Today, cloud security has become a crucial topic of discussion. There are many companies that install expensive software or implement attack programs to safeguard their sensitive information. Breach and Attack Simulation (BAS) tools help companies test their cyber defenses.
Here is our list of the best BAS tools:
- AttackIQ – Provides real-time visibility and automated security validation with an easy-to-use interface. Ideal for its MITRE ATT&CK framework support and continuous testing capabilities. Its flexibility and ability to quickly prioritize remediations makes it ideal for most environments.
- Cymulate – Offers end-to-end cyber-risk management with quick installation and actionable insights. Its continuous testing and recommendations make it a top choice for dynamic environments.
- SafeBreach – Known for simulating an extensive range of attacks and offering continuous updates, SafeBreach excels in identifying and prioritizing security gaps.
- CyCognito – Specializes in attack surface visibility and risk detection and remediation, valuable for organizations seeking comprehensive vulnerability management.
- DXC Technology – Provides a wide range of cybersecurity solutions, including threat intelligence and advanced threat protection, suitable for multinational enterprises.
- Rapid7 – Features real-time reporting and a customizable dashboard for incident detection and response, emphasizing full network visibility and prioritization of vulnerabilities.
- Infection Monkey – As an open-source tool, it is effective for testing network adherence to zero-trust frameworks, scalable and suitable for various IT environments.
- Picus – Offers real-time network vulnerability insights and immediate feedback, making it a reliable choice for long-established security frameworks.
- XM Cyber – Focuses on end-to-end network scanning and continuous attack simulations, supported by advanced analytics, ideal for comprehensive threat detection and remediation.
Despite implementing various defensive security systems and attack programs, many IT teams do not find their cybersecurity strategy comprehensive enough to protect the company from unwanted threats. Also, most of the time, the IT teams don’t know how to assess the damage or find how effective the security system is as they have limited capabilities.
Experts might conduct security audits, penetration testing, red team testing, or follow other approaches. But getting an overall picture of the organization’s security is a hard task as these approaches have certain limitations.
To fill up the requirement, companies have shifted to a new tool that helps vendors test a network’s cyber defense. The BAS tools help protect crucial data by spotting vulnerabilities in the security environment and offering prioritized remediation guidance.
What is Breach and Attack Simulation?
BAS tools are powerful tools that most companies incorporate to test IT security efforts, continuously simulate attacks, and run scenarios. These tools help determine if the selected security measures or strategies are effective and serve the main purpose.
The tools update businesses on whether they are strong enough to withstand increasingly sophisticated attacks. Also, it helps discover weak spots or security gaps with continuous testing of the enterprise network.
Despite modern security controls, many organizations still face attacks. Hackers create hidden paths to enter your system and breach the data. With the help of BAS tools, companies can discover these hidden paths to critical assets and remediate security gaps.
Further, calculate the overall risk score, prioritize actionable remediation insights, and analyze the performance with these tools.
Why BAS?
Breach and Attack Simulation has now become a popular IT security technology that helps spot vulnerabilities automatically and performs penetration testing. Also, it aids businesses to test existing security components and provide useful insights. There are many reasons and benefits why most companies choose BAS tools over other security measures:
- Enables businesses to understand the stages of attack events
- Continuous simulation of cyber attacks
- Measure deployed security control
- Test threat hunting
- Validate security posture
- Adds more visibility to the network
- Offers automation and continuous monitoring of attackers
- Simulate malware attacks on endpoints that move laterally
- Identify vulnerabilities and prioritize remediation steps
- Alert on risks to the management
- Faster planning of security investments
- Provides continuous coverage by merging red and blue team techniques
- Risk management
- Provide awareness to attack paths
- Discover faults responsible for exposing critical assets
How to Select the Best Breach and Attack Simulation Tools?
Follow the below-listed steps to choose the best BAS Tools:
1. Understand the Level of Expertise
Before commencing the search for the right BAS tool for your organization, it is a must to analyze your ability to manage the popular tools. If you have an experienced team that can handle these tools, we recommend avoiding considering the easy-to-use feature.
Rather, you must switch to tools like Infection Monkey as they are open-source and do not require enough technical support. If your IT team lacks experience and is looking for an easy-to-use BAS tool, go with SafeBreach or Picus.
2. Learn about your network scenario complexities
BAS tools with a simple layout can deliver scanning results as per your expectations.
However, there are a few BAS tools with significant complexities that may expose your network to unusual vulnerabilities. Thus, when looking for a BAS tool, make sure to measure its complexity level for the network scenarios.
From the below list, AttackIQ provides maximum complex scenarios and can run in a short period. On the other hand, XM Cyber and Cymulate can run extreme scenarios.
3. Get suggestions and advice on how to fix problems
Do you think your team needs help deciphering the results of the scenario scans? If not, choose from any of the below-listed BAS tools. However, if you need suggestions on how to fix or remediate problems, you can pick between Rapid7 products or Cymulate.
You can also go with Infection Monkey if need some basic information about vulnerabilities on the network.
4. Benefit of Constant Updates
Lastly, think about your concern related to a cyber security failure or constant attacks. If you believe that your network will not be able to handle newly discovered attacks, choose the BAS tool from the shared list to help you with scenarios.
If you want a tool that offers constant updates related to the new scenarios, go for AttackIQ or SafeBreach.
The Best BAS Tools
By implementing BAS tools on the network, users add more security to their business data. Hackers are always on the move and make every attempt to put your security measures to test.
However, with the help of BAS tools, you can monitor the attacker’s move, make better decisions, and identify misconfigurations beforehand. Follow some of the below-listed best BAS tools that will allow you to discover weak spots or security gaps in advance. Avoid letting hackers take advantage of your weak spots with these powerful BAS tools.
