You must have heard of the term “API,” but do you know what it means?
The word “API” stands for Application Programming Interface. It enables two or more software to interact with each other and complement or leverage each others’ capabilities without knowing the intricate and code details of either software. In other words, the API acts as a bridge for two pieces of software to interact and work with each other.
APIs also facilitate the easy transfer of data between applications to be connected to a larger workflow within the organization. To give you an example, let’s say you use a tool called Slack for communications within your organization and Atlassian Jira for tracking issues, tasks, and performance. An API allows you to create a ticket on Jira from a message on Slack. In this sense, both the tools are connected as a part of a larger workflow and enable seamless access to each other.
Undoubtedly, APIs are highly beneficial, and this is why enterprises and developers spend so much time developing them. That said, there’s also a security issue with APIs as they expose data to the outside world. If an unauthorized application or entity uses API to connect to another application within the organization, it’s possible to steal the data easily.
Further, APIs are often seen as the access door for backend systems and databases and thus exposes the entire infrastructure to the outside world.
Security Vulnerabilities and Attacks Through APIs
Security controls and precautions are an absolute must as APIs can pose a severe threat to an organization’s security. In particular, it can facilitate the following attacks on your infrastructure.
- Distributed Denial of Service (DDoS) In these attacks, a system or a hacker floods a network with an enormous amount of requests. As a result, its resources get exhausted in handling these floods of requests, and eventually, the system crashes or becomes unavailable to users.
- Credential stuffing This is an attack where credentials stolen from genuine users are used on APIs to access the network.
- Cross-site Scripting In this attack, a malicious code is inserted through APIs into an organization’s applications and network. Depending on the purpose, this code can crash the website or provide unauthorized access to specific applications.
- Injection It is similar to cross-site scripting, except that the former taps into an existing vulnerability to gain access. In injection, APIs are used in standard inputs such as username and password to access applications.
Besides the above types of attacks, hackers are coming up with new ways to access proprietary systems and networks through APIs. All these make it necessary to secure your APIs and prevent them from accessing unauthorized users or programs.
So, this brings up the next question – how can you make your APIs secure?
A combination of best practices and tools are required to secure your APIs, and both these must work in tandem to provide complete protection.
Best Practices for API Security
Here’s a look at some of the practices that must be implemented to boost API security.
- Create a Security-Centric Approach In many organizations, security is an afterthought, and unfortunately, such an approach is thoroughly exploited by hackers.
- Make security a priority today and see how best you can incorporate it in all aspects of your organization. Work with experts if needed to build security into your APIs as they are developed and use third-party tools to secure the existing APIs.
- Manage your APIs The first step to managing your APIs is to know what is available in the first place. Start with an inventory of your APIs, where you store their name, functionality, the applications that use them, and more. Next, do an audit of their security to understand which applications can access them and decide on a plan of action to secure them. Finally, work closely with the DevOps team to efficiently connect and manage these APIs.
- Improve Authentication Measures A poor authentication mechanism coupled with a ton of publicly available APIs is a recipe for disaster. You must beef up the authentication and authorization measures in the organization to ensure that only the right people and software can access your networks through the API. Consider using strict access controls and authorization mechanisms like OpenID Connect.
- Embrace Encryption If your APIs transmit sensitive information like login credentials, encryption is an effective way to protect unauthorized people from using these credentials to log into your system. While some organizations may believe that non-sensitive data don’t have to be encrypted, it is good to encrypt all data transmitted through APIs as a fool-proof way to ensure that unauthorized entities do not access it.
- Share Only What’s Needed A thumb rule of data sharing through APIs is – share only what’s needed. Since APIs are used mainly by developers, they can contain extra data such as keys and passwords. Developers must ensure that all these are removed before the APIs are made public. Also, any information that reveals more about the network or its endpoints must be released by the developers instead of relying on user interfaces to filter them out.
- Validations and Setting Limits You must put some checks in place before allowing an API to access your resources. A fundamental step is to validate the inputs before they access the API. Also, establish limits beyond which requests will be rejected. Setting these limits will prevent DDoS attacks and will ensure that your resources are not misused. Where possible, have an application firewall as an extra layer of security.
Thus, these are some of the best practices that must be followed if your APIs are available for public access.
