An unsecured network can cause a lot of damage to your business and increase the chances of data breaches. Thus, looking after your network security must be the primary responsibility of the administrators in a corporate IT environment. Each business must invest in tools or look for processes that will help in fixing vulnerabilities.
With the rise in cyberattacks and threats, investing in a continuous security solution is worth the cost. A data breach can expose all your personal or sensitive information without authorization. Also, it can lead to unhappy customers and is highly advantageous for your competitors. Instead of bearing so much loss, it is best to go for Vulnerability Management Software that can save you from losing sensitive data.
Here is our list of the best Vulnerability Management tools:
- NinjaOne Vulnerability Manager – EDITOR’S CHOICE This scanner provides automated patching as part of a cloud platform of remote monitoring and management services. Available for a 14-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL This package provides a vulnerability scanner and a linked patch manager that automatically fixes discovered problems with out-of-date operating systems and software. Available for Windows Server. Get a 30-day free trial.
- ManageEngine Network Configuration Manager – FREE TRIAL A network configuration and change management tool. It’s designed to help IT teams manage routers, switches, firewalls, and other devices across multi-vendor networks. Available for a 30-day free trial.
- Invicti This package can be used as a vulnerability scanner for live systems or a continuous tester for Web applications under development. Available as a SaaS package or for installation on Windows Server.
- Acunetix This system provides Web application security testing and also vulnerability scanning for operating Web applications and mobile apps. Available for Windows, macOS, and Linux.
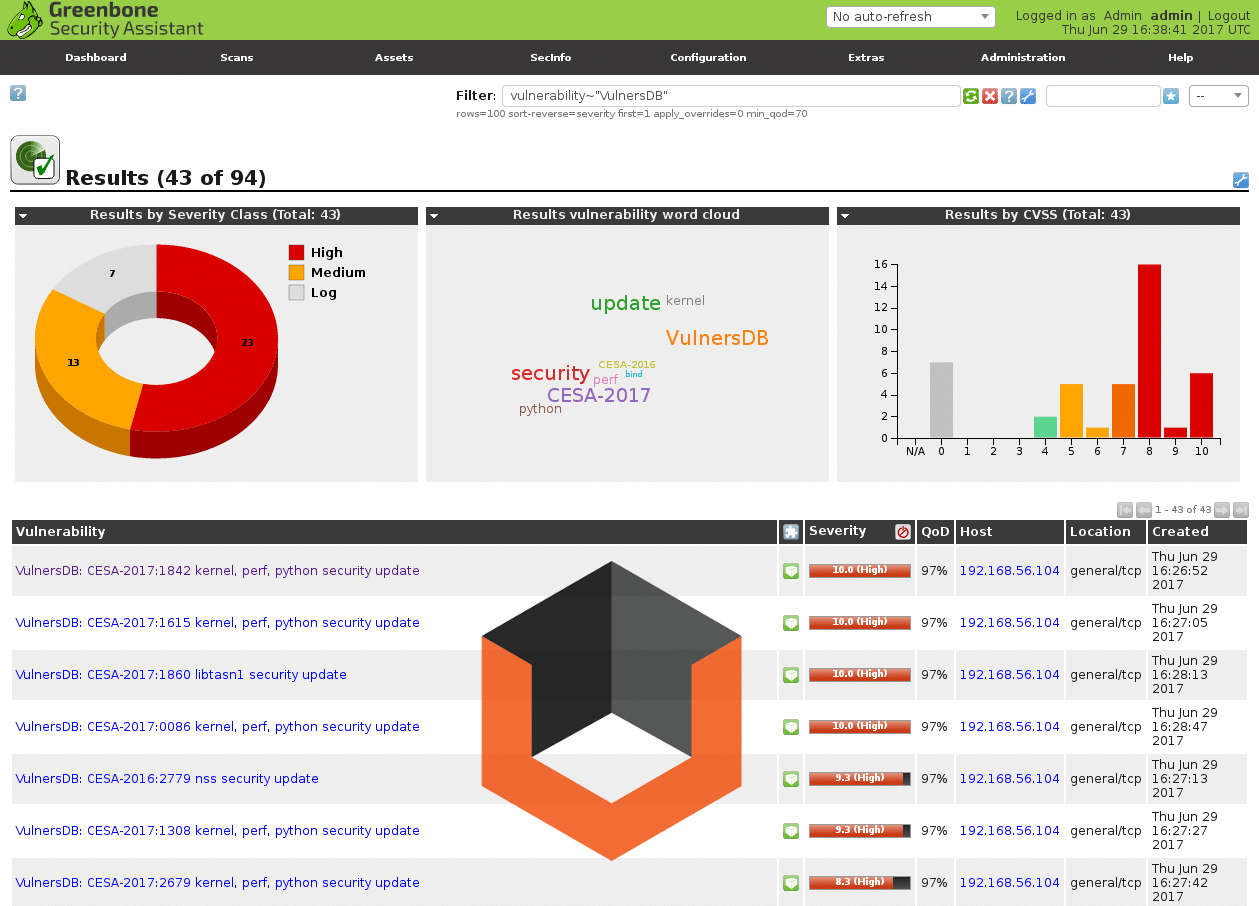
- OpenVAS This popular free vulnerability scanner can also be used for penetration testing. Runs on Linux or on Windows over a VM.
- Tenable This package is a stablemate of the Nessus vulnerability scanner and performs very similar functions for on-premises and cloud systems. This is a cloud platform.