Our methodology for selecting breach and attack simulation (BAS) tools
We’ve broken down our analysis for you based on these key criteria:
- Real-time insights and continuous validation of security controls
- Scalability across various environments including cloud, on-premises, and hybrid
- Integration with existing security infrastructure and compatibility with multiple platforms
- Capacity to simulate a broad range of attack scenarios, reflecting emerging threats
- Advanced reporting features for actionable insights and remediation strategies
1. AttackIQ
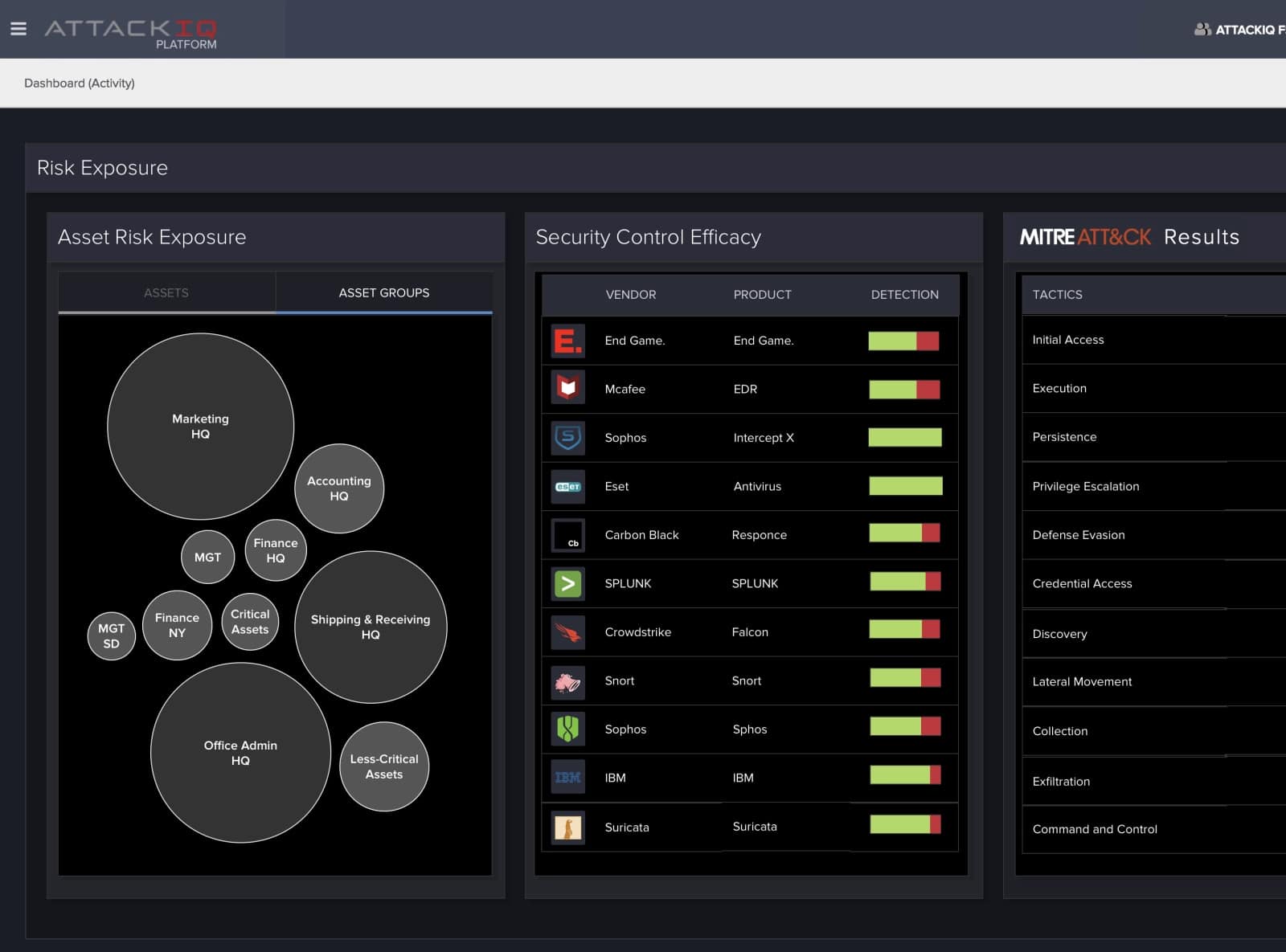
AttackIQ is a leading breach and attack simulation platform that provides real-time visibility and helps discover security gaps, identify misconfigurations, and prioritize remediation strategies. All you require is to deploy test point agents and run scenarios to get real-time insights on how the system responds to the emerging threats.
Key Features:
- Easy-to-use interface
- Supports MITRE ATT&CK framework
- Conducts threat-informed defense operations
- Real-time visibility of security posture
- Validates security controls
- Maps regulatory and compliance controls
- Performs continuous test
- Automated security validation
- Performs threat-informed operations
- Seamless integration
- Quick identification of misconfigurations and prioritizes remediation
- Takes little time to set up and implement
- Offers real-time insights
- Supports Windows, Linux, OSX platforms
- Compatible with cloud or on-premises environment
- Easily scales up
- Continuously generates new scenarios as per the emerging threats
- Built-in scenario inventory
- Automated reporting features
- Dedicated Slack channel
Why do we recommend it?
We recommend AttackIQ for its comprehensive features like real-time visibility, continuous testing, and support for the MITRE ATT&CK framework. The platform’s ability to quickly identify misconfigurations and prioritize remediation makes it a powerful tool for enhancing security posture.
Most companies trust the AttackIQ BAS tool as it helps test the security system’s effectiveness. It has an easy-to-use interface that allows administrators to run multiple tests continuously in a short period. It is an agent-based solution compatible with Windows, Linux, and OSX platforms. Also, the users can deploy the BAS tool on-premises or in the cloud environment.
AttackIQ can run complex scenarios in an extremely safe manner. It also has a strong research team to work on new security scenarios.
Who is it recommended for?
