With more use of cloud services and applications with multiple entry points, it has become essential for organizations to invest in tools and solutions that help identify vulnerabilities in real-time, detect entry points to the network, and offer better security features.
Here is our list of the best SOAR software:
- Logpoint SOAR This service partners with the Logpoint SIEM unit. While the SIEM gathers data from around the system using its own agents, the SOAR pulls in contributions from third-party security tools.
- Rapid7 Insightconnect One of the best security orchestration, automation, and response solution that allows teams to streamline security operations in different areas such as, threat and vulnerability management, incident response, and security operations automation.
- Siemplify A modern security operations platform that allows security teams to investigate, analyze, and remediate threats.
- Cyberbit A SOAR platform that provides security leaders with a single destination for managing all SOC readiness and skill development activities.
- DFLabs IncMan A cloud-based and on-premise SOAR solution that is capable of full incident lifecycle automation.
- Splunk Phantom A SOAR system that investigates and responds to security incidents in seconds, and increases productivity to better protect your organization.
- LogRhythm RespondX It has built-in automation capabilities and playbooks that helps your SOC team automate standard responses to common alerts and alarms.
- ServiceNow It is one of the best SOAR solutions that simplifies the identification of critical incidents and provides workflow and automation tools to speed up remediation.
- IBM Security SOAR A SOAR platform that helps organizations to effectively orchestrate responses to cyber threats.
Over the years, cyber threats have become more sophisticated, and attackers are aware of different means and mediums to enter the system and ways to steal your data. Even with an experienced team of security analysts in your organization, the chances are high that you might miss out on responding to incidents or threat detecting.
Managing disparate systems manually is not an easy task. SOAR tools eliminate this issue by automating the data collection process and managing threats in real-time. Being able to monitor data from a single location helps with threat detection and incident response.
Here, we will discuss SOAR software in detail and how it is an effective solution for any organization. Additionally, we have listed some of the top SOAR software with their features, pros, and cons to make it easier for you to choose one for your business.
What is SOAR?
SOAR stands for Security Orchestration, Automation, and Response, a collection of tools that help organizations manage security threats and vulnerabilities. It is a combination of Security Orchestration and Automation (SOA), Threat Intelligence Platforms (TIP), and Incident Response Platforms (IRP). Together these solutions enable organizations to collect data from multiple sources, view and analyze them.
With the increase in threats, many organizations are looking for software solutions that help automate security operations and processes, further manage vulnerabilities, and respond to incidents.
The SOAR is one such solution that enables IT teams to collect data, analyze and address potential threats before they launch and cause any major damage. With the help of these tools, IT teams gain more visibility and can respond to security threats faster.
Another advantage of SOAR software is they rely on artificial intelligence, machine learning, and other latest technologies, which help in quick detection and response delivery of security issues at scale.
Additionally, with the help of detailed diagnostics and insightful reports, organizations can improve decision-making and resolve security threats faster.
How Does SOAR Work?
SOAR solutions have a dashboard that provides all the information related to the security data and metrics compiled from different other sources and systems. It is a monitoring platform that allows users to analyze the collected data and develop a comprehensive view of threats.
Most of the tools supported by the platform use threat intelligence and AI to improve user’s response to threats. With automated detection and incident response tools, businesses can run detailed diagnostics, fix issues faster, and improve decision making.
We have broken the SOAR platform into three components to make it easier for you to understand how it works.
- Orchestration A process under which the users collect data from different sources and store it in one place to get a top-down perspective of existing security threats. As a security analyst, instead of moving between different systems and checking every other source for alerts, the SOAR tools help in the easy management of alerts and other information from a single location. Additionally, it eases the vulnerability management process.
- Automation The second vital component of the SOAR tool designed to reduce the burden on network administrators and security analysts. It is not a simple task to manually respond to every cyberattack and manage and detect all security events. A single administrator cannot monitor multiple systems and look for every alert or notification throughout the day. However, with the help of SOAR solutions, network administrators and security analysts find it much easier to monitor security events. Its automated workflow, alert, and response feature saves administrators time and reduces the burden. Further, on detecting any anomalous activity, the solutions automatically shut down the device or user account to prevent damage.
- Response The Response component focuses on incident management. The dashboard provides complete information on the response activities that take place. With the help of this information, users can view alerts, manage threats in real-time, and respond to security events effectively. It also provides other details that help users to find solutions that will make security events faster.
How can SOAR help your organization?
Today, many organizations are facing issues with maintaining security. One cannot manage the security events manually as it is a time-consuming task. Security analysts need to identify, detect, and analyze multiple sources and systems, which can be challenging. Additionally, the chances are high that the analysts might miss the existing threats or respond to incidents under so much pressure.
That’s where security orchestration and automation come into play. With the help of an effective SOAR solution, organizations can achieve results in less time and make better decisions for the future.
Instead of depending on point-to-point integrations, the solutions help build different processes that connect you with the right technology to achieve security goals.
Further, it helps build automated workflows and streamlines different operations that accelerate your security program.
SOAR solutions also add more flexibility and open opportunities for collaboration. There are many benefits of choosing SOAR software for your organization. We have also shortlisted a few SOAR software that will work best for your organization and suit your budget.
The Best SOAR Software
SOAR solutions automate workload processes, thus making network monitoring more efficient and your business more secure from unwanted threats. Here are some of the best Security Orchestration and Automation (SOAR) software that can help identify threats, manage vulnerabilities in real-time, and respond to incidents faster.
Methodology for Selecting SOAR Software Tools
Security Orchestration, Automation, and Response (SOAR) is a cybersecurity strategy that aims to automate a response to cyber-attacks. This can be done by either automatically executing the response or by providing an interface for human operators to execute it. There are many SOAR systems available online, but to make it easier for you to select the right one we have listed a few criteria:
- Is it capable of interacting with other oyster packages?
- Does it support the alert feature, i.e., the ability to send or receive triggers immediately?
- Does the selected SOAR system contribute to threat-hunting goals?
- Does it support data exchange and automation for script-based execution?
Check out some of the best SOAR software that might suit your requirement.