- Qualys This cloud platform provides asset management with autodiscovery as well as vulnerability management.
In this post, we will discuss a few Vulnerability Management Tools, how they work, and their key features.
What is Vulnerability Management Software?
You might have come across many tools like antivirus software and firewalls that help save your systems from attacks. But, vulnerability management software is a bit different and follows a different approach to cybersecurity.
Vulnerability management is a cybersecurity process that helps identify, evaluate, treat, and report security vulnerabilities found in a system or software.
It performs proper scanning and looks for weaknesses and vulnerabilities in the network. Further, it guides the operators by offering remediation suggestions to reduce the chances of data breaches. By adopting this technique, you can stay ahead of your competitors and prioritize possible threats.
Another advantage of investing in vulnerability management tools is that you can assign and monitor the threat levels to weaknesses. This feature may help you address the most significant issues at first. As such, you can prioritize the threats as per your need.
Also, in some cases, these tools automate all the processes and provide solutions automatically via patches and other features.
How Do Vulnerability Management Tools Work?
Vulnerability Management tools follow different approaches to identify and fix vulnerabilities in a system:
- Vulnerability scanners The approach makes the process to find vulnerabilities, security holes, and patches easier by scanning all endpoints. It accesses all the possible vulnerabilities in the internal and external networks that attackers can exploit.
- Penetration testing This approach involves an actual attack similar to what hackers would do in most cases. It involves thinking like the hackers and targeting the areas from the hacker’s point of view to see how and which defense areas can be breached.
- Breach and attack simulation (BAS) Αn advanced testing method that identifies vulnerabilities and weaknesses by acting like attackers. The BAS tools also enable the operators to prioritize fixes.
- Vulnerability assessments Αnalyze and evaluate if there is any known vulnerability and prioritizes solutions. It looks for an organization’s overall security posture and reviews weaknesses.
- Patch management Corrects the errors and fixes vulnerabilities as prioritized by the vulnerability management tools.
Vulnerability management tools adopt some of the above-listed approaches to prioritize threats and offer remediation. A few products also automate these functions to reduce the burden on security staff.
Key Features of Vulnerability Management Tools
Here are a few advanced features that most of the vulnerability management tools comprise that help fulfill all your company’s security needs and requirements. To determine which specific cybersecurity solution is best for your organization, consider the one that comprises most of these features:
- Scan and monitor potential vulnerabilities and bugs continuously
- Profile and rule system monitoring
- Set up Notification rules
- Display vulnerability severity levels in the dashboard and reports
- Risk scoring
- Alert options
- Advanced Authentication Functionality
- Policy assessment
- Centralized management of agents and vulnerability scanners
- Network access path analysis
- Supports scanning of network perimeter and internal network
- Attack surface visualization
- Patch management
- Customizable reporting
- Automated updates and remediation
- Attack vector analytics and modeling
A few vulnerability management tools also offer asset discovery features. To test if a vulnerability management tool matches your requirement, lookup for the above-listed features and compare the tools before making the final call.
The Best Vulnerability Management Tools
Methodology for Selecting the Best Vulnerability Management Tools
An unsecure network can increase the risk of data breaches and damage your goodwill. But, with the help of vulnerability management tools, users can quickly track system weaknesses and remediate vulnerabilities in real time. There are several benefits to using vulnerability management tools, but make sure you choose the right tool for your organization.
Here, we have listed a few methodologies that will help you select the best vulnerability management tool in the market.
- Check if the tool offers vulnerability scanners that can run as and when you demand or scheduled as per your choice.
- Check if your tool has the ability to connect scan results to corrective action
- Check if it can keep an eye on ongoing bugs and potential vulnerabilities on a constant basis
- Check if the tool generates updates and remediations automatically
- Check if it can be easily managed by both technical and non-technical users
- Check if it is versatile and can operate on different operating systems.
- Is your tool capable of generating detailed reports for various compliance standards?
- Can you test the system for free or perform free trials?
Vulnerability management tools reduce data breaches and offer a way to identify and fix vulnerabilities before the damage. We have shortlisted some of the best vulnerability management tools that will help spot incipient attacks before they occur and provide data protection at all times. Have a look!
