Today, it has become vital for organizations to strategize and secure endpoints to protect networks from cybersecurity risks. However, protecting endpoints is not as easy as it sounds. You can find a wide range of threats available online, making it difficult to protect your infrastructure at all times.
Hence, one should adopt endpoint security tools that will secure end-user devices, such as laptops, computers, and other devices, from malicious attackers. By taking on this step, you will in a way keep your enterprise’s IT system safe and secure.
The effective endpoint security tools will shut the entry points and save your devices from getting exploited by attackers.
Most endpoint security software includes root cause analysis, whitelisting tools, integrated firewall system, network access control, endpoint management, intrusion detection, and response features.
Deep Instinct is one such popular endpoint security software that covers the majority of the features and prevents zero-day exploits, PowerShell attacks, ransomware, code-injection attacks, etc. Here we will learn more about Deep Instinct, its benefits, pros, cons, and pricing plans.
Further, we will highlight a few alternate solutions that provide similar functionalities and help protect your endpoints against attackers.
Deep Instinct Product Overview
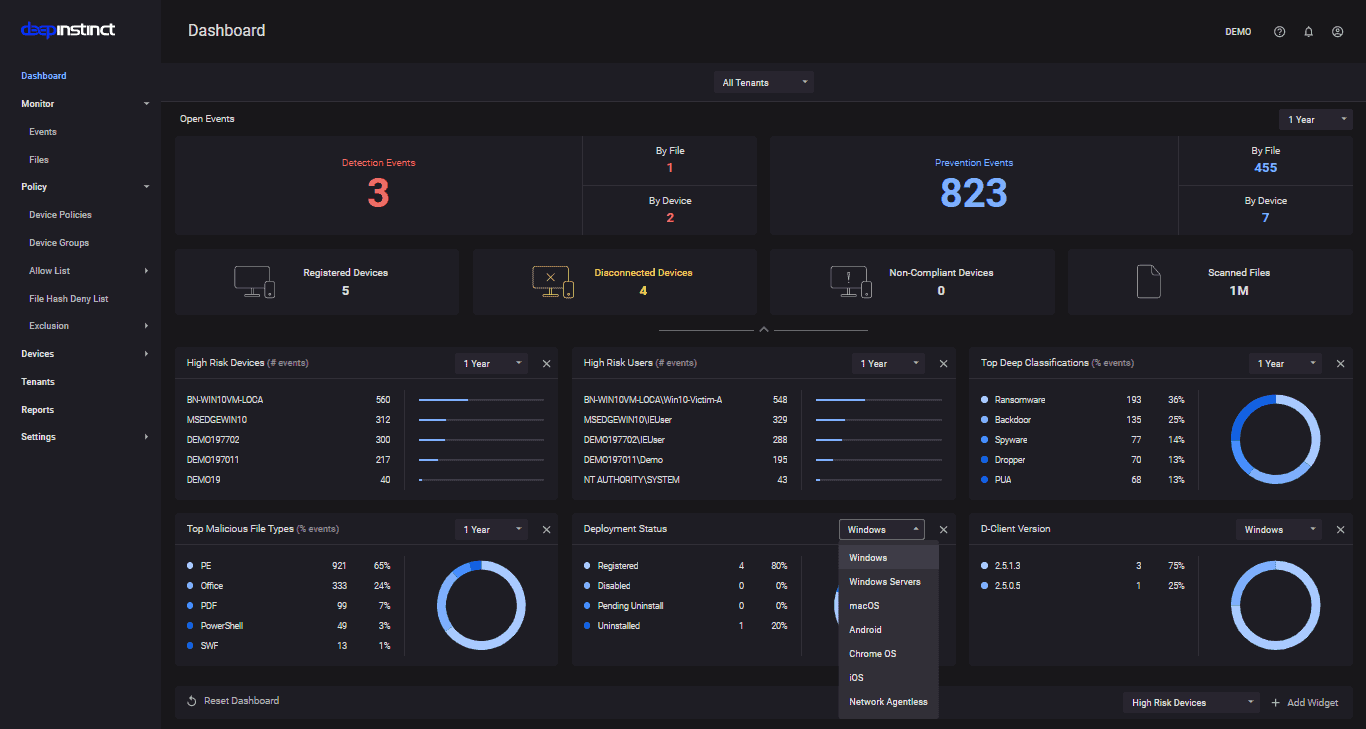
Deep Instinct is the first company to adopt deep learning as its core basis to prevent threats in zero time. The proactive solution harnesses the power of Deep Learning and follows a prevention-first approach to stop and prevent your endpoints from getting attacked by ransomware and other malware.
