Locking down USB ports is one of the best security practices to ensure organizations are safe from data loss, data theft, or malware infection. In this post, we will go through the ten best USB lockdown software tools that will help you protect your organization from data theft, data leaks, or malware.
USB pen drives are the most accessible removable media for anyone wanting to steal data or inject malware. An insider can steal sensitive company data stored in servers or workstations with unsecured I/O ports by simply plugging in a USB drive. In addition, an outsider (such as a hacker) could use social engineering techniques like USB baiting or USB scams to inject malware into the network.
Here is our list of the best USB lockdown software tools:
- ThreatLocker Storage Control – EDITOR’S CHOICE Blocks all USB devices from attaching to computers on a network. These blocks can be lifted by a central administrator for access by an authorized user. Access a free demo.
- ManageEngine Device Control Plus – FREE TRIAL An endpoint security solution with a focus on DLP. It lets you monitor, control, and block USBs. Start a 30-day free trial.
- Acronis DeviceLock DLP – FREE TRIAL An endpoint DLP solution that offers device control and endpoint management. Start a 30-day free trial.
- CrowdStrike Falcon Device Control A USB lockdown software that gives you full visibility and granular control for safe USB utilization.
- Endpoint Protector by CoSoSys A DLP solution that can centrally monitor, control, and block USB ports (and other peripherals).
- USB-Lock-RP An enterprise-grade device control software, capable of monitoring, controlling, and locking down USB ports.
- DriveLock Device Control A cloud-based endpoint protection platform, with a focus on zero-trust security, and fantastic USB lockdown capabilities.
- Symantec Endpoint Protection More than a simple USB lockdown tool, Symantec Endpoint Protection emphasizes data protection.
- McAfee DLP Endpoint (now Trellix DLP) An all-in-one DLP solution that integrates Endpoint Protection capabilities, including USB blocking (and much more).
- Trend Micro IDLP A solution that lets you implement device protection controls and policies, to prevent data loss from USB devices, and other media.
- Ivanti Device Control A solution for enforcing data encryption and security policies on USBs or other removable media.
What to consider when looking for a USB lockdown software tool?
A USB lockdown software tool is usually a component or utility from a Device Control or Data Loss Prevention (DLP) solution. These USB lockdown tools are rarely dedicated software specially designed for locking down USBs.
Most enterprise endpoint protection or antivirus solutions with centralized management usually come with device control capabilities or DLP, which let you block USB devices. These solutions will also allow you to create device allowlists/blocklists, OTPs (One-Time-Passwords), enforce encryption, transfer limits, etc. These tools can even extend to the point that they allow you to block USB drives by vendor, type, product ID, etc. These solutions install on the endpoint (as agents) and are password-protected so that the end-user cannot tweak any settings.
Recommended features when looking for a USB lookdown tool:
- Support and identify different USB peripherals.
- Centralized control to enforce policies and monitor USBs.
- Automated response to policy violations.
- Set policies for USB transfer limits.
- Configure allowlists to allow or block certain USBs.
- Active Directory integration.
- Enforce USB encryption.
Keep in mind that disabling USB storage does not disable USB functionality entirely. USB storage lockdown software prevents the computer from recognizing storage (usbstor values), but the USB port is still alive. This means end-users would still be able to charge their phones or USB-powered devices and use phone apps like tethering to connect to the network. This is why complete endpoint protection with DLP capabilities and Antivirus becomes handy.
Methodology for selecting the best USB lockdown software tools
Here are some of the various methods and criteria one must take into account when selecting the best USB lockdown software tools.