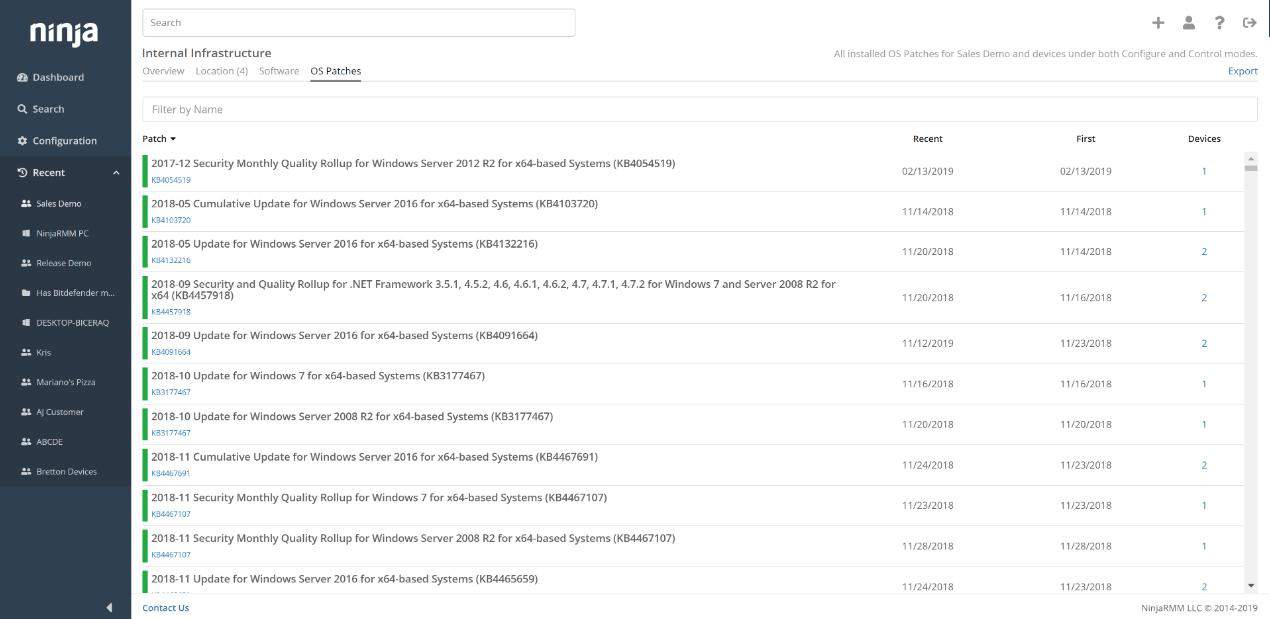
1. NinjaOne Vulnerability Manager – FREE TRIAL
The NinjaOne Vulnerability Manager is a component of an RMM package that is delivered as a SaaS platform. NinjaOne implements a discovery routine that logs all devices on a network and then scans each endpoint for its software. This creates a software inventory and provides license management. Drawing from industry benchmarks, NinjaOne’s standing is reinforced by its long streak of recognitions with G2.
Key Features:
- Device asset inventory
- Software management
- Configuration policy management
- Automated patch manager
Why do we recommend it?
We recommend NinjaOne Vulnerability Manager for its comprehensive approach to vulnerability management, particularly its automated patch manager. This feature ensures that all software and operating systems are up-to-date, enhancing the overall security posture of a network.
The main vulnerability management feature of NinjaOne is its automated patch manager. It works through the list of operating systems and software packages installed on a site and then keeps checking with software providers for updates.
When patches become available, the NinjaOne platform copies over the installers and schedules them. You define maintenance days and times in the interface and all patches will be held in a list until the next available maintenance period arises.
The tool will apply the patch to all relevant endpoints. The system works best when scheduled to run out of office hours so that the endpoints won’t be in use. The tool is able to start up endpoints for patch installation and can also reboot where necessary and turn off each computer at the end of the process.
Who is it recommended for?
NinjaOne is suitable for businesses that prioritize automation and full-stack monitoring in their vulnerability management. Its SaaS platform is convenient for remote or distributed teams, and its flexibility in scheduling makes it ideal for organizations that require off-hours patching.
Pros:
- Task automation
- Full stack monitoring
- Provides configuration standardization
Cons:
- You need to register for a quote – no published price list
This package is suitable for use by managed service providers and also for IT departments. It is able to manage a fleet of endpoints and the networks that connect them. You can get a custom quote according to your network’s needs. You can assess the package with a 14-day free trial.
EDITOR'S CHOICE
NinjaOne is the editor’s choice for the best vulnerability management tool, as it comes with extensive features to identify different security loopholes. A highlight of this tool is its automated patching, which scans all the endpoints in your network to identify unpatched applications. It also downloads the required patches, tests them in a sandbox to ensure that nothing breaks the system, and, based on your policies, deploys them to the endpoints. Since all this happens automatically, it saves time and effort for your team, while keeping you secure and compliant. Also, this tool helps with configuration management, automatic discovery of new devices in your network, and more. All this data is presented in intuitive dashboards, making it easy to stay on top of vulnerabilities. With such features, NinjaOne is the best tool on our list.
