IT Security is a word that we keep hearing often as it encompasses a wide variety of systems, devices, networks, and a company’s IT infrastructure as a whole. In reality, though, this word is more talked about than implemented as is evident from the 2021 Cybersecurity Report that states that 21 % of files are not protected at all, 70% of organizations believe that their security risk has increased significantly, and 41% of companies have more than 1,000 unprotected files containing sensitive information.
Well, the statistics can go, but the underlying fact is that security is not as widely implemented as we believe. In particular, not a lot of effort goes into protecting files, and many times, these become the destination of hackers.
Here is our list of the Top File Integrity Monitoring Tools:
- SolarWinds Security Event Manager – FREE TRIAL A comprehensive file integrity monitoring tool that continuously monitors your system to detect any suspicious activities and helps you to respond to them at the earliest. Get a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL An on-premises compliance package that logs user activity on files and within Active Directory instances. Runs on Windows Server. Access a 30-day free trial.
- ManageEngine EventLog Analyzer – FREE TRIAL Comes with in-depth analytical capabilities to continuously monitor your resources and to point out anomalies at the earliest. Access a 30-day free trial.
- Datadog Security and Compliance Monitoring Addresses governance, risk, and compliance within your organization by automating audits, collecting logs and data, and ensuring compliance with existing standards.
- CrowdStrike Falcon FileVantage A file integrity package that is part of a SaaS platform of system protection tools and can be combined with other services.
- Netwrix Auditor Detects security threats, enhances compliance, points to the root cause, and enhances the overall efficiency of your organization.
- OSSEC A free and open-source intrusion detection software that analyzes logs, checks file integrity, monitors the Windows registry, sends alerts when needed, and more.
- Samhain File Integrity A comprehensive file integrity checking and log monitoring and analytics software that can give insights into the unauthorized access of your files.
- Qualys FIM Logs and tracks file changes across your entire infrastructure.
- Trustwave Endpoint Protection A cloud-based solution that delivers anti-malware, file integrity monitoring, compliance management, policy enforcement, and more.
- Tripwire File Integrity Monitor Continuously monitors your files for changes and any other suspicious activities, and the same is reported, so you can take the required action.
To prevent your files from becoming potential hacking targets, consider using file integrity monitoring tools. As the name suggests, these tools monitor and detect changes in files to indicate a possible cyberattack or even a vulnerability that can open the floodgates to potential hackers.
The best File Integrity monitoring tools
- Does it support integration and records all file access operations?
- Does it allow encrypting files containing sensitive data?
- Detects malware and other threats in real-time?
With these selection criteria in mind, we have defined a list of suitable File Integrity Monitoring Tools.
Let’s now take a deeper look at the features and pricing of these tools to help you identify the appropriate one that best meets your needs.
1. SolarWinds Security Event Manager – FREE TRIAL
Security Event Manager from SolarWinds is a comprehensive file integrity monitoring tool that continuously monitors your system to detect any suspicious activities and helps you to respond to them at the earliest. Its extensive features and its high compliance rates to existing industry standards enable you to focus on the core aspects of your business with the confidence that even the smallest anomaly will be brought to your notice.
Key Features
Here’s a look at the features of SolarWinds’ Security Event Manager.
- Comes with the advanced pfSense reporting and analysis tool to provide continuous monitoring
- Keeps track of logon and logoff events through its centralized login manager
- Automates risk management, and in the process, improves your compliance with existing standards
- Provides real-time situational awareness to minor for threats and attacks from bots
- Its centralized log management gives complete and streamlined control to your logs
- Gives actionable insights for you to take quick action
- Collects data and correlates it with your environment to give a holistic view of your infrastructure’s security
- Uses cyber threat analysis tools
- Its in-memory correlation capabilities are designed to prevent cross-site scripting attacks
- Monitors traffic from different sources to prevent DDoS attacks
- Protects your database from SQL Injection attacks
- Detects intrusions in real-time
- Simplifies firewall and routing security auditing
Why do we recommend it?