- Make sure it allows identifying different USB devices and blocking unauthorized access
- Ability to automatically respond to violations
- Uses encryption methods to keep the data secure and safe at all times
- Option to set allowlist and block specific USBs as per preference
- Supports integration with active directory and other settings
The Best USB Lockdown Software Tools
1. ThreatLocker Storage Control – GET DEMO
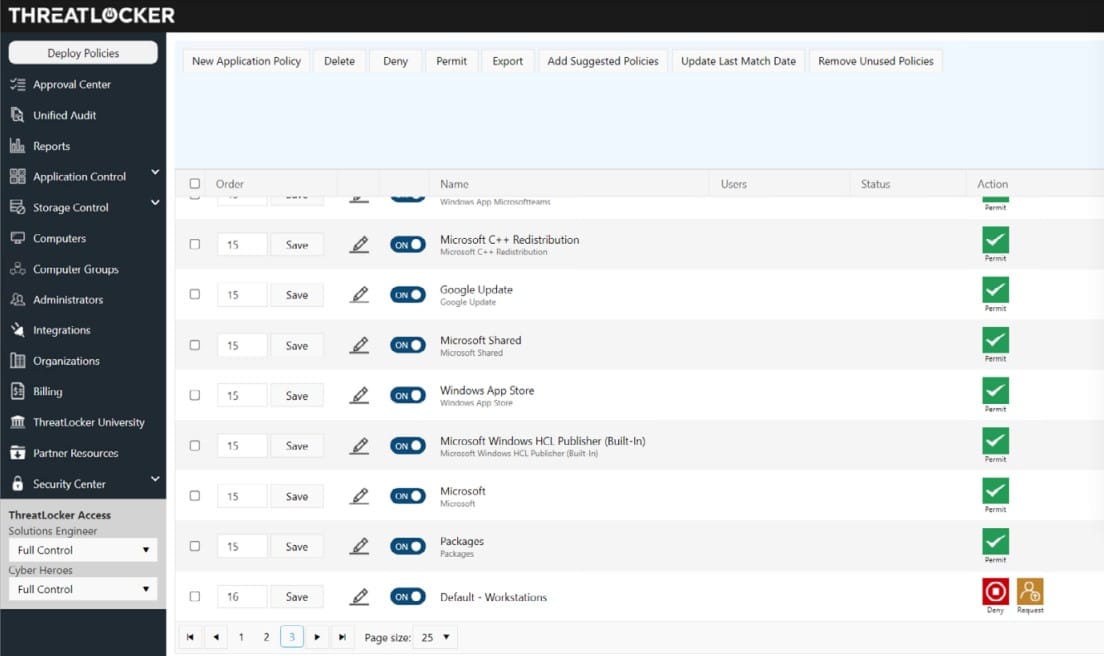
ThreatLocker Storage Control is a USB device management package that is available as part of a package of system security tools. The USB manager blocks all storage devices from attaching to a computer on the network by default. Each device is identifiable by a serial number and the system administrator can choose to allow a specific device to connect.
Key Features:
- Storage Control: Sets granular policies over storage devices to keep the data safe and secure from theft and unauthorized access
- Unified Audit: Gives users on the network and remote workers access to a central log of all storage access
- Access Request: Users need to request the access to the storage device from administrators
- USB Device Blocking: USB policies permit access according to the vendor, file type, or serial number of the device
- Access Rights: Allows only a few specific users to access the storage device for security purposes
- Logs All File Access Events: Generated log messages can be routed to an SIEM tool for auditing.
Why do we recommend it?
ThreatLocker Storage Control is a centralized solution that offers data security to all your USB storage devices and ensures seamless integration with existing security systems. It prevents any unauthorized user from accessing your confidential data without permission thanks to its granular policies.
The ThreatLocker system is a combination of disabling the ability of equipment and software and an extended access rights management service that selectively reactivates those assets. While typical ARMs apply permission levels for resources when accessed by a named user account, the threatLocker system splits that resource part in two – so you have combinations of software and resources (files, devices, printers, etc) to which users are granted access.
Who is it recommended for?
This tool is highly beneficial for organizations that manage sensitive data or security professionals that enforce strict security policies across networks. By default, everything is prohibited, which prevents errors from allowing data to move out of the company.
Pros:
- Data Security: Offers protection to local drives and peripheral devices
- Block Feature: All USB devices are blocked by default but the user can create an allowlist and make changes
- Permission: Administrators have the access to allow or disallow the device to connect to the system
- USB Device Identification: Using the serial number or vendor or file type, admins can recognize a device and permit
- Authorization: Based on user identity or endpoint, certain users gain access to resources and functionalities
Cons:
- No Price List: For product cost and other details, you need to contact the sales team
How to start with ThreatLocker Storage Control? The way to understand the ThreatLocker system is to access the free demo to assess the entire platform, including the Storage Control module.
EDITOR'S CHOICE
ThreatLocker Storage Control is our top pick for USB lockdown software because it applies a security policy for all USB devices across an organization. All USB ports remain active and contactable for further instructions while rejecting all USB devices by default. The system administrator can then selectively approve a device by its ID. Its usage can be limited to one device for a specified user or it can be approved to attach to any computer on the system. There is a mechanism for users to seek approval for a device.