AttackIQ is ideal for organizations of all sizes that are focused on strengthening their security infrastructure. It is especially beneficial for security teams that want to conduct threat-informed defense operations and validate security controls in real-time, whether they are using cloud or on-premises environments.
Pros:
- Easy-to-use interface enhances user experience
- Real-time visibility into security posture
- Automated security validation streamlines operations
- Sorts remediations and misconfigurations by severity
- Supports a wide range of platforms and integrations
Cons:
- Setup and implementation may require technical expertise
EDITOR'S CHOICE
AttackIQ, a leading breach and attack simulation platform, is our top choice for its exceptional capabilities in providing real-time visibility into security gaps and prioritizing remediation strategies. Its deployment of test point agents and running of various scenarios offer insightful, real-time responses to emerging threats.
The platform’s user-friendly interface, seamless integration with existing systems, and comprehensive support for the MITRE ATT&CK framework make it an invaluable tool for any security team. Additionally, its compatibility with Windows, Linux, OSX, and adaptability to both cloud and on-premises environments, coupled with the ability to scale up and continuously generate new scenarios, positions AttackIQ at the forefront of security innovation.
Download: Request a Demo
Official Site: https://attackiq.com/
OS: Windows, Linux, macOS; Cloud-Based or On-Premises
2. Cymulate
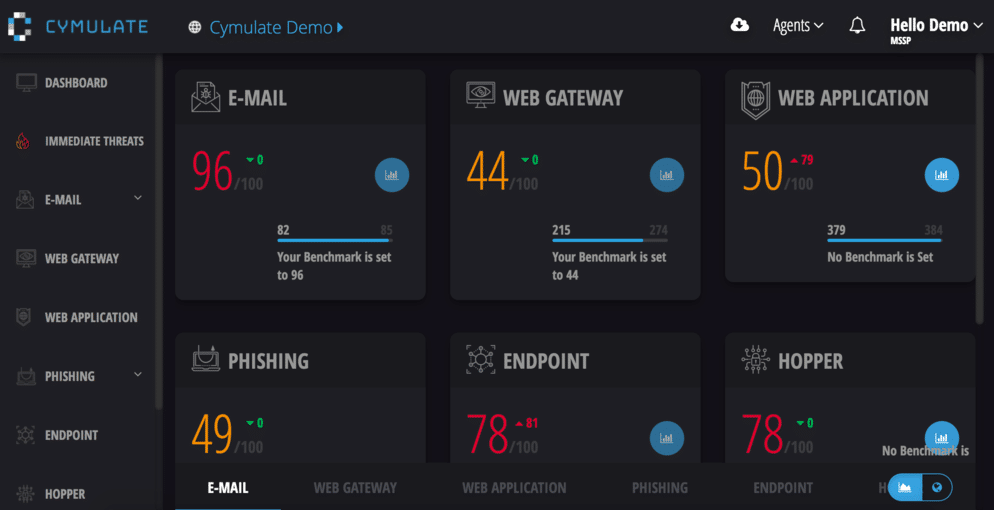
Cymulate is a popular breach and attack simulation platform that automatically identifies security gaps and tests its strength by exposing itself to real-life attacks. It also simulates attacks in prescheduled intervals and generates insightful reports for analysis and recommendations.
Key Features:
- End-to-end cyber-risk management
- Prioritize mitigation
- Security posture visibility
- Quick installation features
- Offers actionable insights
- Advanced attack campaigns
- Covers the entire kill-chain
- Assessment management
- Security auditing
- Vulnerability scanning
- Supports third-party integrations
- Removes false positives
- Offers continuous testing and recommendations, and instant threat alerts
- IOC Verification
- Fully automated and customizable BAS tool
- Data exfiltration
- Lateral movement
- Simulate malicious inbound traffic
- Runs customized phishing campaigns
Why do we recommend it?
We recommend Cymulate for its extensive range of features that not only identify security gaps but also offer actionable insights. Its ability to cover the entire kill chain while running in the background ensures that business operations are not disrupted, making it a valuable asset for any organization.
Cymulate is the best choice if you want to run the BAS tool in a short period. It is a SaaS-based solution that optimizes security posture and makes efforts to protect business-critical assets from threats or attacks at all times. Users can monitor and track thousands of attack simulations with the help of its exclusive features.
It covers the entire kill chain and runs in the background without affecting or slowing down business operations. Many small businesses and large enterprises trust Cymulate as it has an easy-to-use interface. Also, it is fast and easy to deploy a BAS tool that requires minimal investments. Its exclusive features enable businesses to stay ahead of potential cyberattacks.
Who is it recommended for?
Cymulate is recommended for both small businesses and large enterprises looking to optimize their security posture without slowing down day-to-day operations. It’s particularly useful for organizations that require a fully automated and customizable BAS tool that can offer continuous testing and instant threat alerts.
Pros:
- Comprehensive cyber-risk management
- Quick installation and setup
- Provides immediate, actionable insights
- Advanced attack campaign simulations
Cons:
- May require regular updates to maintain effectiveness
3. SafeBreach
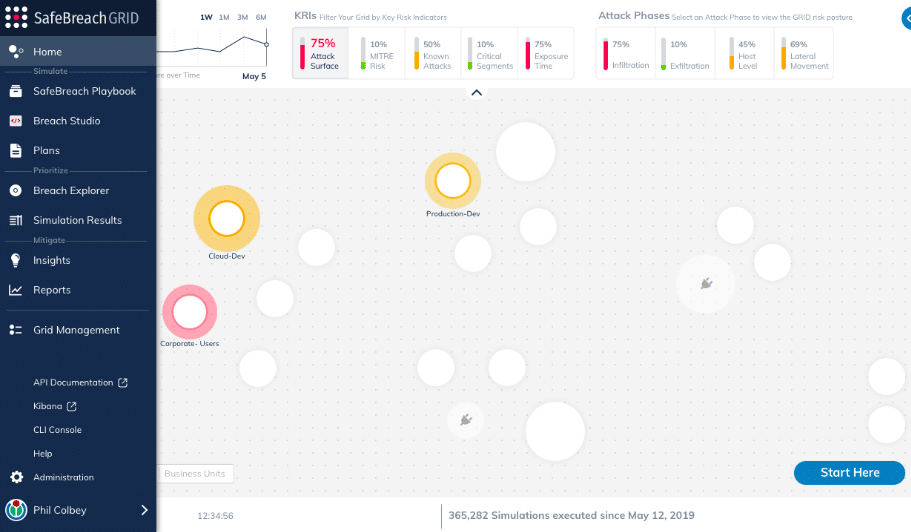
SafeBreach is one of the first and oldest BAS tools introduced to the market. The tool runs scenarios for the latest attacks that originated inside or outside the organization. Further, it helps identify security gaps and prioritizes them as per the security issues.
