There is a false sense of security when you envision your network as inside and outside, with a firewall protecting you from hostile users on the outside.
One particularly nasty problem is when users bring their laptops home, surf, read email, and then plug it right back in to the corporate LAN on Monday morning.
Windows Server 2003 has a fairly flexible host based firewall that you can install to protect your servers from those inside your main firewall.
Here is an Nmap scan of a fresh install of Windows Server 2003 with IIS, and the default client, printer, and file sharing for Microsoft Networks enabled:
[usr-1@srv-1 ~]$ nmap -sV 10.50.100.112 Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2005-08-03 17:09 EDT Interesting ports on 10.50.100.112: (The 1655 ports scanned but not shown below are in state: closed) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS webserver 6.0 135/tcp open msrpc Microsoft Windows msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds Microsoft Windows 2003 microsoft-ds 1025/tcp open msrpc Microsoft Windows msrpc Nmap run completed -- 1 IP address (1 host up) scanned in 42.176 seconds |
Let’s block everything going to this server except port 80, the HTTP port that IIS uses by default, and the standard port for HTTP.
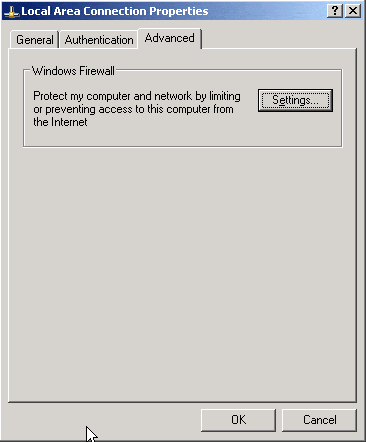
First, go into the Local Area Connection Properties and click the Advanced tab:
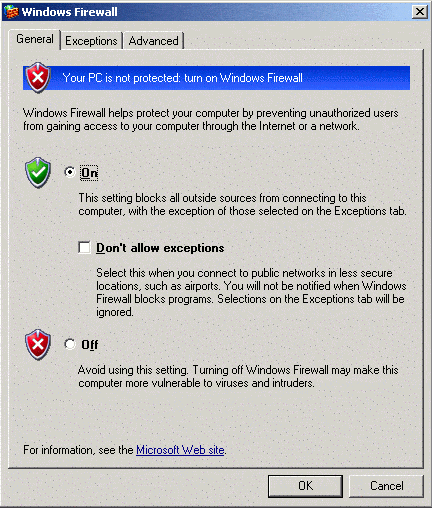
Click the settings button. Click the On radio button:
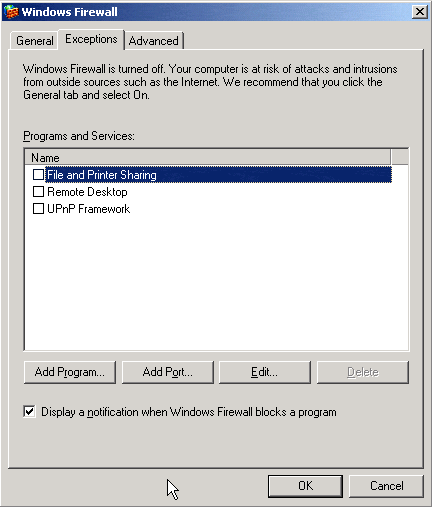
Click the Exceptions tab, and click Add Port:
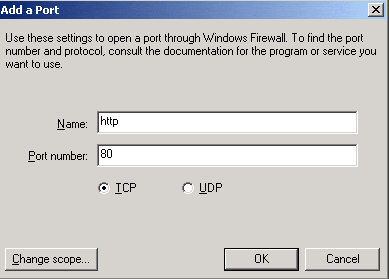
Enter http (or whatevery you want to call the service), and type 80 in the Port number box:
Click OK until all of the dialog boxes are closed.
The service will be running correctly right away without a reboot.
Let’s run another scan and make sure everything is being blocked except for port 80:
[usr-1@srv-1 ~]$ nmap -sV 10.50.100.112 Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2005-08-03 17:19 EDT Interesting ports on 10.50.100.112: (The 1659 ports scanned but not shown below are in state: filtered) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS webserver 6.0 Nmap run completed -- 1 IP address (1 host up) scanned in 37.085 seconds [usr-1@srv-1 ~]$ |
We are good.
Now, this box is locked down so well that it will be difficult to authenticate users against a domain or share files, of course, but that may be desired in some cases.
Choose what ports you have to have open and specifically allow those ports if needed.
Disallow the rest by default.
If you don’t need full time access to file shares on your webserver, consider only allowing access when you prop the new site.