Today, cloud technology is not limited to only IT operations, various business models have also adopted the staple technology. The use of cloud services will accelerate in the future as many businesses are shifting to digital platforms. As a result, the demand for workloads will increase to maintain data center operations and support remote operations.
Workloads in the cloud environment are databases, containers, virtual machines, and physical servers that consume cloud-based resources. In simple terms, these are programs and applications that run on a cloud and deliver the requested information to the users.
Here is our list of the best cloud workload security platforms:
- Datadog Cloud Workload Security This cloud protection platform uses eBPF to sandbox and test cloud systems to detect vulnerabilities and deploys an adaptation of that system for live security monitoring.
- Trend Micro Deep Security This cloud-based system provides preventative scanning and live security monitoring for on-premises and cloud applications.
- Microsoft Defender for Cloud Evolved from Azure Security Center, this package can secure applications and infrastructure on AWS and GCP as well as on Azure.
- Illumio Core Use this tool to implement Zero Trust Access to cloud-based applications and services and protect communications with IoT devices.
- Prisma Cloud Palo Alto Networks has developed this cloud platform into a security service for applications from coding through to deployment.
- Armor Cloud This Security Operations Center manages your security software and recommends tools if you haven’t yet got all of your protection systems in place.
- Lacework This Cloud-Native Application Protection Platform includes vulnerability scanning and live security monitoring for cloud systems and cloud-based applications.
- Kaspersky Hybrid Cloud Security This package covers DevOps testing, physical and virtual on-premises servers, and cloud platforms and also scans and monitors applications for security issues.
Moving businesses to the cloud can improve your business, but there are also many challenges one must keep in mind. Remember, attackers in the cloud always look for opportunities to damage or breach data. In this case, missing out on adding protection to workloads when moving between different cloud environments can go against you.
Businesses must use various cloud workload protection platforms to save their crucial information from common cloud workload security threats, such as Misconfiguration, Malware Threats, Stolen Credentials, Container Escape, etc.
Here, we will discuss some popular cloud workload protection platforms, their features, and their benefits in detail.
Our methodology for selecting a Cloud Workload Protection Platform tool
We’ve broken down our analysis for you based on these key criteria:
- Emphasis on comprehensive security coverage for diverse cloud environments
- Ability to seamlessly integrate into existing cloud infrastructures and workflows
- Consideration of cost efficiency and usage-based billing features
- Focus on operational flexibility and adaptability to varying cloud conditions
- Importance of full visibility and compliance with data protection regulations
What is a Cloud Workload Protection Platform?
The term Cloud Workload Protection Platform (CWPP) was introduced by Gartner to protect and secure cloud workloads from various cybersecurity threats and challenges. The technology solution guarantees complete protection to virtual machines, containers, physical servers, and other cloud infrastructures when moving through their domain or data to different cloud environments.
Ransomware attackers and cybercriminals are always looking for opportunities in the cloud. Thus, proper security strategies are essential that will limit access to endpoint devices and secure the workload level.
With the CWPP, all your outgoing or incoming data into an application will remain secure. Also, the administrators can monitor the movement and performance of the workloads.
Remember, if the workloads or any part gets compromised, the application will stop functioning properly. Thus, if you want the smooth functioning of cloud services, it is best to implement Cloud workload protection platforms to keep workloads safe from unwanted threats.
Another benefit of implementing these popular security tools for your organization is they will aid in keeping track of all misconfigurations and vulnerabilities.
Benefits of Cloud Workload Protection Platform
The purpose of introducing the CWPP is to provide a security tool to organizations that will protect workloads on a constant basis. Apart from addressing the security issues, the CWPP offers many more benefits to organizations, including:
- Minimizes Complexity Most businesses use legacy tools to protect endpoints and physical servers. However, the tools miss the features that could provide full protection to virtualization or containers. To fix it, CWPP was designed that target security for cloud conditions and provide full protection to all workloads that might be difficult to achieve using legacy tools.
- Adds More Consistency Another advantage of using the CWPP is it offers a more consistent view. It does not matter how many workloads your organization uses or where they are located, CWPP always offers consistency.
- Portability CWPP provides security to workloads regardless of their location. For instance, if today your workload is running in an on-premises hypervisor and later moved to a container running on an engine to Azure Container Instances, CWWP will ensure full security at all times.
- Cost-efficient CWPP provides built-in usage-based billing features. These features unlike other physical appliances in on-prem environments aid businesses to save on costs.
- Agility The security tools can easily integrate into DevOps CI/CD pipelines. The integration features allow automatic configuration and secure applications using workloads without any unnecessary overhead. Also, it allows quick and easy deployments of workloads.
- Better Security Cloud service providers often face various cybersecurity challenges. To overcome it, the CWPP was designed and tailored with unique security controls, offering full visibility to cloud workloads. These security options for the workloads also fulfill the cloud security requirements and enable organizations to safeguard their data from unwanted threats.
- Full Visibility Earlier, the monitoring and management of multi-cloud deployments was a difficult task for developers. However, with the introduction of CWPPs, organizations can easily keep track of workloads running in different environments using a single console. It also supports network segmentation features that enable developers to get deeper visibility into their traffic flows. As a result, with the help of CWPP, developers can monitor and track all incoming threats coming from different cloud environments.
- Compliance CWPP offers data protection regulations that are mandatory to implement for the organization’s security. It also offers various security controls that enable businesses to protect their sensitive data. Using popular security tools, developers can auto-scan vulnerabilities and compliance violations.
- Flexibility Cloud often scales the resources up and down as per their requirement. CWPP, being a cloud-based security tool, provides similar features and the same level of flexibility to organizations when it comes to securing different applications and workload security.