Key Features:
- Ability to simulate 15,000+ attacks
- Easy-to-install
- Generates quality reports in minutes
- Assesses network risk
- Strong customer base
- Compatible with all cloud and endpoint networks
- Offers constant updates
- Lateral movement
- Identifies uncovered security gaps
- Prioritizes threats and vulnerabilities
- Easy to deploy and integrate
- Continuous validation of security controls
Why do we recommend it?
We recommend SafeBreach because of its extensive experience and strong customer base in the BAS market. The tool’s ability to simulate over 15,000 different types of attacks and offer continuous updates makes it a reliable choice for identifying and prioritizing security gaps.
If you are looking for a BAS tool that has been in the market for a long time and has built strong trust among customers, we recommend SafeBreach. It can simulate 15000+ attacks and provides regular updates to users.
Also, it is quite easy to install, deploy, and integrate SafeBreach. With the help of its insightful, actionable reports, administrators can quantify business risk and prioritize investments in network security.
It analyzes the system from a hacker’s perspective and uses a wide range of breach methods to spot weaknesses in an organization’s cyber defense system.
Who is it recommended for?
SafeBreach is recommended for organizations of all sizes that are looking for a well-established, easy-to-deploy BAS tool. It’s particularly suitable for companies wanting to understand their vulnerabilities from a hacker’s perspective and prioritize threats effectively based on insightful, actionable reports.
Pros:
- Simulates over 15,000 attack types
- Generates detailed reports swiftly
- Compatible with various networks
- Strong customer trust and market presence
Cons:
- May require specific configurations for optimal use
4. CyCognito
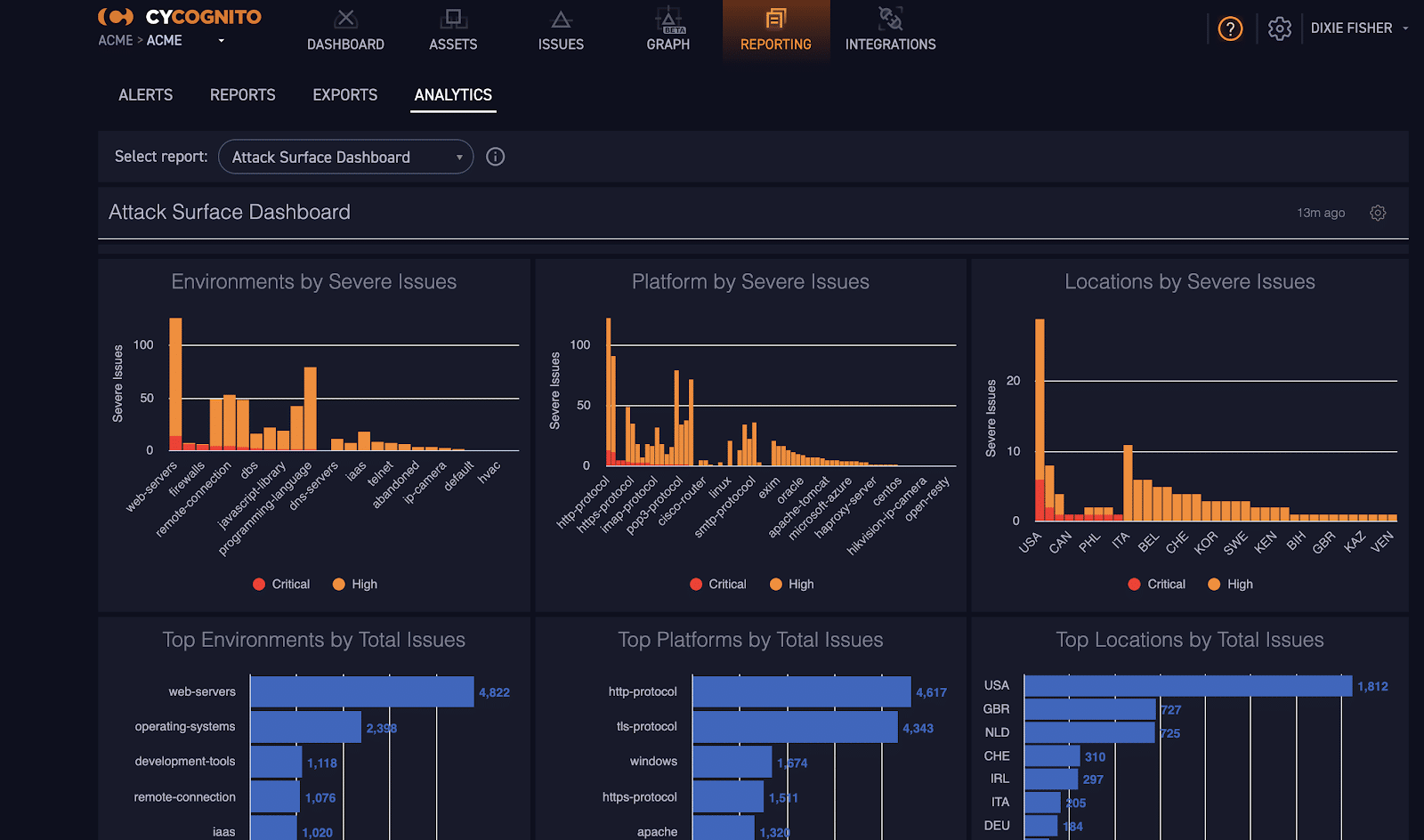
CyCognito is a leading cloud-based vulnerability management BAS tool that was introduced in 2017. The main purpose of introducing CyCognito was to help businesses monitor and detect advanced threats. Further, eliminate and remediate critical security risks across enterprise assets.
