With businesses becoming increasingly digital, there’s a huge rise in hacking and ransomware cyberattacks. These attacks are designed with the purpose of turning the computer systems into an unusable state, and demanding a lump sum value in return. Cybercriminals might have other reasons to break into your system, such as stealing confidential information, exposing all your data, etc.
It is not so easy to find the loophole, decode, and prevent hacking. At times, even an expert with good experience fails to turn the computer systems into a stable state. The inexorable rise of the digital age is very much responsible for an increase in hacking cases.
Even with so many security protocols and encryption techniques, hackers often figure out the loophole and make their move. In order to protect your systems and company data, penetration tests are crucial in helping to probe security weak spots and fix them on time. However, it is not a perfect solution for hacking.
The only way to secure your systems against hacker attacks is to use the white hat hacker practices, also referred to as ethical hacking.
Here, we will discuss ethical hacking, and some of its popular tools that can prove to be exceptionally helpful.
What are Ethical Hacking Tools?
Historically, the term hacker signified experts with knowledge and skills to re-develop mainframe systems. They had the ability to increase efficiency and multi-task. However, today the term hacker defines experts as skilled programmers who gain access to different computer systems without authorized access by exploiting weaknesses or using bugs.
To prevent hackers from fulfilling their purpose, the ethical hacking practice was introduced. It is also referred to as a “white hat” hacking technique that identifies and corrects vulnerabilities in a network.
Under ethical hacking, experts bypass security systems to discover potential threats present in a network. Unlike malicious hacking, it is a legal process where cybersecurity engineers investigate the network and perform activities to spot weak areas and loopholes. Ethical hackers collect data and fix the loopholes that malicious hackers can exploit or destroy.
Today, most companies invest in ethical hacking practices to look into the vulnerabilities of their systems and prevent data breaches.
Is it Legal to Use Hacking Tools?
There are six types of hackers:
- The Ethical Hacker (White Hat)
- Cracker
- Grey Hat
- Script Kiddies
- Hacktivist
- Phreaker
Hacking or penetration tests are mostly performed by a team of highly skilled professionals for research. However, if the same practice is conducted without permission against a company or a person, it is taken as an offense. In fact, there are certain acts introduced by the government that cover hacking offenses and include severe punishment for illegal activities.
Hacking tools can be used, without punishment, only if it fulfills the following conditions:
- The tool is used for only white hat hacking practice.
- The practitioner has legal and secured written permission from the targeted site; the one you are planning to attack.
Make sure you fulfill both conditions or else you’ll have to bear the consequences. Launching a penetration attack without the owner’s knowledge can be offensive, and you might have to go through the legal process.
Our methodology for selecting the best ethical hacking tools
We’ve broken down our analysis for you based on these key criteria:
- Emphasis on diverse vulnerability detection capabilities.
- User-friendly interfaces and easy-to-navigate tools.
- Support for multiple platforms and compatibility with various systems.
- Robust real-time monitoring and alert systems.
- Comprehensive reporting and actionable insights for remediation.
The Best Ethical Hacking Tools
Ethical hackers are professionals who use their hacking skills and knowledge for defensive purposes. They use their strengths to identify and discover vulnerabilities that most attackers target to exploit or break into the system.
Today, one can easily find various tools available in the market for ethical hacking. We have shortlisted the best ethical hacking tools that will help organizations protect their information and systems against professional hackers.
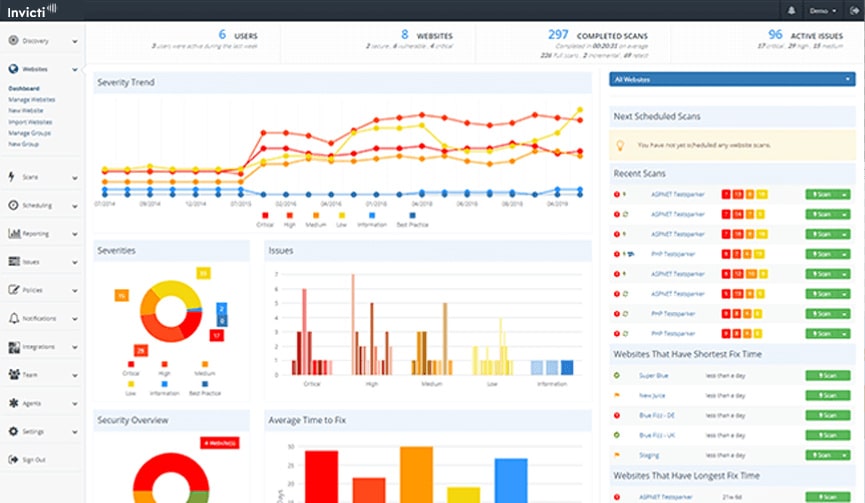
1. Invicti
Invicti is a popular security solution that prevents your web applications from hacking practices. It uses proof-based scanning to discover SQL Injection, Cross-Site Scripting (XSS), and other vulnerabilities. Further, it mimics how hackers work in various languages including, .NET, PHP, etc.