The Best Cloud Workload Security Platforms
With the increasing demand for public cloud services, the threats have also increased. Thus, the need for security tools that offer optimal cloud protection has become a necessity. Cloud workload protection platforms aid businesses in managing and monitoring various critical workload security across all public and private clouds.
Compare and choose from a wide range of CWPPs from the below list:
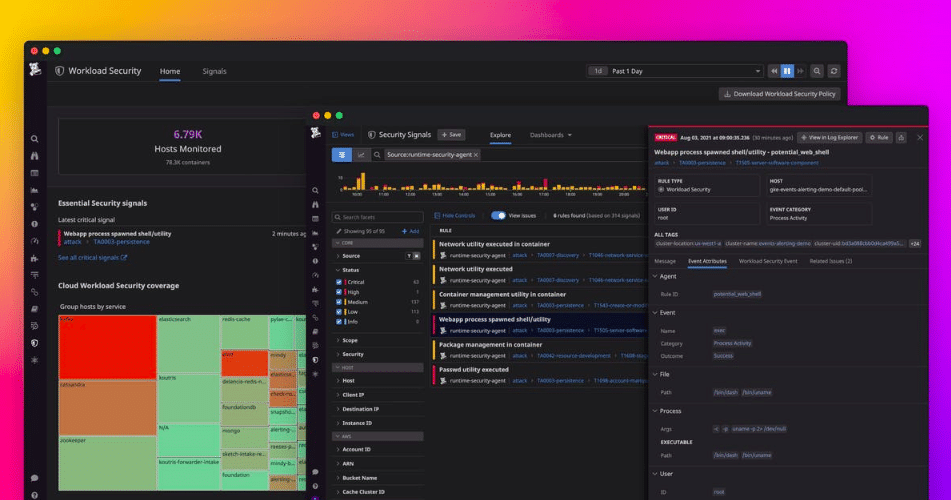
1. Datadog
Datadog’s Cloud Security Platform is one of the popular security platforms for cloud applications with deep observability capabilities. It helps detect, monitor, and respond to potential threats faster in comparison to other security tools and supports 600+ integrations. Developers can analyze all operational and security logs using its features. The security tool is scalable and hardly takes any time to set up.
Key Features:
- Data aggregation
- Custom Alert System
- Sensitive Data Scanner
- Allows monitoring end-to-end user experience
- Real-time threat detection
- Network Device and Container Monitoring
- Deep monitoring of workload activities
- Datadog takes only a few minutes to setup
- Reduces complexity
- Supports 600+ integrations
- Supports Datadog File Integrity Monitoring (FIM)
- Scalable and offers deep visibility
- Network Performance Monitoring
- Distributed Tracing
Why do we recommend it?
Datadog’s Cloud Security Platform offers exceptional real-time threat detection and supports over 600 integrations, making it highly versatile and effective for cloud application security. Its scalability and quick setup time give it an edge over other platforms in the same category.
With Datadog’s Cloud Workload Security, users can manage workloads, monitor files and kernel activities, make trade-offs between visibility, and track all incoming threats to production workloads in real-time. Also, it enables DevOps and Security teams to address different cybersecurity challenges using deeper insights and quality reports.
Further, it has unified Datadog Agents, which eliminates the need or provisioning of additional resources or new agents. It is an ideal cloud security platform for detecting threats that already reside in cloud instances and containers.
Who is it recommended for?
Datadog is ideal for organizations that prioritize quick, efficient, and comprehensive cloud security, especially those with complex, multi-service architectures. It’s particularly beneficial for DevOps and Security teams who need to manage a wide variety of workloads and want deep visibility into both operational and security metrics.
Pros:
- Efficient real-time threat detection capability
- Supports over 600 integrations, enhancing versatility
- Offers deep workload activity monitoring for comprehensive insights
Cons:
- May be overwhelming due to its extensive features
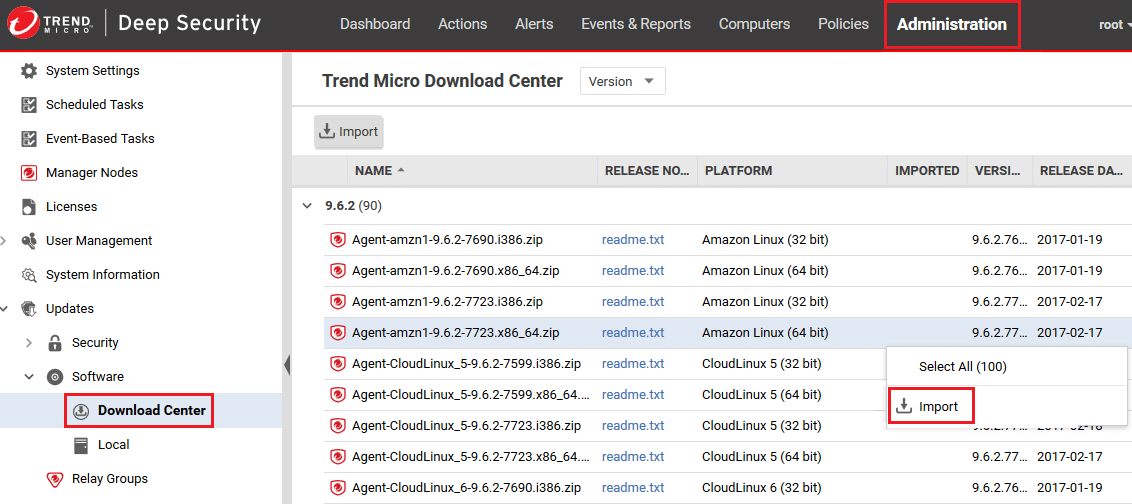
2. Trend Micro Deep Security
Trend Micro Deep Security is another trusted CWPP with an advanced set of functions that help secure cloud workloads. The powerful tool identifies and protects crucial data from malware and other threats. It also prevents any unauthorized software changes with its deep security features and application control capabilities.