Key Features:
- Helps detect and prioritize risks faster
- Provides continuous attack surface visibility
- Attack surface management
- Compatible with cloud, on-premises, and other environments
- Maps the vulnerable assets
- Comprises workflow automation capabilities
- Vulnerability management and scanning
- Advanced analytics tools
- Security frameworks & compliance
- Remediates faster
Why do we recommend it?
We recommend CyCognito for its robust capabilities in attack surface visibility and fast risk detection and remediation. Its advanced analytics tools and workflow automation make it a comprehensive solution for vulnerability management.
With the help of CyCognito, administrators can automate offensive cybersecurity operations, monitor all risks generated by the attackers, and focus on how to fix the security gaps. Get more clarity on how attackers view your organization and break in using CyCognito in-built features.
Businesses that trust CyCognito can scan up to 300% more assets than exist on the network. Also, it enables administrators to define risk categories and prepare for advanced attacks.
Who is it recommended for?
CyCognito is best suited for businesses that require continuous monitoring and remediation of security risks across a variety of environments, including cloud and on-premises. It is especially useful for organizations looking to automate offensive cybersecurity operations and expand their risk detection capabilities.
Pros:
- Efficient detection and prioritization of risks
- Offers continuous attack surface visibility
- Streamlines vulnerability management
- Compatible across various environments
Cons:
- The depth of analytics may require skilled interpretation
5. DXC Technology
More than 70+ countries use DXC Technology tailored with high-class security solutions for digital businesses. DXC Technology was introduced with various in-built features to reduce risks and help businesses stay ahead of attackers. It provides threat intelligence feeds, advisory services, monitoring and incident response, etc.
Key Features:
- Manages incident response and threats
- OT and IoT security
- Threat intelligence feeds
- Automated security services
- Managed SIEM
- Protect data with a zero-trust strategy
- Offer full visibility to the network
- Advanced threat protection
- Multifactor authentication
- Privileged account management
- Cyber Defense services
Why do we recommend it?
We recommend DXC Technology for its comprehensive suite of security solutions, including incident response management, OT and IoT security, threat intelligence feeds, and advanced threat protection. It offers a holistic approach to cybersecurity, making it suitable for organizations looking to protect their digital assets effectively.
Secure your applications and data with the amazing BAS tool that offers advanced threat protection. It also provides full visibility to the networks using its cyber defense services and protects critical assets from breaches.
The popular tool also encourages users to verify their digital identities and adopt multifactor authentication features to secure data and services. Administrators can further track attackers, optimize data architectures, and secure information across public, private, and hybrid clouds.
Who is it recommended for?
DXC Technology is recommended for businesses operating in various industries and across multiple countries. It is particularly beneficial for organizations that require robust incident-response management, threat intelligence, and advanced threat protection to safeguard their digital assets and maintain a strong security posture.
Pros:
- Extensive incident response capabilities
- Offers advanced threat protection
- Provides threat intelligence feeds
- Zero-trust strategy for data protection
Cons:
- The complexity of services might be overwhelming for smaller businesses
6. Rapid7
Rapid7 is a best-in-class solution with various products that help detect suspicious behavior, spot critical threats, and remediate quickly. It is one of the best BAS tools that scans the entire network and provides detailed reports explaining the network vulnerabilities.
Key Features:
- Offers real-time reporting
- Customizable and easy-to-use dashboard
- Attack surface monitoring
- Universal translator to uncover vulnerabilities
- Offers unparalleled attacker insights
- Helps prioritize vulnerabilities and misconfigurations
- Supports 95+ attack types and practices to address issues
- Attack replay
- Vulnerability risk management
- Scans multiple environments simultaneously
- Immediate feedback
- Identifies external threats
Why do we recommend it?
We recommend Rapid7 for its comprehensive suite of security solutions, real-time reporting, and customizable dashboard. It excels in detecting suspicious behavior, identifying critical threats, and providing actionable insights for remediation. Rapid7’s ability to scan multiple environments simultaneously and support various attack types makes it a robust choice for improving security posture.
The software also provides recommendations related to fixing problems. One can easily identify and remediate external threats using Rapid7 products. Its in-built features enable businesses to create a smooth path and minimize compliance challenges. Furthermore, the solution helps discover the weak spots in all environments.
With its insightful data and reports, administrators get full visibility into the network and can prioritize vulnerabilities and misconfigurations just like the attackers. It supports the cloud-SIEM and XDR approach to create more signals and less noise. Another advantage of Rapid7 is it supports orchestration and automation features that help spot threats and respond faster.
Who is it recommended for?
Rapid7 is recommended for organizations of all sizes that prioritize proactive security measures. It is particularly valuable for businesses seeking real-time threat detection, vulnerability management, and incident response capabilities. Rapid7’s user-friendly interface and automation features make it suitable for both security professionals and IT teams looking to enhance their security defenses.