We recommend SolarWinds Security Event Manager for its robust and continuous monitoring capabilities, which include everything from pfSense reporting to real-time intrusion detection. With its high compliance rates and automated risk management, it stands out as a comprehensive solution for enterprise security.
Who is it recommended for?
This tool is recommended for IT security professionals and system administrators who are responsible for overseeing a complex IT infrastructure. Its extensive features make it particularly useful for businesses that need to adhere to stringent compliance standards, and those looking for an all-inclusive tool for real-time threat detection and response.
Pros:
- Constantly monitors devices and updates on detecting suspicious activities
- Uses centralized login manager to watch over logon as well as logoff events
- Performs Azure AD logs auditing
- Reduces cross-site scripting threat risk
- Detects malware threats using a file integrity checker
Cons:
- Uses FIM only for log files
It starts from $2,613. Click here to download a fully functional 30-day free trial.
2. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is an activity tracking system that protects files and also operates logging for changes to Active Directory instances. This system includes facilities for compliance auditing and includes compliance report templates. The tool is also able to identify user behavior.
Key Features
Some of the important features of ADAudit Plus are:
- Activity tracking, creating user profiles
- Compliance auditing for GDPR, GLBA, SOX, PCI DSS, FISMA, and HIPAA
- Compliance reports for data privacy standards
- Monitoring for account takeover and insider threats
- Identification of brute force credentials cracking attempts
- Protection against ransomware
- Anomalous behavior identification
- Alerts and notifications
- Option to feed records into a third-party SIEM
- Runs on Windows Server
Why do we recommend it?
We recommend ManageEngine ADAudit Plus for its advanced features in compliance auditing and activity tracking. The tool excels in monitoring for various types of threats, including insider threats and brute force attempts, making it a reliable choice for safeguarding your Active Directory instances.
Who is it recommended for?
ManageEngine ADAudit Plus is ideal for IT security teams and compliance officers who need to ensure the integrity of their Active Directory environments. With its specialized compliance reports and templates, it is especially useful for organizations that have to comply with GDPR, GLBA, SOX, PCI DSS, FISMA, or HIPAA standards.
Pros:
- Offers compliance auditing and report templates
- You can create user profiles and track activities
- Identifies anomalous behavior
- Set alerts for unauthorized access
- Supports running on Windows Server
Cons:
- Sensitive data files are not locked using encryption
ManageEngine doesn’t publish a price list, so you have to contact the Sales Department and request a quote. Start a 30-day free trial.
3. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine’s EventLog Analyzer continuously monitors your files and systems to identify potential threats, so they can be fixed before they turn into attacks. It also comes with advanced auditing and IT compliance features.
Key Features
Some of the important features of EventLog Analyzer are:
- Provides end-to-end log management for comprehensive insights
- Comes with both agent-based and agentless ways of log collection, parsing, analysis, reporting, and more
- Has flexible log archiving options
- Makes it easy to audit all critical resources
- Generates reports in predefined formats to meet different business needs
- Helps you to comply with a wide range of regulatory policies
- Advanced features such as log forensics and threat intelligence help with quick vulnerability detection
- The dashboard and console are highly intuitive
- The enhanced correlation interface has more than 30 predefined attack rules to match the sophisticated strategies of hackers.
- Provides real-time alerts for suspicious traffic and access
- Tracks the response and resolution aspects
- Handles cross-platform audit
Why do we recommend it?
We recommend ManageEngine EventLog Analyzer for its robust log management capabilities and real-time threat detection features. With both agent-based and agentless log collection methods, as well as predefined reporting formats, it offers a comprehensive solution for IT compliance and auditing.
Who is it recommended for?
This tool is recommended for IT security professionals, compliance officers, and system administrators who need a robust, end-to-end log management system. Its advanced features like log forensics and threat intelligence make it particularly suitable for organizations requiring immediate vulnerability detection and those that need to comply with various regulatory policies.
Pros:
- Tracks all files and identifies potential threats in real-time
- Provides full log management for in-depth views
- Run an audit on all crucial resources
- Produces insightful reports in predefined formats
- Notifies on detecting suspicious access or traffic
Cons:
- Limited scalability and automation require improvement
Contact the support team for a custom quote. Start a 30-day free trial.