Key Features:
- Saves time by automating security tasks
- Identifies real and false vulnerabilities, then assigns for remediation
- Offers full visibility into web assets
- Supports dynamic + interactive (DAST+IAST) scanning approach
- Updates on remediation efforts status
- Supports behavior-based testing and two-way integrations
- Permission control for unlimited users
- Generates more secure code
- Allows continuous scanning and prevents delays
- Scans and reports zero false positives
- Accessible to users as an online service or Windows software
- Eliminates the manual verification process
- Offers real-time monitoring
- IOC verification
- Risk management
- Vulnerability assessment
- Asset tagging
- Maintenance scheduling
Why do we recommend it?
We recommend Invicti for its comprehensive approach to web application security, including its proof-based scanning that effectively identifies vulnerabilities like SQL Injection and XSS. Its automation capabilities, real-time monitoring, and seamless integration into the SDLC make it a standout solution.
Invicti automates security throughout SDLC and reduces the risk of attacks. It offers full visibility into each web application and web APIs. Furthermore, the tool aids businesses in discovering lost assets. Another benefit of Invicti is it provides real-time monitoring and saves DevOps time by verifying the identified vulnerabilities. If you are looking for an ethical hacking tool that mimics a hacker’s move, look no further.
Who is it recommended for?
Invicti is ideal for organizations that require a robust, automated security solution for their web applications and APIs. It’s especially useful for DevOps teams, as it streamlines vulnerability identification and verification, saving valuable time.
Pros:
- Automates security tasks, saving time.
- Effectively identifies real and false vulnerabilities.
- Provides comprehensive visibility into web assets.
- Offers dynamic and interactive scanning methods.
Cons:
- May be complex for beginners in web security.
EDITOR'S CHOICE
Invicti stands out as our top ethical hacking tool due to its proof-based scanning technology, which accurately identifies vulnerabilities like SQL Injection and XSS. Its unique feature of mimicking hacker tactics across different programming languages, such as .NET and PHP, makes it highly effective. Additionally, its capability to offer full visibility into web assets and provide real-time updates on remediation efforts elevates its status as an indispensable tool for DevOps teams and organizations prioritizing web application security. Invicti is available as an online service or Windows software, catering to a wide range of users.
Download: Get a Demo
Official Site: https://www.invicti.com/plp/ethical-hacking-tools/
OS: Windows, Cloud-Based
2. Acunetix
Acunetix is an automated ethical hacking solution that scans all vulnerabilities like SQL Injection, Cross-site scripting, etc., pinpoints network weaknesses and makes efforts to stand one step ahead of malicious intruders. Further, it provides end-to-end solutions for Windows and serves various agencies and SMEs.
Key Features:
- Access to prioritize high-risk vulnerabilities
- Users can detect multiple vulnerabilities in less time
- Schedule scans
- Extensive reporting facilities
- Provides network alerts against the webserver
- Automatically eliminates false positives
- Scan applications written in code language (JavaScript, .NET framework, and PHP)
- Scans all internal network
- Acunetix is highly compatible with HTML5, JavaScript, and Single-page applications
- Performs audits on all complex applications
- Automatically discovers out-of-band vulnerabilities
- Supports Windows and Linux platforms
Why do we recommend it?
We recommend Acunetix for its advanced scanning capabilities that cover a wide array of vulnerabilities, including SQL Injection and Cross-site scripting. Its automatic Javascript analyzer and compatibility with various code languages make it an excellent choice for complex web applications.
