Data breaches have unfortunately become a common occurrence in today’s world.
Most of us think it is done by malicious hackers and criminals or intelligence agencies of certain countries who have access to some of the most sophisticated technologies needed to break into even the most secure networks.
But in reality, these outside attacks are only one side of the coin.
It is not always hackers and criminals who compromise a network, but also employees who want to make some quick money by selling confidential data to competitors.
Sometimes, data breaches also happen when employees are ignorant of security policies or have too much access to different system resources.
2018 Insider Threat Report by CA Technologies shows that 90% of organizations feel vulnerable to insider attacks.
According to this report, the main reason for insider attacks is excessive access privileges (37%), increasing number of devices with access to confidential data (36%) and the overall growing complexity of information systems as a whole (35%).

Source: CA Technologies
The above statistics as well as infographic throws the spotlight on access rights management.
Giving users limited access to file shares, AD and other resources within the organization is sure to go a long way in reducing the possibility of both malicious and accidental attacks and thefts within your organization.
But managing access is easier said than done considering the wide geographical spread of today’s network and the thousands of devices that are a part of it.
This is why automated tools like SolarWinds Access Rights Manager help with auditing user permissions and access to different resources.
SolarWinds Access Rights Manager Review
SolarWinds Access Rights Manager (ARM) helps IT administrators to stay on top of user authorizations and access permissions. This tool is aimed to make user provisioning, deprovisioning, tracking and monitoring easy and to help minimize the chances for insider attacks.
Features
The salient features of SolarWinds Access Rights Manager include:
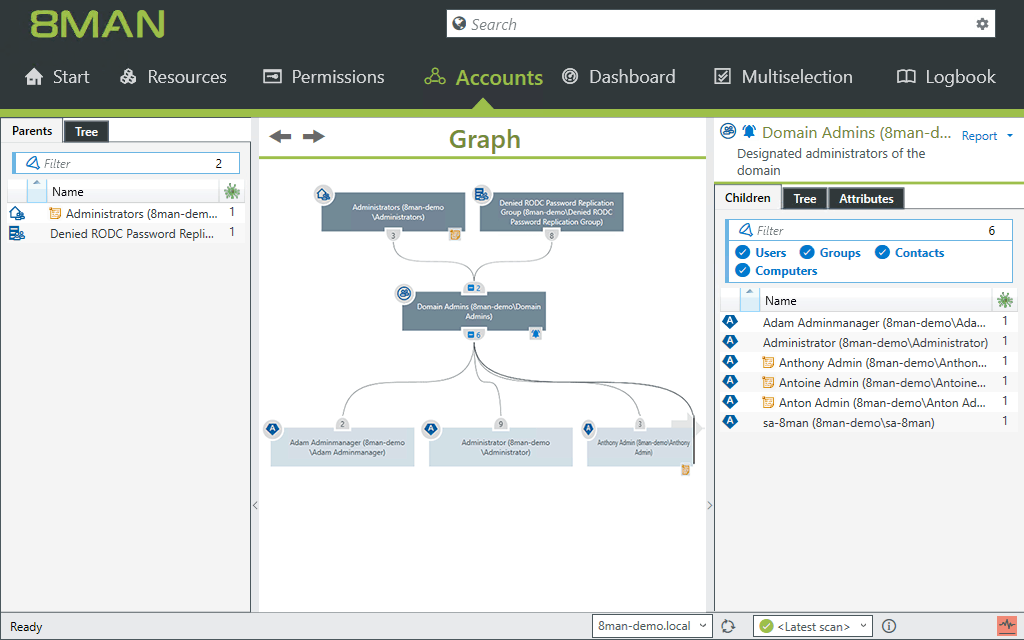
– Monitoring Active Directory
SolarWinds ARM monitors and audits changes to Active Directory and Group Policy.
As an IT admin, you can see who has made what changes to the group policy or Active Directory settings, and the date and time of these changes.
Based on this information, it is easy to spot unauthorized users and also the malicious or ignorant acts, if any, committed by any user.