4. Datadog Security and Compliance Monitoring
Cloud environments are complex, to say the least, hence Datadog’s Security and Compliance Monitoring tool can be the one tool that can avoid serious data breaches in your cloud-based applications. It makes it easy to track the compliance levels within your organization, automate audits, and even catch errors such as misconfigurations to help your organization to stay protected at all times.
Key Features
Some of the important features of Datadog Security and Compliance Monitoring are described below.
- Detects threats in real time with turnkey threat detection rules.
- Continuously monitors and collects information from logs to identify anomalies at the earliest.
- Correlates and investigates issues to give you insights into the possible root cause of the problem.
- Catches misconfigurations right away, and helps to prioritize and remediate the same
- Enriches raw data with threat intelligence to give you the right context for meaningful actions
- Comes with expert dashboards to give a single pane of information for you
- Deploys production-ready file integrity monitoring capabilities
- Monitors cloud-native stacks, traces, container, and Kubernetes configurations, logs, workloads, and cloud resources to give a comprehensive idea of the state of security.
- Detects drifts from critical compliance controls
Why do we recommend it?
We recommend Datadog Security and Compliance Monitoring for its exceptional capability to manage the complexities of cloud environments. The tool excels in real-time threat detection, catching misconfigurations, and providing end-to-end visibility, making it a standout solution for maintaining cloud security.
Who is it recommended for?
This tool is ideal for IT security teams, cloud administrators, and compliance officers working in cloud-native or hybrid-cloud environments. Its comprehensive monitoring of cloud stacks, containers, and Kubernetes configurations makes it especially useful for organizations that require a holistic view of their cloud security posture.
Pros:
- Identifies misconfigurations that might put your security at risk
- End-to-end visibility
- Raises alerts right away
- Notifies about potential threats
- Custom governance policies
Cons:
- Gets expensive as it scales
- Complex log analytics process
There are three plans to choose from – Free, Pro ($15 per host per month), and Enterprise ($23 per host per month). You can add-on to these plans at an additional cost. Click here to start a 14-day free trial.
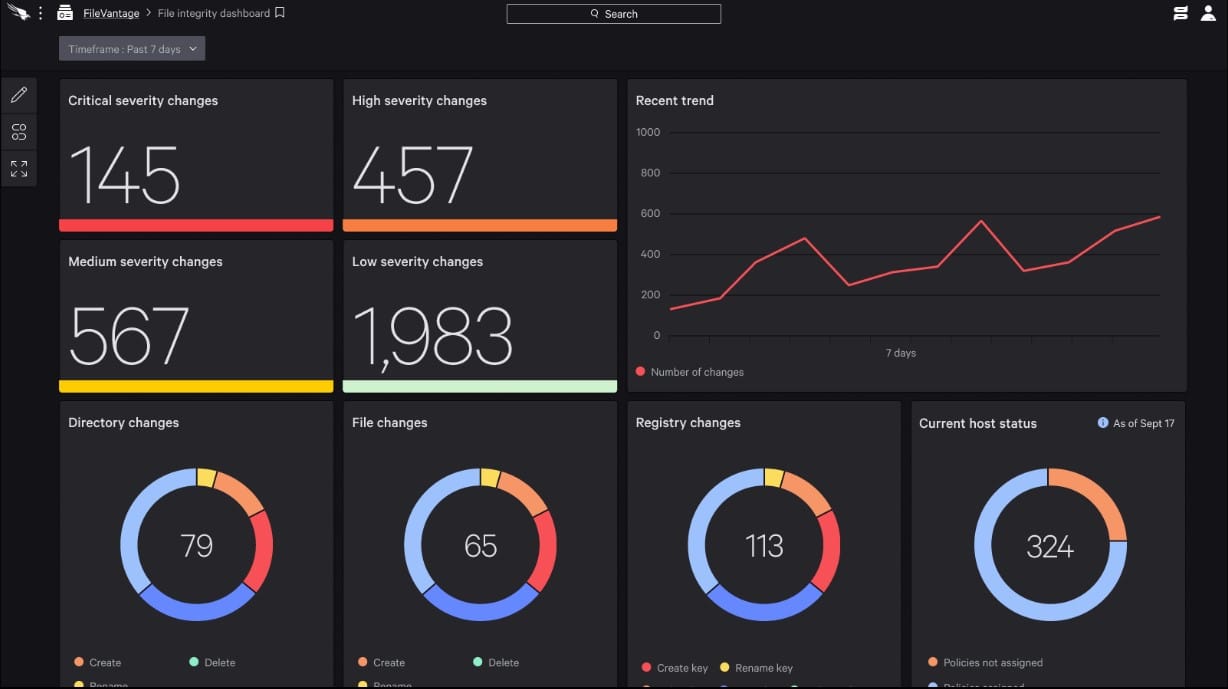
5. CrowdStrike Falcon FileVantage
CrowdStrike Falcon FileVantage is an activity logging system that focuses on changes to files. The service is part of the Falcon family of cybersecurity systems and it can be subscribed to in combination with other tools. For example, CrowdStrike offers a threat intelligence system, called Falcon X, and that will enhance the efficacy of the FileVantage unit by focusing on files that are currently the main targets of hacker campaigns.