1. Logpoint SOAR
Logpoint SOAR partners with Logpoint SIEM. The SIEM has a local component, which is called AgentX. This is resident on each endpoint and it gathers activity data and logs, which it sends to the central threat-hunting unit. The SOAR can contribute to the data pool for the SIEM but its main aim is to integrate the discoveries of the threat-hunting services of other security tools that are present on the same system as the Logpoint platform.
Key Features:
- Combines with a SIEM
- Available as an on-premises package or a SaaS platform
- Acquires the threat discoveries of third-party tools
- Provides a library of playbooks for automated responses
- Implements automated responses via third-party services
- Centralized pool of activity data
- Context enrichment for arriving analysis
- Provides more than 620 integrations
Why do we recommend it?
Logpoint SOAR combines with a SIEM on the same platform. While the SIEM works with gathered data, the SOAR channels the assessments of outside tools into the Logpoint environment. The dual SIEM-SOAR strategy creates a coordinated approach for businesses that already have other tools on site when they take on the Logpoint system.
The core of the SOAR is a library of playbooks. This included more than 6,800 rules that trigger actions from specific atomic discoveries from one third-party tool or a combination of alerts.
The SOAR system is particularly connected to firewalls and gateways. These tools provide functions that the Logpoint platform doesn’t offer. So, while Logpoint’s SIEM looks for the activities of miscreants who have already got into the network, it relies on the guardians of the network to slam the door on discovered intruders.
Similarly, the Logpoint platform needs to reach out to access rights managers in order to shut down hijacked accounts or disgruntled users. The connections to outside tools is a major benefit of the SOAR service.
Who is it recommended for?
The Logpoint platform is designed for mid-sized and large companies. Subscriptions to the package have a minimum order quantity requirement, which makes the package unsuitable for small businesses. Logpoint also markets its platform to managed security service providers for use in protecting the systems of their clients.
Pros:
- More than 6,800 automated response rules
- Activity records are stored as logs in files for auditing
- Alert deduplication reduces the number of notifications that all point to the same problem
- Opportunities for post-attack analysis
- HIPAA and GDPR compliance reporting
Cons:
- No free trial
Logpoint is available in two formats. The first of these is a SaaS platform and the second is a software package for Ubuntu Linux. The pricing structure for the two platforms is different. The on-premises package has a price per protected unit with a minimum order size. Logpoint advertises a minimum price for its SaaS package but doesn’t specify the size of network that price will cover – you have to contact the Sales Department for details. The prices for Logpoint are given in Euros.
Logpoint doesn’t offer a free trial for its SIEM and SOAR platform. However, you can learn about the service by accessing a free demo.
2. Rapid7 Insightconnect
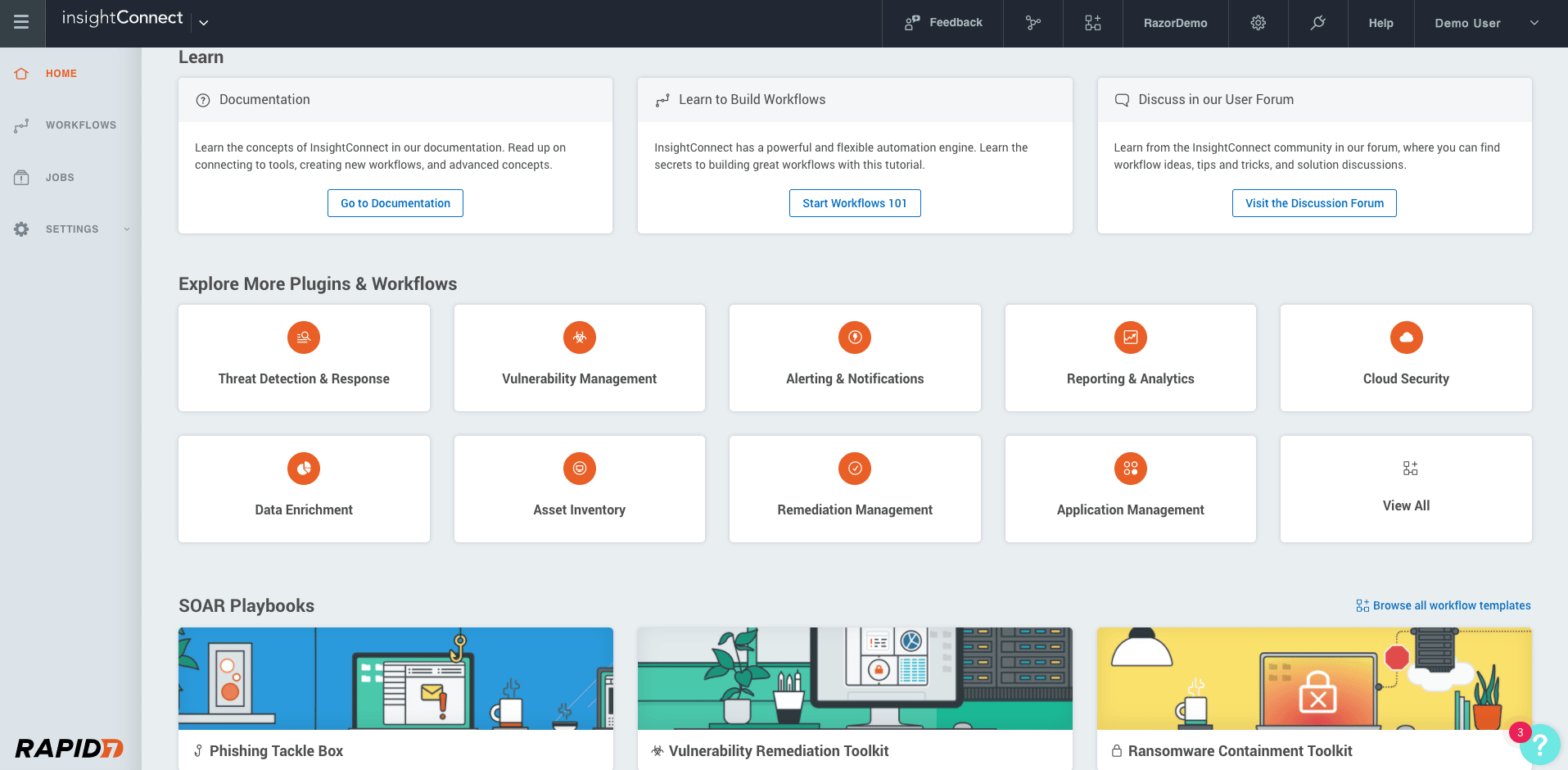
Rapid7 Insightconnect is one of the popular SOAR software that helps eliminate manual tasks and enables users to build a comprehensive security system. It streamlines repetitive tasks, accelerates security options without sacrificing analyst control, and connects the team for better communication and integration.
