[January 5 update: Microsoft released a fix for this vulnerability available here. The below information has some related procedures that may be useful. ]
There is a zero day expoit in the wild that can infect your Windows system via email and web browsing. There is no known fix yet, but there is a workaround for known methods of attack. The workaround is to unregister the Windows Picture and Fax Viewer dll file. The published workaround here is to click start, then click run, and enter:
regsvr32 -u %windir%\system32\shimgvw.dll |
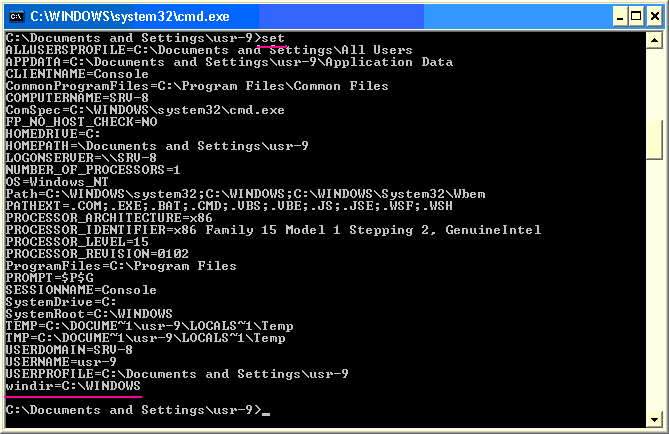
That is fine and all if you like throwing around environment variables. We prefer to nibble at this a bit. Go to a command line by clicking start->run->cmd, or however you normally get to a command prompt. Determine where your root windows directory is. On ours, this is c:\windows. You can determine this by running the set command. The set command will show all of your environment variables. The entry for windir is where your root Windows directory is:
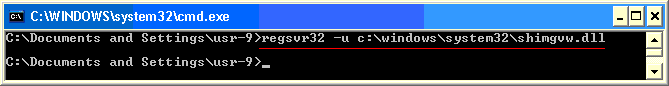
Notice that the path in the title bar also shows the path to the location of the system32 directory. To unregister the Windows Picture and Fax Viewer dll, run the regsvr32 command with the -u option against the shimgvw.dll library file:
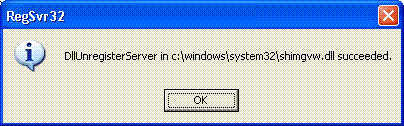
You will see a confirmation that the unregister command was successful:
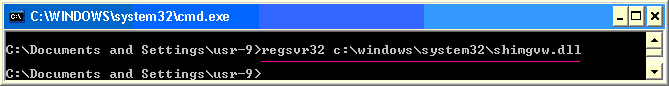
Once the patch has been released, to return to the same functionality the library file can be re-registered by omitting the -u option:
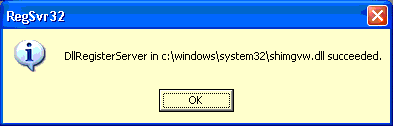
You will see a confirmation that the register command was successful:
Update your virus sigs, run Windows Update, and generally be vigilant during the coming weeks as different iterations of the patch are released. Probably Microsoft will release a quickee patch, and then they will actually fix the problem. We’ll see. For details on this, see the CERT notice.