Pros:
- Real-time reporting enhances responsiveness
- Customizable dashboard for tailored use
- Supports a wide range of attack types
- Comprehensive vulnerability risk management
Cons:
- Some features may require advanced technical knowledge for optimization
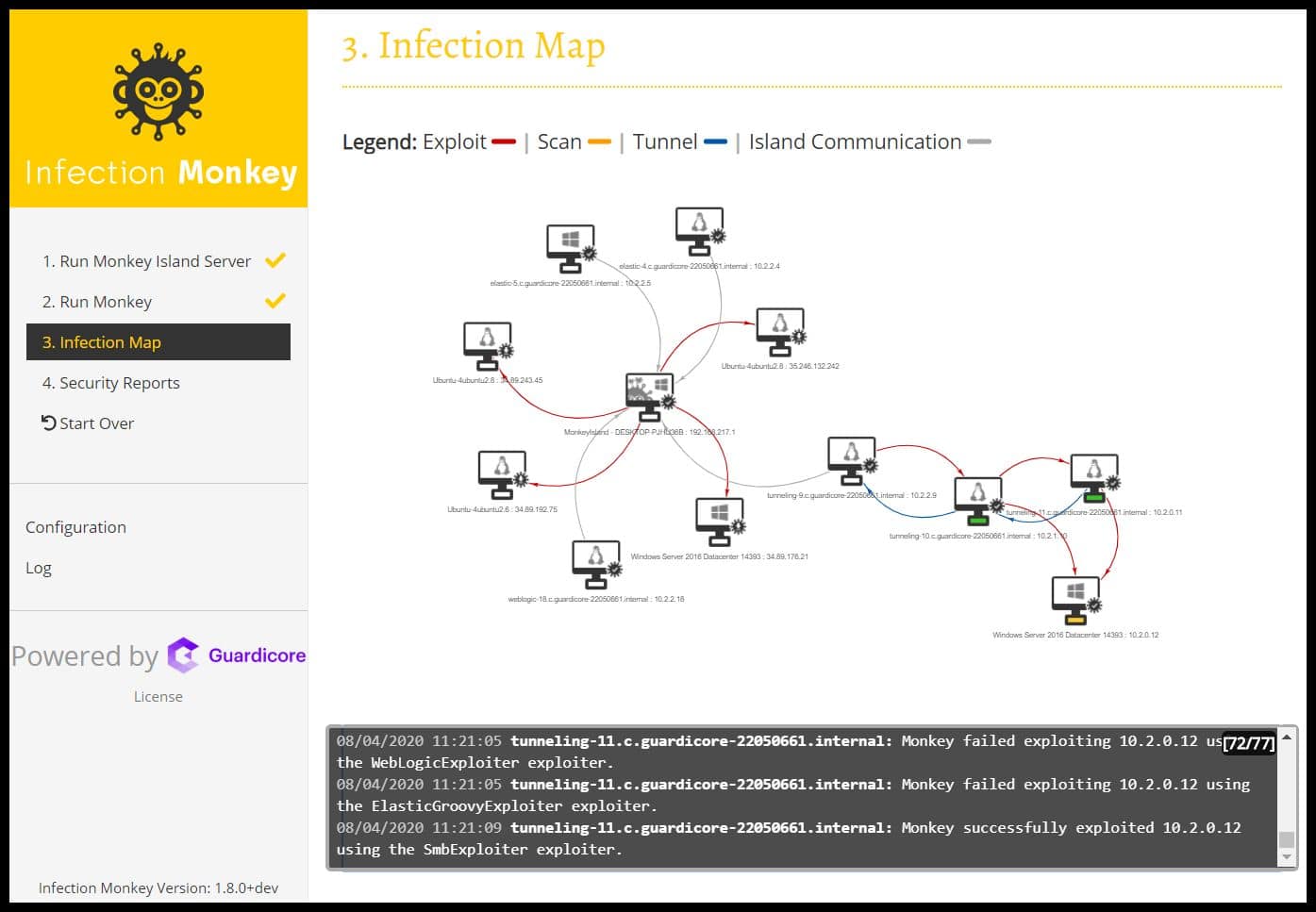
7. Infection Monkey
Infection Monkey is a free, open-source security tool that most IT teams use to test network adherence to a zero-trust framework. It is an easy to deploy, secure, and stable tool with an intuitive user interface. The purpose to design Infection Monkey was to help organizations discover and map the attacker’s move.
Key Features:
- Free and open-source
- Intuituve user interface
- Strong reporting features
- Compatible with on-premises, containers, and cloud-based environments
- Allows continuous testing of network security
- Developed under the GPL v3 license
- Analysis and in-depth testing
- Visualizes and maps the attacker moves
- Scalable and easy to deploy
- Automates attack simulation without impacting network operations
- Generates audit report
- Supports installation on Debian, Windows, and Docker
- Low CPU and footprint memory
Why do we recommend it?
We recommend Infection Monkey for its effectiveness in testing network adherence to a zero-trust framework. This free and open-source tool is easy to deploy, secure, and stable, making it an excellent choice for organizations looking to discover and map potential attacker movements within their network.
Infection Monkey has become a notable open-source software over the years. It is trusted by large organizations as it helps them discover weaknesses in their on-premises and cloud-based environments. Further, it supports a wide range of MITRE ATT&CK techniques for testing.
Another advantage of choosing open-source software is it helps generate strong actionable reports. With the help of these insightful reports, users can identify exact machines carrying vulnerabilities. Also, it includes recommendations on how to protect the network from cyber criminals.
Who is it recommended for?
Infection Monkey is recommended for IT teams and organizations of all sizes that want to continuously test their network security posture. It is particularly valuable for those seeking a scalable and easy-to-deploy solution compatible with various environments, including on-premises, containers, and the cloud. Infection Monkey’s intuitive user interface and detailed reporting capabilities make it suitable for security professionals and IT administrators focused on identifying and addressing vulnerabilities effectively.