Unlike other EPP or EDR solutions, Deep Instinct is quick at detecting threats with greater efficacy. The endpoint security software also ensures that the malware gets identified and detected before it executes.
The purpose-built deep learning framework adds more precision and ensures the lowest number of false positives. Further, it helps optimize SOC teams and delivers a sense of satisfaction to enterprises that the threats will be prevented before execution each time.
Using our single agent, businesses can automatically block all known, unknown, and unprecedented attacks in zero time. No matter whether your device is off-site, offline, requires updating, or employees use apps they shouldn’t, Deep Instincts protects all endpoints.
It is compatible with multiple operating systems, including Windows, macOS, and Chrome OS. Another feature why most businesses prefer Deep Instinct is it is a lightweight model with low memory consumption.
Get access to unmatched accuracy and speed with the lightweight on-device solution that offers comprehensive defense and protects your endpoints and servers from all known and unknown malware.
LG, BlackRock, Samsung, and COATUE are a few high-profile companies that have invested their time and money into Deep Instinct for many years.
Key Features of Deep Instinct
- Application Security
- Behavioral Analytics
- Device Management
- Root Cause Analysis
- Prevents Attack Vectors
- Offers end-to-end Mobile Protection
- Powered by Deep Learning
- Safeguard endpoints against zero-day threats and APT attacks
- Real-time malware detection
- Offers higher visibility of security breaches
- Alerting and event management capabilities
Why do we recommend it?
Deep Instinct stands out for its prevention-first approach powered by deep learning, ensuring rapid and accurate threat detection. It not only prevents known and zero-day threats but also minimizes false positives, offering a more efficient and autonomous solution for SOC teams.
Benefits of Deep Instinct
Look at some of the benefits of Deep Instinct:
- Supports Prevention-first Approach: Powered by a Deep learning cybersecurity framework, the software uses the prevention-first approach to prevent ransomware and other malware from reaching out to endpoints, servers, and mobile devices.
- More Accurate: Many machine learning-based tools overdo the protection task and flood the team with false positives or lack precision. However, with Deep Instinct, you fill in the lowest number of false positives and add more precision to prevent unknown threats.
- More Autonomous: The Deep learning cybersecurity framework is designed and trained to automatically detect and prevent threats on hundreds of millions of files. As a result, it reduces the burden on the team and makes them smarter, faster, and agile.
- Focus on Real Threats: Deep Instinct focuses more on detecting and preventing real threats and not the perceived ones. As a result, you can improve your operational efficiencies.
- Fast and Secure: Compared to other EPP or EDR solutions, Deep Instinct offers true prevention and detects threats 750 times faster than some of the most well-known fastest ransomware. It also enables businesses to detect unknown and zero-day threats before execution.
- Prevents Against Multiple Threats: Most businesses choose Deep Instinct over other EDP tools in the world because its advanced features help prevent endpoints from all unknown and known threats. It offers zero-time prediction and broad attack surface protection with no operational headaches. Also, it supports no trade-off from the existing security stack.
Who is it recommended for?
Deep Instinct is ideal for enterprises and businesses of all sizes that prioritize endpoint security. It’s particularly beneficial for organizations requiring robust protection against zero-day threats, ransomware, and other malware, without the operational overhead of constant alerts and updates.