Key Features
- Automate responses and investigations
- Seamless integration
- Customizable remediation policies
- Supports 300+ plugins
- Incident response
- Workflow builder
- Prioritizes and manages new vulnerabilities
- Supports webhooks for ITSM solutions
Why do we recommend it?
Rapid7 Insightconnect stands out for its capability to automate complex tasks while offering a high level of customization in remediation policies. With support for over 300 plugins and seamless integration capabilities, it provides a comprehensive SOAR solution that empowers businesses to focus on impactful security strategies.
It supports 300+ plugins and a library of customizable workflows that accelerate vulnerability management and automate incident response.
With Rapid7 Insightconnect, businesses have to no longer worry about the bigger challenges as the SOAR solution investigates every suspect email, attachment, or URL and focuses on implementing more impactful strategies.
It also supports ChatOps systems like Slack or Microsoft Teams that help increase visibility and aid in vulnerability management processes. If you have large-scale teams and want to construct complex remediation solutions with ease, look no further.
Who is it recommended for?
This platform is ideal for businesses that have large security and IT teams and are seeking to automate manual tasks efficiently. It’s also suitable for companies already utilizing ChatOps systems like Slack or Microsoft Teams, as it integrates seamlessly to improve visibility and vulnerability management processes. With its built-in vulnerability management and extensive library of workflows, it caters to organizations looking for a more proactive approach to cybersecurity.
Pros:
- Monitors emails, user behaviors, attacker activity, etc.
- Allows automating manual tasks
- Implements impactful strategies to stop malicious emails
- Allows integration with existing IT and security systems
- Built-in vulnerability management
- Supports several visual tools to build workflows
Cons:
- Plugins that support existing workloads require attention
- In large environments, onboarding can be complex
The Rapid7 Insightconnect platform provides security teams with a 360-degree view of their organization’s cyber risk and threat landscape. It also includes features such as automated vulnerability assessment and remediation, security monitoring, and threat intelligence feeds.
Using this SOAR system, you can cut down on manual tasks and employ customizable remediation strategies. It also provides access to 300+ plugins that aid in integrations and better workflow.
3. Siemplify
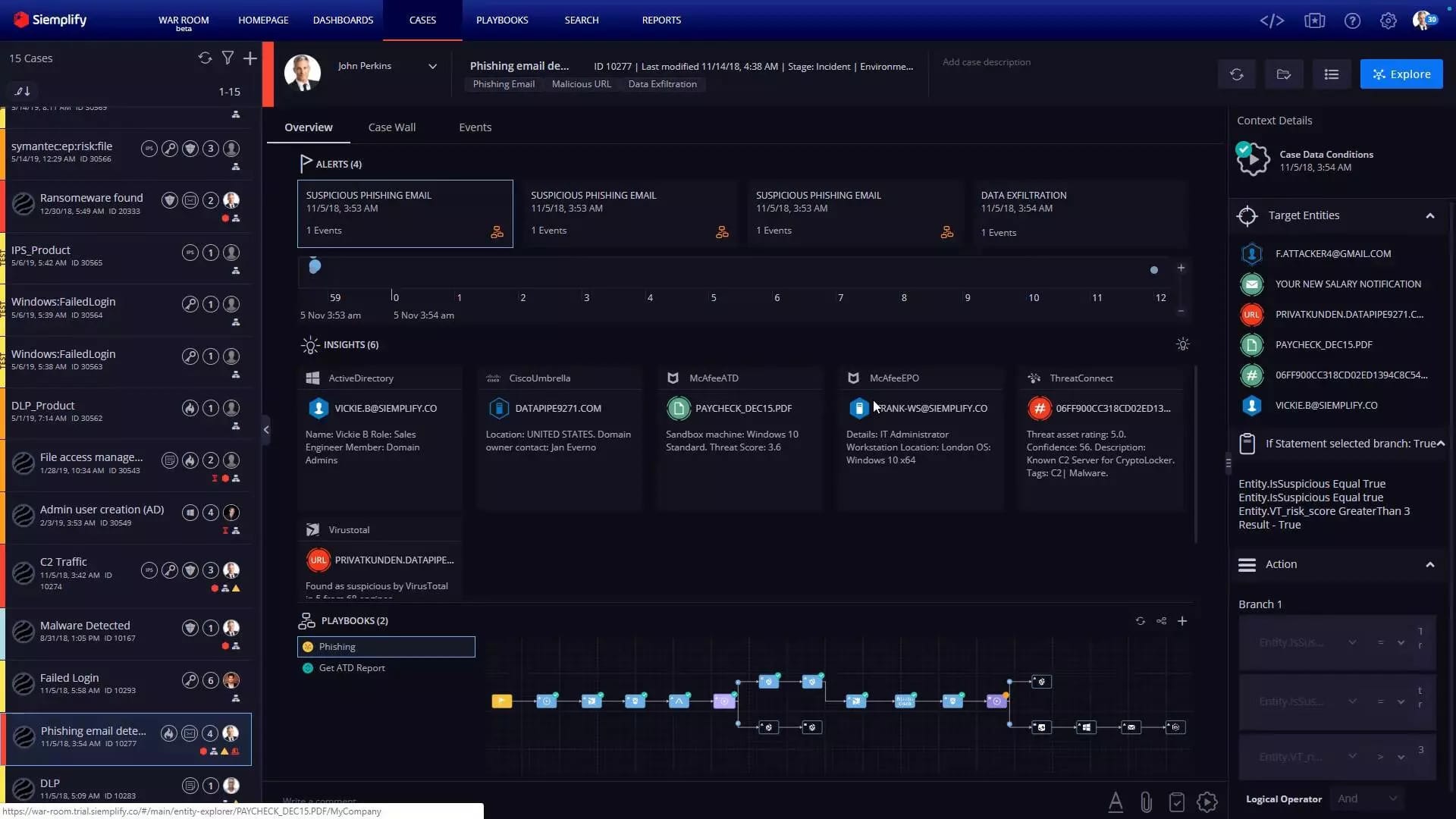
Siemplify is a SOAR solution that allows administrators to collect data from SIEM and EDR tools in one place and perform an analysis. It provides a high-quality user experience and uses machine learning and other latest technologies to create a prioritized list of alerts that enables users to speed up remediation.