Work through a workflow map and easily manage all security threats in real time with the popular ethical hacking tool. It comprises an automatic Javascript analyzer that helps in testing various Ajax and Web 2.0 application security.
You can also integrate the tool with multiple applications and rectify detected vulnerabilities instantly. Acunetix Web Vulnerability Security Scanner is a great option as one can perform complex audits and scan all HTML5 and Single-page applications.
Who is it recommended for?
Acunetix is best suited for agencies and small to medium-sized enterprises that require comprehensive, automated vulnerability scanning. It’s particularly useful for teams managing complex applications written in multiple code languages and those needing real-time threat management.
Pros:
- Advanced scanning covers a wide array of vulnerabilities.
- Efficient in detecting multiple vulnerabilities quickly.
- High compatibility with various code languages and applications.
Cons:
- Primarily tailored for Windows and Linux, possibly limiting for other OS users.
3. Intruder
The Intruder is one of the proactive ethical hacking tools responsible for identifying and detecting cybersecurity weaknesses in the system. It helps detect vulnerabilities and provides remediation for them.
Key Features:
- Network and Web Scanning
- Patch Management
- Risk Management
- Access Controls
- Asset Discovery
- Prioritize vulnerabilities
- Identifies misconfigurations and other vulnerabilities like cross-site scripting
- Detects SQL Injection
- Integrates with major cloud providers
- Scans systems for the latest vulnerabilities
- Supports 9000+ security checks
- Provides a holistic view of vulnerabilities
- Monitors ongoing attack surface
- Discovers cyber security weaknesses
- Supports Two-Factor Authentication
- Provides actionable remediation adviсe
- Compliance and automated management reporting
- Performs continuous Penetration Testing
- Alerts on noticing exposed ports and changes in service
Why do we recommend it?
We recommend Intruder for its proactive approach to identifying a wide array of vulnerabilities, from misconfigurations to SQL injections. Its integration with major cloud providers and support for 9000+ security checks make it a robust solution for managing cybersecurity risks.
Companies of all sizes can invest in Intruder and check misconfigurations, missing patches, SQL injection, cross-site scripting, and other vulnerabilities with a few clicks.
Another notable feature of the trust ethical hacking tool is it integrates with major cloud providers, including Slack and Jira. Prioritize and fix all critical vulnerabilities using Intruder and spend most of your time focussing on real matters.
Who is it recommended for?
Intruder is ideal for companies of all sizes that need an all-encompassing solution for vulnerability management. It is particularly beneficial for organizations using cloud services like Slack and Jira and those who require real-time, actionable remediation advice.
Pros:
- Proactively identifies a broad range of cybersecurity weaknesses.
- Supports over 9000 security checks for thorough assessments.
- Offers actionable remediation advice and compliance reporting.
Cons:
- Could be overwhelming for small organizations due to its extensive feature set.
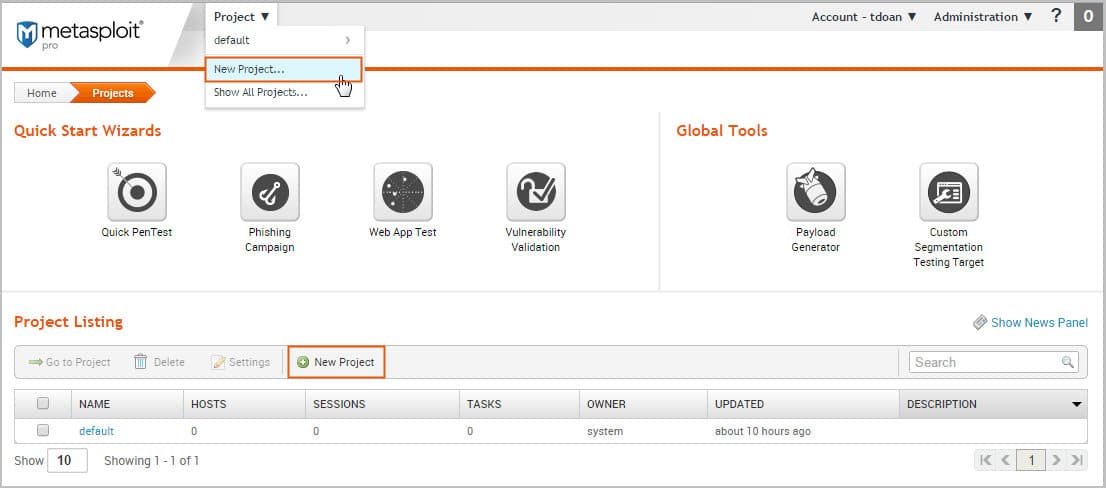
4. Metasploit
Metasploit is a free, open-source framework that helps businesses verify vulnerabilities and manage security assessments. Most security engineers trust Metasploit as it is one of the leading penetration testing systems that probe systematic vulnerabilities on networks and servers and prioritize solutions. It is easy to customize and configure Metasploit.