Pros:
- A simple and easy-to-deploy lightweight on-device, proactive endpoint solution
- Prevents against zero-day threats and other malware before execution
- Offers 24/7 support
- Fast and adds more precision
- More accurate than other EDP tools
- Reduces the burden on your SOC team by preventing threats autonomously.
- The engines are compatible with older versions too.
- Deep Instinct has a good user interface
- Quick response and 24/7 support
- Supports non-signature-based methods for eradicating ransomware
Cons:
- Requires improvement with Linux and Unix operating systems
- Need to work on SLAs as they are not up to the mark
- Require better documentation
- Pricing can be an issue.
- It stops working if you run two servers simultaneously and add Windows Failover Cluster mode.
- Deployment is difficult without a VPN or if the user is working remotely.
Deep Instinct Pricing Plans
Deep Instinct is a bit expensive compared to other endpoint protection software. It is not the product that makes it sound costly but the console. The console manages and controls everything, which raises its price.
For a customer who holds 300 to 500 agents, PCs, or users, the software may become too pricey. Each endpoint is priced around $50-75 per instance, all based on the volume. Let me tell you the mobile solution will range slightly more than this.
Further, the support services and training facilities are included in the Deep Instinct package.
The Best Deep Instinct Alternatives
No doubt, any attack on privately-owned devices is a big concern as it can lead to heavy losses. Hence, the main focus for most businesses is to bid on a solution that will help defend their businesses at all times.
Deep Instinct is one of the trusted tools that help address all endpoint security issues and protects against zero-day exploits and other unknown attacks. It can protect all your networks, servers, endpoints, and mobile devices, yet most companies look for alternate solutions because they cannot afford them.
Deep Instinct is a bit expensive and carries a few more drawbacks. So, we have listed a few alternate solutions with similar features that might protect your endpoints and defend businesses.
Have a look at some of the top endpoint protection alternative solutions:
1. ManageEngine Endpoint Central Next-Generation Anti-Virus – FREE TRIAL
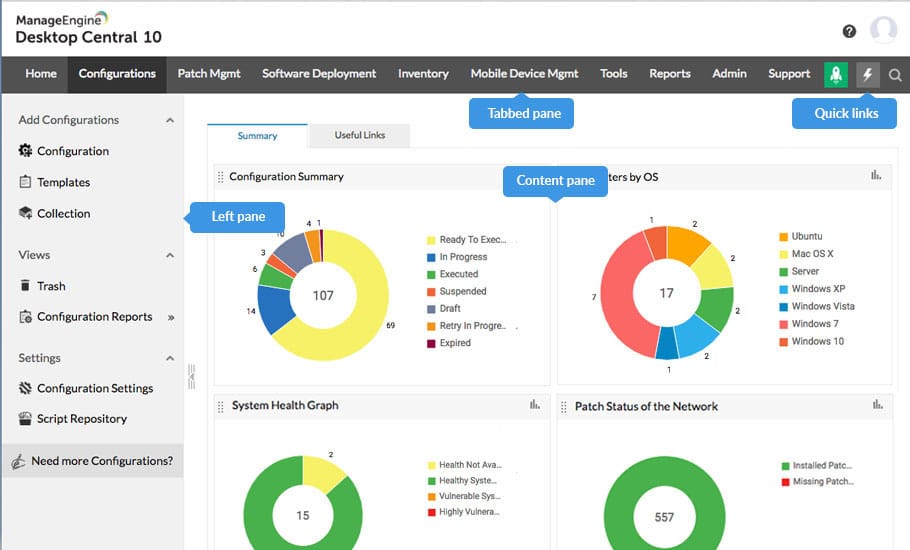
ManageEngine Endpoint Central recently changed its name from Desktop Central and the system’s screens are still headed by the old name. This package includes a next-generation anti-virus system that is a good alternative to Deep Instinct because it uses anomaly detection. This strategy establishes a baseline of normal activity on an endpoint and then alerts when some activity doesn’t fit. This enables the system to spot new malware that hasn’t been cataloged by any of the major cybersecurity systems providers.