Key Features:
- Behavioral and sandbox analysis
- Provides context-based proactive protection
- Regularly updated compliance
- Anti-malware and IPS capabilities
- Application control capabilities
- Faster detection and protection against vulnerabilities
- Virtual patching techniques
- Supports machine learning
- Seamless auto-scaling
- Unified security
- Seamless integration
- Automate security deployments
- Accelerates incident response
- Provides actionable insights
- Deep Security has a centralized web-based management console
- Web reputation service
- Integrity monitoring
- Perform health checks
- Log inspection and protection
Why do we recommend it?
Trend Micro Deep Security provides a comprehensive set of cloud workload protection features, including machine learning and virtual patching techniques, that make it a standout choice for robust cloud security. Its integration capabilities with DevOps processes and its centralized web-based management console facilitate ease of use and operational efficiency.
Trend Micro Deep Security also supports integrity monitoring, web reputation service, firewall, behavioral analysis, and sandbox analysis. Another feature why developers recommend this tool is it seamlessly integrates into DevOps processes. The security tool also provides instance-based protection to new and existing workloads using machine learning and Virtual Patching techniques.
The intuitive dashboard of Deep Security accelerates incident response and provides actionable insights that aid in better decision-making. It also enforces consistent security across clouds and container environments that help prevent security gaps.
Who is it recommended for?
This tool is ideal for enterprises that require advanced, multi-layered cloud workload security and have a focus on integrating security into their DevOps pipelines. It is particularly useful for organizations that need to meet stringent compliance standards and are looking for a unified, scalable solution.
Pros:
- Utilizes machine learning for enhanced security
- Offers virtual patching techniques for faster response
- Centralized web-based management console for ease of use
Cons:
- Might be resource-intensive for smaller setups
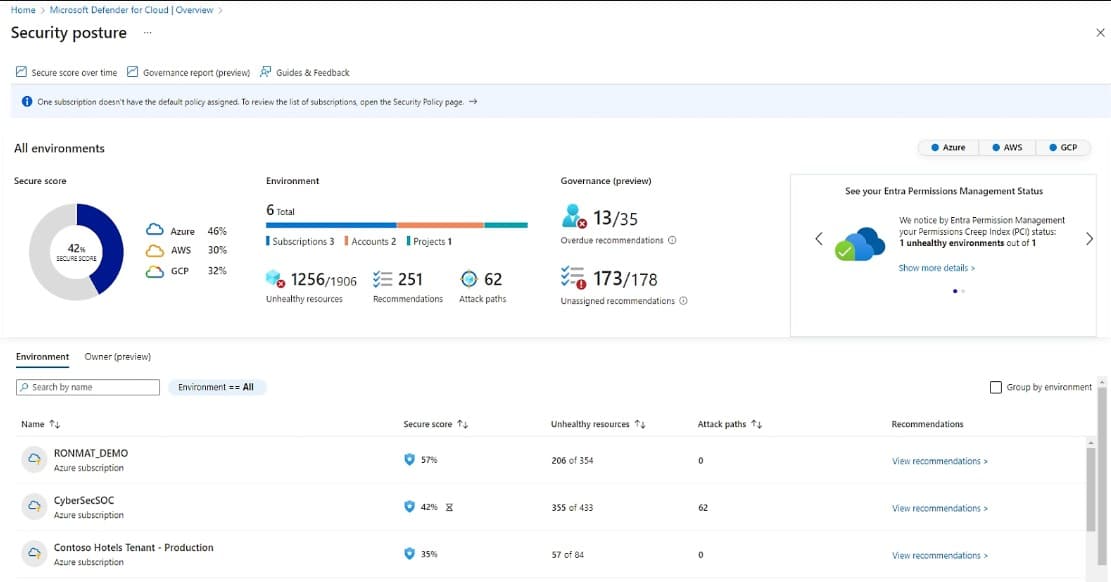
3. Microsoft Defender for Cloud
Microsoft Defender for Cloud is the new name for Microsoft Azure Security Center. This platform is now a full Cloud-Native Application Protection Platform. Its units provide preventative scanning and live security monitoring. Although this is an Azure service, the systems in the package can also protect assets on AWS, Google Cloud Platform, and on private clouds.
Key Features:
- Discovers weak spots and vulnerabilities
- Strengthens security posture
- Full threat protection to workloads across different environments
- Manage compliance and regulatory standards
- Regular workload monitoring
- Offers continuous security assessment of cloud resources
- Provides actionable insights
- Streamlines security administration from a single console
- Unified security management
- Automated application controls
- Centralized security policy management
- Prioritize alerts and recommendations
- Policy configuration
- Supports regular scanning of Virtual machines
- Integrates log data for alerts
- Advanced cloud defenses
Why do we recommend it?
Microsoft Defender for Cloud offers an extensive set of security features and integrates seamlessly with various cloud platforms, not just Azure. Its unified management console and ability to prioritize alerts make it a comprehensive and user-friendly security solution.
The Microsoft system is a flexible package and you don’t have to subscribe to all of the units. There is an XDR solution that can also be managed from the Defender for Cloud console. The system centralizes all of your cloud protection services in one dashboard, which is resident in the cloud and can be accessed from anywhere through any standard web browser.
Who is it recommended for?
This platform is recommended for businesses operating in multi-cloud environments, including AWS and Google Cloud, who need a centralized, robust security solution. It’s also suitable for organizations looking to manage compliance and regulatory standards effectively across different cloud resources.
Pros:
- Provides comprehensive threat protection across multiple environments
- Streamlines security administration from a unified console
- Integrates log data effectively for enhanced alert management
Cons:
- Primarily focused on Azure, though it supports other clouds
Microsoft Defender for Cloud is not a free service. However, you can experience this and any other Microsoft service on the Azure platform with a 30-day free trial.