Key Features
Some of the most important features of the CrowdStrike Falcon FileVantage service are listed below.
- Compliance with PCI DSS, CIS, and SOX
- A security policy creation system that helps you narrow down the files that are to be monitored
- The option of a threat intelligence feed that identifies types of files that need to be monitored
- A cloud-based dashboard that can be accessed from anywhere through any standard Web browser
- The ability to monitor servers in multiple locations, allowing security monitoring to be centralized
- A summary of activities that shows constantly updated statistics on file activities
- The choice over how to manage alerts
- Logging of each change action on a file, including a timestamp and the user account involved
- The option to feed file activity logs into a SIEM or an XDR
Why do we recommend it?
We recommend CrowdStrike Falcon FileVantage for its specialized focus on file activity monitoring and its seamless integration with other cybersecurity tools like Falcon X. Its compliance features and threat intelligence feed make it a robust solution for identifying and mitigating file-based threats.
Who is it recommended for?
CrowdStrike Falcon FileVantage is particularly beneficial for cybersecurity teams and compliance officers who need granular control over file activities. The service is ideal for organizations that need to adhere to PCI DSS, CIS, and SOX compliance standards and are looking for a centralized, cloud-based monitoring solution.
Pros:
- Tracks all file activities
- Integrates with other systems
- Provides threat intelligence feed
- Ensures compliance with PCI DSS
- Displays activity stats on the dashboard screen
Cons:
- Navigation is a bit tricky
- You can export reports in CSV or JSON format that is not visual
CrowdStrike doesn’t publish a price list, so you need to contact the Sales Department to get a quote. You can start with a 15-day free trial. CrowdStrike Falcon FileVantage is a SaaS package so there is no download.
6. Netwrix Auditor
Netwrix Auditor is an IT monitoring tool that monitors your files, systems, and other aspects of your infrastructure to detect anomalies, identify threats, and increase compliance. Through it all, this tool strives to improve the overall efficiency of the organization.
Key Features
Some of the salient features of Netwrix Auditor are as follows:
- Reduces the risk to critical assets by continuously monitoring them
- Identifies security gaps, uncontrolled access, and other potential vulnerabilities in the system
- Sets up alerts through automation to ensure that these issues are brought to your notice for mitigation
- Offers a centralized platform for auditing all IT systems
- Collects information from the cloud, hybrid, and on-prem systems to give you a comprehensive view of security in your infrastructure
- Supports a ton of platforms and operating systems
- Automates the process of data discovery and classification
- Improves the overall speed and quality of your decisions with the right information
Why do we recommend it?
We recommend Netwrix Auditor for its comprehensive IT monitoring capabilities that span across cloud, hybrid, and on-premises systems. The tool excels in automated alerting for vulnerabilities and offers a centralized platform for auditing, making it indispensable for maintaining a secure and compliant IT environment.
Who is it recommended for?