Despite these efforts, security practices alone may not be enough, given the sophistication and intelligence of hackers today. You have to combine these practices with the appropriate security tools that can quickly detect intrusions and vulnerabilities, so you can fix them before it impacts your organization’s resources in a big way.
Tools for API Security
Below are some tools (paid and free) that can help beef up your APIs’ security and identify any potential threats right away.
- Postman This is a scalable tool for API testing and ensures the reliability and usability of APIs at any time.
- OpenAPI Initiative Formerly known as Swagger, APIs that analyze code to identify vulnerabilities and enhance streamlined workflow and development are a framework for APIs.
- Graylog API Security A software package that discovers APIS, scans them for security issues, and then provides constant activity monitoring, disconnecting sessions that look as though they are about to access the exploit.
- SoapUI This is a widely-used API testing tool that tests APIs across different web services.
- Fiddler This tool comes with the capabilities to capture traffic from different sources and use them for testing APIs and the possible vulnerabilities present in them.
- Apache JMeter This open-source Java-based tool can be used for testing different web applications and APIs.
Let’s take a detailed look into each of these tools to understand their features, so you can decide if this is right for you.
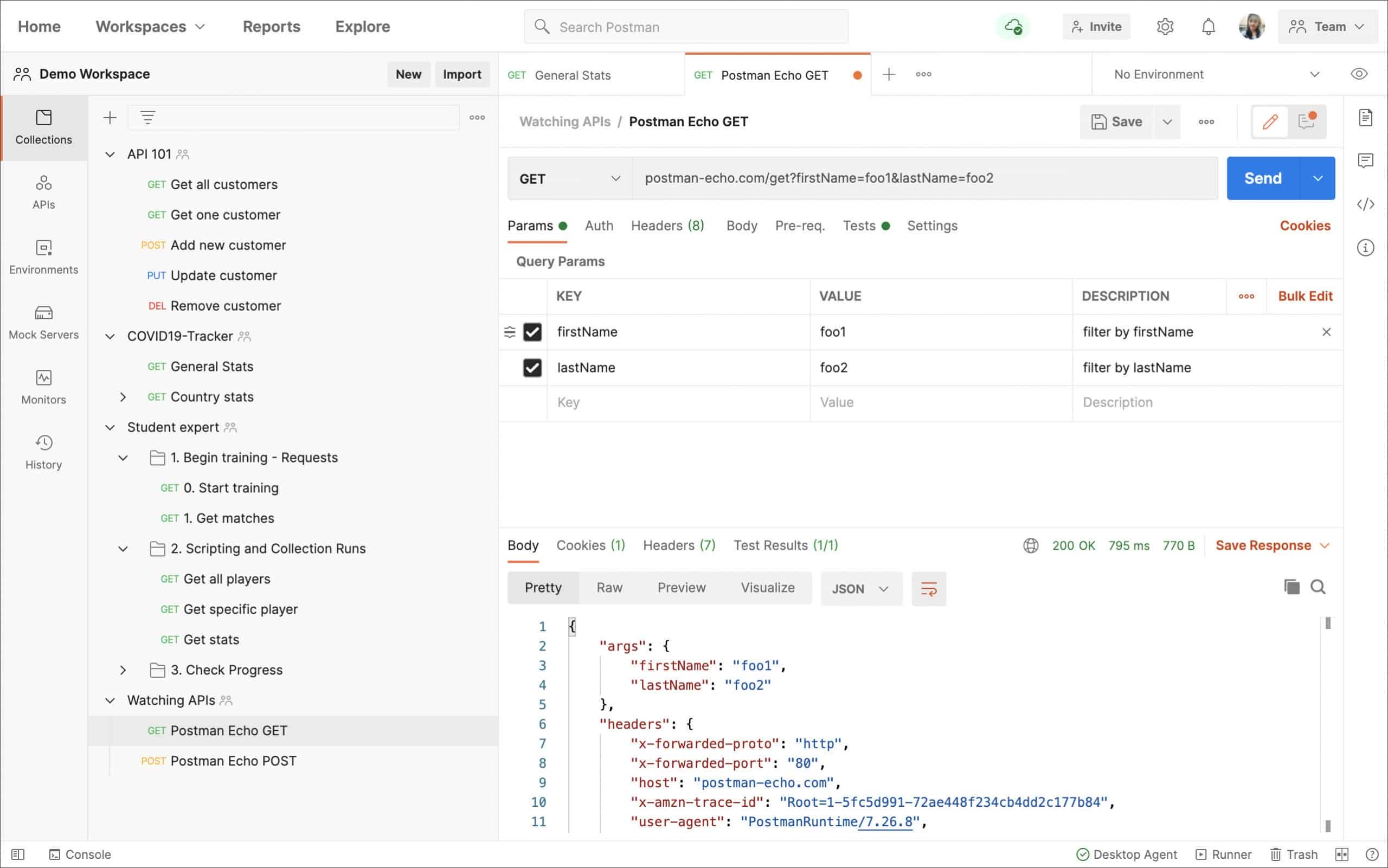
Postman
Postman is a comprehensive API testing tool that constantly tests your APIs for vulnerabilities and ensures that they are reliable and available to those who want to use them.