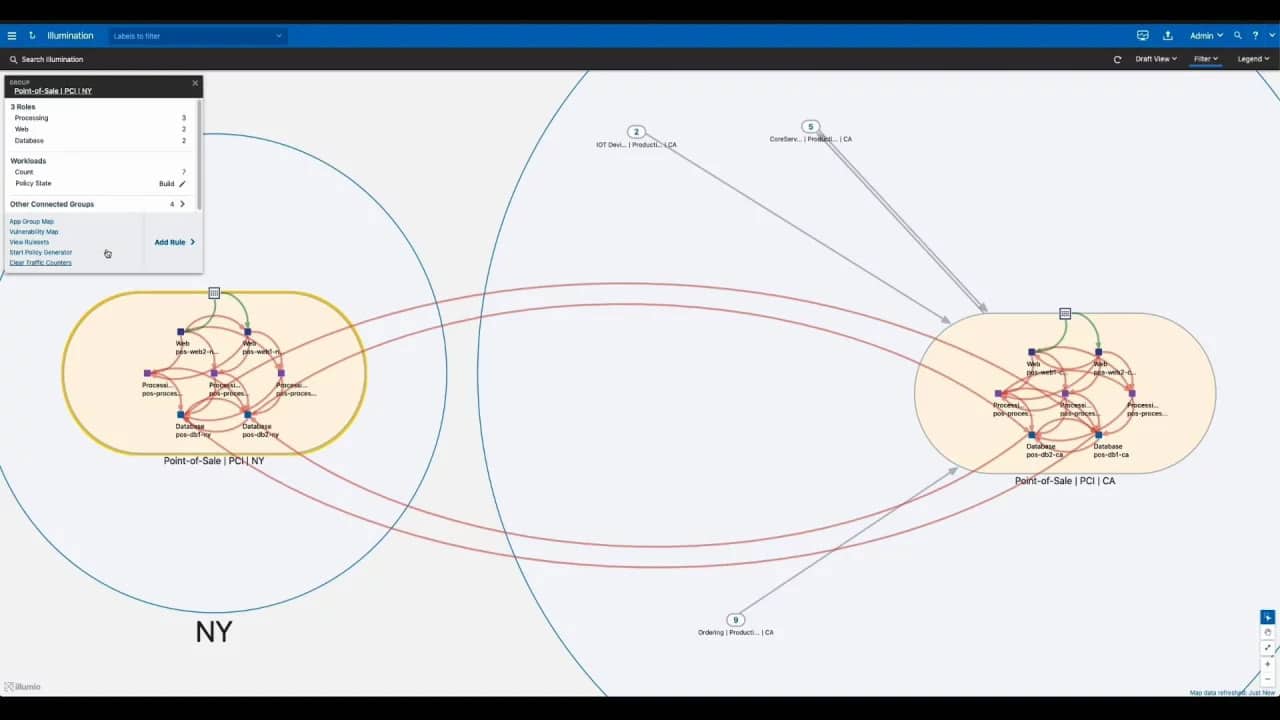
4. Illumio Core
As the data centers are extending and moving into clouds and containers, the need for a security framework like Illumio Core has become a necessity. Illumio Core is a robust cloud workload security solution that provides full protection to the assets stored within complex cloud-based IT infrastructures. The security tool maintains compliance throughout the organization and delivers threat-detection features.
Key Features:
- Provides multi-cloud protection
- Streamlines procedure management using Policy Compute Engine (PCE)
- Full visibility
- Application Programming Interface (API)
- Automated segmentation
- Real-time application insights
- Data encryption tools support
- Historical traffic record analysis
- Delivers threat remediation capabilities
- Fast micro-segmentation solution
- Host-to-host traffic encryption
- Real-time application dependency map.
- Generates quick segmentation policies
- Vulnerability maps
- Rest APIs and UI
- Roles-Based Access Control (RBAC)
- Multi-dimensional labeling
- Workload security enforcement at a massive scale
Why do we recommend it?
Illumio Core excels in providing granular control and visibility over complex cloud-based IT infrastructures. With features like real-time application insights and automated segmentation, it stands out as a robust solution for workload security in multi-cloud environments.
Who is it recommended for?
Illumio Core is ideal for organizations with complex, multi-cloud setups who require advanced threat detection and remediation capabilities. It’s particularly well-suited for enterprises that need to maintain stringent compliance standards and seek an automated approach to security policy management.
It involves a security policy management toolkit with advanced features like application dependency maps, automated segmentation and enforcement, Policy Compute Engine (PCE), core service detector, and more. It also provides vulnerability insights to the enterprises that help locate the attackers and remediate issues.
Cyberattacks and ransomware are common in clouds and often left undetected. But, with the help of Illumio Core, administrators can monitor workloads coming in and out of applications and protect them from threats. Also, organizations can control and deploy automated policies using trusted security tools.