Key Features
- Real-time metrics
- Prioritize alerts
- Team Collaboration
- Supports Recording features
- Supports threat-centric approach
- Code-free playbook builder
- Threat Intelligence
- Disaster Recovery
- Incident Management
- Process/Workflow Automation
- Incident Response and Reporting
Why do we recommend it?
Siemplify excels in providing a centralized platform for data collection and analysis from various SIEM and EDR tools. Leveraging machine learning, it efficiently prioritizes alerts and significantly speeds up the remediation process. Its real-time metrics and KPI visualizations offer actionable insights, making it a robust solution for threat detection and response.
With the help of Siemplify, administrators and security analysts can also view real-time metrics and KPIs in different forms. For instance, you can view the Alert Distribution data in pie chart form, which helps simplify complex data and makes it easier for admins to figure out some of the biggest security vulnerabilities.
It also helps in quick detection of the root cause of a security incident. Further, Siemplify supports team collaboration and recording options.
If you are looking for a solution that will help improve your response time and generate real-time metrics, go for Siemplify.
Who is it recommended for?
Siemplify is ideal for organizations with complex security infrastructures that require a centralized SOAR solution. It suits administrators and security analysts looking for real-time metrics and a tool that can prioritize threats intelligently. If your team needs a platform that supports collaboration, scales easily and offers code-free playbook building, Siemplify is a strong candidate.
Pros:
- It is quick at incident detection and responding to threats
- Allows administrators to access more context and perform better analysis
- Simplifies management and saves time
- Easily meets scalability demands
- Prioritizes threats more effectively and boosts productivity
- Helps lower costs
- Turns complex data easier in large environments
- Reduces false positives and prioritizes alerts
- Supports messaging and data sharing features
Cons:
- Conflated expectations
- Often fails to remediate a broader security strategy
- Less metrics
- Deployment complexity
- Supports no trial version
4. Cyberbit
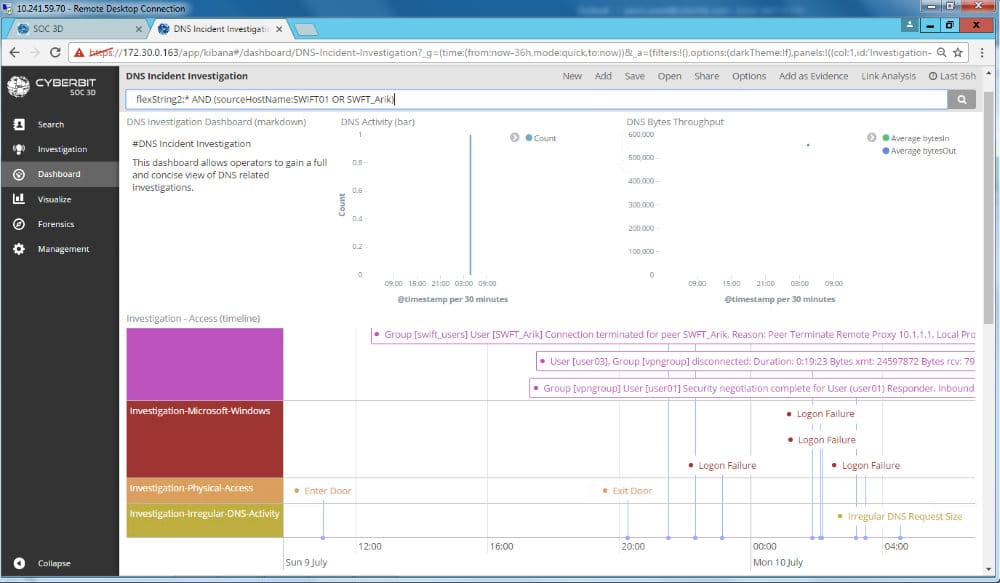
Cyberbit ensures that your SOC teams comprise foundational skills and stay fully prepared for the attacks at all times. It is one of the best platforms that validate the team’s performance and delivers the entire cyber skilling spectrum.
Key Features
- Malware Detection
- Remediation Management
- Supports Commercially licensed security tools
- Behavioral Analytics
- Identifies gaps and benchmarks SOC
- Quick response to recent threats
- Compare and share progress reports with management
- Allows integrating commercial tools
- Management Dashboards
- Live-fire cloud security exercises
Why do we recommend it?
Cyberbit is a comprehensive platform that not only focuses on malware detection and remediation but also emphasizes the skills and readiness of SOC teams. It offers real-world, live-fire cloud security exercises and supports commercially licensed security tools, making it a complete package for modern cybersecurity needs.
Cyberbit supports live MITRE ATT&CK techniques and commercial tools for threat hunting. It focuses on delivering a hyper-realistic SOC team that looks for threats before they launch an incident response.
It also allows administrators to define and track your KPIs. Businesses can view the detailed reports, track progress and understand performance gaps using the customizable dashboard.
Sparkle, Sirius, Optiv, Miami Dade College are some of the high-profile companies and educational institutes that trust Cyberbit.
Who is it recommended for?
Cyberbit is best suited for organizations looking to empower their SOC teams with foundational skills and preparedness for real-world cyber threats. It’s an excellent fit for security leaders who want to manage skill development and readiness from a single platform. If your organization requires robust KPI tracking and customizable management dashboards, Cyberbit should be on your shortlist.