Download: Get FREE Demo
Official Site: https://portal.threatlocker.com/signup.aspx
OS: Cloud-based
2. ManageEngine Device Control Plus – FREE TRIAL
The ManageEngine Device Control Plus is an endpoint security solution with a strong focus on data loss prevention. The software lets you monitor in real time and remotely control (block or allow) removable devices such as USB devices, drives, and other peripherals.
Key Features:
- Detect and Block: Allows only trusted devices and immediately blocks any unverified device on detection
- Data Security: Prevents unauthorized removable devices from stealing data or injecting malware
- USB Port Security: Prevent unauthorized devices from getting access to your sensitive data and endpoints
- Read-Only: Prevents any third user from deleting or modifying data as they have access to read-only
- Temporary Approval: Admins can provide access to a device or user on a temporary basis
Why do we recommend it?
Rather than preventing data loss, ManageEngine Device Control Plus targets the malware threat infiltrating an endpoint via a USB device. The program does, however, include real-time monitoring, activity logging capabilities, automatic updates, and alert investigators when a file is copied to a removable storage device.
The ManageEngine Device Control Plus comes with a web-based administrative UI console that helps you block and monitor all USB devices easily from a single place. The software provides granular control by allowing you to assign access and data transferring policies and respectively push them to clients. You can also get device and information activity reports from clients.
Who is it recommended for?
If your organization is constantly worried about endpoint security or unauthorized access, this tool is great for you as it will disable all your USB ports. It is even great for enterprises that demand role-based access control along with monitoring features.
Pros:
- Prevent Threats: Stops malware entry and data breaches by locking USB ports
- Third-Party Scanning Software: No need for any additional scanning software for unauthorized device detection
- Backup Data: Password-protected backup files can only be accessed by the administrator
- Customizable Widgets: Helps build unique reports using 200+ customizable widgets
- Intelligent Alerts: Eliminates alert fatigue using the intelligent alert system
Cons:
- Time-Consuming: Configuration and app distribution process could be time-consuming for new users
How to start with ManageEngine Device Control? Register to get a fully functional 30-day free trial.
3. Acronis DeviceLock DLP – FREE TRIAL
Acronis DeviceLock DLP is an endpoint data loss prevention (DLP) solution designed to lower the risk of insider data leaks, threats, or data theft. Acronis Device DLP offers device control and endpoint management under the Data Loss Prevention umbrella solution.
Key Features:
- Data Shadowing: Creates duplicate data for backup and redundancy requirements
- Granular Control: Controls and allows permissions to users at a granular level
- Temporary Access: Allows temporary access to USB devices, for example, read-only options
- OCR Technology: Helps extract and inspect textual data
Why do we recommend it?
Acronis DeviceLock DLP offers forensic investigations and ransomware protection with backup and recovery features. Its OCR capabilities along with fine-grained control and its capacity to analyze the content and context of data transfers make it a great tool for protecting sensitive information.
Acronis DeviceLock uses a simple and lightweight agent deployed on the client. It also offers Active Directory integration and a centralized management console from which you can set and enforce policies. Device Lock is one of the best USB lockdown software because of its flexibility. It can work via local data channels (USB, FireWire, SMBs, etc.) that can be allowed, blocked, alerted, or logged.
Who is it recommended for?
If your organization is looking for a solution that offers protection against data leaks and insider threats, this solution is a perfect fit for you. Businesses that need to adhere to strict data protection standards, managed service providers, and IT teams that need exact control over data transfers would find it ideal.
Pros:
- Deployment Process: No need for a lengthy deployment process to stop data leaks from endpoints
- Policy-Based Preventive Controls: Identifies, evaluates, and applies policy-based preventative controls to data transfers in order to stop data leakage through peripheral devices.
- Backup and Recovery: Ensure the company’s data safety by creating regular backups and recovery options
- Centralized Management: Uses a central console to manage, set, and implement strict security policies
Cons:
- Yandex Browser Issue: Does not allow Yandex Browser to open HTTPS websites
How to start with Acronis DeviceLock DLP? Register to download a 30-day free trial.
