Today, many organizations are adopting cloud computing and storage services to minimize costs and enhance their agility. With the introduction of more and more applications to the cloud, the risk of data breaches or exposing systems has become high. Furthermore, maintaining security across environments has become more complex as organizations deploy services in various public clouds.
With this rapid adoption of cloud services, security teams find it hard to keep pace. As per the Gartner research report (2021), 50% of cloud security issues were the result of customer misconfiguration and mismanagement.
A single misconfiguration in the cloud can expose all your sensitive data to the public internet. Thus, it is essential to look into the factors responsible for misconfigurations and mistakes.
Generally, misconfigurations can occur:
- If the cloud is inherently programmable or driven by cloud applications and APIs.
- When a “sprawl” of new services and technologies is adapted for use.
- If cloud features new technologies different from the ones available in physical data center environments.
- The size and complexity of enterprise environments with thousands of resources can lead developers to create the wrong resource or lose track of cloud assets.
There are various risks and challenges associated with cloud environments. Thus, various organizations are adapting a CSPM strategy. Let us discuss CSPM, how it works, and its associated benefits in detail.
What is Cloud Security Posture Management (CSPM)?
CSPM stands for Cloud Security Posture Management, an IT security tool that offers real-time visibility, aids in monitoring existing resources, enables team members to discover misconfiguration issues and compliance risks in the cloud.
The term CSPM was coined by an IT research and advisory firm – Gartner in a 2019 innovation paper. The main purpose of designing CSPM programming was to reduce the attacks occurring within a cloud environment. Also, it enables continuous monitoring of the cloud infrastructure and helps discover gaps in security policy enforcement.
A modern CPSM tool has various advantages such as automating security, offering compliance assurance in the cloud, and remediating risks across different platforms, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (Saas). The CSPM tool performs analyses over data sources and compares the cloud environment against defined best practices. In most cases, the Cloud Security Posture Management alerts when there is a requirement for remediating a security risk. While, in some cases, it automatically remediates issues using Robotic Process Automation (RPA).
Generally, organizations use the CSPM strategy for DevOps integration, compliance monitoring, incident response, visualizing and assessing associated risks, or extending security best practices to hybrid cloud, multi-cloud, and container environments.
At present, it is one of the key components of cloud data security that aid organizations to address all cloud security risks and misconfigurations in the public cloud services.
Key Features of Cloud Security Posture Management (CSPM)
- Automates Identification of all cloud security risks
- Automates remediating risks across cloud infrastructures and address misconfigurations
- Creates an inventory of best practices for various cloud configurations and services
- Report and map out configuration statuses as per the regulatory standard or security control framework
- Performs analysis over data resources across IaaS, SaaS, and PaaS platforms in different environments
- Monitors storage buckets
- Enables encryption and account permissions for misconfigurations
- Offers centralized and real-time visibility across different cloud environments
- Evaluates and displays robust security posture at one location without any deep expertise
- Allows better insights into potential compliance risks
- Creation of quick audit-ready reports
- Enable protection against malware and other threats
Who is Responsible For CSPM?
In 2020 a cloud security survey was conducted, according to which around 76% of people believed that cloud security was a complete responsibility of the Cloud Service Provider (CSP). However, AWS and Azure had different thinking processes.
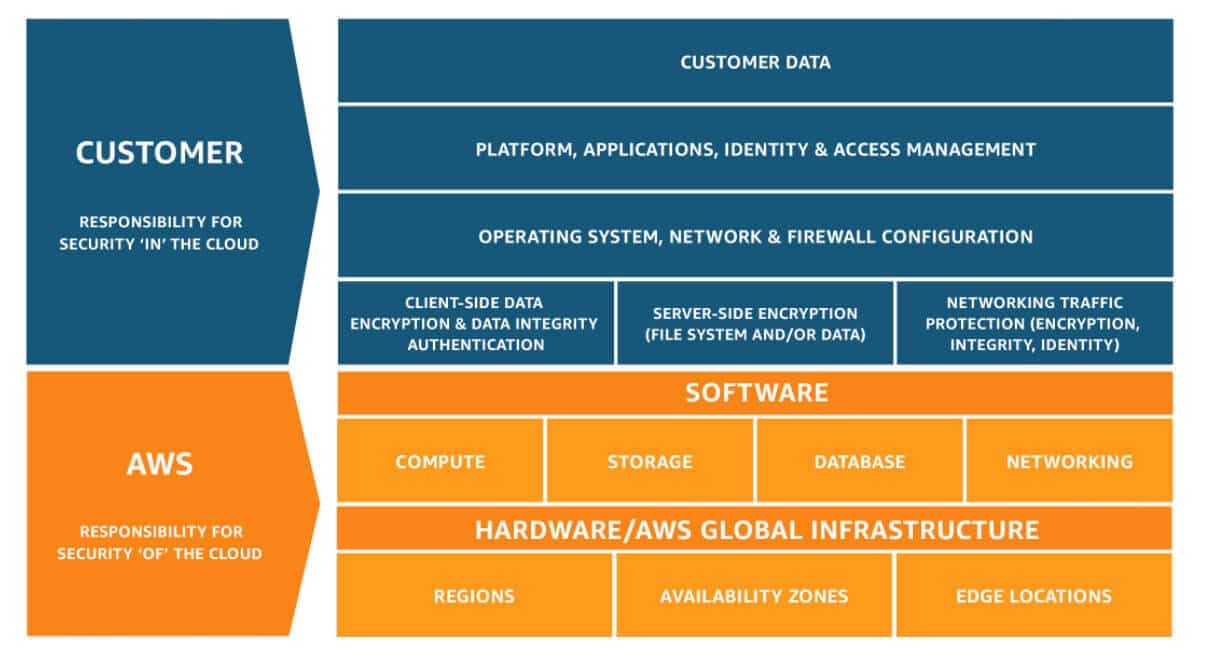
As per the AWS’ responsibility model, both AWS and customers are responsible for cloud security. AWS protects the infrastructure, including hardware, software, networking, and other services that run in the AWS Cloud services. However, customers must take responsibility for security in the cloud.