Features
Here’s a look at the key features of this tool.
- Works well for front-end, back-end, and full-stack development teams
- Enhances collaboration within team members and even across teams
- Ensures that your APIs work as intended
- Supports many API standards such as JSON, REST, SOAP, Swagger, OpenAPI, and more
- Thoroughly tests the functionality of APIs
- Checks if the APIs are capable of handling the anticipated workloads and stress
- Ensures that your APIs can handle unexpected inputs and behavior
- Tests if the API delivers reliable responses
- Performs regression testing to determines any changes in expected behavior due to code changes
- Its console is intuitive and gives the information you need
- Makes it easy to share API requests and collections across teams with just a link
- Allows you to create test suites for comprehensive testing
- Offers the flexibility to import schema formats like GraphQL and RAML
Pricing: There are four plans, and they are:
- Free – A good starting point to develop and test APIs
- Team ($12 per month, billed annually) – Ideal for collaborating with your team members in designing and testing APIs
- Business ($24 per month, billed annually) – Scale your APIs and manage them across the entire organization
- Enterprise ($69 per month, billed annually) – Offers tools to securely manage and accelerate the development of APIs across the organization
Download: Click here to sign up and buy.
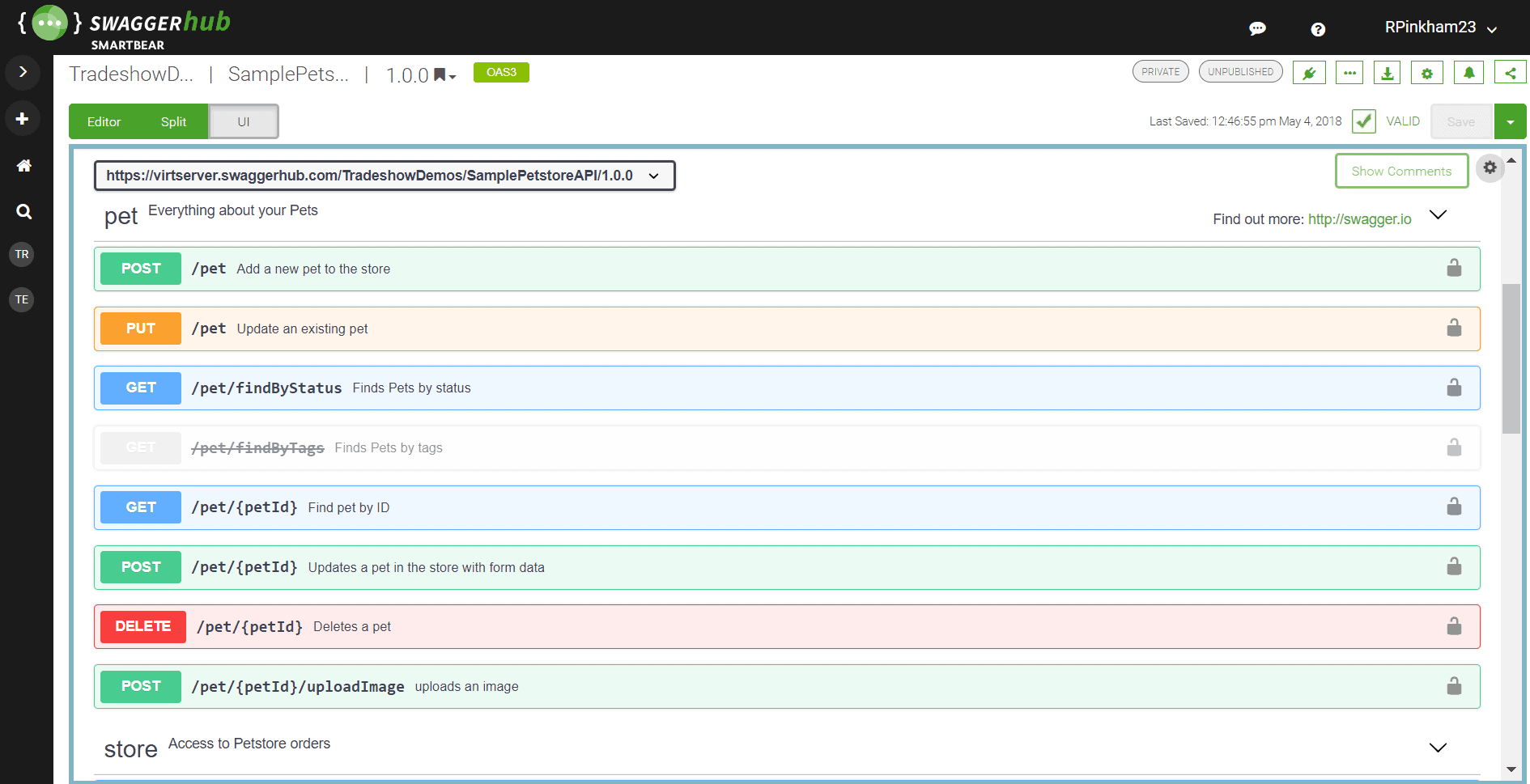
OpenAPI Initiative
Swagger or OpenAPI Initiative is an API testing tool that tests your APIs’ functionality, security, and performance. This constant testing and monitoring empower you to create and manage APIs across the entire organization easily.
Features