Netwrix Auditor is recommended for IT security professionals, system administrators, and compliance officers who require a unified view of their IT infrastructure. It’s particularly useful for organizations that operate across multiple platforms and need automated alerting and remediation features to maintain a secure and efficient system.
Pros:
- Detects security threats
- Identifies gaps in your monitoring
- Identifies threat patterns and raises alerts
- Performs detailed audit trails
- Automated remediation via scripts
Cons:
- It would be nice to have longer trial periods
- Intuitive alerting could be improved
Contact the sales team for a custom quote. Click here for a 20-day free trial.
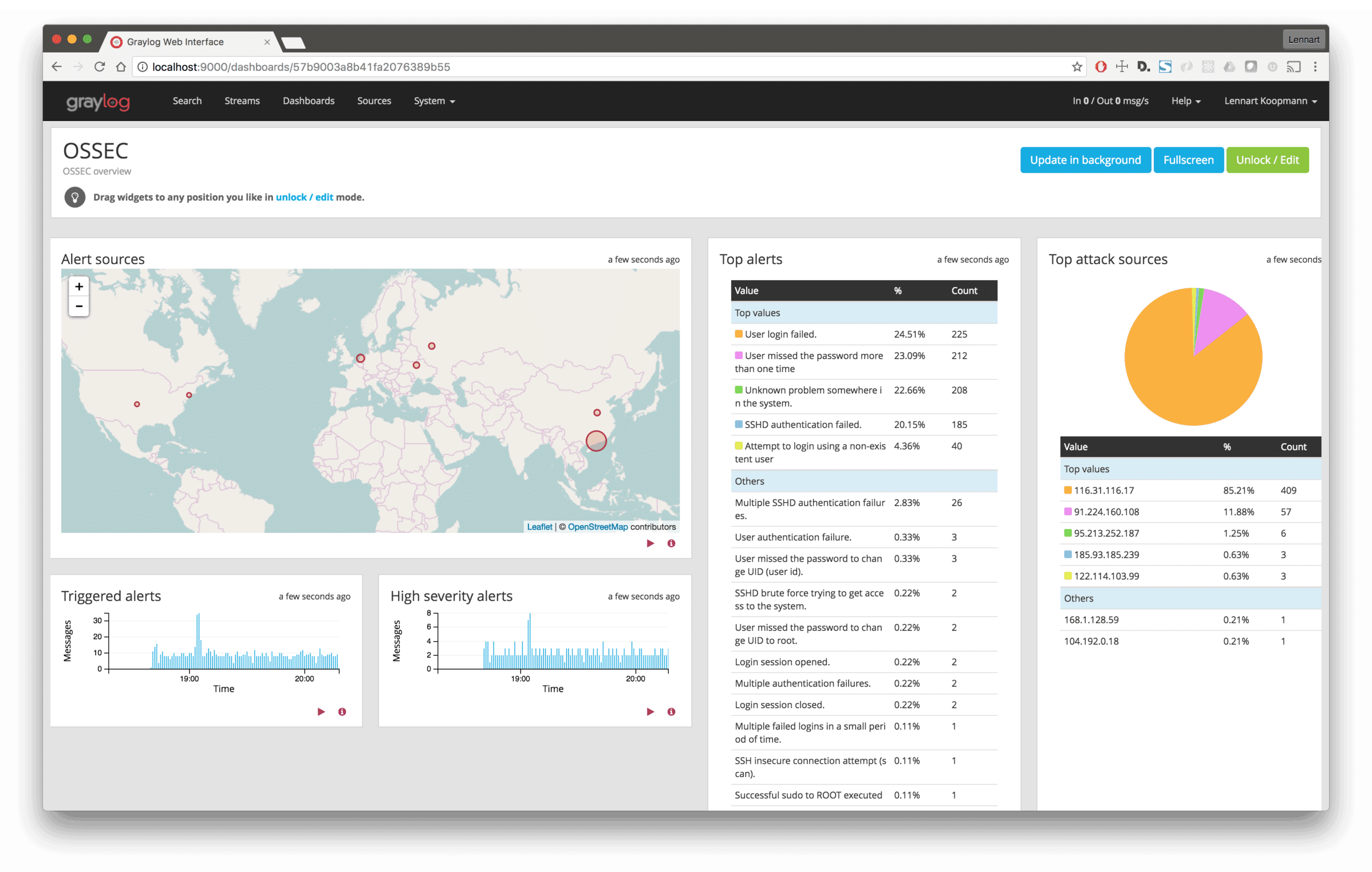
7. OSSEC
OSSEC is an open-source intrusion detection system that can be configured to meet your specific needs. It comes with extensive capabilities to analyze your logs, check for file integrity, monitor the Windows registry, and more.