Pros:
- Helps boost SOC performance
- Enables security leaders to manage the entire skill development lifecycle in one platform
- Stress-test and retrieves the team’s readiness score
- Integrates commercial tools for better security
- Guides defensive techniques and master their security tools
Cons:
- No cons found in Cyberbit
5. DFLabs IncMan
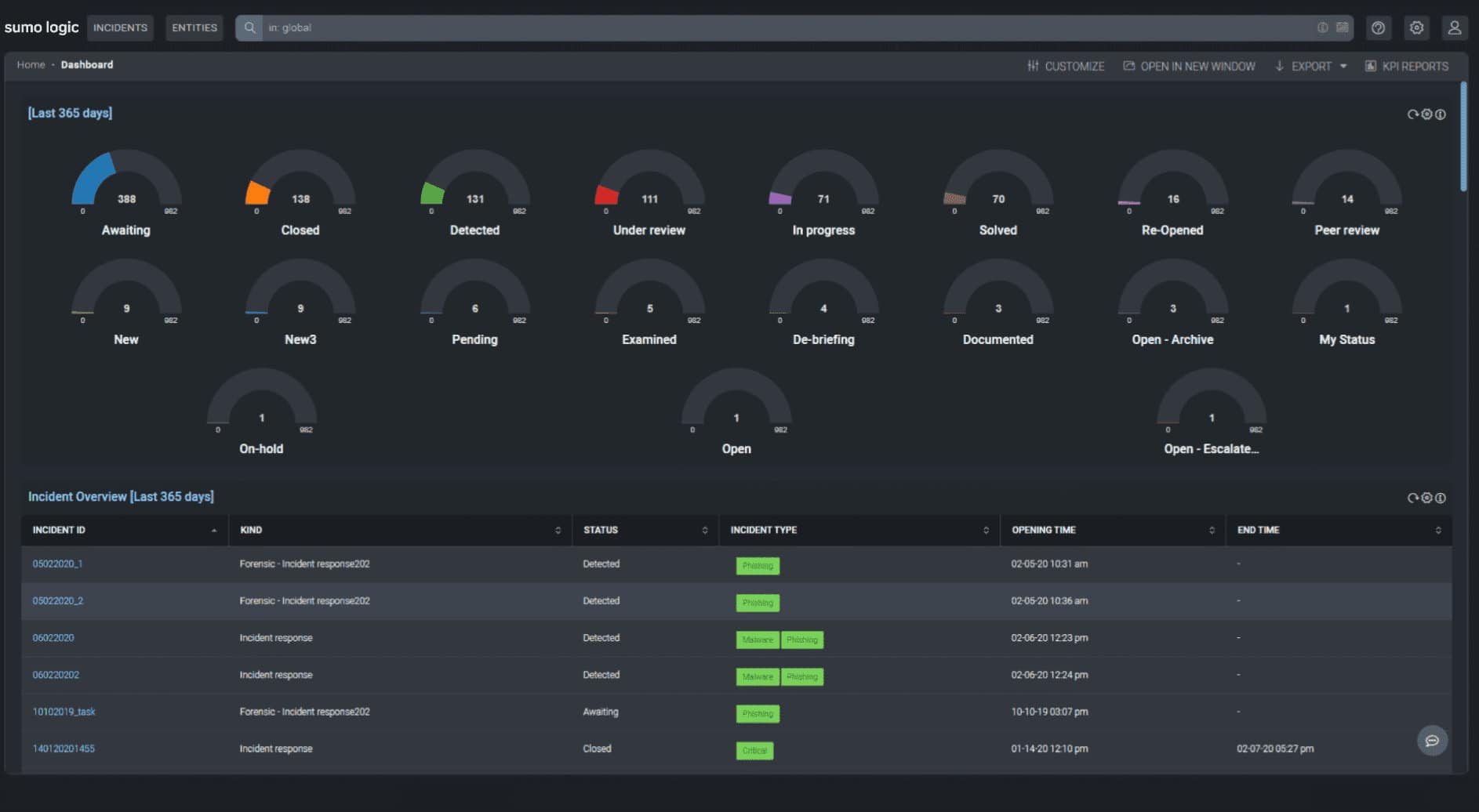
DFLabs IncMan is another trusted tool that helps measure security operations and automates orchestration to improve the overall performance of your SOC. It supports several customizable playbooks for different threat scenarios and manages incidents in less time.
Key Features
- Disaster Recovery
- Investigation Management
- Corrective and Preventive Actions (CAPA)
- Incident Management and Reporting
- Workflow Automation
- View historical incidents
- Customizable Dashboards
- Threat containment
- 100+ customizable playbooks
- Threat reporting
- Supports customizable KPI and reporting templates
Why do we recommend it?
DFLabs IncMan stands out for its robust orchestration capabilities and the breadth of its customizable playbooks for different threat scenarios. Its ability to track, predict, and visualize cybersecurity incidents quickly makes it an invaluable asset for improving SOC performance.
Most companies choose DFLabs IncMan over other tools for it has the capability to assess, investigate, hunt threats and share knowledge within the SOC team. Also, it helps reduce the security complexities.
With the help of this centralized and automated SOAR solution, the business can track, predict and visualize cyber security incidents in less time and measure operational performance and cyber risk across different stages.
Who is it recommended for?
This tool is ideal for businesses that need a centralized and automated SOAR solution capable of coordinating complex threat investigations and incident management. Companies that value customizable dashboards, KPI tracking, and easy third-party integrations will find DFLabs IncMan especially beneficial.