Pros:
- Delivers granular control and visibility over complex IT infrastructures
- Real-time application insights and automated segmentation
- Supports historical traffic record analysis for deeper insights
Cons:
- May require advanced technical knowledge for optimal utilization
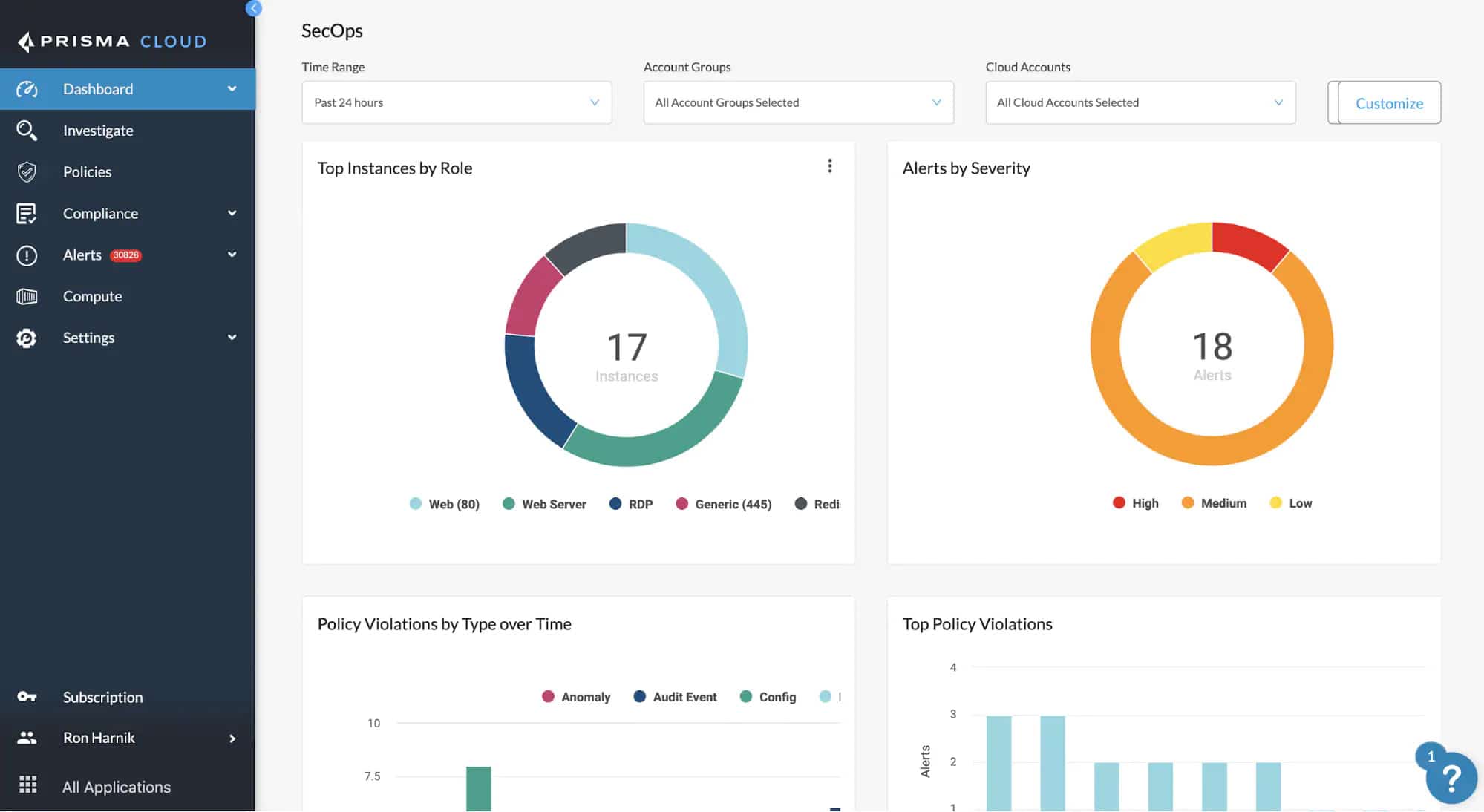
5. Prisma Cloud
Prisma Cloud is a comprehensive cloud-native security platform that delivers full protection across lifecycle development on any cloud, including Azure and Google Cloud. It has also added a new feature that allows access to container image sandboxing. With the help of this feature, developers can inspect all the files, processes, and pre-deployments of network activity.
Key Features:
- Provides unmatched visibility and protection
- API security
- Network Data Exfiltration Detection
- Allows scanning infrastructure-as-code (IaC) templates
- Offers container security
- Allows malware scanning on public cloud storage
- Provides full-stack runtime protection
- User and entity behavior monitoring
- Threat detection and response
- Automates risk prioritization
- Secure configurations
- Enforces governance policies
- Monitors security posture
- Network visibility
- Microsegmentation
- Maintain compliance across cloud environments
- Offers full protection to the hosts, containers, and serverless functions
- Integrates with continuous integration and continuous delivery (CI/CD) workflow
Why do we recommend it?
Prisma Cloud offers a comprehensive suite of features like API security, network data exfiltration detection, and full-stack runtime protection, making it a standout choice for cloud-native security. The tool’s ability to integrate seamlessly with CI/CD workflows helps in automating risk prioritization and threat response.
Another advantage of using Prisma cloud is it helps remove all the dangerous cloud blind spots and reduces the burden of alert fatigue. As more and more businesses are moving to the cloud, it is essential to invest in cloud workload Protection Platforms that offer full network visibility, container security, API security, full-stack runtime protection, user and entity behavior monitoring services, and more.
The leading CWPP leverage continuous vulnerability management and maintain compliance on multi and hybrid-cloud environments.
Who is it recommended for?
Prisma Cloud is best suited for businesses that have adopted multi-cloud or hybrid-cloud environments and are in need of robust, all-encompassing security solutions. Organizations looking to enforce governance policies, automate risk assessments, and achieve compliance across their cloud infrastructure will find Prisma Cloud particularly beneficial.