[“ctech_download_btn anchor=”Acronis DeviceLock DLP” target_url=”https://www.netadmintools.com/go/acronis-best-usb-lockdown-software-tools/l/list/” tagline=”Start a 30-day FREE Trial”]
4. CrowdStrike Falcon Device Control
CrowdStrike is a leading cloud-native cybersecurity platform built to provide complete protection. The software allows users to use one platform with a single agent to deliver endpoint security, cloud security, threat intelligence, identity protection, and security & IT operations. CrowdStrike’s Falcon Device Control is one of the best USB lockdown software tools that gives you the proper visibility and granular control for safe USB usage.
Key Features:
- Granular Control: Manage settings and permission at a detailed level and generate detailed insights
- Policy Configuration: Configures security policies and keeps a close watch over USB usage
- Pre-Built Dashboards: Displays insights and key metrics using pre-built dashboards
- Log Management: Collects and analyzes USB usage logs
- IT Automation: Uses AI-powered techniques and automation functionalities to protect and ensure smooth operations
Why do we recommend it?
One notable feature of CrowdStrike Falcon Device Control is its all-encompassing, cloud-native approach to device security. It provides quick local controls and an integrated dashboard that enables real-time threat detection, tracking, and blocking.
Falcon Device Control uses an agent that can be installed in Windows and macOS systems. Once installed, the software can automatically discover agents within the same network. This agent collects data from the monitored USB device and reports back to the server. Users can also push commands to the agent from the server to limit USB usage.
Who is it recommended for?
For those working in security teams or IT departments in companies that need a comprehensive cybersecurity solution, especially in settings that are growing or changing quickly, this platform is recommended. For enterprises that rely heavily on the cloud, its cloud-native architecture further qualifies it.
Pros:
- Monitoring Features: Helps identify risks in real-time and keeps user updated about the status
- Quick Alerts: Provides streamlined notifications and alerts on noticing anything suspicious or unauthorized USBs
- Pre-Built Dashboards: Enables users to track and block threats in real-time using these dashboards
- No Additional Software: Users no longer need to install any additional software or hardware to use its features
- Usage Restriction: Possible for users to restrict USB usage by sending commands to the agent from the server
Cons:
- Look and Feel: Some users might find it difficult to adapt to the different look and feel of the platform
How to start with Falcon Device Control? Contact CrowdStrike customer service for more information. You can also begin with CrowdStrike software by trying Falcon Prevent (a powerful AV) for a 15-day free trial.
5. Endpoint Protector by CoSoSys
Endpoint Protector by CoSoSys is a cross-platform Data Loss Prevention (DLP) solution. It prevents data leaks and theft and provides granular control for USBs and other portable storage devices. The software can be deployed via virtual appliance, over the popular cloud services, or SaaS.
Key Features:
- Device Control: Regulates peripheral ports and keeps an eye on USB devices
- Content-Aware Protection: Runs scans, regulates, and stops uncertain file transfers to safeguard all the content
- Enforced Encryption: Converts USB storage device data into an encrypted format for security purposes
- eDiscovery: Carries out both automatic and manual scans for data at rest
- Compliance: Guarantees that your data complies with SOX and HIPAA regulations.
Why do we recommend it?
With its advanced features and compatibility with multiple operating systems, Endpoint Protector is an effective multi-OS data loss prevention product. Its comprehensive policy, device restrictions, enforced encryption, and eDiscovery capabilities are just a few of the characteristics that make it the best choice for hybrid OS networks.
Endpoint Protector’s Device Control is one of our favorite USB lockdown software tools. It can centrally block, control, and monitor USB (and other peripheral) ports to avoid data loss, theft, or potential USB-borne Malware. The software monitors (remotely) USB ports using a lightweight agent installed on Windows, macOS, or Linux. The agents enforce the policies on the client and are password-protected.
Who is it recommended for?
Businesses of all sizes who want to improve internal data security protocols and avoid data loss should use this software. Businesses that employ various operating systems and languages, such as Windows, macOS, and Linux, will find it especially helpful.
Pros:
- Fast Remote Client Deployment: Allows the quick installation of client software across numerous devices from a remote location, which shortens the deployment time
- Scanning: Keeps scanning for data that is at rest and data that is moving
- Highly Compatible: With Linux, Windows, and macOS, the program functions seamlessly across all platforms
- Full Protection: Offers full safety for all of the data you have on USB devices
- Data Exporting: Makes all logs and reports exportable in a readable format for users
Cons:
- No Protection: Does not provide security for apps created by third-party tools
How to start with the CoSoSys endpoint protector? Request a demo.