Pros:
- DFLabs IncMan is easy to implement, customize and integrate
- Helps measure security ops and incident response
- Offers complete visibility
- Allows admins to prioritize responses
- Supports several third-party security and threat intelligence sources
Cons:
- 24/7 support service is not available
6. Splunk Phantom
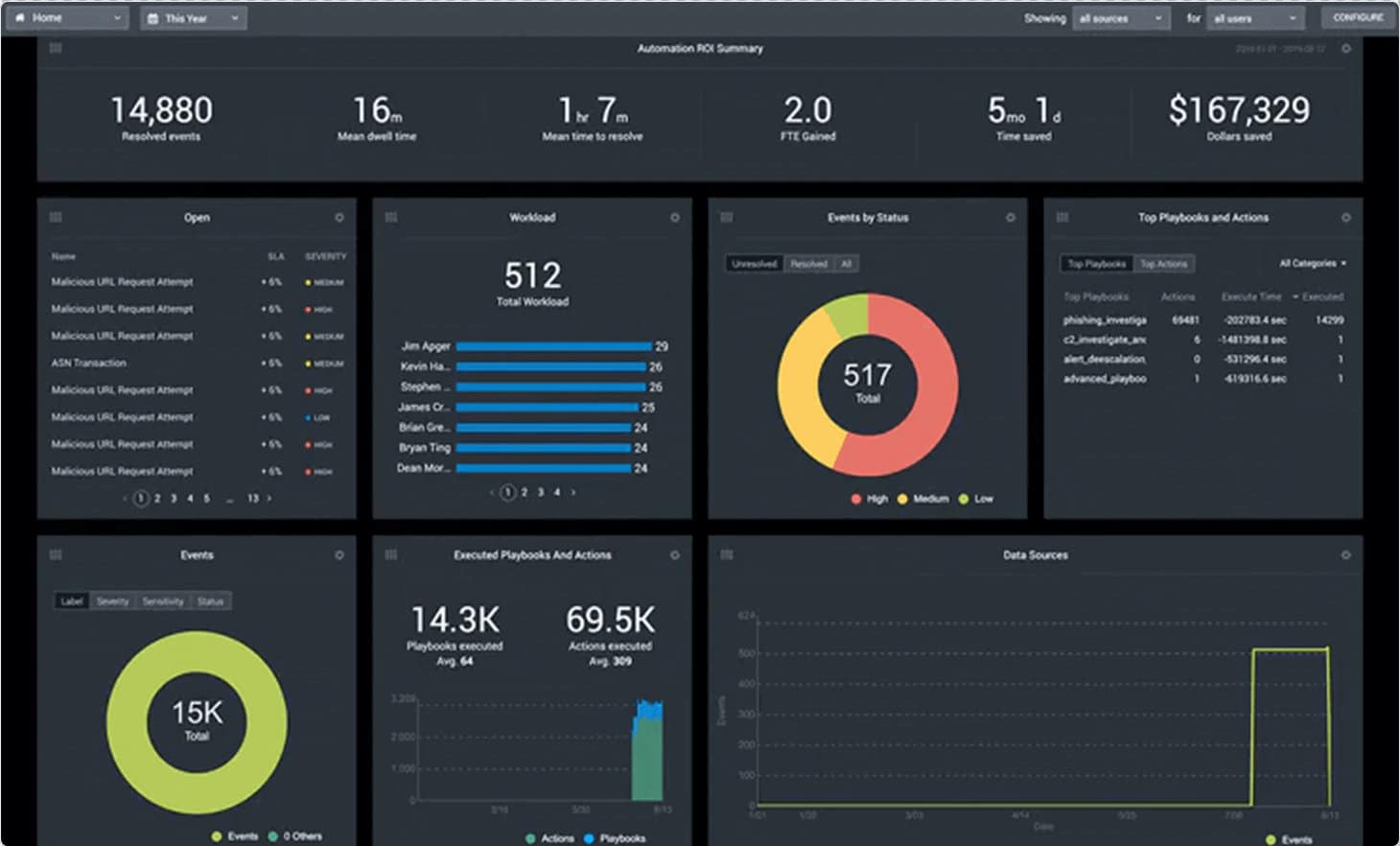
Splunk Phantom is a Security Orchestration, Automation, and Response (SOAR) software that supports various tools that help in the quick detection of internal and external threats. It also helps the team gain better insights and respond faster.
Key Features
- Data filtering
- Team collaboration
- Real-time decision making
- Custom automation processes
- Quickly addresses incidents
- Offers Centralized visualization
- Visual editors
- Supports Event per day (EPD) feature
Why do we recommend it?
Splunk Phantom distinguishes itself with its advanced orchestration, automation, and response capabilities. The platform is highly flexible and scalable, offering end-to-end data coverage and real-time analytics-driven insights, which help in quick threat detection and response.
Further, the popular tools comprise a visual playbook editor (VPE) that helps construct comprehensive playbooks. It also supports other capabilities that aid in automating repetitive security tasks and delivering quick responses to threats.
It is a flexible and scalable platform that provides end-to-end data coverage and visibility across hybrid and multi-cloud environments. As a result, the security analysts need to spend less time combining data and more on performing actions.
Who is it recommended for?
Splunk Phantom is well-suited for organizations seeking a comprehensive SOAR solution that can seamlessly integrate with other apps and tools. It’s particularly beneficial for teams that need to focus more on action-taking rather than data consolidation and for businesses looking to modernize their security operations across hybrid and multi-cloud environments.
Pros:
- The dashboard highlights all notable events, playbooks, security tools, workloads, etc.
- Supports integration with other apps
- Supports advanced orchestration, automation, and response capabilities
- Allows executing automated actions in seconds
- Modernizes your security operations
- Offers unified security posture across different environments
- Offers End-to-end data coverage
- Flexible and provides real-time access to analytics-driven insights
- Helps reduce downtime
- Strengthens cyber defense and lower the risk of fraud and data breach
Cons:
- Lacks simulation features
- Not easy to navigate
7. LogRhythm RespondX
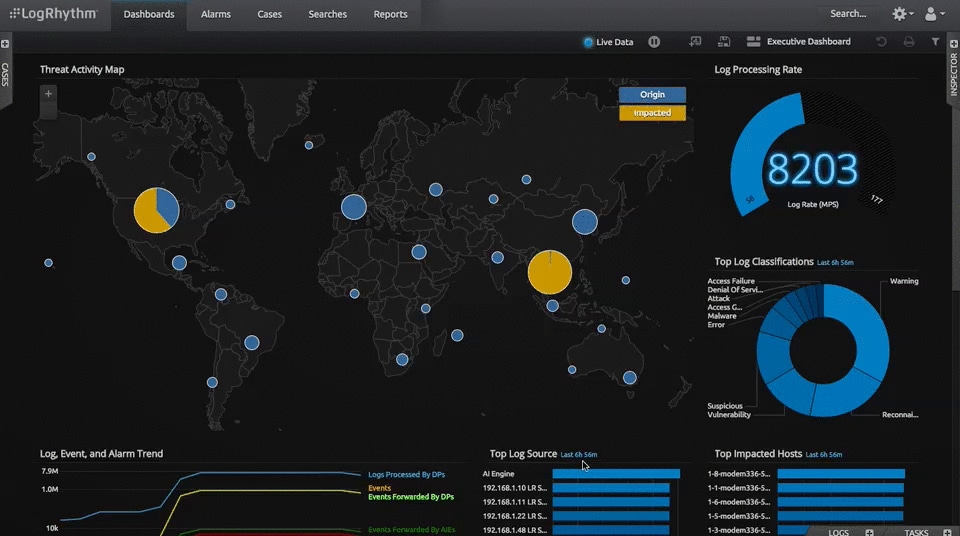
LogRhythm is another SOAR solution trusted by many companies for it helps streamline the investigation and mitigation of threats. Further, it reduces the burden on your team members and encourages them to communicate and collaborate well.