Pros:
- Unmatched visibility and protection across cloud environments
- Offers extensive container and full-stack runtime protection
- Integrates effectively with CI/CD workflows for automated risk management
Cons:
- Could be complex for users new to cloud-native security platforms
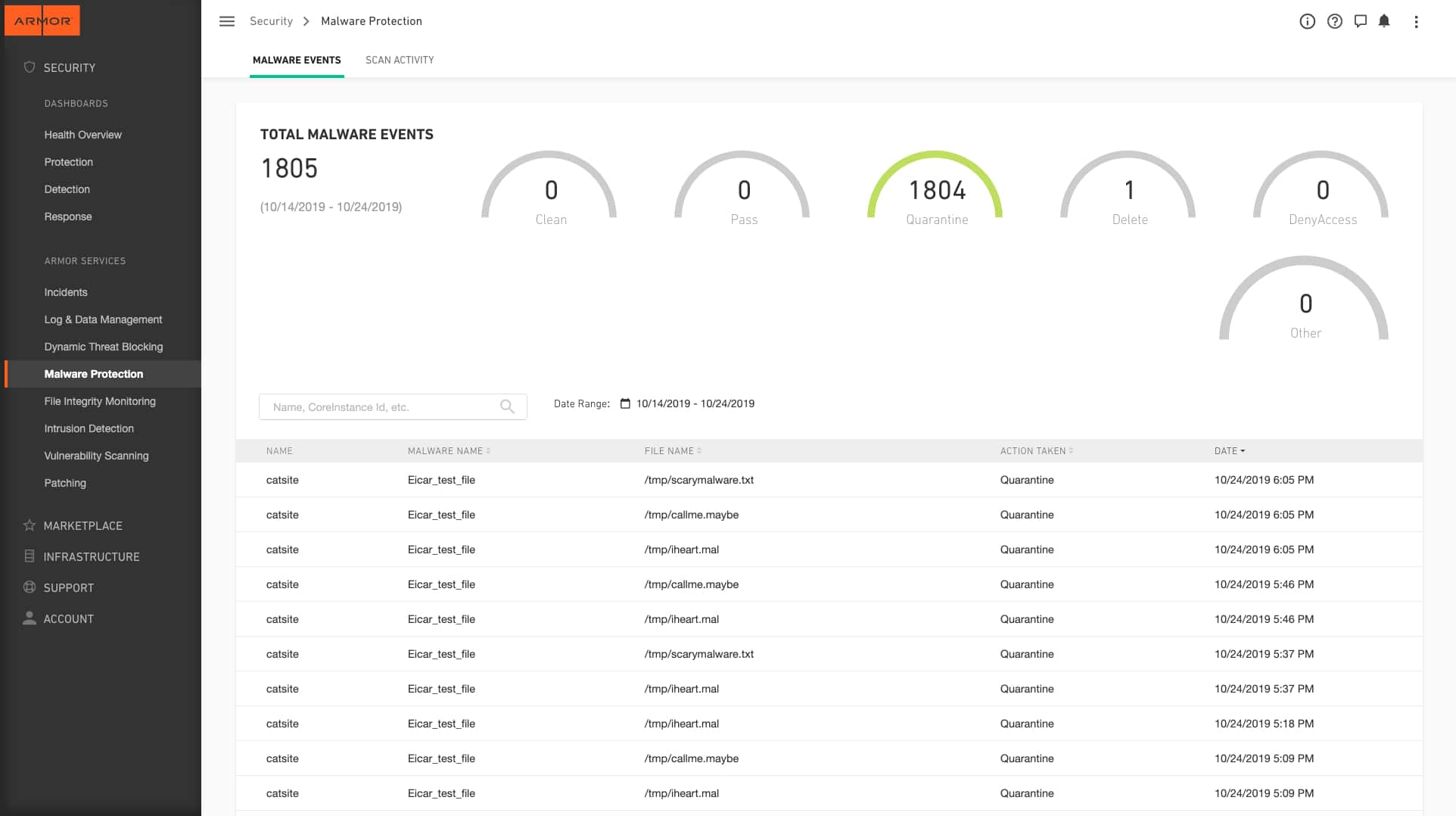
6. Armor Cloud
Armor Cloud is a package of third-party security systems – usually open-source software – that has been put together by Armor and is constantly supported by the Armor team. Security and compliance are the top challenges that most businesses face on moving workloads to the cloud.
Key Features:
- Intrusion detection
- File integrity monitoring
- Offers malware protection
- Supports patch monitoring
- Log management
- Scans internal and external vulnerabilities
- FIM service status
- Quick deployment and scaling
- Monitors alert activity
- Offers unified visibility and control
- Data monitoring and protection
- Provides real-time insights
- Operational control
- Risk management and compliance
- Workload protection for all environments
- Threat detection and response
- Policy recommendation scans
Why do we recommend it?
Armor Cloud stands out for its robust Security Operations Center (SOC) and its versatile package of security systems, including intrusion detection, malware protection, and log management. The tool is particularly strong in providing real-time insights and operational control, enhancing overall security posture and compliance.
The Armor Security Operations Center (SOC) will install agents on your Windows and Linux servers and in your cloud accounts. This is a log collector, called Armor Anywhere and it feeds data into Armor’s collection of threat detection, anti-virus, malware protection, and all-time incident response. It protects your data centers from cyber threats and monitors alert activity to instant respond and remediates the issue.
It also helps keep an account of agent logs for 30 days and provides in-depth system scans for better visibility. Access the robust Security Operations Center (SOC) to get help at any hour of the day.
The dashboard provides an overview of the entire IT infrastructure streamlining data log history, vulnerabilities, threats, and health scores.
Some of the new features include Intrusion Prevention, Policy Recommendation Scans, and flexibility to turn security capabilities on and off. Armor Cloud has been in practice by many organizations and enables them to meet their business security needs.
Who is it recommended for?
Armor Cloud is ideal for businesses of all sizes seeking an integrated, third-party security solution that offers real-time monitoring and threat detection. Companies with hybrid or multi-cloud environments looking for a security tool that can offer quick deployment, scaling, and compliance capabilities would benefit the most from using Armor Cloud.