6. USB-Lock-RP
USB-Lock-RP by Advanced International Systems is an enterprise-grade device control software capable of controlling and locking down USB ports. The USB-Lock-RP software provides a centralized platform for managing and monitoring USB devices, including other removable storage, mobile devices, wireless adapters, and groups of computers.
Key Features:
- Easy to Set: Centralized management tool is quite easy to install and operate
- Device Control: Admins can control the USB or removable devices even in large networks without any hassle
- Group Policy Settings: Allows setting and implementing security configurations, software installation policies, and more for groups of users in real-time
- Read-Only: Admins can provide read-only or temporary access to specific USB drives
- Export Reports: Users can export detailed reports in CSV format as well
Why do we recommend it?
USB-Lock-RP is one one of the most robust USB device control software solutions that delivers real-time policy enforcement, data encryption, and enterprise-grade control over USB ports and other removable storage. Because of its advanced functions, it’s a great option for businesses that require all-encompassing USB security.
Who is it recommended for?
For enterprise environments where centralized control of USB and other portable devices is essential, this application works well. It’s especially helpful for businesses that need to monitor security rules in real-time and mostly rely on Windows-based machines.
USB-Lock-RP’s centralized management console runs on-premises on Windows machines. The sys admin can configure access policies to control devices and enforce new rules on individual computers or entire groups of computers. In addition, the software also shows alerts and logs, including USB file transfer monitoring.
Pros:
- Detect and Lock: Enables users to detect unknown USBs and lock USB ports using the advanced features
- Block USB: Mostly all USBs are blocked by default and a few specific ones are only supported for security purposes
- Encryption: Keeps all the files encrypted when transferring from one system to authorized USB drives
- Group Policies: Enforces group policies in real-time to keep the network safe and secure
- Compatibility: Works well with all remote desktops
Cons:
- Incompatible: Does not work well with all platforms like Linux and Mac
How to start with USB-Lock-RP? Download the USB-Lock-RP free demo and manage device access for up to five clients. The license price is $20.00 USD per client (for 10-100 clients) and $15.00 USD per client (for 110-500 clients).
7. DriveLock Device Control
DriveLock is a fully integrated cloud-based endpoint protection platform designed to safeguard a company’s data, devices, and systems. The software uses a zero-trust approach (never trust, always verify) and its team of security experts to achieve a high degree of security. DriveLock’s solutions are certified with the Common Criteria EAL3+ certificate, a global security standard.
Key Features:
- Monitoring Capabilities: Keeps a close track of all the USB devices and their data transfers
- Encryption: Encrypts all the USB devices and removable devices automatically for more security
- Reporting: Comes with forensic investigations and in-depth reporting capabilities
- Device Configuration: Uses machine learning and artificial intelligence methods to streamline and automate the configuration of integrated devices
Why do we recommend it?
With features like data transfer monitoring and automated USB encryption, DriveLock Device Control offers a strong multi-layered endpoint security solution. The software’s accreditation with Common Criteria EAL3+ further validates its reputation as a provider of high-level security.
DriveLock’s Device Control is a fantastic USB lockdown software tool. It allows organizations to protect themselves from unauthorized or unencrypted USB devices and data transfers. With DriveLock, you can also create allowlists to permit specific devices and deny others. You can deploy DriveLock on-premise or via their cloud solution.
Who is it recommended for?
For businesses looking for an all-inclusive, certified endpoint security solution, DriveLock is great. It’s especially helpful for companies that need to have both on-premises and cloud deployment options and employ a zero-trust security posture.
Pros:
- File Monitoring: Allows users to monitor each file that is copied from one place to another
- Forensic Analysis: External USB data carriers are automatically encrypted by DriveLock, which also does thorough forensic investigation
- No Third-Party Tool: Doesn’t require any further third-party software
- Multi-Layered Endpoint Security: Allows users to monitor all connected external and internal devices
Cons:
- Not Suitable for All Users: Non-technical users might not find it a great fit
How to start with DriveLock Device Control? Register to download a 30-day free trial.
8. Symantec Endpoint Protection
Symantec Endpoint Protection by Broadcom is an excellent choice if you are looking for more capabilities than simply locking down USBs. This solution might seem feature-overkill for people only looking to lock down USB ports. The software also includes capabilities for intrusion prevention, firewall, anti-malware, and the foundational features of DLP software. It deploys in on-premise, cloud, or hybrid environments.