Key Features:
- Helps discover security vulnerabilities
- Offers penetration testing and supports pen-testing concepts
- Benefits in IDS signature development
- Compatible with Windows and Linux OS
- Metasploit is an open-source framework available for free
- Addresses systemic weaknesses
- Prioritizes vulnerabilities
- Antivirus evasion capabilities
- Easy to switch between payloads
- Generates instant reports
- It has a friendly GUI environment
- Supports third-party integrations
- Clone websites and mask malicious files for USB drop campaigns
- Easy-to-use interface
Why do we recommend it?
We recommend Metasploit for its comprehensive penetration testing capabilities and its ability to prioritize vulnerabilities effectively. It’s a trusted choice among security engineers and offers an easy-to-use interface along with third-party integrations.
Further, the ethical hacking tool is used by most operating systems to address systemic weaknesses. If you are looking for an easy-to-install and reliable hacking tool, go for Metasploit, as it provides auxiliary functions, payloads, and more features.
It is also used by experts for testing patch installations and implementing regression testing. Furthermore, the tool briefs businesses about places where hackers are most likely to attack. This information provided by the hacking tool helps users fix weaknesses before the attack.
Who is it recommended for?
Metasploit is suitable for both small businesses and large enterprises looking to discover and manage security vulnerabilities in their network and servers. It’s also a great choice for experts involved in IDS signature development, patch testing, and regression testing.
Pros:
- Open-source and free, making it accessible to all businesses.
- Friendly GUI environment simplifies vulnerability management.
- Supports third-party integrations for extended functionality.
Cons:
- Configuration and customization might be challenging for less technical users.
For commercial purposes, use Metasploit Pro, available for a 14-day free trial.
5. Nikto
Some high-profile companies use Nikto for it is open-source availability and the tool is comprised of 27 vulnerability scanners. Written in Perl language, experts find it easy to use the tool. Also, one can scan web servers for various dangerous files, outdated versions, and other vulnerabilities without affecting the performance.
Key Features:
- Performs web server analysis
- Discovers 6400+ CGIs and files that can be dangerous for your system
- Analyzes outdated versions and related problems
- Plug-ins and misconfigured files analysis
- Finds insecure programs
- Free and open-source
- Full support for SSL
- HTTP Proxy support
- Reports are available in different formats like XML, CSV, etc.
- Discovers script vulnerabilities
- Performs test for web server configuration errors
- Identify installed software
- Indexes all the files and directories
- Assesses intrusion detection system (IDS)
- Supports 27 vulnerability scanners
Why do we recommend it?
We recommend Nikto for its comprehensive web server analysis capabilities, including the ability to perform over 6000+ tests against a website. It’s one of the fastest tools for identifying vulnerabilities and misconfigurations without compromising performance.
Nikto is one of the fastest and most time-efficient hacking tools designed to scan, identify, and detect vulnerabilities and misconfigurations that can exploit the server.
Many security professionals and systems administrators prefer Nikto over other tools because it has the ability to perform 6000+ tests against a website.
Who is it recommended for?
Nikto is best suited for security professionals and systems administrators who are responsible for maintaining web servers and want a detailed, quick vulnerability assessment. It’s also an excellent option for those who need multiple reporting formats and full SSL support.
Pros:
- Performs detailed web server analysis.
- Capable of discovering over 6400 potential threats.
- Free and open-source, making it highly accessible.