Key Features
Here’s a look at some of the features of OSSEC.
- Gives the option to add custom rules when needed to extend the platform’s offerings and to customize them to meet your requirements
- Works across multiple platforms such as Windows, Mac, Linux, BSD, and more
- Helps to meet specific compliance requirements
- Detects and alerts unauthorized file system modifications
- Identifies malicious behavior and brings them to your notice
- Has an extensive community that can provide answers to your questions
Why do we recommend it?
We recommend OSSEC for its high flexibility and extensive configuration options, including the ability to add custom rules to meet specific requirements. Its cross-platform compatibility and active community support make it a versatile intrusion detection system.
Who is it recommended for?
OSSEC is suitable for businesses of all sizes that prioritize intrusion detection and customizable security solutions. It is especially useful for IT administrators and security analysts who work with diverse operating systems and need to meet specific compliance requirements.
Pros:
- Offers extensive configuration options
- You can add custom rules and scripts
- Works smoothly on multiple platforms
- Raises alert on detecting unauthorized file system changes
- Real-time community threat sharing
Cons:
- Relies on the community for support and assistance
- Visualization features could be improved
OSSEC is 100% FREE, and you can contribute voluntarily if you wish. Click here to download OSSEC.
8. Samhain File Integrity
Samhain File Integrity System is a host-based intrusion detection system that comes with advanced capabilities for checking file integrity and monitoring the logs.
Key Features
Here’s what Samhain File Integrity offers for your business:
- Detects rootkits
- Monitors ports and hosts across different operating systems
- Identifies rogue SUID executables, hidden processes, and other malicious behavior
- Provides centralized logging and maintenance
- Can be used as a standalone host as well
- Comes with a web-based Beltane console that monitors both client and server activities
- Supports multiple logging choices
- Offers a PGP-signed database and configuration files
- Comes with a stealth mode as well
- File checking can be scheduled at any time
Why do we recommend it?
We recommend Samhain File Integrity for its comprehensive set of features that go beyond basic file integrity checks to include rootkit detection and centralized logging. The system’s ability to schedule file checks and operate in stealth mode sets it apart from the competition.
Who is it recommended for?
Samhain File Integrity is ideal for businesses that require advanced intrusion detection capabilities and centralized control. It’s well-suited for IT security professionals who need a robust, customizable solution for monitoring both client and server activities across various operating systems.
Pros:
- Helps monitor client and server activity
- Identifies malicious behavior in real-time
- Schedule file checking at any time
- Offers stealth mode
- Offers centralized logging feature
Cons:
- Outdated and challenging interface
- Does not have a strong community
Pricing: 100% FREE
Click here to download Samhain File Integrity System.