Download: Get a 14-day FREE trial
Official Site: https://www.ninjaone.com/vulnerability-management/
OS: Cloud based
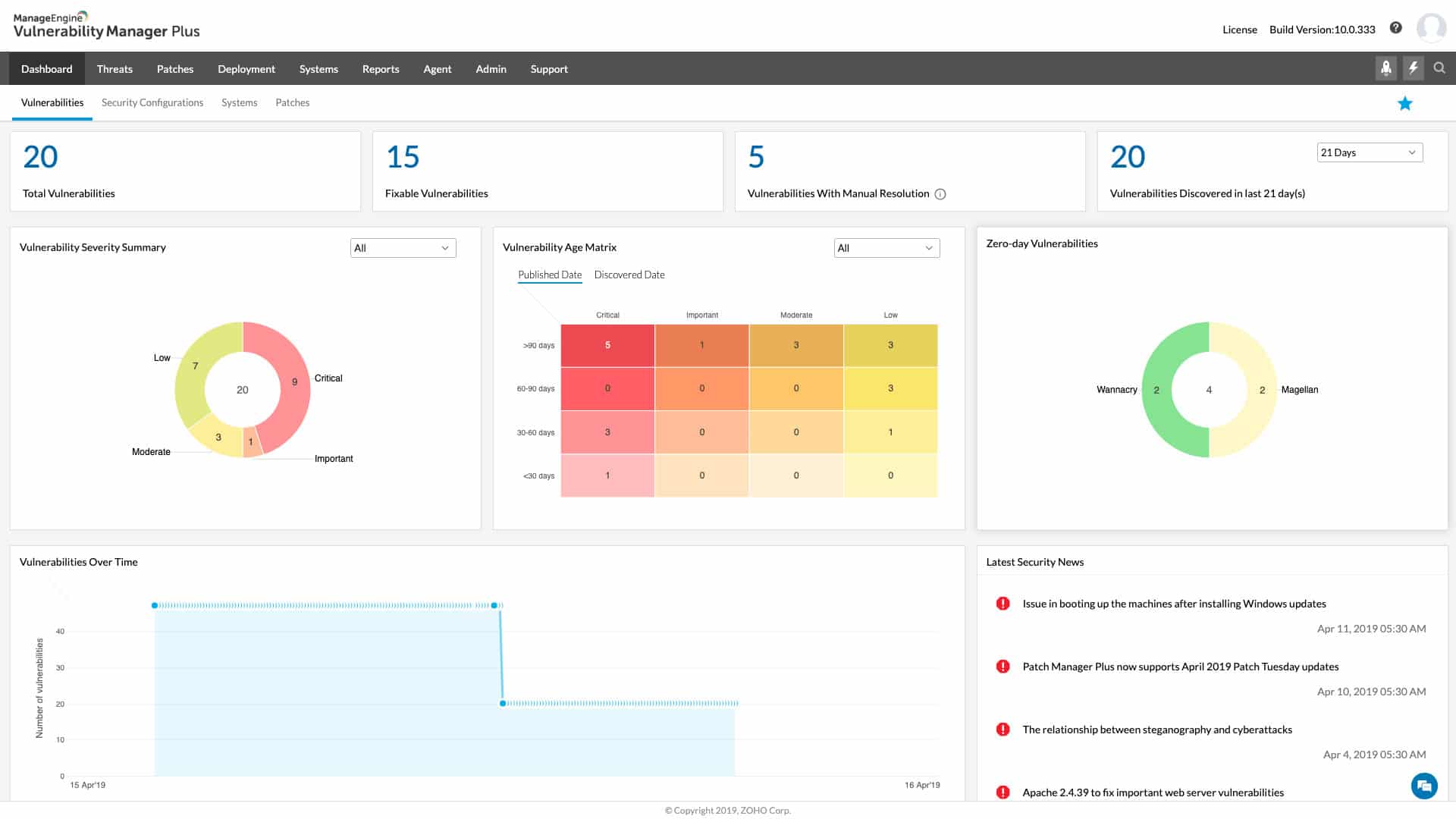
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus (VMP) is a vulnerability remediation software solution that assists businesses and organizations in identifying and patching security issues in their networks and systems. The platform offers various tools for identifying vulnerabilities, evaluating their risks, and formulating plans to remediate them.
Key Features:
- Automated vulnerability scans
- Indepth reporting for various compliance standards
- A mix of manual and automated remediation tools
Why do we recommend it?
We recommend ManageEngine Vulnerability Manager Plus for its robust capabilities in identifying and patching security vulnerabilities. Its strong reporting features, coupled with a regularly updated threat intelligence database, make it an invaluable asset for enhancing network and system security.
For instance, a company could utilize Vulnerability Manager Plus to scan its network for vulnerabilities on a regular basis. If the scan detects any vulnerabilities, VMP can produce a report or alert and prioritize them based on the level of risk they pose. The company can then develop a plan to fix the vulnerabilities, enhancing the overall security of its network and systems.
Who is it recommended for?
ManageEngine Vulnerability Manager Plus is recommended for businesses and organizations of all sizes, particularly those that require ongoing vulnerability scans and patch management. Its compatibility with Windows, Linux, and Mac, as well as a free version ideal for small businesses, makes it versatile for a variety of use cases.
Pros:
- Strong reporting capabilities can demonstrate progress after remediation
- Versatile – can operate on Windows, Linux, and Mac
- The threat intelligence database is regularly updated with the latest threats and vulnerabilities
- Offers a free version, ideal for small businesses
- Excellent for ongoing scanning and patching throughout the lifespan of any device
Cons:
- The ManageEngine ecosystem can take time to fully understand and explore
Click here to download your ManageEngine Vulnerability Manager Plus 30-day free trial.
3. ManageEngine Network Configuration Manager – FREE TRIAL
ManageEngine Network Configuration Manager (NCM) is a multi-vendor network change and configuration management solution. It is built for IT teams that need more than basic vulnerability detection. It works across multiple vendors and helps standardize compliance, cut downtime, and keep operations running smoothly. Unlike traditional vulnerability management tools that only flag problems, NCM goes further. It combines proactive configuration control with automation.
Key Features:
- Manual, real-time, and scheduled backups
- Automates repetitive CLI/REST tasks
- Secure delegation through role-based access controls
- Manage multi-location devices from a central console
- Real-time compliance and vulnerability alerts/reports
Why do we recommend it?
We recommend ManageEngine Network Configuration Manager (NCM) because it hits the perfect balance between cost and reliability. The automated backups and versioning impressed us. While testing them, we noticed it immediately showed device changes—restores were also quick, and rollback worked exactly as promised.