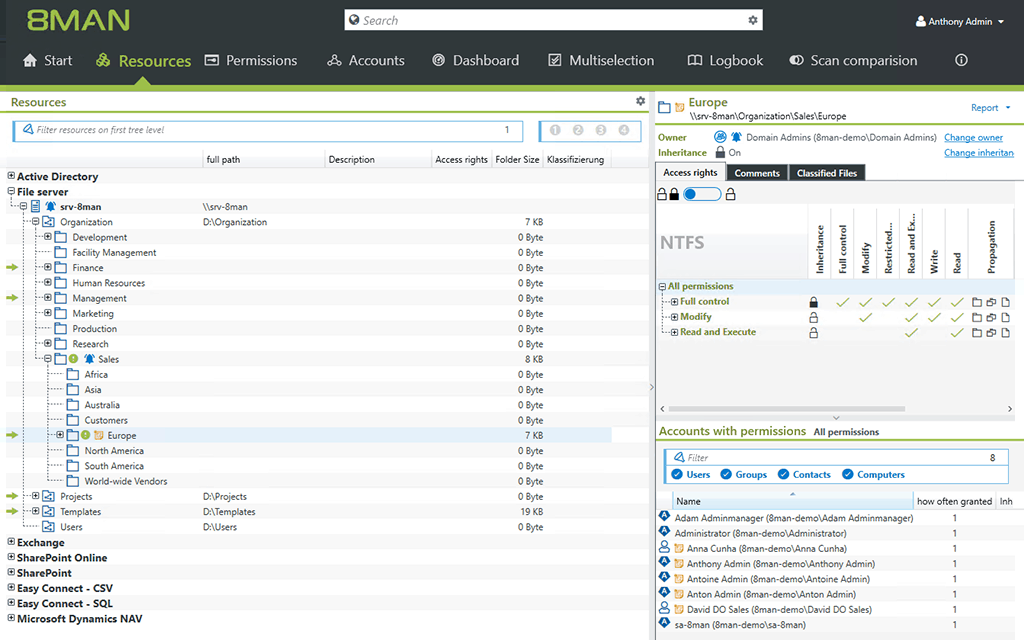
– Changes to Windows File Servers
Many attacks happen when folders and its contents are accessed by users who are not authorized to see them.
This often happens when users are given wide-reaching access to folders and files.
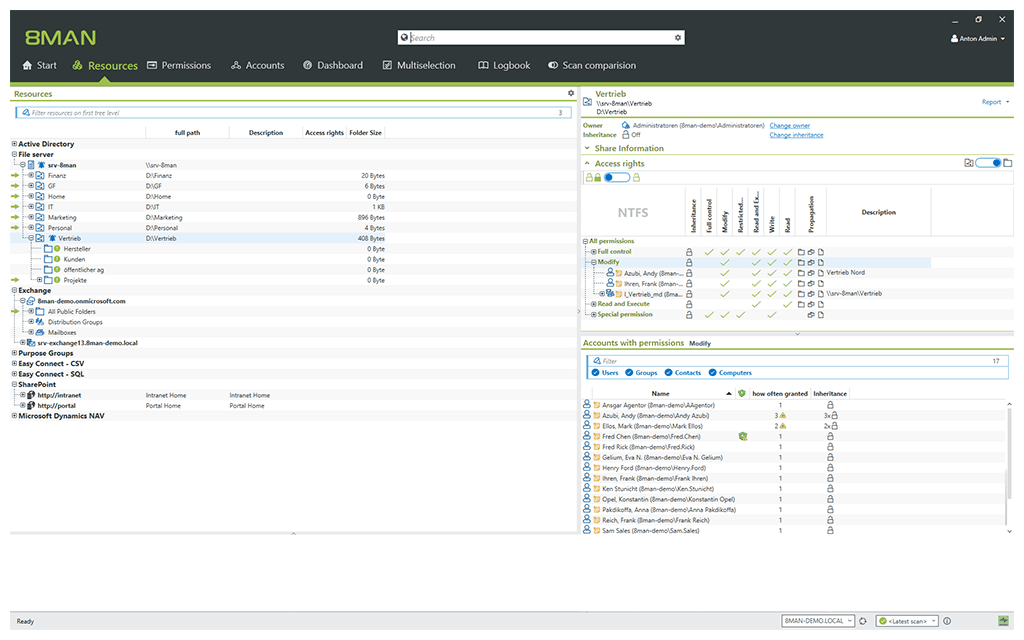
To prevent these data leaks and unauthorized changes to confidential data and files, SolarWinds ARM gives a visual picture of permissions for different file servers.