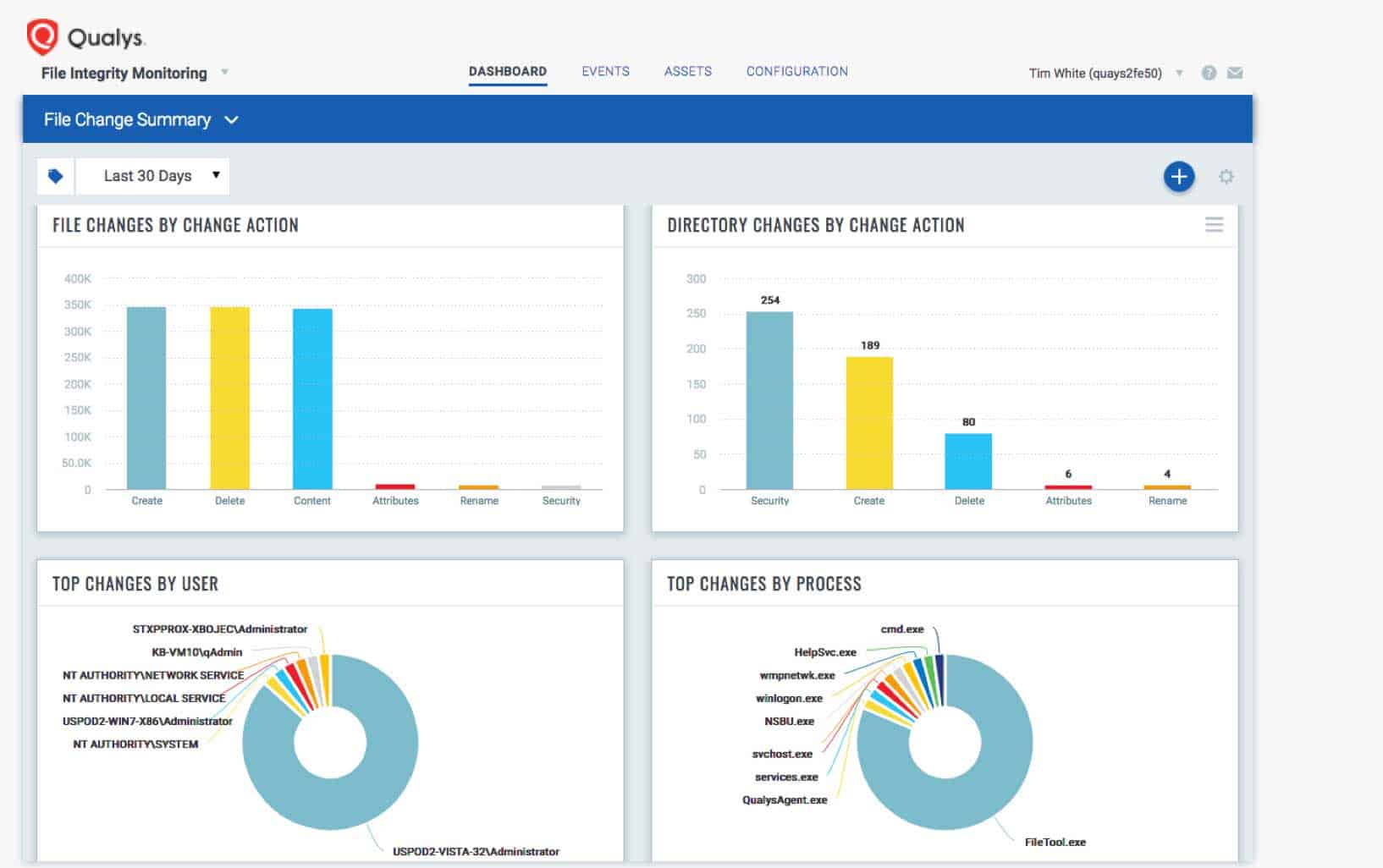
9. Qualys FIM
File Integrity Monitoring from Qualys comes with many out-of-the-box profiles to make it easy for you to log and track changes made to any file across the entire infrastructure.
Key Features
The features of Qualys FIM are as follows:
- Logs and tracks changes to any file across the entire global infrastructure
- Detects and identifies critical risks that come from normal and malicious events
- Comes without-the-box profiles that make auditing easy
- Continuously monitors files and directories to critically review what has been changed and by whom
- Handles system located on-prem and in the cloud
- Has a scalable architecture that can grow with your business
- The Qualys Cloud Agent provides unified security for the file integrity monitor
- Detects changes in real-time with kernel signals
- Sends notifications when new files or directories are created, existing ones are removed or renamed, changes are made to file attributes, data, or security settings
- Collects critical data for in-depth investigation
- Lightweight and versatile, so easy to use and can be installed anywhere.
Why do we recommend it?
We recommend Qualys FIM for its robust real-time monitoring and flexibility in handling both on-premises and cloud environments. Its out-of-the-box profiles simplify auditing, and its scalable architecture ensures it will grow with your business.