Pros:
- Provides comprehensive log management and file integrity monitoring
- Offers unified visibility and control across environments
- Efficient threat detection and response with policy recommendation scans
Cons:
- Third-party dependencies may require additional management
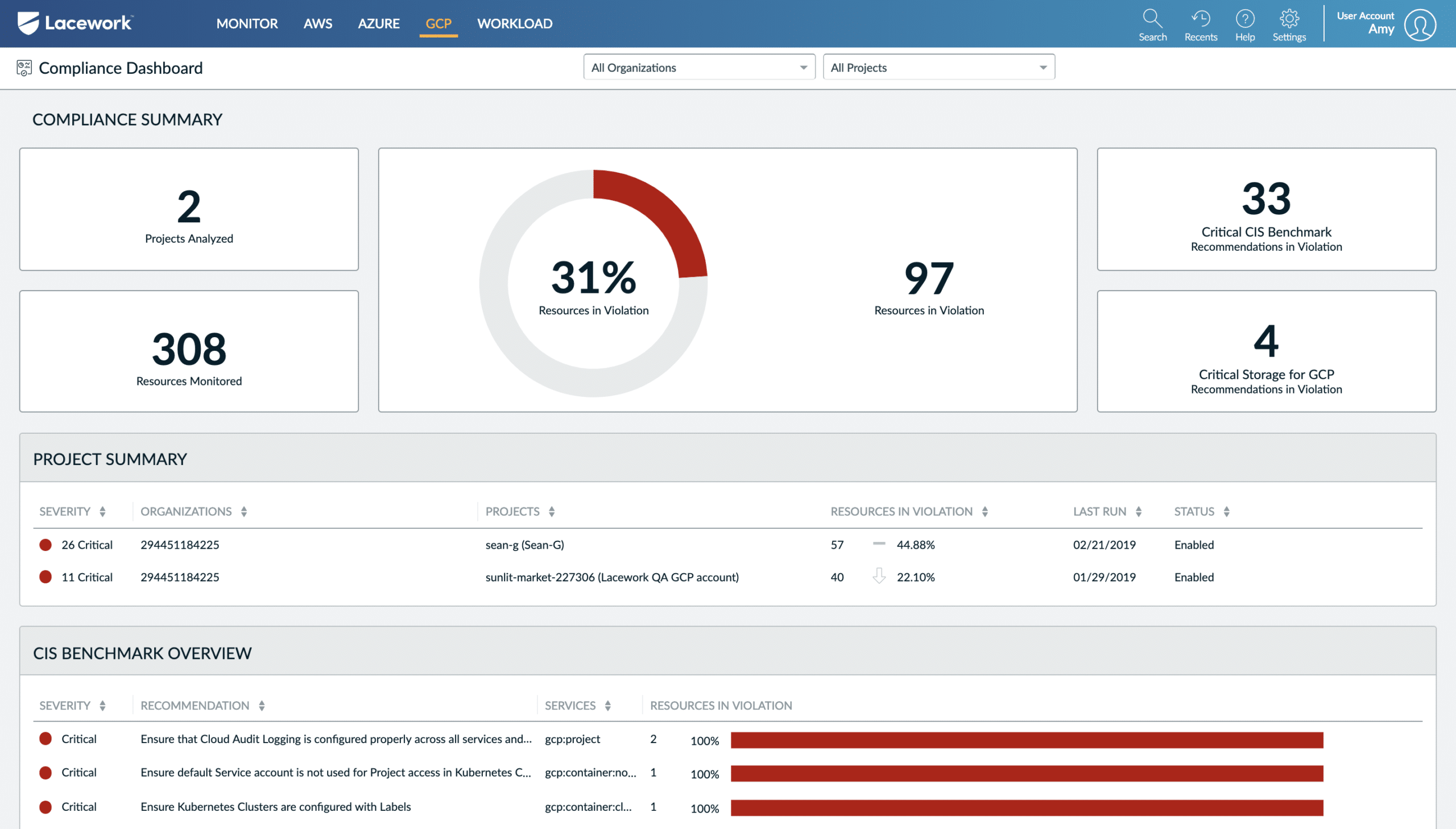
7. Lacework
The Lacework Cloud Security Platform offers both security and compliance to the cloud. It involves faster deployment and enables businesses to automate workload scaling. Developers can easily use machine learning analysis to identify, detect, and monitor incoming threats and vulnerabilities in the system.
Key Features:
- Provides better insights
- Vulnerability management
- Supports behavioral analytics
- Detects misconfigurations and unusual activity
- Offers deep end-to-end visibility
- Container and cloud workload analysis
- Faster deployment
- Auditing of security configuration
- Scalable architecture
- Threat detection
- Intrusion detection
- Alert System
- Automated AWS Security Monitoring
- Graphical investigation tools for all environments
Why do we recommend it?
Lacework excels in providing both security and compliance features, backed by machine learning analysis for swift threat detection. Its capabilities in vulnerability management and behavioral analytics make it a comprehensive solution for cloud workload protection.
Who is it recommended for?
Lacework is well-suited for businesses operating in multi and hybrid cloud environments who require instant breach detection across various processes, workloads, and data centers. Companies looking for a solution with faster deployment and automated scaling would find Lacework especially beneficial.
Lacework is a widely used cloud workload protection platform with simple operational and maintenance rules. The security tool offers deep visibility, delivers contextual data covering the latest updates, problems, and changes made to the configuration. It also provides full support to computer hosts, containers, and various public clouds, including Azure, AWS, etc.
Most vendors do not address multi and hybrid cloud workloads. As a result, Lacework was introduced for instant breach detection covering all the processes, workloads, users, applications, and data centers.