Cons:
- Perl-based tool which may require specific scripting knowledge.
6. Nessus
Designed by tenable network security, Nessus is a free tool that helps discover critical bugs in a system. The main purpose of the tool is to reduce an organization’s attack surface and detect malware. It is highly advantageous and comprises various features that make it a top choice.
Key Features:
- Vulnerability scanning
- Checks which software components are vulnerable to attacks
- Detects remote and local flaws of the hosts and their missing patches
- Patch management
- Supports NASL language that helps in writing security tests
- Tests SSLized services
- Conducts regular non-destructive security audit
- Highly compatible with Windows and Unix-based operating systems
- Detects missing security updates
- Configuration auditing
- High-speed asset discovery
- Network scanning
- Offers broad asset coverage and profiling
- Flexible reporting
- Prioritizes vulnerabilities
- Meets compliance and regulatory standards
- The low total cost of ownership
- Detects hosts communicating with botnet-infected systems
- Supports web scanning
- Policy management
- Vulnerability assessment
Why do we recommend it?
We recommend Nessus for its comprehensive vulnerability scanning capabilities and its effectiveness in reducing an organization’s attack surface. The tool is highly versatile, offering features from patch management to compliance and regulatory standards coverage.
With Nessus, a vulnerability assessment solution also used for ethical hacking, you can scan different operating systems, next-generation firewalls, web servers, critical infrastructure, databases, and network devices.
Who is it recommended for?
Nessus is ideal for organizations of all sizes looking to strengthen their cybersecurity posture. It’s particularly useful for IT teams managing multiple types of operating systems and network devices that require flexible reporting and prioritization of vulnerabilities.
Pros:
- Conducts regular non-destructive security audits.
- Flexible reporting caters to various organizational needs.
- Prioritizes vulnerabilities effectively for targeted responses.
Cons:
- The complexity of features may require experienced IT professionals for maximum benefit.
7. Kismet
Most computer network security professionals and penetration testers use Kismet to identify potential target wireless networks. The purpose of introducing wireless networks was to make it easier for users and enhance flexibility. But hackers have the strength to turn those benefits into potential vulnerabilities. It is exactly where Kismet enters and helps businesses scan wireless networks.
Key Features:
- Compatible with Linux OS platforms
- Tests wireless networks
- Supports raw monitoring mode
- Detects various network IPs
- Detects network configurations
- Sniff wireless technology standards
- Allows channel hopping
- Requires no programming knowledge
- Supports Wi-Fi and Bluetooth interfaces
- Generates reports in different formats, including PDF, CSV, etc.
- Supports plugins that help in WebUI functionality extension
- Optimized for mobile devices
- Suitable for prototyping gameplay mechanics
- Helps visualize the flow of events
- Checks wireless LAN or wardriving
- Detects network and collects packets
- Uses data traffic to discover hidden networks
Why do we recommend it?
We recommend Kismet for its robust wireless network scanning capabilities and the ability to identify hidden networks through data traffic. The tool is versatile, supporting multiple platforms and requiring no programming knowledge.
Kismet can be easily run on Windows, Linux, and macOS platforms and supports large configurations and drivers. Further, with Kismet, you do not have to associate the tool with an access point to monitor traffic and identify wireless networks.
Who is it recommended for?
Kismet is well-suited for network security professionals and penetration testers who need to monitor and assess wireless networks. It’s especially useful for businesses looking to secure their wireless infrastructure or identify vulnerabilities in existing setups.
Pros:
- Detects a wide range of network IPs and configurations.
- Requires no programming knowledge, user-friendly for non-technical users.
- Supports plugins for extended functionality.
Cons:
- Primarily focused on wireless networks, may not be as comprehensive for other security needs.
8. NetStumbler
NetStumbler is an ethical hacking tool available for Windows-based operating systems. It helps detect, explore and filter access points. The tool also prevents wardriving and is used by companies to detect IEEE 902.11g, 802, and 802.11b networks.
Key Features:
- Checks access point network configurations
- Discover interference causes
- Accesses signal strengths
- Identifies unauthorized access points
- Prevents wardriving
- Detects IEEE 902.11g, 802, and 802.11b networks
- Provides details about wireless network
- Hosts user-submitted compatibility reports
- Reports signal strength levels
- Supports auto reconfigure feature
- Signal-to-noise graphs
- Supports various access point filters
- GPS support to track detected APs
- Supports various functions through active scripting languages
- Supports large online community
Why do we recommend it?
