and Linux. It is highly flexible and checks suspicious events written in log files using the SIEM procedures.
Who is it recommended for?
Symantec End-user Endpoint Security is a suitable choice for businesses looking for a flexible and comprehensive cloud-based endpoint security solution. Its compatibility with multiple operating systems and its integration with SIEM procedures make it a strong candidate for organizations with diverse and complex IT infrastructures.
Pros:
- Advanced AI methods for real-time threat detection
- Suitable for multiple operating systems
- Comprehensive protection with innovative security layers
- Integrates well with SIEM procedures
Cons:
- Might be overwhelming for small businesses with simpler needs
- Pricing can be on the higher side for the full range of features
5. Sophos SafeGuard Encryption
Sophos SafeGuard Encryption is another alternative for ESET endpoint security. It offers a full disk encryption feature, allows users to manage keys and recovery functions, offers real-time threat protection, and more. Any unauthorized or unknown application cannot access the data if you have installed Sophos SafeGuard Encryption for your network.
Key Features:
- Full disk encryption
- Real-time threat protection
- Manages keys and recovery functions
- Compatible with Windows, Mac, iOS, and Android devices
Why do we recommend it?
Sophos SafeGuard offers robust endpoint security with its encryption and real-time protection features, suitable for businesses prioritizing data security across multiple platforms.
It can encrypt entire data across Windows, Mac, iOS, and Android devices. If you are looking for a platform that offers endpoint security with secure collaboration and real-time threat protection features, look no further. Secure all your data without impacting your performance and slowing down your workflow with Sophos SafeGuard Encryption.
Who is it recommended for?
Best for organizations that need to secure sensitive data across a variety of devices and operating systems without compromising on performance.
Pros:
- Strong encryption capabilities across multiple platforms
- Does not impact system performance
- Secure collaboration features
Cons:
- Full disk encryption may not be necessary for all businesses
- Can be more complex to manage compared to basic antivirus solutions
6. Panda Endpoint Protection
Panda Endpoint Protection is a great solution for small to medium-sized networks. It is compatible with various cross platforms, including mobile devices, and checks the statuses of peripherals and directly connected devices.
Key Features:
- Collective Intelligence technology
- Centralized cloud-based management
- Cross-platform compatibility
- Range of services including patching, encryption, and remote monitoring
Why do we recommend it?
We downloaded and installed Panda Endpoint Protection to test its capabilities, specifically focusing on its Collective Intelligence technology. The platform did not disappoint, offering centralized administration and an easy-to-use web console that streamlined threat detection and response.
Panda Endpoint Protection offers a wide range of services, including patching, encryption, remote monitoring, management, and more, to detect and respond to threats. One can manage all tasks conveniently and easily from a single web console without any additional technical knowledge with Panda Endpoint Protection.
Using Panda Security’s Collective Intelligence technology, you can protect all workstations and servers within your network. Furthermore, it provides centralized administration and management from the cloud.
Who is it recommended for?
Panda Endpoint Protection is particularly suited for small to medium-sized businesses looking for comprehensive, cloud-based endpoint protection. Organizations that need to manage tasks centrally without requiring specialized technical knowledge will find this platform especially beneficial. Its cross-platform compatibility also makes it a strong choice for environments with a mix of different operating systems and mobile devices.
Conclusion
If you are managing various endpoints as a business user, an open network with remote and user-owned devices is riskier than a contained office LAN. Even a minor security breach on your endpoints can ruin your business and its goodwill. Hence, endpoint protection is highly necessary.
Endpoint protection is a security solution that acts as a defense system and protects endpoints against zero-day exploits, misappropriation, tampering, and other threats. ESET endpoint security solutions are highly trusted solutions that protect your data and systems from cyberattacks or intrusion attempts and offer instant remediation solutions.
The best part about investing in ESET endpoint security solutions is that it is easy to manage, and can run on Windows, Mac OS, Microsoft Azure servers, iOS, Linux, and VMWare virtualizations. You can easily detect malware pre-execution, during execution, and post-execution with EPP.
ESET Endpoint Security solution offers a wide range of features that make it a top choice. Using ESET’s Brute Force Attack Protection feature, it can help discover and block automated attacks that exercise password-guessing techniques and crack network security. It also supports scanners to detect hijacked applications and protect the network against fileless attacks.
The Host-based Intrusion Prevention System (HIPS) in the ESET Endpoint security solution allows users to use a predefined set of rules to identify, monitor system behavior, and prevent the system from suspicious activities.
Today, most companies invest in EPP because it is trustworthy and comprises excellent features. But, a few look for alternatives as it can be expensive. It currently supports different pricing and plans; ESET Protect Entry, ESET Protect Advanced, ESET Protect Complete, and more.
ManageEngine Endpoint Central, CrowdStrike Falcon, Syxsense Secure, Symantec End-user Endpoint Security, Sophos SafeGuard Encryption, and Panda Endpoint Protection are a few alternate options you can invest in. These are perfect solutions if you do not require so many features or have a smaller budget.
Go through the features and benefits of the ESET Endpoint Security solution and compare all the above-listed alternatives to make a final call.