Why do we recommend it?
ManageEngine Endpoint Central is a great deal because it isn’t just an anti-virus system, it is primarily a unified endpoint management package. The bundle also offers data protection systems and insider threat detection. It has a vulnerability scanner and a patch manager. So, there are many security services in this bundle alongside management features for managing workstations and mobile devices.
Who is it recommended for?
ManageEngine offers five editions for Endpoint Central and so it is suitable for many audiences. The package is designed for use by IT departments – there is another package available, called RMM Central, for managed service providers. The next-generation AV is an add-on for all editions, except for the free version, which will secure up to 25 endpoints. Start with a 30-day free trial download.
EDITOR'S CHOICE
ManageEngine Endpoint Central Next-Generation Anti-Virus is our top pick for a Deep Instinct alternative because it implements anomaly detection like Deep Instinct but it also has a much wider series of security units as part of a comprehensive endpoint management package. The unified endpoint management system will look after workstations running Windows, macOS, and Linux plus mobile devices running iOS and Android. The bundle includes vulnerability scanning, patch management, application and content security for mobile devices, and user behavior analysis as well as the AV. The Endpoint Central system also implements data backups to protect against the damage caused by ransomware. This system is available for download onto Windows Server and it is also offered as a cloud-based SaaS platform.
Download: Download a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/desktop-central/free-trial.html
OS: Windows Server and cloud
2. Malwarebytes for Business
Malwarebytes is a cloud-based system that protects endpoints running on platforms, such as Windows and macOS. It creates communication with the agent installed on one of the servers and checks for unusual activities. The tool makes sure that the devices are secure and teams productive. Most tools do not cover every threat, however, Malwarebytes assures businesses to provide malware protection, proactive threat blocking, and remediation. It is a lightweight agent that employs innovative machine learning and artificial intelligence to discover and block threats before launching. Get protection from botnet and browser-based threats using Malwarebytes for Business. Another feature that makes it a great choice is it allows browsers to load infected web pages.
Why do we recommend it?
Malwarebytes for Business stands out for its comprehensive endpoint protection across multiple platforms, employing machine learning and AI for proactive threat blocking. Its ability to handle a range of threats, from malware to botnets, makes it a robust security solution.
Who is it recommended for?
This tool is highly recommended for small to large businesses that prioritize comprehensive endpoint security. It’s particularly well-suited for organizations that operate across multiple platforms like Windows and macOS, and are looking for an intelligent, cloud-based system that can adapt to evolving threats.
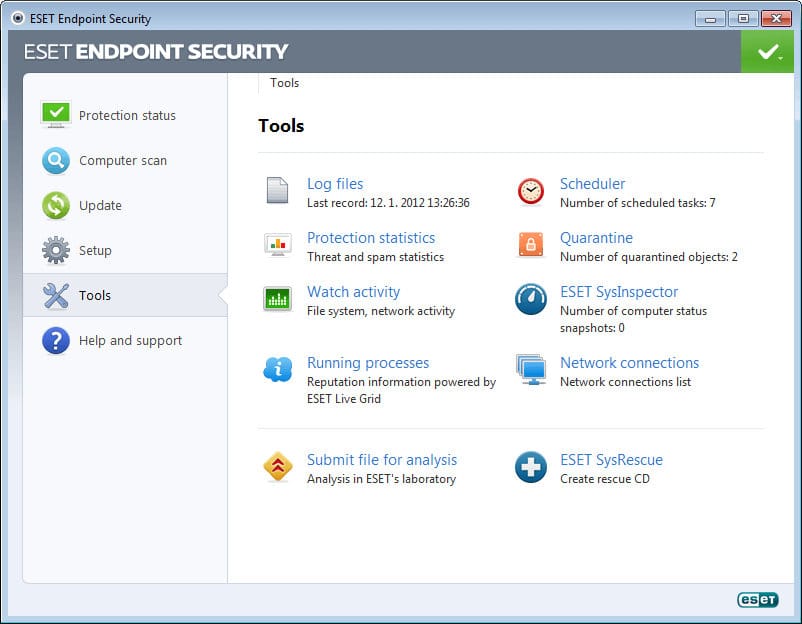
3. ESET Endpoint Security
If you are looking for a tool that will protect your computers from malicious activity and block them before connecting to a network, you are at the right place. ESET Endpoint Security is one such powerful tool that provides instant remediation capabilities and prevents cyberattacks. It protects all your devices, including desktops, laptops, and smartphones with its multilayered defense system. Another plus point about ESET Endpoint Security is it supports Windows, Mac, Linux, and Android. If you want to prevent data breaches, block targeted attacks, protect against ransomware, and stop file-less attacks, look no further. It leverages Host-based Intrusion Prevention System (HIPS) techniques to discover threats by monitoring their behavior and patterns rather than a signature.