We also love this tool for its unique feature, NCM’s Configlets. This is useful whenever you are stuck scripting or fixing misconfigurations. It is a real time-saver. Bulk SNMP setups and firmware upgrades also took minutes (not hours). Something we strongly believe is possible even across multi-vendor environments.
The dashboard has a mild learning curve, but once set up, reporting and compliance really shine. Policies flagged non-compliant configs right away. Plus, the audit-ready reports were exported cleanly. While testing it, even the small misconfigs surfaced clearly—things you’d normally miss in manual reviews.
Who is it recommended for?
This tool fits mid-sized IT teams managing 50 to 1,000 devices across different vendors. It’s also especially useful for regulated sectors like banking and healthcare, where compliance audits are critical. If you’re already using ManageEngine products, the built-in ecosystem integration makes it even more valuable.
Pros:
- Automated backups & easy rollback
- Cost-effective licensing compared to SolarWinds
- Strong compliance enforcement & reporting
- Vendor-agnostic with wide device support
- Mobile app for remote management
Cons:
- UI and dashboards feel dated
Click here to download your ManageEngine Network Configuration Manager 30-day free trial.
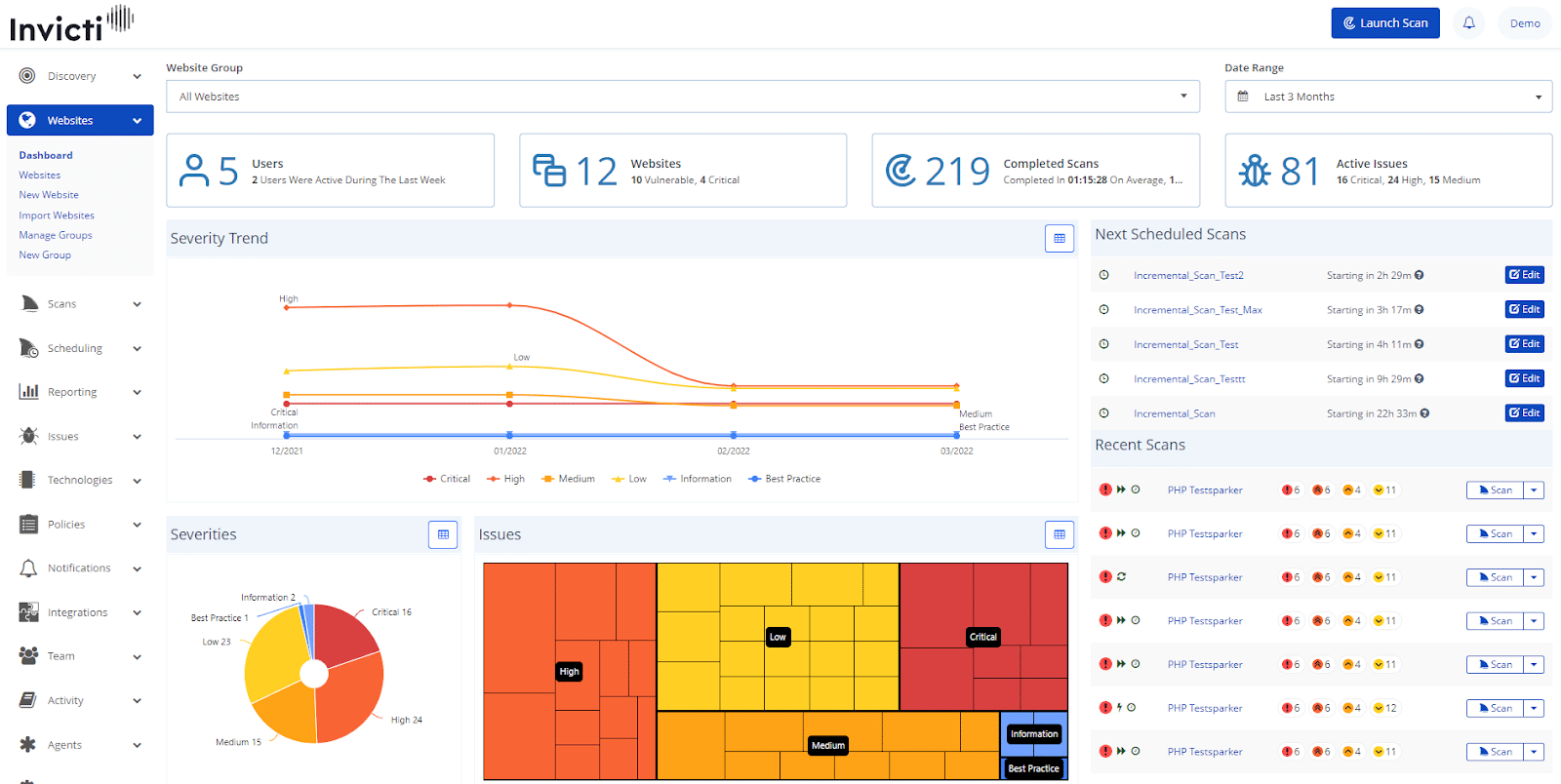
4. Invicti
One of the popular vulnerability management tools that offer security advice at all stages of the CI/CD pipeline and help reduce the risk of attacks. Invicti is best suitable for DevOps and is used in every stage of building Web applications. The tool plays a key role in building the application, pushing it through the new development phase, and checking on live systems.
Why do we recommend it?