Key Features:
- Detect and Response: Uses innovative technologies to detect and protect traditional and mobile endpoint devices
- Endpoint Management: Provides in-depth insights into endpoints inside and outside the perimeter for better security
- Block Unauthorized Devices: On noticing unknown or unauthorized USB flash drives, it automatically blocks all data transfers
- Centralized Management: Uses a single console to manage and monitor all the endpoints
Why do we recommend it?
Symantec Endpoint Protection is not only limited to providing USB lockdowns, but comes with various other capabilities and security solutions that make it a great product. Its low false positive rate due to machine learning and AI makes it an excellent choice for several tiers of endpoint protection.
Symantec Endpoint Protection (SEP) emphasizes data. It protects data wherever it lives; at endpoints, desktops, cloud workloads, mobiles, servers, apps, containers, and storage devices. SEP includes an application and device control policy that lets you block all USB drives, from pen drives to hard drives on the clients. The software can also identify hardware IDs to help create allowlists and permit or stop specific USB drives or peripherals.
Who is it recommended for?
Medium to large sized businesses might find it an ideal solution for it offers intrusion prevention and anti-malware features along with USB port lockdown. It will also be highly beneficial for organizations that need various deployment options, such as on-premise, cloud, or hybrid.
Pros:
- Data Protection: Regardless of your device location, it provides full protection for your data
- Flexible Deployments: Suitable for all on-premises, cloud-based, and hybrid environments
- Reduce Vulnerabilities: Identifies malware in storage devices in real time and prevents data leaks
- Better Decision-Making: Quickly discover vulnerabilities and implement the necessary patches and updates by using historical and real-time data.
Cons:
- Needs Improvement: Certain flaws in the security module that require improvement
How to start with Symantec Endpoint Protection? Contact sales to request a demo or trial.
9. McAfee DLP Endpoint (Now Trellix DLP)
McAfee Data Loss Prevention, now Trellix DLP, is an all-in-one DLP solution including McAfee DLP Discover, McAfee DLP Prevent, McAfee DLP Monitor, McAfee DLP Endpoint, McAfee Device Control, and MVISION Cloud Integration. The McAfee DLP Endpoint can provide USB lockdown capabilities and so much more. It covers all data leaking channels, including USBs, removable media, email, IM, web, cloud, printing, screen captures, clipboard, file-sharing applications, etc.
Key Features:
- Ransomware Protection: Identifies and responds to threats like ransomware in real-time
- Zero-Trust Strategy: Provides visibility into endpoint operations, traffic, and cloud security posture and eliminates blind spots
- AI-Powered Operations: Uses AI to reduce alert noise and automate response
Why do we recommend it?
McAfee DLP Endpoint excels when it comes to offering thorough protection against data leaks across a variety of channels, not just USBs. it is even good in terms of AI-powered operations, providing real-time notifications and strong policy management.
The solution works on-premise but can also be extended to the cloud with its integration to MVISION Cloud. This approach ensures that sys admins can also extend the on-premise DLP policies to the cloud. The native integration to MVISION ePO helps simplify policy and incident management.
Who is it recommended for?
Businesses of all sizes can invest in this tool to prevent data loss across different platforms. Even businesses that are complex in nature and demand compliance with strict data protection rules and regulations will find it especially helpful.
Pros:
- Threat Intelligence: Helps provide protection against the most important threats
- SIEM Integration: Integrates with more than 650 Trellix solutions and external products while utilizing your current security tools
- Data Security: Encrypts all the data and prevents unauthorized access from removable devices
Cons:
- Lacks Certain Features: Discovery mode, OCR, or AI-based technique are not supported
How to start with McAfee DLP? Request a Free Demo.
10. Trend Micro IDLP
Trend Micro Integrated Data Loss Prevention (IDLP) (for Business) is a solution that combines with other Trend Micro solutions (such as Apex One Endpoint Security) and management consoles. IDLP lets you implement device protection controls and policies and improve visibility. With IDLP, you can prevent data loss from USB devices or other media such as email, SaaS apps, web, or cloud storage.
Key Features:
- Automated Threat Detection: Automatically identifies threats like ransomware and fileless and provides endpoint protection
- Centralized Visibility: Provides clear visibility into all endpoints and devices from a central console
- Integration Support: Allows users to seamlessly integrate with SIEM solutions in an efficient manner
Why do we recommend it?