Pros:
- Advanced vulnerability management and behavioral analytics
- Efficient AWS security monitoring with automated processes
- Provides deep end-to-end visibility across cloud workloads
Cons:
- Might be less familiar to users of more established platforms
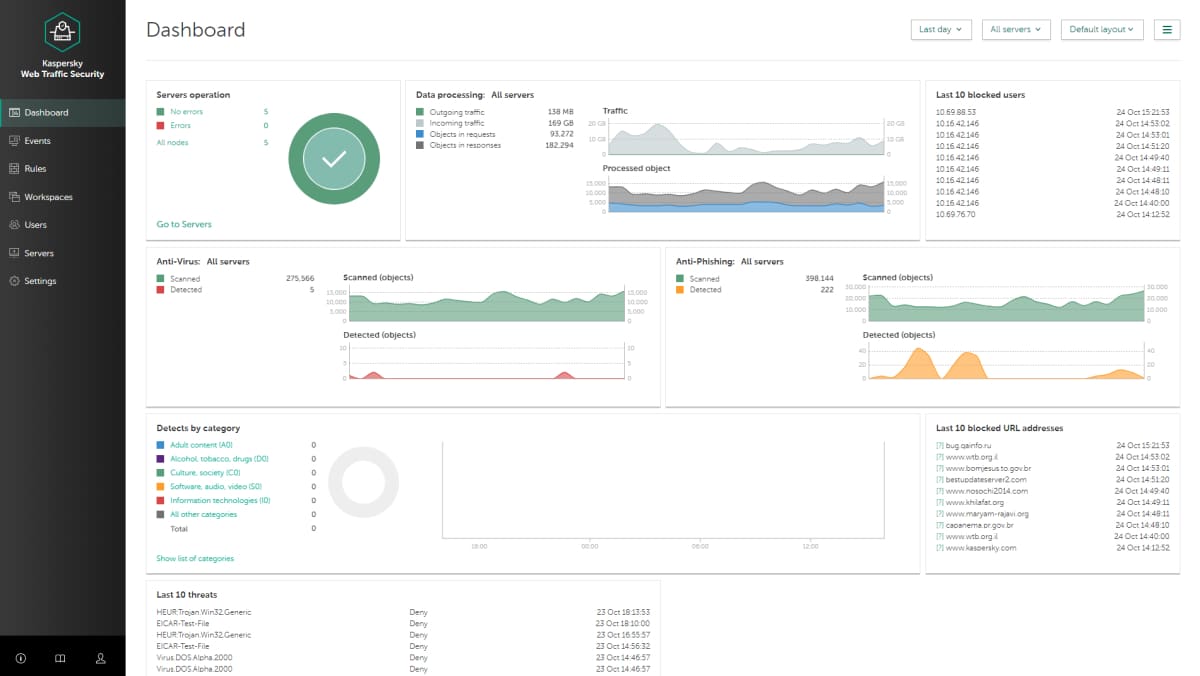
8. Kaspersky
Kaspersky Hybrid Cloud Security was designed for virtual desktops and Windows, Linux servers. It provides the Next Gen protection to all physical machines, virtualized workloads, on-premise, in a data center or cloud against cyber-attacks. Today, the protection of cloud data is essential to maintain business sustainability. Thus, the concept of Kaspersky was introduced to protect company data and digital transformation.
Key Features:
- Supports provisioning of VDI machines
- Next-Gen protection against threats
- Provides protection to physical machines and virtualized workloads in containers, data centers, and complex hybrid environment
- Supports regulatory compliance
- Flexible and agile
- Light Agent security for Linux and Windows Servers
- Provides logs inspection
- File Integrity Monitor (FIM)
- Offers multi-layered protection to all environments
- Anti-spam and anti-phishing features
- Borderless manageability
- It has a unified orchestration console to provide deep visibility
- Advanced protection for AWS and Microsoft Azure Infrastructures
- Meets Service Level Objectives (SLOs) to reduce risk
- Threat detection and response
Why do we recommend it?
Kaspersky Hybrid Cloud Security offers comprehensive, multi-layered protection for various cloud environments, including both virtual and physical machines. Its Next-Gen capabilities, coupled with support for regulatory compliance and flexibility, make it a standout option for cloud workload protection.
Who is it recommended for?
Kaspersky is ideal for businesses that have complex hybrid environments, including those with a mix of physical machines, virtualized workloads, and cloud-based infrastructure. It’s particularly useful for companies that need to meet stringent regulatory compliance standards while maintaining high levels of security.
Kaspersky is a leading CWPP that offers continuous security and multi-layered protection to all cloud environments. Add full protection to your workloads using Kaspersky. It does not matter if your workloads are running on IaaS or in-house infrastructures, the security tool offers guaranteed protection, flexibility, and visibility to users.
Pros:
- Next-Gen protection for a wide range of environments
- Supports regulatory compliance and flexible deployment
- Provides advanced protection for AWS and Azure infrastructures
- Unified orchestration console for comprehensive visibility
Cons:
- May be more suited for larger, more complex environments
Final Thoughts
Securing workloads is essential to maintain business sustainability in the clouds. There are various threats and cybersecurity challenges that various organizations face in the clouds. Thus, to protect your workloads, such as physical servers, virtual machines, containers, and databases, Gartner coined the term – Cloud Workload Protection Platform (CWPP).
CWPP helps provide protection to all programs and applications that run on a cloud. There are various advantages of using these security tools apart from providing security. It also saves on cost, minimized complexities, offers flexibility, consistency, advanced security, compliance, and more.
Keep track of all misconfigurations, and vulnerabilities and protect the workloads regardless of your location using the trusted CWPP.
We have also listed some of the top cloud workload protection platforms that enable businesses to easily manage and monitor workloads on various cloud environments and data centers.
Your cloud service provider might lack some of the features that will not provide overall cloud workload security. Later, you might have to invest in premium tools to unlock its advanced features. Thus, make sure to check their plans and pricing before installing.
Datadog, Trend Micro Deep Security, Microsoft Azure Security Center, Armor Anywhere, etc., are some of the popular security tools that help discover weak spots, threats, and vulnerabilities. Follow the above list to compare each security tool and its features before investing your time and money.