Invicti stands out for its extensive integration with the CI/CD pipeline and its automated security features throughout the Software Development Life Cycle (SDLC). Its capabilities in Dynamic and Interactive Application Security Testing, along with real-time monitoring and risk management, make it a comprehensive solution for vulnerability management.
Available as a cloud platform, the main purpose of designing Invicti was to support the CI/CD pipeline. It uses its approach to discover possible pitfalls and security glitches.
Another feature of Invicti is that it provides automated security throughout your SDLC and saves time. By investing in Invicti, you can easily discover and prioritize vulnerabilities. Also, seamlessly assign the prioritized vulnerabilities for remediation.
Who is it recommended for?
Invicti is particularly suited for DevOps teams and organizations that have a strong focus on continuous integration and continuous delivery. It is also ideal for businesses that require a scalable vulnerability management solution capable of handling multiple integrations and providing full visibility into applications.
Pros:
- Supports the CI/CD pipeline
- Supports Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) scanning approach
- Scans for security glitches and pitfalls in the codes under development
- Automates security throughout SDLC and saves time
- Offers full visibility into apps
- Helps in discovering lost web assets
- Provides real-time monitoring and risk management
- Supports 50+ integrations
- Supports combined signature and behavior-based testing for discovering vulnerabilities
- Allows controlling permissions for unlimited users
- The tool helps developers to write more secure code to prevent vulnerabilities
Cons:
- Invicti does not support patch manager
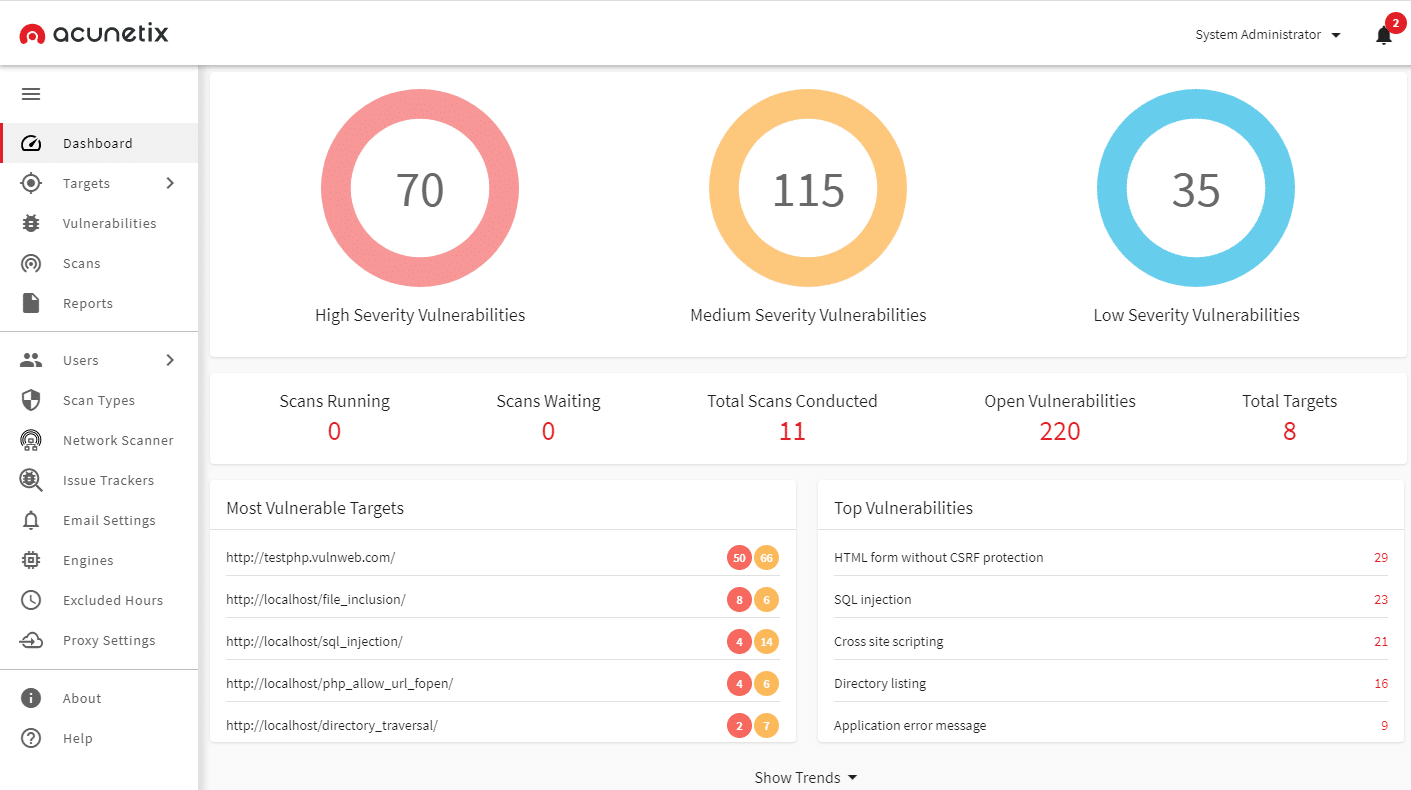
5. Acunetix
Acunetix is a web application scanner that discovers and fixes the vulnerabilities responsible for putting your applications at risk of attacks. It provides Dynamic Application Security Testing (DAST) and Interactive Application Security Testing (IAST) scanning and can detect multiple vulnerabilities in minutes.
Why do we recommend it?