Key Features
- SmartResponse automation
- Case Metrics and Management
- Playbooks
- Supports Contextualization
- File integrity monitoring
- Endpoint monitoring
- Reporting
- Prioritize events and workflow tasks
Why do we recommend it?
LogRhythm RespondX offers a comprehensive set of features including SmartResponse automation and file integrity monitoring, which make it a strong contender in the SOAR space. The platform is also highly customizable and provides real-time insights, helping organizations to effectively prevent threats both on-premises and in the cloud.
LogRhythm is one of the best enterprise-class platforms that supports top tools for security, compliance, and operations and uses machine learning and other techniques to detect advanced threats.
LogRhythm RespondX also allows admins to access useful and actionable insights that update on the current status of the enterprise IT environment. It instantly updates analysts on detecting malware-related registry changes, theft of sensitive data, or other suspicious activities using its file integrity monitoring feature.
The software supports several other features that make it a good choice.
Who is it recommended for?
This tool is an excellent choice for enterprise-level organizations that are looking for a SOAR solution that combines security, compliance, and operations. It’s particularly beneficial for teams that require machine learning-based threat detection, real-time insights, and long-term data storage capabilities.
Pros:
- It is easy to implement simple remediation actions
- It helps prevent threats either on-premises or from the cloud.
- Visually stunning and highly customizable
- Offers real-time insights
- Supports automatic archiving data for long-term storage
Cons:
- Some people find the SOAR solution a bit expensive
8. ServiceNow
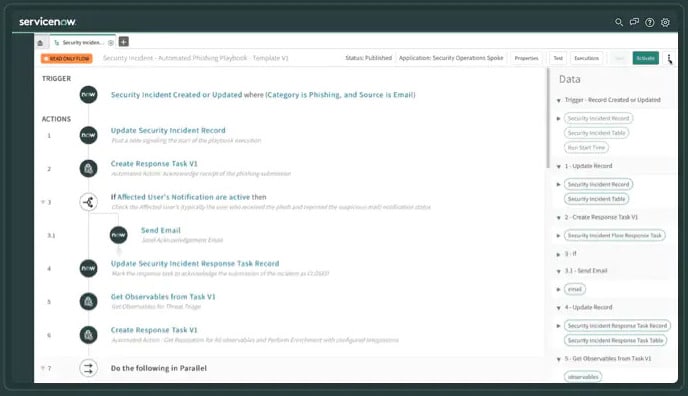
ServiceNow is a successful cloud-based solution that can be purchased as a SaaS platform. It supports several programmed ITSM modules and workflow automation processes. As a result, your team members have to no longer spend their time investigating complex processes manually.
Key Features
- Automated Testing Framework (ATF)
- Process/workflow automation
- Supports programmed ITSM modules
- Machine learning (ML)
- Supports AI-powered chatbots
- Change Advisory Board (CAB) Workbench
Why do we recommend it?
ServiceNow excels in automating routine tasks and streamlining ITSM modules, which significantly cuts down on manual processes and reduces costs. Its machine learning and AI-powered chatbots further enhance productivity and response time.
Further, it makes use of machine learning and other latest technologies to automate routine tasks and improve productivity.
There are many benefits to the tool such as it enables organizations to quickly detect and resolve IT incidents before they cause any major damage and visually tracks automated workflows.
Who is it recommended for?
ServiceNow is ideal for organizations that want a cloud-based, SaaS platform to manage IT service tasks efficiently. It is particularly well-suited for businesses looking to integrate both on-premises systems and cloud-based solutions while minimizing manual effort and paperwork.
Pros:
- Allows admins to track applications and negate risks faster
- No requirement for separate test data
- Eliminates paperwork and manual processes
- Allows integrating on-premises systems and cloud-based solutions
- Troubleshoot and resolve incident tickets quickly
- Reduces cost
- Improves response time
Cons:
- The SOAR solution is expensive
- Users find it difficult to understand the navigation panel
9. IBM Security SOAR
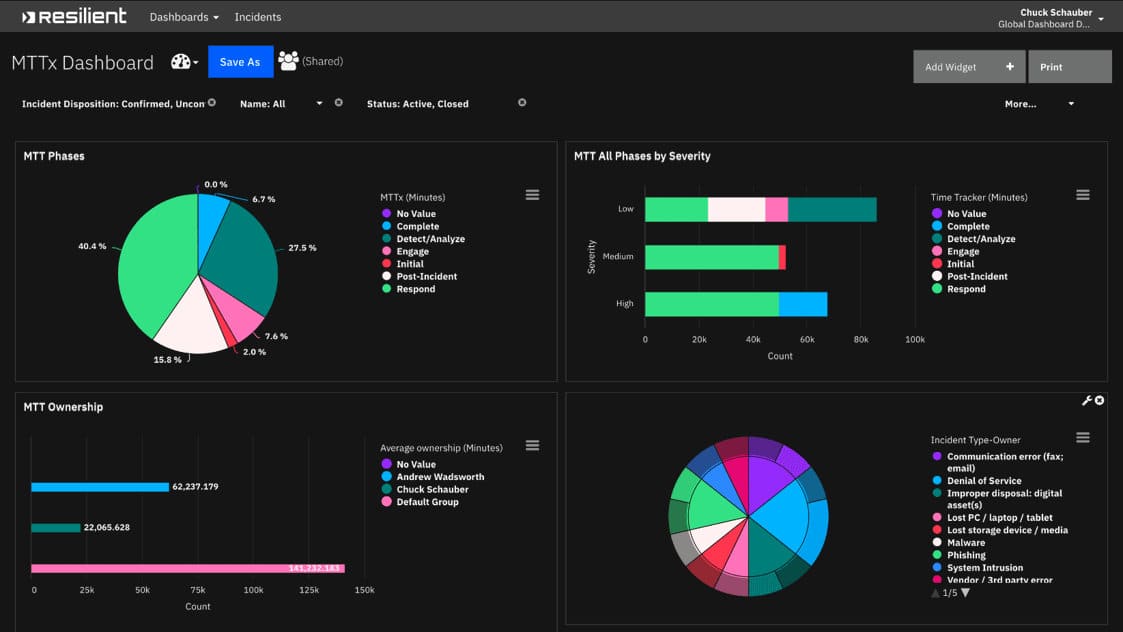
IBM Security SOAR is also a great choice. The SOAR solution helps companies deal with and respond to cyberthreats with confidence. It can be used either on-premises or in a hybrid cloud environment. Also, you can purchase the tool as a SaaS option.