The salient features of Swagger are:
- Tests APIs and documents their performance for easy tracking
- Validates APIs on the cloud and auto-saves them so that they can be accessed anywhere
- No limits on the type and functionality of API as it supports REST, SOAP, GraphQL, and more
- Creates documents so that the testing results can be shared with others. It can also act as a record for future testing and development
- Tracks the changes and integrations
- Creates and runs complex validations
- Empowers teams to collaborate for development and testing
- Its visual editors and graphics enable beginners and non-technical personnel to understand the test results
- Records live API traffic
- Imports endpoints from your API management tool
- Natively integrates with CI/CD tools such as Jenkins, Maven, and other API lifecycle tools
- Simplifies regression testing
Pricing: There are three pricing plans to choose from, and they are:
- API Test Module starts at $749 per license per year
- API Performance Module starts at $6,449 per license per year
- API Virtualization Module starts at $1,270 per license per year
You can also bundle these three modules and get them at a consolidated rate. Again, contact the sales team for this custom quote.
Download: Click here to start a free trial.
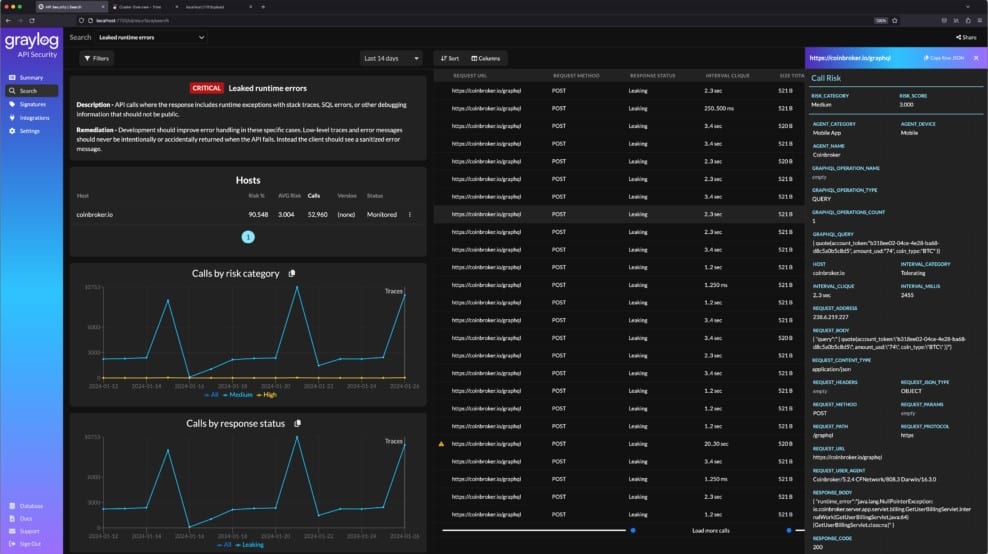
Graylog API Security
Graylog API Security provides multiple scanning cycles that implement a failsafe strategy to block threats to components that might not be within the control of the company that buys the security software. Often APIs are supplied by third parties and if they have security loopholes, there is nothing that a business that integrated those modules into their own products can do about them.