Acunetix offers a robust set of features including DAST and IAST scanning capabilities, along with the ability to automatically eliminate false positives. Its compatibility with multiple coding frameworks and platforms, as well as its focus on intelligent automation, makes it one of the most comprehensive tools for web application security.
You can also prioritize your high-risk vulnerabilities and schedule scans with the help of this tool. Also, it enables operators to pinpoint vulnerable locations and fix them. Another advantage of Acunetix is that IT professionals have to no longer manually confirm the real vulnerabilities. Instead, the tool prioritizes and automatically eliminates false positives.
It also offers all the solutions and information to the developers necessary to resolve the security flaws. Acunetix Deep Scan crawler, Acunetix Out-of-Band Vulnerability Tester, and AcuSensor are a few additional services included in the Acunetix bundle.
Who is it recommended for?
Acunetix is ideal for IT professionals and development teams that require a versatile and powerful web application scanner. It is especially suitable for organizations using CI/CD pipelines, and those looking to conduct thorough security audits on complex and authenticated web applications.
Pros:
- Allows scanning 7,000+ Web vulnerabilities
- Supports a Web application discovery module to chain all services
- Scans code written in JavaScript, .NET framework, and PHP
- It provides scanning of the internal network and internet-accessed Web applications
- It is designed for the CI/CD pipeline
- Supports static, dynamic, and interactive application testing features
- The tool is compatible with HTML5, JavaScript, and Single-page applications
- Audits all complex and authenticated applications
- Detects out-of-band vulnerabilities automatically
- Supports integrated vulnerability management features
- Compatible with Windows and Linux platforms
- Acunetix offers fast scanning, quick reports, and intelligent automation
Cons:
- It does not support patch manager or configuration manager
6. OpenVAS
OpenVAS stands for Open Vulnerability Assessment System, an open-source project that does not support advanced features. Yet, it is a great choice if you are looking for vulnerability management tools. It is a free tool that helps detect vulnerabilities.
Why do we recommend it?
OpenVAS offers an extensive range of features, including a web-based GUI and daily security status updates, all while being a free and open-source tool. Its focus on community support and frequent scan engine updates make it a reliable choice for vulnerability management.
It is a full-featured vulnerability scanner with a GUI interface that analyzes IT networks for vulnerabilities and offers daily security status updates. It also enables the operators to set priorities and remediate solutions.
The active community of OpenVAS can be easily contacted using a community message board. In addition, the tool provides a live security feed, and its database comprises network vulnerability tests (NVTs).
Who is it recommended for?
OpenVAS is particularly recommended for small to medium-sized enterprises looking for a cost-effective vulnerability assessment solution. With its open-source nature and active community support, it’s also a good choice for organizations willing to contribute to or customize their vulnerability management tool.
Pros:
- A free, open-source vulnerability assessment tool
- Around 26000 Common vulnerabilities and exposure (CVE) coverage
- Best suitable for small and medium-sized enterprises
- An all-in-one scanner
- Frequently updates scan engine
- All test routines are available with source code
- Performs regular audits and scans
- Offers automatic setup and future upgrades
- It has a web-based Graphical User Interface (GUI)
- Provides product documentation for tool usage
- It has an activity community and forum support
- Supports performance tuning for large-scale scans
Cons:
- No policy management
- Fewer CVEs are covered
- The learning curve can at times be frustrating for the enterprises
7. Tenable
Tenable’s Cyber Exposure Platform is trusted by a large number of enterprises worldwide for its excellent results and features. It follows a risk-based approach to discover, identify, and resolve weaknesses found across the websites and applications. Tenable offers full visibility into your system’s entire infrastructure.
Why do we recommend it?
Tenable’s Cyber Exposure Platform stands out for its comprehensive risk-based approach and advanced features like threat intelligence, which help in prioritizing vulnerabilities. Its ability to offer full visibility into a system’s infrastructure, coupled with its scalability and advanced automation features, make it a top choice in the vulnerability management category.
The tool also enables the organization to find even the rarest variants without any failure. Using threat intelligence, the operators can predict the severity of the vulnerabilities to your system’s security. Furthermore, it provides comprehensive reports and actionable insights to act on detected critical risks.
Tenable makes it easier for IT operators to communicate and compare cyber exposure while managing risks simultaneously.
It adds security to the Active directory and disrupts attack paths. If you are looking for a simple and automated vulnerability scanning tool for your web applications, invest in Tenable’s Cyber Exposure Platform.
Who is it recommended for?
Tenable is ideal for large enterprises and organizations that require a scalable and comprehensive vulnerability management solution. It’s particularly useful for businesses with complex IT environments, including cloud instances and virtual machines, who need real-time alerts and highly customizable dashboards to manage their cybersecurity efficiently.
Pros:
- Offer complete visibility and control of the OT network
- Actionable insights and reports
- Managed on-premises
- Highly scalable vulnerability management tool
- Offers automated vulnerability scanning
- It helps track dynamic IT assets, including cloud instances, virtual machines, etc.
- Provides Advanced Automation features
- Threat Intelligence to prioritize weaknesses
- Continuous scanning and vulnerability assessment
- Operators can easily detect and assess hard-to-scan devices
- Cloud connectors provide full visibility to public cloud environments
- Supports Prebuilt integrations and APIs
- Supports third-party systems
- Eliminates blind spots and provides instant insights
- Offers Real-time alerts and notifications
- Highly customizable dashboards
- Offers wide coverage and continuous monitoring of applications and cloud infrastructure
Cons:
- Operators face the challenge of switching between interfaces to access a few functionalities.