Trend Micro IDLP stands out with providing comprehensive device control and data loss prevention rules across several media platforms. It helps expand the scope of threat visibility throughout the entire business by improving detection, investigation, and response capabilities across several security layers.
Trend Micro IDLP uses a lightweight agent installed on clients, which gives you visibility and control over your USB ports. You can restrict specific USB devices while allowing others. When the software detects a violation, you can configure it to automatically respond with actions like logging, blocking, encrypting, alerting, bypassing, modifying, quarantining, or deleting data.
Who is it recommended for?
Businesses that want a thorough and integrated approach to prevent data loss across several platforms, like USB devices, emails, and cloud storage, will find this solution highly appropriate. Because of its templates that are already configured, it is also perfect for companies that need to comply with different regulations.
Pros:
- Flexible: SaaS and on-premises deployment choices allow you to gain deployment flexibility
- Effective Protection: Uses behavior analysis to protect data against ransomware, injection, and other threats
- Actionable Alerts: Triggers alerts bout anomalies and recommendations on the actions that need to be taken in response to the alert
Cons:
- Needs Improvement: Logging feature demands attention and improvement
How to start with Trend Micro IDLP? Register to start an Apex One Endpoint Security free SaaS trial that integrates with IDLP.
11. Ivanti Device Control
Ivanti Device Control is a solution that allows you to enforce data encryption and security policies on USBs and other removable media. Ivanti Device Control is one of the best USB lockdown software because it will enable you to quickly lock down and re-take control of devices (such as USBs) highly associated with data loss and malware infection.
Key Features:
- Endpoint Encryption: Lets you quickly implement data encryption and safety measures for removable devices
- Detect and Block: Offers visibility and prevents unknown apps from getting installed by identifying and locking endpoints
- Transparency Across Silos: Enables you to respond and be proactive for the emerging security risks
Why do we recommend it?
Ivanti Device Control stands out for its robust, centralized platform and scalable protection capabilities that make it a great product for most organizations. Using this tool, you can manage and monitor multiple endpoints and lock down unknown apps, reducing your attack surface.
Ivanti discovers every endpoint where a client has been deployed. These discovered devices can be managed and controlled from a single console. The system uses a zero-trust approach, so you’ll be able to set allowlists, where you define which devices are allowed (while the rest are blocked). You can then enforce the security policies for the specific USB devices (determined by type or ID).
Who is it recommended for?
Large organizations with complex network systems and the ones that demand centralized control might find it an ideal option. With its smooth integration with Windows Active Directory, it provides granular permissions depending on user roles, making it particularly helpful for enterprises that follow a zero-trust security strategy.
Pros:
- Enhance Security Policies: Uses whitelist to manage data and devices centrally
- Secure Productivity Tools: Make sure users can still access these tools as needed while maintaining data security
- Authorization: Without authorization, even administrators are unable to eliminate Ivanti Device Control agents
Cons:
- Complicated: Design of the console is a bit complicated and challenging for beginners
How to start with Ivanti Device Control? Request a free demo.
USB Lockdown Software FAQs
Can you lockdown USBs without DLP or device control software?
If you are using Windows, you can disable USBs within an Active Directory domain simply by using Group Policy Objects (GPO). Within an AD, you can use Group Policies to enforce USB restrictions. The simplest way to lock down USB ports in a domain is to configure a GPO to disable ubstor.sys.
How to manually lock down USB ports?
Another simple (but more extreme) suggested solution is to disable USB ports via BIOS. Some computers allow changing these values for removable media (USB storage) but not for main peripherals like mouse and keyboard. Always ensure that USB-based peripherals like mouse, printer, or keyboard are not affected.
How to lockdown USBs if the computer is outside a domain?
If the computer (or set of computers) is outside a domain and you are unable to apply Group Policies, then you could change local registry settings (usbstor values) manually, change BIOS or use hardware-based solutions, such as USB port blockers (find them on Amazon).
Alternatives to USB lockdown software tools?
The first and most simple way would be to train employees not to use USB ports and instead stick to the storage/transferring mechanisms given by the company or charge their phones using wall sockets. You can also use hardware-based USB port blockers.
Can a USB lockdown software protect you from Malware coming from USB baiting?
No, not every USB lockdown solution can save you from avoiding complex USB-infected devices such as those found in the parking lots. Some of these USB scams install drivers (just like a mouse or keyboard) would and are not necessarily storage-based. To protect from such threats, the software can be strengthened with antivirus or endpoint protection.