Why do we recommend it?
ESET Endpoint Security offers a multilayered defense system, effective against a wide range of cyber threats from ransomware to targeted attacks. Its Host-based Intrusion Prevention System (HIPS) enables it to detect threats based on behavior, making it highly adaptable.
Who is it recommended for?
This tool is ideal for businesses of all sizes, looking for comprehensive endpoint security across multiple operating systems including Windows, Mac, Linux, and Android. It is especially useful for organizations concerned with data breaches and those who prefer a behavioral approach to threat detection.
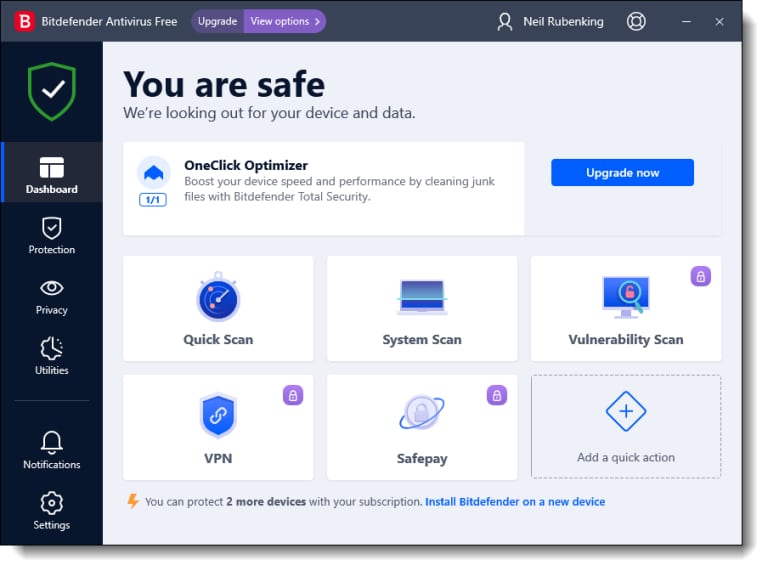
4. Bitdefender
Bitdefender, starting in 2001, is a leading company that shifted its traditional antivirus model to a comprehensive defense system. It provides endpoint protection as well as defense networks. Bitdefender GravityZone Business Security provides security to businesses of all sizes and protects against malware. It uses proven machine learning techniques and performs behavioral analysis to monitor and detect threats, such as zero-day attacks, viruses, spyware, ransomware, phishing, etc. The easy-to-use software is managed from a single console and ensures maximum protection. Whether you want to protect your desktops, laptops, or physical or virtual servers, the tool will fit best in every case.
Why do we recommend it?
Bitdefender GravityZone Business Security employs advanced machine learning and behavioral analysis techniques to offer robust protection against a wide array of threats, including zero-day attacks and ransomware. Its centralized console makes it easy to manage, streamlining the security process.
Who is it recommended for?
Bitdefender is suitable for businesses of all sizes that require comprehensive endpoint protection, be it for desktops, laptops, or servers—physical or virtual. The tool is particularly useful for organizations that seek advanced threat detection capabilities like machine learning and behavioral analysis.