Key Features:
- Asset discovery: A scanner looks through known applications for APIs
- System documentation: The scanner creates a list of all the APIs used by the business
- Vulnerability scanning: Security testing runs through common vulnerabilities and implements security testing
- Usage tracking: Logs the access events to each API
- Automated responses: Blocks connections that seem to be aiming for APOI weaknesses
The three phases of the Graylog system discover, scan, and monitor APIs. Here are some more interesting features of the package:
- Works through multiple layers of code, discovering APIs within APIs
- Checks for common vulnerabilities, such as the OWASP Top 10
- Runs the APIs with a range of inputs to test for operational weaknesses
- Generates a report on weaknesses per API
- Provides a bug fix plan
- Retests for fixes
- Continuously rescans for new APIs or altered code with new vulnerabilities
- Monitors executions
- Tracks the usage events and their parameters
- Blocks sessions that are approaching known API security weaknesses
- Free edition available
- Software package for cloud or on-premises hosting
- Activity analysis
Pricing:
- Free: Monitors 1 node and 16GB of local rolling storage = FREE
- Standard: Monitors 2 nodes = $1,500 per month
An increase in the number of nodes monitored by the Standard plan increases the price.
Pros:
- Continuous discovery: Constantly checks for new APIs
- Fix checking: Keeps retesting known vulnerabilities to see if fixes have been made
- Activity logs: Records user access to APIs
- Activity analysis: Provides insights into API demand
- Guards vulnerable APIs: Disconnects connections that threaten APIs
Cons:
- No SaaS option: You need to budget for hosting space for the software and its logs
SoapUI
SoapUI makes it easy to test APIs across different frameworks and web services to empower you to develop and deliver top-quality software in the shortest possible time.
Features
Below are the important features of SoapUI.
- Supports both open source and commercial tools and web services, including REST, SOAP, JDBC, JMS, and more
- Automates API testing and fits it into your continuous delivery pipeline
- Tests the functionality to ensure that the API functions as it is intended to
- Loads and stresses the APIs to measure their performance
- Evaluates the security of APIs and makes recommendations accordingly
- Enables virtualization of APIs, depending on your preferences
- Supports data-driven testing to accelerate the speed and quality of software development
- Provides detailed test reports for analysis and compliance
- Runs automated tests for greater accuracy
- Identifies vulnerabilities in APIs and recommends the fix for the same
Pricing: The cost of this tool is $749 for a one-year license, $1,498 for a two-year license, and $2,247 for a three-year license.
If you choose a floating license, the cost is $4,799 per year.
Besides, this tool also offers certifications and training that cost,
- $119 for SoapUI Open Source Certification, ReadyAPI Certification, and ReadyAPI On-Demand Video Training
- $179 for ReadyAPI On-Demand Video Training Bundle with Certification
Download: Click here to try this tool for free.
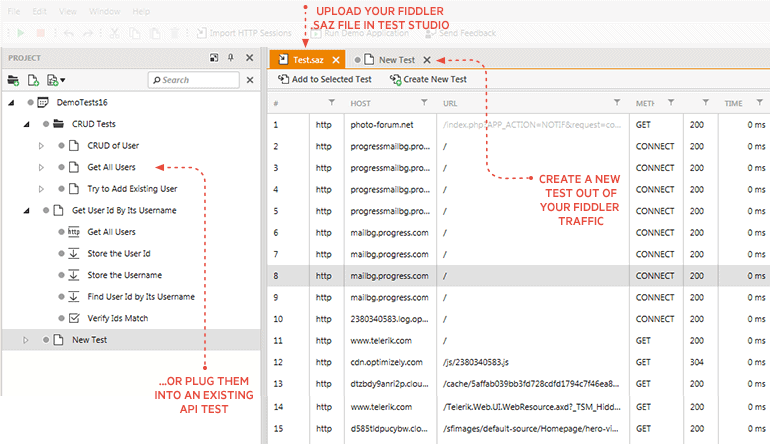
Fiddler
Developers and testers use Telerik to test the functionality and security of their APIs exposed to HTTPS.