Pros:
- Free, open-source software with low overhead
- Intuitive user interface facilitates ease of use
- Capable of in-depth testing and analysis
- Supports a variety of installation environments
Cons:
- Open-source nature may require internal expertise for maintenance
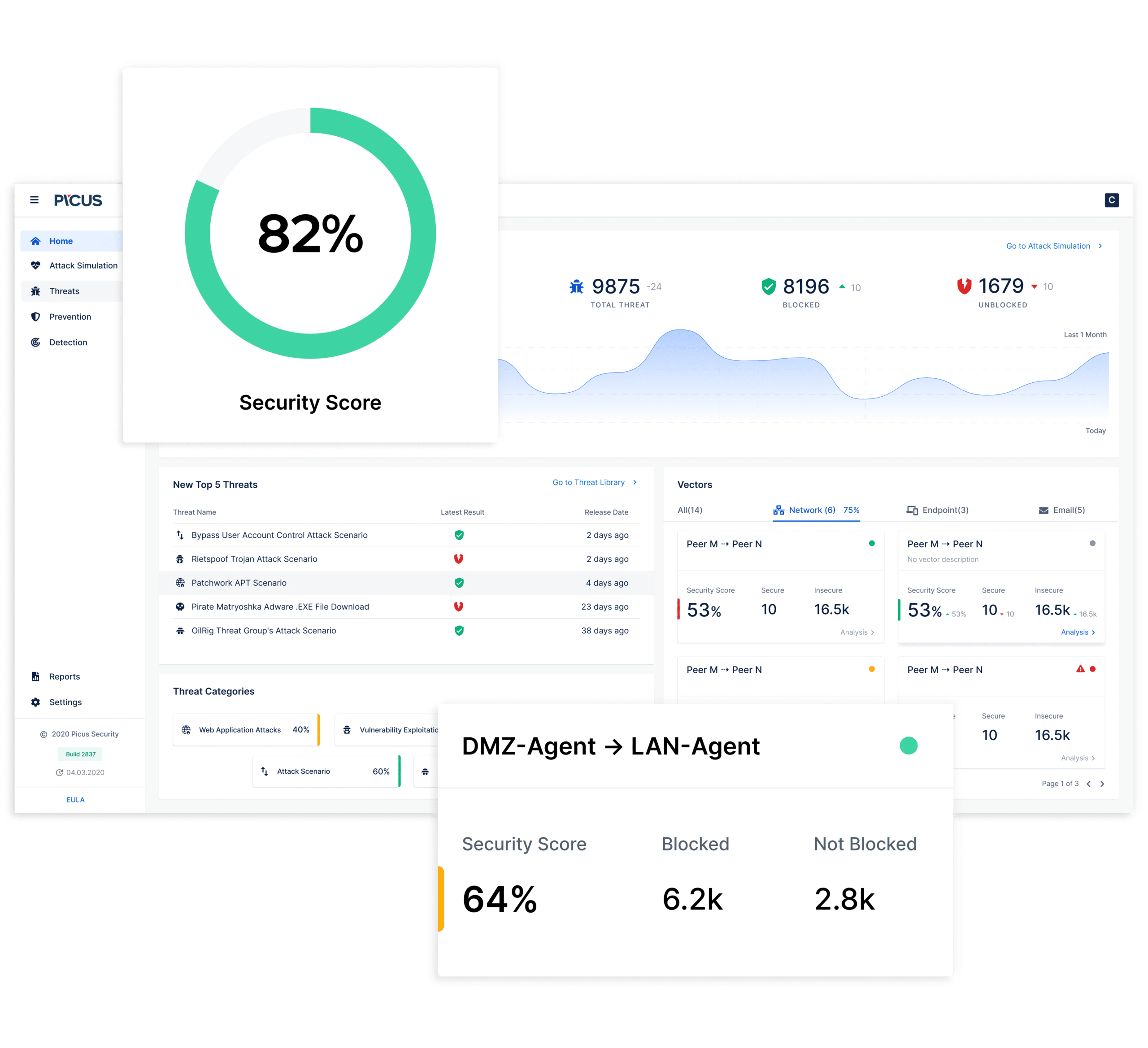
8. Picus
Picus has been in the market for nearly a decade and is one of the great BAS tools. It provides real-time data on network vulnerabilities and offers immediate feedback. The product is specifically designed for cybersecurity professionals to analyze and detect threats before the attacker makes a move.
Key Features:
- Provides immediate feedback
- Real-time network vulnerabilities
- Quick installation and easy to run
- Provides insightful reports and focuses on the vulnerable areas of a network
- Offers continuous and up-to-date attack scenarios
- Supports 100+ APT and malware scenarios
- Offers endpoint security
- Log & alert gaps discovery
- Pinpointed log sources
- Activity monitoring
- Threat response
- Policy management
- Supports advanced useability and filtering features
- Watchlists
Why do we recommend it?
We recommend Picus for its nearly decade-long presence in the market, and its ability to provide real-time data on network vulnerabilities. It offers immediate feedback, making it a valuable tool for cybersecurity professionals who want to proactively analyze and detect threats before attackers can exploit them.
Another reason why most vendors trust Picus security over other tools is thst it hardly takes any time to install, and is highly flexible. Unlike other BAS tools, Picus runs simulations within a short period. Also, the tool is easy to use with exclusive reporting tools, and can handle complex simulations.
As one of the oldest BAS tools, Picus Security has a strong customer base and offers continuous and up-to-date attack scenarios and simulations. Another benefit of using Picus is it helps discover log and alert gaps.
Who is it recommended for?
Picus is recommended for cybersecurity professionals and organizations seeking a BAS tool with a proven track record. It is ideal for those who prioritize quick installation and ease of use, as Picus runs simulations efficiently. The tool’s insightful reports focus on vulnerable areas within a network, and it offers continuous and up-to-date attack scenarios. Picus supports a wide range of APT and malware scenarios, making it suitable for advanced threat detection.