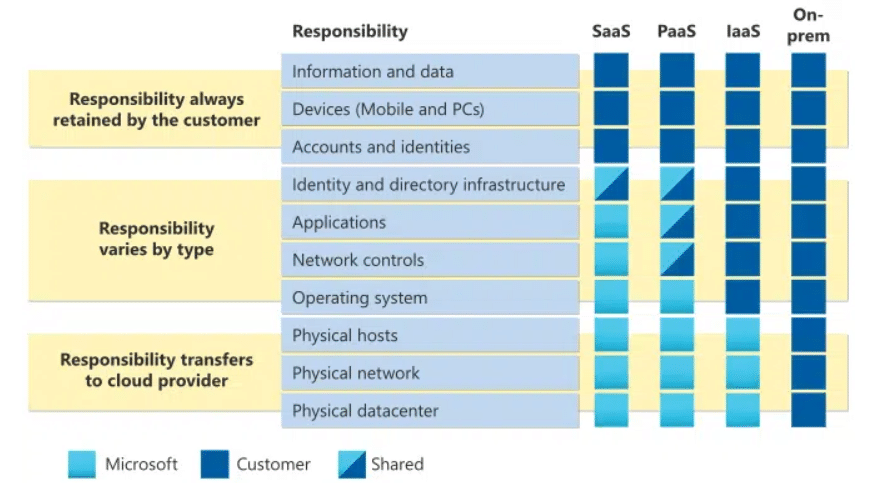
Azure’s responsibility model also has the same belief.
It states that the customer must check the security of data, accounts, endpoints, and access management. The more you shift from IaaS, PaaS, or SaaS platforms, the more responsibility will transfer to Microsoft.
Why do Organizations need CSPM?
With the advancement in technology, many businesses have shifted to cloud-based applications and services to increase productivity and flexibility. However, it has also enabled the greater risk of cybersecurity threats simultaneously. Despite proper training and the use of best practices, security issues have been at risk. Also, vulnerabilities remain, and chances of risking sensitive data are visible.
However, IT experts constantly work to address any data breach occurring due to cloud infrastructure misconfiguration, continuous compliance for cloud apps, and other challenges responsible for cloud governance, yet have not achieved 100% success.
Thus, to maintain security and increase productivity at the same time, businesses are looking forward to adopting the CSPM strategy. CSPM tools aid organizations in minimizing the possibility of data breaches and cloud-based security incidents faced due to misconfigurations. They help IT experts in identifying and remediating risks through constant security assessments and compliance monitoring.
There are many benefits of using CSPM tools apart from automatic monitoring and checking of misconfigurations responsible for data breaches and leaks.
Here are some of the additional benefits of Cloud Security Posture Management tools in the enterprise:
- Better Visibility Getting access to all the resources, real-time security and compliance posture, applications, and distributed data over multiple environments is quite challenging. However, with the help of CSPM, the admins can monitor and track all the listed information. The powerful tools offer real-time visibility and enable organizations to analyze different data resources gathered from various environments. It also helps generate a detailed asset inventory. Furthermore, the Cloud Security Posture Management tools enable organizations to track all existing resources, evaluate the data, and display security posture at a centralized place. It is best to monitor different aspects from one location rather than switching to different sources to gain accurate data. CSPM helps security teams to get visibility into several clouds in one place and save time.
- Proper Governance Every organization has a set of data security policies, but most employees find it difficult to implement or enforce them in the cloud as they lack security expertise. As a result, the Security Operations Center (SOC) teams receive thousands of alerts constantly from multiple tools and clouds. CSPM tools in such cases help build a robust security posture across different environments. As these cloud security postures are properly defined, the tool aids organizations to enforce them across multiple clouds. With the help of these tools, organizations can faster discover security violations and automate remediation of risks across various cloud infrastructures.