In other words, you can see who are allowed permissions on what files, so you monitor what is happening and at the same time, control access.
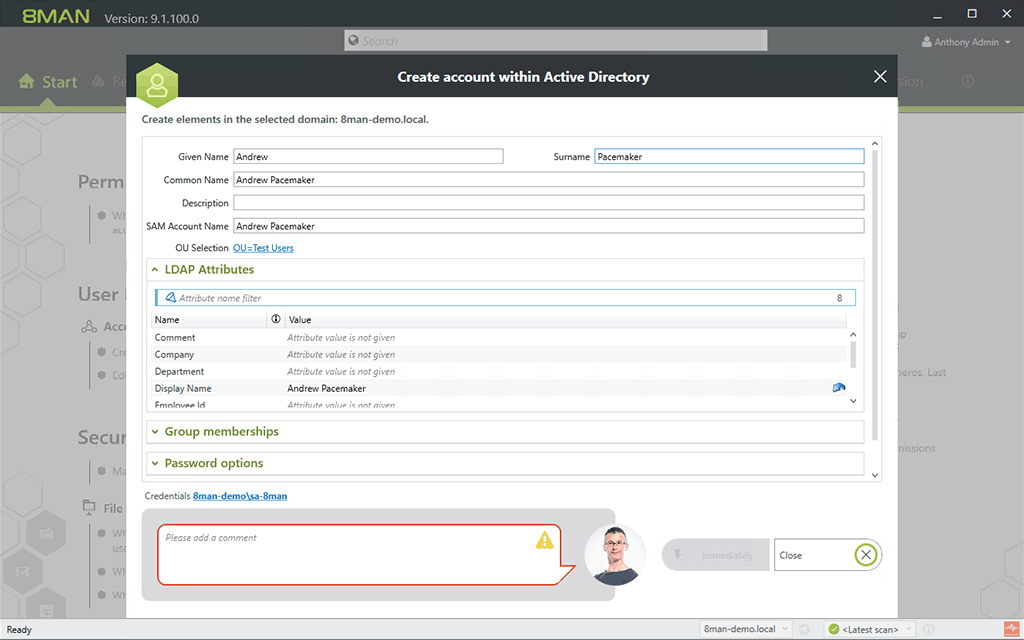
– User management
With an intuitive dashboard, you can create, modify, delete, activate and deactivate user access to different files and folders.
ARM also comes with role-specific templates that gives users access to specific resources on your network.
All this means you can create or delete users with just a few clicks.
– Permission Analysis
You get to not only manage different users, but you can also analyze which users have accessed which services and file servers.
SolarWinds ARM offers visibility into group memberships of Active Directory and file servers as well, so you are in the best position to prevent insider attacks.
– Reporting
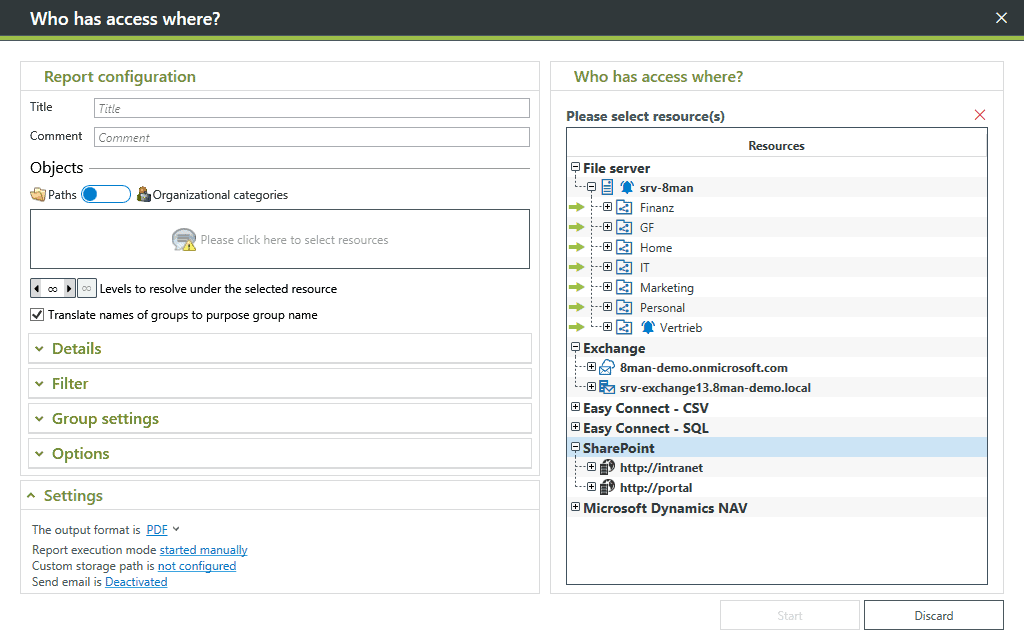
Checking user access alone is not enough, you also need to generate evidence in case of disputes in the future.