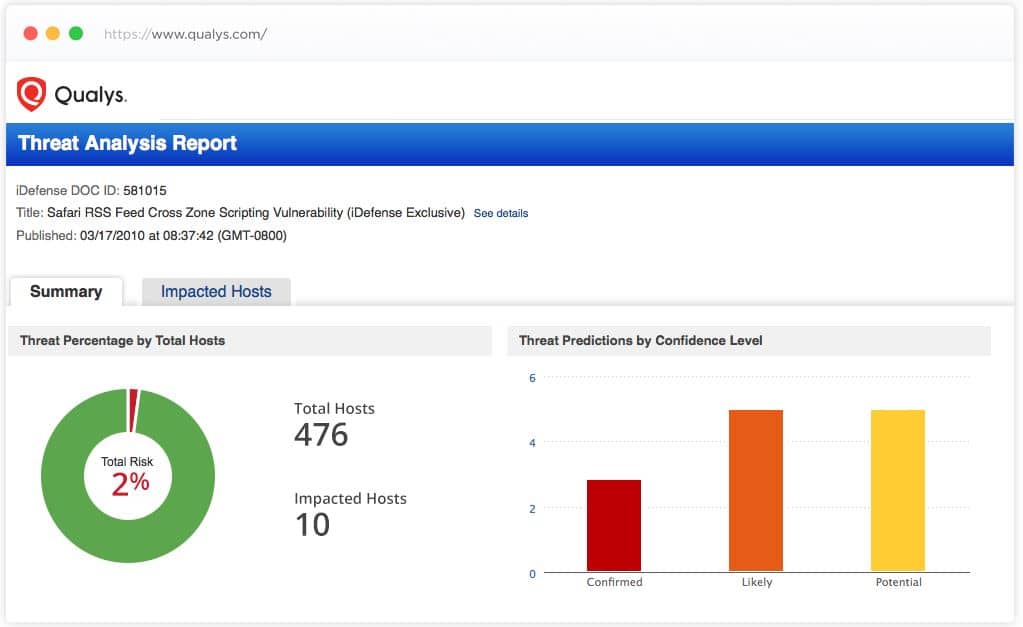
8. Qualys
Qualys Cloud Platform provides endpoint security and enables organizations to detect and monitor assets automatically from a single dashboard. It has an intuitive dashboard that collects data from all types of IT assets and analyzes it to detect vulnerabilities.
Why do we recommend it?
Qualys Cloud Platform excels in offering continuous monitoring and real-time analysis of IT assets, whether they are on-prem or in the cloud. Its ability to automatically detect and prioritize vulnerabilities, coupled with features for endpoint security and automated patch deployment, make it a robust choice for vulnerability management.
With the help of Qualys Cloud Platform, operators can stay prepared for the threats. As and when any threat or suspicious activity is detected by the tool, it immediately notifies the operators. They can address threats before they cause any major damage to the system.
Moreover, it offers a complete and continuous view of the IT assets to detect vulnerabilities at all times. No matter if they are deployed in the cloud or on-premises, the tool offers continuous monitoring of the IT assets.
Who is it recommended for?
This platform is suitable for medium to large organizations that are seeking an all-encompassing vulnerability management solution. Businesses with hybrid IT environments, including both on-premises and cloud deployments, will particularly benefit from Qualys’s comprehensive monitoring and real-time threat analysis features.
Pros:
- It helps eliminates network weaknesses
- Provides endpoint security
- Detects all known and unknown IT assets automatically
- Offers full visibility into on-prem, endpoints, clouds, containers, and OT
- Offers a real-time analysis of threats and misconfigurations
- Alerts on noticing compromised assets and network irregularities
- Prioritizes the risky vulnerabilities
- Automatically deploy patches to remediate vulnerabilities
- Offers control of all your IT assets
- Eliminate false positives
- Provides cloud security, instant visibility, and compliance control
- Tests threats throughout the development cycle
Cons:
- Offers low scans and unexpected downtimes
- Qualys Cloud Platform is expensive
- Susceptible to false positives
- Independent modules can affect the licensing costs
- Stability issues have been reported due to separate module updates
Conclusion
With the rise in cyberattacks and threats, it is a must to look after network security to save your business from losses and damage. A data breach can lead to unhappy customers and expose all your sensitive information. Thus, increase your system’s security by investing in Vulnerability Management Software.
Vulnerability management tools help in the identification, evaluation, and reporting of security vulnerabilities found in the system. These tools enable organizations to perform proper scanning and monitoring of IT assets and networks to look for weaknesses and vulnerabilities. After analyzing the vulnerabilities, the operators can also prioritize them and remediate solutions.
Another advantage of choosing a vulnerability management tool for your enterprise is that you can assign and monitor the threat levels to weaknesses.
By installing any of the above-listed tools, you can stay ahead of your competitors and save your system from the risk of threats and attacks.
You can find many Vulnerability Management Software on the market today, but we have listed some of the best tools with their pros and cons. Go through the above-listed to choose one for your system’s security as per your need and budget.
Also, keep a few factors in mind when choosing a tool for your business. Make sure that the scanner runs on demand and can be scheduled. Further, it is an easy-to-manage software package that offers good results and detects threats faster.