Key Features
- Automates manual tasks
- Orchestrate and automate response
- Supports customizable playbooks
- Quick deployments
- Integrates seamlessly with existing tools
Why do we recommend it?
IBM Security SOAR stands out for its focus on automating manual tasks and offering customizable playbooks, allowing IT teams to concentrate on more strategic objectives. The tool’s seamless integration with existing security tools and multiple deployment options make it a versatile choice for threat management.
The main purpose of designing the software was to highlight critical security incidents that need immediate attention and reduce the burden by automating all manual tasks. As a result, your IT teams can focus on other vital areas rather than performing complex investigations.
It also allows admins to visualize data through several topological maps and flow charts. Further, it supports playbooks and multiple deployment options.
Who is it recommended for?
IBM Security SOAR is suitable for organizations seeking a flexible approach to security, whether it be on-premises or in a hybrid cloud environment. It’s ideal for companies that already have a set of security tools in place and are looking to integrate a solution that can automate responses and offer insightful visualizations.
Pros:
- It helps codify existing incident response processes into dynamic playbooks.
- Allows integrating with other security tools.
- Offers visibility into incident progression
- Provides timely alerts and notifications
- Establishes a support hub that prepares your team for and respond to privacy breaches
Cons:
- IBM Security SOAR takes time to deploy integrations.
Final Thoughts
Applications with multiple entry points are more prone to security vulnerabilities. Also, the ones with large workloads demand automation processes as modern networks are too diverse and complex which makes it difficult for analysts to manage everything manually.
As a result, companies look for tools and solutions that save them from such vulnerabilities in real-time and support automation workload processes. SOAR software is an automation solution that suits best here.
These are a collection of Security Orchestration and Automation (SOA), Threat Intelligence Platforms (TIP), and Incident Response Platforms (IRPs) that automate the process of data collection and manage threats in real-time. With the help of these tools, organizations can detect and respond to security threats faster.
It uses threat intelligence and AI to improve a user’s response to threats. Look at the three main components of the SOAR solution to figure out how it works and can be useful for your organization.
Further, we have shortlisted some of the best SOAR software that can automate workload processes and make your network monitoring more efficient and safe from threats.
ManageEngine Vulnerability Manager Plus, Rapid7 Insightconnect, Siemplify, Cyberbit, DFLabs IncMan, Splunk Phantom, LogRhythm RespondX, ServiceNow, and IBM Security SOAR are a few popular Security Orchestration, Automation, and Response (SOAR) software that helps streamline the investigation and mitigation of threats.
Compare each SOAR solution and then make a final call for your business security.
SOAR Software FAQs
What are three key SOAR drivers?
Security Orchestration and Automation (SOAR) is a process that automates security operations. It's a continuous process that requires the three key drivers of SOAR to be in place. The first is security orchestration, i.e., collecting information from multiple sources, identifying the assets and target environment, and defining the protection requirements. The second key SOAR driver is automation which focuses on eliminating manual tasks. The automation component is to design and implement an automated security operation model. Lastly, the third key SOAR driver is the response, i.e., it ensures that the user reacts to security events effectively. The third pillar's main role is to monitor and tune the automated security operations model in order to meet any changes in the environment or assets. Under this model, users run root-cause diagnoses, and manage and respond to threats in real time.
Is SOAR better than SIEM?
Security Information and Event Management (SIEM) is a system that monitors and analyzes security-related events from multiple sources, including firewalls, intrusion detection systems, operating systems, applications, network devices, and more. SIEMs are often used for compliance purposes. SOAR is a system that manages the response to an incident or event. It's designed to coordinate with other systems such as SIEMs to provide a unified view of the situation. SOARs can also be used for compliance purposes. The main difference between these two types of security tools is how they are used in response to an event or attack. SOARs are designed to coordinate with other tools such as SIEMs while SIEMs are not designed to work with other tools on the same level as SOARs.
Can you have SOAR without SIEM?
Organizations are always looking for a new ways to improve their security. One of the most popular ways is to implement SIEM. SIEMs can provide organizations with a better understanding of their security risks, but they cannot provide all the necessary tools and functions. SOAR provides organizations with the tools they need in order to better protect themselves from cyber threats. SOAR is not a replacement for SIEM, but it complements it in many ways. But even if you have SIEM, the SOAR tool will collect alerts from other sources, such as email security, cloud security tools, EDR, etc. Hence, SOAR can work without SIEM as many use cases begin from the other alert sources.
What is the main purpose of SOAR?
SOAR is a framework for developing AI systems that are able to learn from experience and develop new strategies for solving problems. The SOAR model was developed to collect data from different sources and view them from a single location. It is a very powerful framework for designing intelligent systems, which has been used in many areas of artificial intelligence research. The main purpose of SOAR is to enable machines to learn from experience and develop new strategies for solving problems.