Pros:
- Provides real-time network vulnerability data
- Quick installation and user-friendly operation
- Continuous, up-to-date attack scenario coverage
- Supports a wide range of APT and malware scenarios
Cons:
- May require regular updates for the latest threat scenarios
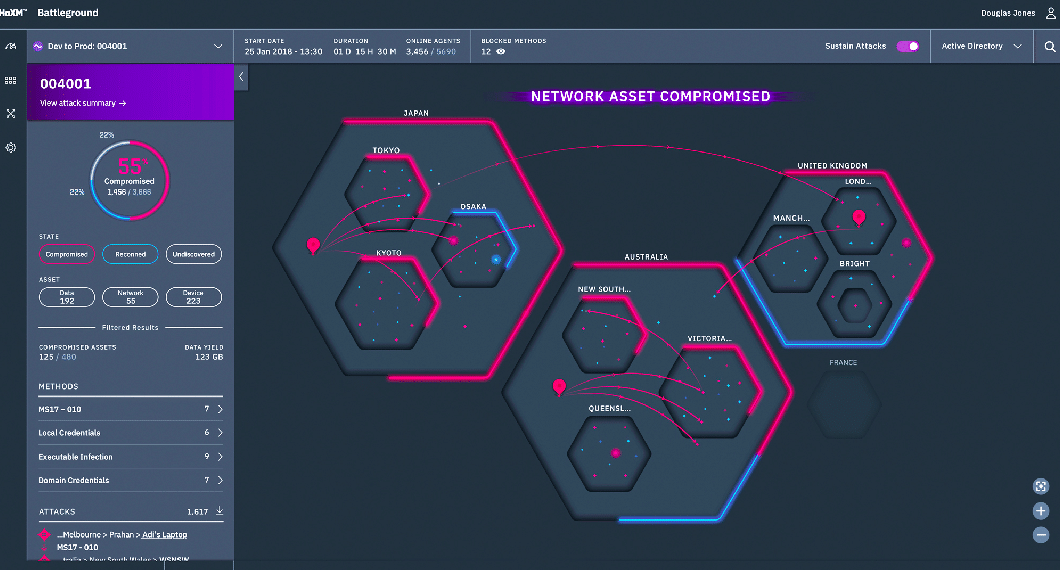
9. XM Cyber
XM Cyber is another powerful breach and attack simulation tool launched in 2016 that automatically runs attack simulation processes in the background and discovers attacks before they happen. It uses Attack Path Management features to monitor the hybrid network and spot attackers.
Key Features:
- Offers end-to-end network scanning
- Discovers vulnerabilities and suggests remediation efforts
- Continuously simulates attacks
- Patch management
- Security posture visibility
- Users can view all critical attack paths
- Supports advanced analytics features
- Scalable and easy to deploy regardless of location
- Attack graph
- Offers faster remediation
Why do we recommend it?
We recommend XM Cyber for its powerful capabilities in breach and attack simulation. The platform stands out for its ability to automatically run attack simulation processes in the background, proactively discovering attacks before they occur. XM Cyber offers end-to-end network scanning, continuously simulates attacks, and provides insights into vulnerabilities, helping organizations prioritize and implement remediation efforts effectively.
Formerly known as HaXM, the powerful tool provides end-to-end scanning of the networks and operates continuously without affecting your network performance.
With the help of XM Cyber, users can manually select attack targets and observe the simulations. Also, it helps uncover all the hidden attack paths across different network environments, and reduces the chances of internal attacks. It supports various advanced analytics tools that pinpoint locations to target for disrupting attack paths. Furthermore, the tool uses the attacker’s perspective and offers advice on remediation efforts.
XM Cyber is a highly scalable and easy-to-deploy BAS tool that offers real-time visibility and allows users to spot hidden connections leading a path to put all your critical assets at risk.
Who is it recommended for?
XM Cyber is recommended for organizations looking for a robust breach and attack simulation tool that can detect and mitigate threats in real-time. It is suitable for security professionals who want to monitor hybrid networks, discover vulnerabilities, and gain visibility into attack paths. XM Cyber’s advanced analytics features and attack graph capabilities make it ideal for those seeking comprehensive threat detection and remediation solutions. Whether for large enterprises or small businesses, XM Cyber offers scalable protection against potential attacks.
Pros:
- Automated, continuous attack simulation
- Provides end-to-end network scanning
- Offers insights for faster remediation
- Scalable across various network environments
Cons:
- Advanced features may require skilled personnel for full utilization
Final Thoughts
Data breaches and threat growth are a few common lasting issues that most businesses face within cyber security. On one end, where growth in cloud computing has improved scalability and flexibility, it has also increased the risk factors. Nowadays, managing risk in a hybrid environment is quite challenging.
A large number of malware and attackers run on clouds and networks daily. To fix it and maintain robust organizational security, many companies have launched malware programs in the past. However, to check how effective is the security system, one must switch to breach and attack simulation (BAS) platforms.
These platforms provide continuous monitoring and automated testing features. However, selecting the best one is the key. Remember each BAS tool has its own feature and purpose. The only way to find the right tool for your organization is to select the BAS tool on the basis of its core features.
A perfect BAS solution enables organizations to detect misconfigurations, identify security gaps, and simulate attacks in the cloud. It must have the capability to identify gaps and prevent them in hybrid environments. The right BAS tool will help assess their risk posture and understand how attackers enter the on-premises devices or access the cloud data.
Instead of assessing the risk associated with cloud and on-premises risks separately, it is best to invest in a tool that is compatible with all environments. It also helps understand how each environment affects the other.
Attackers often create hidden paths to run into the system. It is best to find a tool that can simulate Advanced Persistent Threats (APTs), test security controls, and discover attack pathways.
Lastly, check if the above-listed BAS tool offers prioritized remediation of security gaps and validates security controls. If a tool comprises most of the above-listed core features, select it as it will provide your organization with better risk assessment and protection. Go through the above list of BAS tools, compare their features, and select the one as per your budget and organizational security requirement.