- Threat Detection Misconfiguration is a common threat to cloud data security. But, apart from this, organizations face both malicious insider threats and external threats, including crypto mining, ransomware, hacking, etc. Threats with stolen credentials are generally not visible until a breach takes place. To discover the attacker, SOC teams manually go through each log. Thus, to save time, most organizations use cloud security tools that help protect their data against threats and offer better visibility. Cloud Security Posture Management is a popular tool that collects information from different clouds and shares it with SOC teams. It helps them view threat intelligence data from different clouds in one place. These tools also support their threat intelligence sources, which helps organizations prioritize threats with a high-risk rate.
How does CSPM work?
The reason behind designing and launching the tool in the market was to discover and remediate issues that occur due to cloud misconfigurations. Misconfigurations can occur at any stage during the initial setup or any time later during the cloud deployments. Even the most experienced application developers miss out on a setting and make mistakes in the cloud. Unsecured internet connectivity paths, open access to unencrypted storage buckets, etc., are a few common cloud misconfigurations.
Cloud security posture management provides real-time security to risky activities and compliance posture. There are specific CSPM tools that use only defined best practices as per the cloud environment. For instance, some have limited access to identify misconfigurations in an AWS or Azure environment. While some can automatically remediate issues using the real-time monitoring features. They can even configure compliance, detect and fix improper account permissions.
The popular tool adds more visibility to cloud infrastructure assets and security configurations. Furthermore, users can discover data from multi-cloud environments and accounts in one place. Cloud security posture management provides all information related to misconfigurations, networking, change activity, and security automatically to the users upon deployment.
It has a single console to manage all security group policies across different accounts and virtual networks. Further, the tool helps eliminate threats and security risks by identifying issues and remediating them in real-time. CSPM tools have benefitted organizations in many ways. It provides continuous threat protection, monitors all unauthorized activities, and prioritizes vulnerabilities based on the environment.
CSPM further reduces overhead and allows users to capture insights related to misconfigurations and policy violations. For faster remediation, users can also integrate the CSPM tool with other DevOps tools.
CSPM vendors
Earlier, users could only detect and visualize IaaS and PaaS asset inventory. But now, Cloud Security Posture Management vendors can easily detect, alert, and remediate cloud misconfigurations. CrowdStrike Falcon Horizon CSPM, Zscaler CSPM, Trend Micro Cloud Conformity, Orca Security are a few CSPM vendors.
Zscaler CSPM – The tool works great with Google Cloud Platform, SaaS, IaaS, PaaS platform, AWS, and Azure environment. It allows users to detect and remediate misconfigurations in the cloud automatically. The company Zscaler added CSPM to its platform in the year 2020.
Orca Security – Another startup company added the CSPM tool to the platform for more visibility and better analysis. It works best on AWS, Azure, and Google Cloud services. Apart from CSPM features, it also includes cloud workload protection platform (CWPP) capabilities.
Trend Micro acquired Cloud Conformity – It is a CSPM tool that works with only AWS and Azure Cloud environments. It allows users to maintain security, proper governance, and compliance in the clouds.
Things to Consider when selecting a CSPM tool:
- Offer real-time and regular visualization of cloud infrastructure
- Multi-cloud asset discovery and risk assessment
- Threat protection
- Defends against all common misconfiguration, such as incorrect permissions, disabled logging, expired keys, etc.
- Offers compliance with security frameworks, including HIPAA, SOC 2, GDPR, etc.
- Enforces DevOps and DevSecOps policies
Conclusion
With the advancement in cloud computing and storage services, there has come a need for tools that provide real-time visibility and monitor all existing resources.
Cloud Security Posture Management is one such tool that allows quick detection of misconfiguration issues and compliance risks in the cloud. Further, it enables users to perform analysis over data resources across IaaS, SaaS, and PaaS platforms in different environments.
Today, most companies are adopting CSPM tools as it has various benefits. Also, they help minimize the possibility of data breaches. Further, it helps generate insights, reports, and map out configuration statuses as per the regulatory standard or security control framework.
Users can easily monitor all cloud-based security incidents faced due to misconfigurations. It has a single console to manage all security group policies. In the 2019 innovation paper, the term CSPM was coined by an IT research and advisory firm – Gartner. Since then, till now, most companies have adopted CSPM strategy to maintain security and increase productivity at the same time.
Most people believe providing cloud security is the complete responsibility of the Cloud Service providers. However, it is not true. Both cloud service providers and customers are responsible for cloud security.
Zscaler CSPM, Trend Micro Cloud Conformity, Orca Security are a few CSPM vendors that work great with Google Cloud Platform, SaaS, IaaS, PaaS platform, AWS, and Azure environment. Look for CSPM tools that suit your business requirement and budget.