Features
Some of the salient features of FIddler are:
- Enables the authoring of HTTPS requests
- Examines all responses, including XML, JSON, and more
- Offers a Request History pane to help you check the history of all the tests and reuse them as needed
- Displays the existing list of features and executes them as needed
- Captures traffic from different sources and runs them on your APIs to check its response
- Validates the behavior of web APIs
- Use simple drag and drop to add tests
- Providers a ton of built-in validators to evaluate the performance of an API
- Makes it easy to build your API testing infrastructure
- You can test instantly or schedule it for a later time
Pricing: Fiddler comes in three pricing options.
- DevCraft UI – $1,299 per developer
- DevCraft Complete – $1,499 per developer
- DevCraft Ultimate – $2,199 per developer
Download: Click here for a free trial.
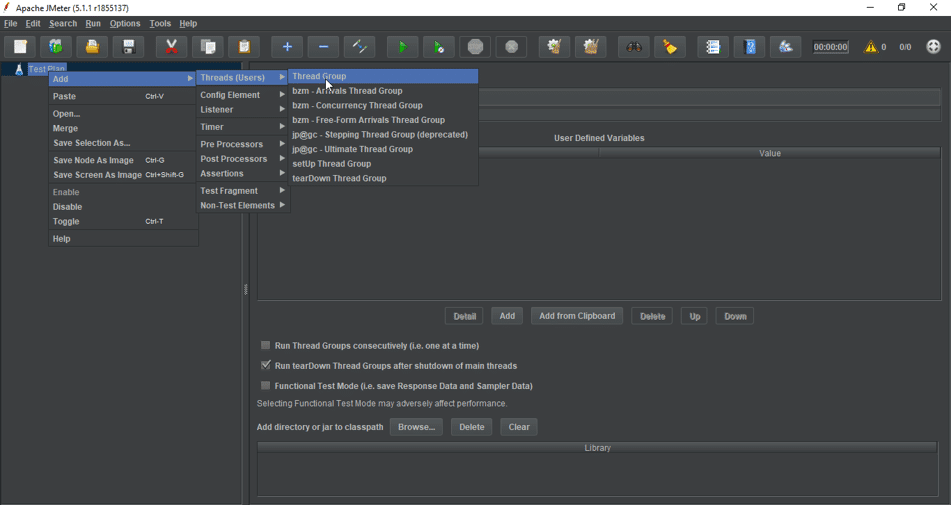
Apache JMeter
Apache JMeter is a load testing application that can be used for testing web services, applications, APIs, and more. It is an open-source Java-based tool that can test performance on both static and dynamic resources.
Features
Some of the salient features of Apache JMeter are:
- Load and performance test SOAp, REST, FTP, LDAP, TCP, SMTP, and more
- Offers a full-featured Test IDE
- Generates a dynamic HTML report for viewing the results
- Highly portable
- Extracts data from well-known response formats such as HTML, XML, and JSON
- Uses a multi-threading framework for concurrent sampling
- Comes with a highly extensible core
- Caches and analyses the results
Pricing: 100% FREE
Download: Click here to download
Thus, these are some of the tools you can use to test the functionality and security of your APIs and ensure that they don’t impact your overall performance.
Conclusion
In all, APIs are a highly versatile and flexible way to communicate between different pieces of software. Unfortunately, with this versatility comes security loopholes. This makes it necessary to beef up the security so that the APIs don’t act as gateways for malicious intruders to enter your network.
Handling API security is complex and requires a mix of best practices and tools to continuously check and evaluate the performance of APIs against traffic from a wide range of sources. However, the tools mentioned above are well-known for their efficacy in handling API-based threats and making your APIs more beneficial for you and the world.