5. CrowdStrike
CrowdStrike Falcon is another cloud-based protection tool that deploys AI techniques and threat intelligence for threat detection. It uses a scanning process to detect threats and malware. You can operate the popular tool both on-site and in the clouds. The real task of providing protection and monitoring activities is performed from a single console with an agent. It is one of the best alternative solutions as it uses machine learning to monitor the behavior and track regular activities. Available in four editions – Pro, Enterprise, Premium, and Complete, the tool is highly useful and enables businesses to spot problems and remediate them faster.
Why do we recommend it?
CrowdStrike Falcon stands out for its use of AI techniques and threat intelligence to quickly and accurately identify threats. Operable from a single console, its machine learning capabilities make it a high-performing alternative in the endpoint protection market.
Who is it recommended for?
CrowdStrike is suitable for businesses that are looking for both on-site and cloud-based endpoint protection solutions. Available in various editions to meet different needs, it’s ideal for organizations that require real-time threat monitoring and quick remediation capabilities.
6. SentinelOne
SentinelOne is another amazing tool that empowers enterprises to detect threats and take action in real-time. It is not just limited to the identification of malicious behaviors but allows the user to take action by blocking and remediating advanced attacks autonomously. You can prevent breaches at a faster rate by defeating evolving cyber threats before they launch. Get access to unprecedented speed and secure all your endpoint, cloud, and identity with a single platform. It also uses AI-powered automation techniques to offer greater visibility to its dynamic attack surface. On detecting threats, it will help you act faster and smarter.
Why do we recommend it?
SentinelOne offers real-time threat detection along with autonomous remediation capabilities. Its use of AI-powered automation provides unparalleled speed and visibility, making it highly effective against evolving cyber threats.
Who is it recommended for?
SentinelOne is ideal for enterprises that require not just threat detection but also autonomous action against advanced attacks. This tool is particularly useful for organizations looking to secure multiple aspects like endpoints, cloud environments, and identity management, all from a single platform.
Conclusion
Endpoints are a key target for cyber attackers which is why every business must tighten its defenses and incorporate tools that will protect an entire network and endpoints from all known and unknown threats.
When starting your search for security tools, we recommend businesses to invest in endpoint protection tools rather than antivirus solutions as they are superior.
With the help of these endpoint protection tools, businesses can monitor and manage a network full of devices from a single console. Further, block threats or remediate them instantly. It has become vital for companies to find up-to-date solutions that will provide all-time protection to the endpoints.
Deep Instinct is one such popular tool that detects threats faster with greater efficacy. Powered by deep learning, the tool enables users to prevent endpoints attacked by ransomware and other malware. It assures that the threats will be prevented before execution each time.
If you run Windows, macOS, and Chrome OS, then Deep Instinct is the best solution for your enterprise. Also, it is a lightweight model with low memory consumption. Many high-profile companies, including LG, BlackRock, Samsung, COATUE, etc., use Deep Instinct.
It has various advantages, such as reducing the burden on your SOC team by preventing threats autonomously, and fast, and adding more precision.
There are many reasons to choose Deep Instinct over other popular endpoint protection solutions.
Go through the above-listed features, benefits, pros, cons, and pricing plans before making any final decision. We have also listed a few alternatives to Deep Instinct because most companies find it very expensive.
ManageEngine Endpoint Central Next-Generation Anti-Virus, Malwarebytes for Business, ESET Endpoint Security, Bitdefender, CrowdStrike Falcon, and SentinelOne are a few endpoint protection software that we have selected as alternative solutions for your business. Most of the tools use machine learning techniques to monitor behavior and track regular activities.
ESET Endpoint Security supports a multilayered defense system to protect all devices, whereas Malwarebytes provides botnet and browser-based threats protection. Each tool has a unique feature and capabilities that make it stand out from the rest.
Compare each above-listed tool and its features before choosing the right one for your business and its endpoint security.