You also need detailed reports for auditing purposes and to comply with the specifications set by different industry standards.
In SolarWinds Access Rights Manager, you can generate reports that are perfectly geared for auditors and for the compliance of different standards.
In fact, you can create these reports with just a few clicks.
Even log activities in Active Directory and file server accesses can be encapsulated in a report.
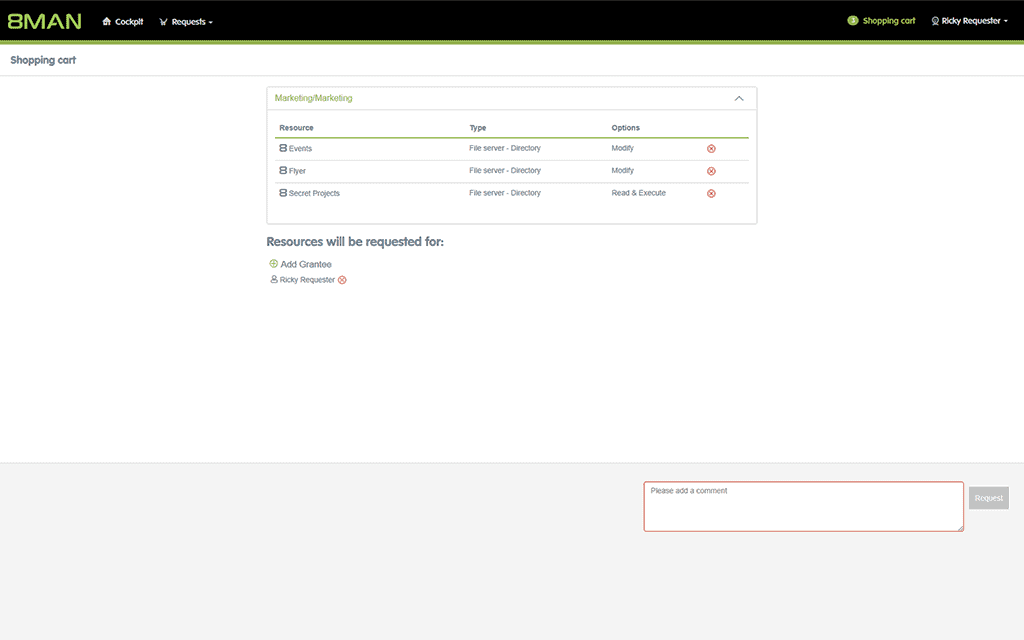
– Request Direct Access
SolarWinds ARM gives the choice to give access rights directly in the hands of the person who created it.
In other words, a person who created a file can decide who can access it.
Such a self-permission system would greatly prevent unauthorized access to information.
A web-based self-permission portal makes it easy for owners to handle access requests.
