A progress page will show the packages as they are downloaded and installed:
Choose where you want icons:
Start cygwin by double clicking on the icons (wherever). Some initial configuration will take place automatically:
Copying skeleton files. These files are for the user to personalise their cygwin experience. These will never be overwritten. `./.bashrc' -> `/home/Administrator//.bashrc' `./.bash_profile' -> `/home/Administrator//.bash_profile' `./.inputrc' -> `/home/Administrator//.inputrc' Administrator@win1 ~ $ |
Run the ssh-host-config script, and answer the questions:
$ ssh-host-config Generating /etc/ssh_host_key Generating /etc/ssh_host_rsa_key Generating /etc/ssh_host_dsa_key Generating /etc/ssh_config file Privilege separation is set to yes by default since OpenSSH 3.3. However, this requires a non-privileged account called 'sshd'. For more info on privilege separation read /usr/share/doc/openssh/README.privsep. Should privilege separation be used? (yes/no) yes Warning: The following function requires administrator privileges! Should this script create a local user 'sshd' on this machine? (yes/no) yes Generating /etc/sshd_config file Added ssh to C:\WINDOWS\system32\drivers\etc\services Warning: The following functions require administrator privileges! Do you want to install sshd as service? (Say "no" if it's already installed as service) (yes/no) yes You appear to be running Windows 2003 Server or later. On 2003 and later systems, it's not possible to use the LocalSystem account if sshd should allow passwordless logon (e. g. public key authentication). If you want to enable that functionality, it's required to create a new account 'sshd_server' with special privileges, which is then used to run the sshd service under. Should this script create a new local account 'sshd_server' which has the required privileges? (yes/no) yes Please enter a password for new user 'sshd_server'. Please be sure that this password matches the password rules given on your system. Entering no password will exit the configuration. PASSWORD=password User 'sshd_server' has been created with password 'password'. If you change the password, please keep in mind to change the password for the sshd service, too. Also keep in mind that the user sshd_server needs read permissions on all users' .ssh/authorized_keys file to allow public key authentication for these users!. (Re-)running ssh-user-config for each user will set the required permissions correctly. Which value should the environment variable CYGWIN have when sshd starts? It's recommended to set at least "ntsec" to be able to change user context without password. Default is "ntsec". CYGWIN=ntsec The service has been installed under sshd_server account. To start the service, call `net start sshd' or `cygrunsrv -S sshd'. Host configuration finished. Have fun! Administrator@win1 ~ $ |
Start the service:
$ net start sshd The CYGWIN sshd service is starting. The CYGWIN sshd service was started successfully. Administrator@win1 ~ $ |
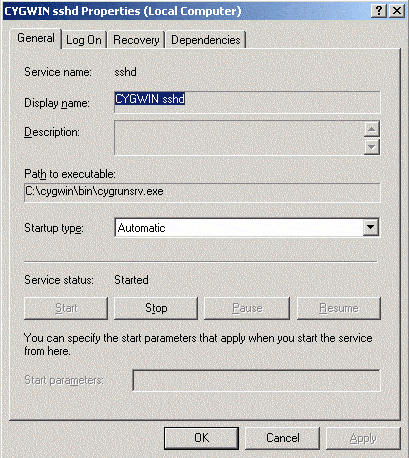
Here is the Windows service information:
Test out SSH:
[usr-1@srv-1 ~]$ ssh administrator@10.50.100.112 The authenticity of host '10.50.100.112 (10.50.100.112)' can't be established. RSA key fingerprint is 28:d1:72:f3:02:fa:46:ba:80:3a:61:86:18:6a:3b:4d. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.50.100.112' (RSA) to the list of known hosts. administrator@10.50.100.112's password: Administrator@win1 ~ $ |
If you would like to copy your public key over to the server, make a directory for it on the Windows box with SSHd:
$ mkdir ~/.ssh |
If you don’t have a public key, that is beyond the scope of this article. A hint is that you need to use ssh-keygen -t dsa; however, there are implications to this and better ways to do it in some cases. Let’s assume you have an id_dsa.pub key, copy it over, and log on, this time without having to enter a password:
[usr-1@srv-1 ~]$ scp ~/.ssh/id_dsa.pub administrator@10.50.100.112: ~/.ssh/authorized_keys2 administrator@10.50.100.112's password: id_dsa.pub 100% 621 0.6KB/s 00:00 [usr-1@srv-1 ~]$ ssh administrator@10.50.100.112 Last login: Fri Mar 17 14:47:04 2006 from sv-1 Administrator@win1 ~ $ |
We can now run some simple remote commands to get CPU and memory info from the Windows server:
[usr-1@srv-1 ~]$ ssh administrator@10.50.100.112 'cat /proc/meminfo' total: used: free: Mem: 964116480 231288832 732827648 Swap: 1447034880 8290304 1438744576 MemTotal: 941520 kB MemFree: 715652 kB MemShared: 0 kB HighTotal: 0 kB HighFree: 0 kB LowTotal: 941520 kB LowFree: 715652 kB SwapTotal: 1413120 kB SwapFree: 1405024 kB [usr-1@srv-1 ~]$ ssh administrator@10.50.100.112 'cat /proc/cpuinfo' processor : 0 vendor_id : GenuineIntel type : primary processor cpu family : 15 model : 1 model name : Intel(R) Pentium(R) 4 CPU 1.70GHz stepping : 2 brand id : 8 cpu count : 1 apic id : 0 cpu MHz : 1715 fpu : yes flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clfl dtes acpi mmx fxsr sse sse2 ss htt tmi [usr-1@srv-1 ~]$ |
An excellent resource is How to install OpenSSH sshd server and sftp server on a Windows 2000 or Windows XP or Windows Server 2003 by Nicholas Fong.