Who is it recommended for?
Qualys FIM is suitable for organizations of all sizes looking for a comprehensive and flexible file integrity monitoring solution. It’s particularly useful for businesses that operate in mixed environments, combining on-premises and cloud infrastructures, and require real-time, actionable insights for securing their files.
Pros:
- Identifies risks that might occur from normal or malicious events
- You can install Qualys FIM from anywhere
- Uses kernel signals to identify changes in real-time
- Collects and sends critical events to Qualys Cloud Platform for evaluation
- Adapts well to various on-premises and cloud settings
Cons:
- Not a great solution for small networks
- Ineffective scan efforts led to confusion or application outages
Contact the sales team for a custom quote. Click here for a 30-day free trial
10. Trustwave Endpoint Protection
Trustwave Endpoint Protection is a cloud-based solution that aims to protect your organization’s endpoints from malware, malicious attacks, and other types of attacks. It also ensures compliance with leading standards.
Key Features
The features of Trustwave Endpoint Protection are:
- Simplifies log management and lowers operational costs
- Covers a wide range of devices including laptops and desktops
- Provides real-time protection against possible malware attacks
- Collects and centrally stores logs for compliance and security audit
- Offers endpoint correlation and detailed analysis
- Continuously monitors file data changes
- Gives 360-degree visibility of changes in your infrastructure.
Why do we recommend it?
We recommend Trustwave Endpoint Protection for its comprehensive, real-time protection against malware and malicious attacks. The tool’s ability to simplify log management while reducing operational costs is particularly commendable.
Who is it recommended for?
This tool is ideal for organizations that require robust endpoint security without the complexity. It’s especially useful for businesses that need to maintain compliance standards and want centralized log storage for easy audits.
Pros:
- Protects endpoints against malicious attacks
- Reduces operational costs by simplifying log management
- Offers full visibility and tracks all file data changes
- Examines sensitive file changes and deletions
- Warns users when files and apps have been accessed without their permission
Cons:
- The user must contact the vendor for
- Encryption or data masking is not available
Contact the sales team for a custom quote. At the time of writing this piece, this company doesn’t offer any trials or free downloads.
11. Tripwire
Tripwire’s File Monitoring Solution comes with advanced capabilities to continuously monitor all the files and directories across the entire infrastructure. It assesses, prioritizes, and reports changes, so you can take the necessary actions.
Key Features
Some of the salient features of this tool are:
- Reduces your signal-to-noise ratio, so only the relevant changes are brought to your notice
- Captures extensive details about who changed files and when
- Analyzes changes in your file system to determine your level of security risk
- Helps with compliance to major standards
- Its automated process requires minimal human interference
- Integrates with existing ticketing systems
- Combines well with security configuration management, SIEM, and log management tools
Why do we recommend it?
We recommend Tripwire for its robust, continuous file and directory monitoring across your entire infrastructure. The tool reduces the signal-to-noise ratio, ensuring you only get alerted for relevant changes, which is invaluable for focused security management.
Who is it recommended for?
Tripwire is a great fit for organizations looking to automate their file monitoring processes and reduce manual oversight. It’s particularly useful for companies with ticketing systems, as it integrates seamlessly, allowing for a more efficient security workflow.
Pros:
- Monitors all of the infrastructure’s files and folders on a constant basis
- Enables you to detect only the relevant changes by lowering the signal-to-noise ratio
- Monitors change made to the file system to assess the security risk level
- The automated feature reduces the need for human intervention
- Supports integration with current ticketing systems
Cons:
- Offers a free demo, not the version
- Need to work on the interface
Click here to request a quote. You can request a demo here.
Conclusion
To conclude, file integrity monitoring tools can make it easy to enforce security and compliance within your organization. More importantly, it can help you stay on top of the changes made to your file system by unauthorized users, so you can thwart possible attacks before they happen.
For businesses that manage many critical files, a file integrity monitoring tool can be indispensable. We hope you can identify the appropriate tool for your needs based on the extensive description of the features we have given in this article.