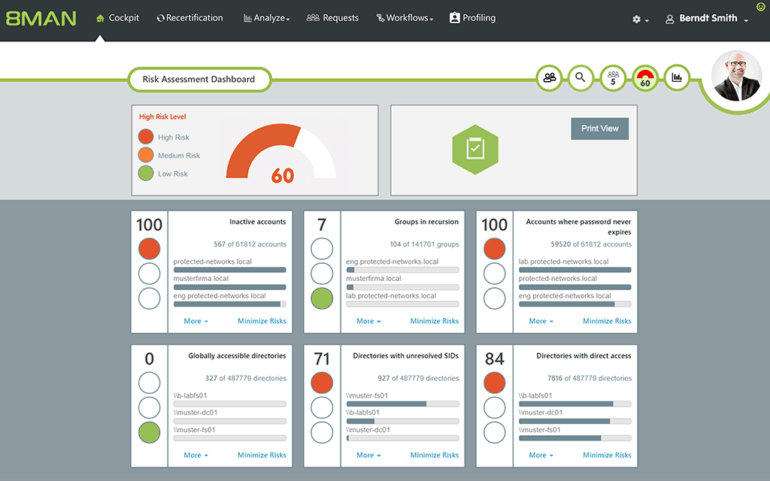
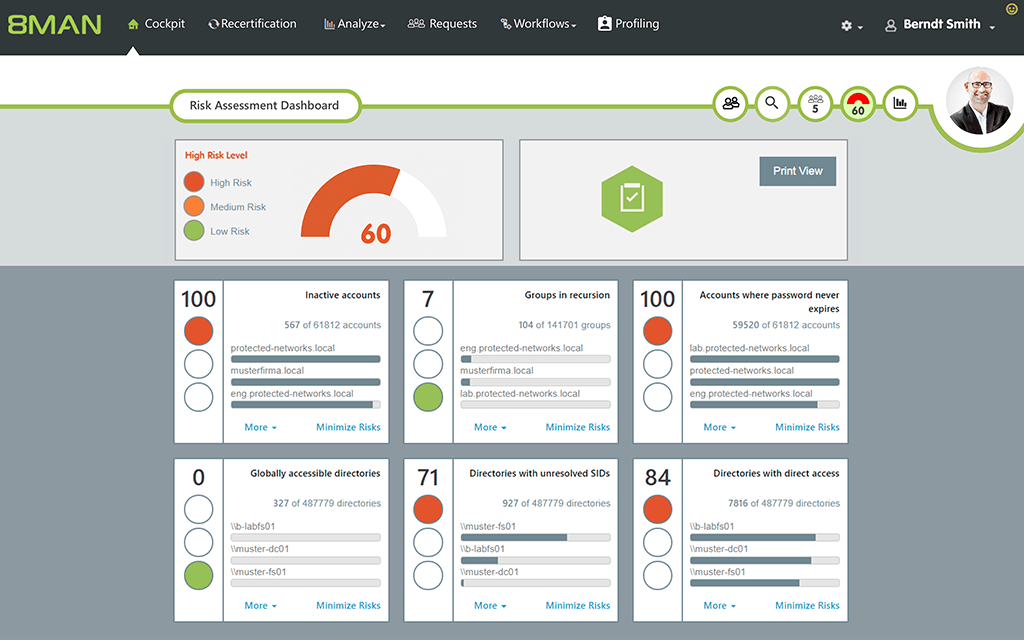
– Risk Assessment
At any given point in time, you can get a real-time idea of the possibility of risk for your organization.
Based on the level of access and permissions, SolarWinds ARM calculates the percentage of risk for every user.
This makes it convenient for IT administrators and even the top management of IT security to have complete control over user activity and the level of risk for each employee.
Obviously, IT administrators can keep a closer watch over those users with high risk levels.
Download Info & Pricing
SolarWinds ARM can be download on a 30-day free trial!
Use the Download Link below to Download it from SolarWinds.com
https://www.solarwinds.com/access-rights-manager/registration
After the trial period is over, Pricing for Access Rights Manager starts at $2,995.
Conclusion
To conclude, insider attacks are more common than we imagine and contribute to a substantial amount of data breaches and the resultant financial loss.
Monitoring the activity of every user and controlling their access is essential to ensure that such insider attacks do not happen – But its not easy to implement such an elaborate monitoring system manually.
This is why a tool like SolarWinds Access Rights Manager can help to streamline access and can help you to stay on top of user activity – all of which are essential to reduce the possibility of insider attacks.
Grab a Free Download from Above and try it in your Network – We were Pleasantly surprised how Powerful and Flexible this tool was!