We recommend NetStumbler because of its ability to accurately identify and filter access points, as well as assess the strength of received signals. Its comprehensive feature set includes GPS support for mobile tracking and a range of access point filters.
If you are looking for a hacking tool that helps identify access point network configurations and access the strength of received signals, opt for NetStumbler. It also supports mobile tracking with GPS.
Who is it recommended for?
NetStumbler is ideal for IT professionals and network administrators who are focused on wireless network security. It’s especially useful for those looking to prevent wardriving and unauthorized access to their network, or who need to understand the strength and reach of their wireless signals.
Pros:
- Effective in detecting and filtering access points.
- Assists in preventing wardriving and unauthorized network access.
- GPS support enhances mobile tracking capabilities.
Cons:
- Limited to Windows-based operating systems, restricting broader use.
9. Aircrack-Ng
Aircrack-Ng helps keep the Wi-Fi secure using the best ethical hacking practices. It supports an array of command-line tools to identify, analyze, and evaluate Wi-Fi network security. Most security professionals find it easy to use the hacking tool as it supports a wide range of operating systems, including 2Free BSD, NetBSD, OpenBSD, Windows, OS X, Linux, Solaris, and eComStation.
Key Features:
- Crack WEP keys and WPA2-PSK
- Identifies Wi-Fi cards
- Compatible with various platforms, including 2Free BSD, NetBSD, OpenBSD, Windows, OS X, Linux, Solaris, and eComStation
- Check WiFi networks for weaknesses
- WiFi security monitoring
- Capturing and exporting data packets to text files
- Crack WPA and WEP protocols
- Helps sniff wireless packets
- Manages wireless drivers
- Helps in recovering lost keys
- Performs deauthentication
Why do we recommend it?
We recommend Aircrack-Ng for its robust capabilities in identifying and evaluating Wi-Fi network security, including cracking WEP and WPA-PSK keys. Its compatibility with a wide range of operating systems makes it a versatile choice for security professionals.
Further, it also helps in cracking WEP and WPA-PSK keys.
Who is it recommended for?
Aircrack-Ng is recommended for cybersecurity experts and IT professionals specializing in wireless network security. It’s particularly useful for those looking to crack WEP and WPA-PSK keys or those who need to monitor Wi-Fi networks for vulnerabilities.
Pros:
- Excels in cracking WEP keys and WPA2-PSK.
- Effective in WiFi security monitoring and vulnerability detection.
- Assists in managing wireless drivers and sniffing wireless packets.
Cons:
- Command line interface may be intimidating for users unfamiliar with such environments.
Final Thoughts
With businesses shifting their operations online, the risk of hacking and ransomware attacks has also increased. Hackers try to put the computer system into an unstable state and demand a lump sum amount in return. They use different codes and tactics that are hard to crack and take a lot of time.
In most cases, companies have to pay the money to the hackers to avoid major losses.
The only way to secure your systems and company data from these hackers is to implement white-hat hacker practices, i.e., ethical hacking.
It is true security protocols and encryption techniques can save your devices from threats and data breaches, but hacking is way different and hard to crack. Even experts with good knowledge and skills find it difficult to decode and fix hacking.
But, ethical hacking practices can prove to be exceptionally helpful. Ethical hackers bypass security systems to identify and correct vulnerabilities in a network. They collect data and fix the loopholes that attackers might find an opportunity to exploit or destroy.
If you are planning to do hacking make sure it is used for white hat hacking purposes, and the user carries secured written permission from the targeted site. Furthermore, here we have shortlisted some of the most vital tools available on the market for ethical hacking.
Netsparker, Acunetix, Intruder, Metasploit, Nikto, Nessus, Kismet, NetStumbler, and Aircrack-Ng are a few popular tools that companies can invest in.
These popular hacking tools help discover vulnerabilities, offer full visibility into web assets, allow scanning, support patch management, and more. Some of the tools also help generate more secure code and eliminate the manual verification process.
Compare the ethical hacking tools and their features before selecting one for your business operations.