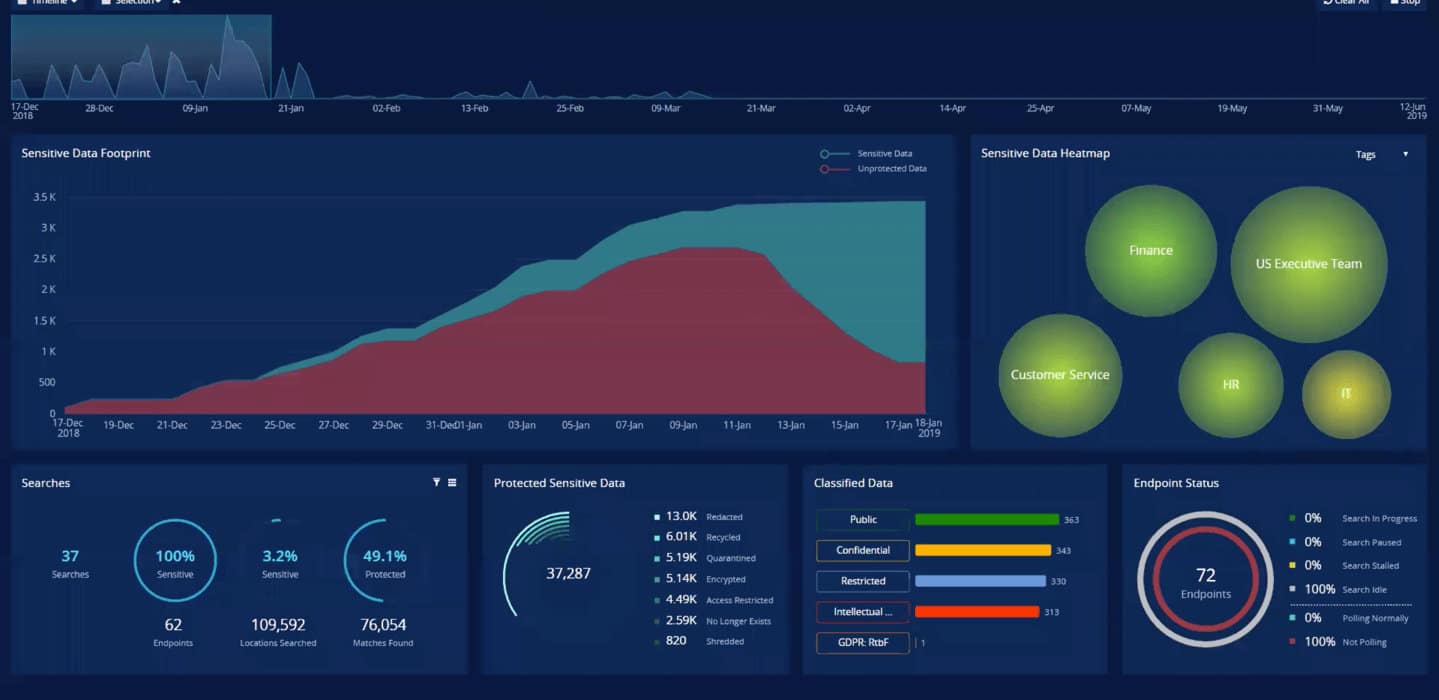
One of the biggest risks businesses face today are cyber incidents. Cyber incidents can not only disrupt your business operations but can also harm your goodwill and create financial damage.
If your business adapts a data-centric security approach, i.e., the use of technologies like encryption and tokenization, we are sure you can minimize the risk of attacks. Further, your business can protect its sensitive information from reaching attackers.
Also, there are many tools and practices available online that organizations can implement to mitigate the risks and drive more success. Here, we will discuss Comforte, a data security platform that has helped various businesses protect sensitive data and prevent breaches.
Further, we will discuss its features, pros, cons, how it works, etc. Also, we have listed a few alternatives to Comforte that can be helpful for your business.
Comforte Product Overview
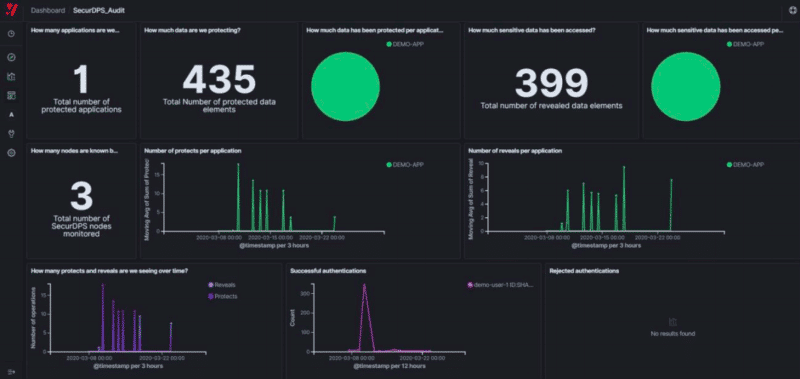
In 1998, Comforte AG was introduced as a data transfer protection system, which later expanded its service and turned into a cloud-based SaaS platform. The purpose of the SaaS platform was to provide data protection to businesses of all sizes.
Today, Comforte is recognized as one of the best Cloud-based Data Security Platforms that helps businesses identify and protect crucial data at all times.
No matter whether you hold your data in the different stores on cloud platforms or other locations, the platform aims to provide 24*7 protection of your business information.
To use the platforms, a business must have personally identifiable information (PII) of each private individual. The system is ideal for financial sectors and other fields that store highly sensitive data, such as payment card data in finance.
How Does Comforte Work
The Comforte Data Security Platform controls the use of crucial data as per the user type. Only the exclusive and authorized users are permitted to access information that further protects your system from any inappropriate use.
It also supports various tools that allow document release without revealing PPI information to third parties.
Here are the five stages for data protection practiced under Comforte:
- Discover and Classify Scans and identifies data for further classification and analysis. This process helps businesses in improving security, privacy, and data governance.
- Inventory The scanning and discovery process continues in this step to keep the inventory up-to-date. Using the collected information, businesses determine access and data exchange requirements.
- Policy The discovery result helps decide which policies must be implemented and who must get the access.
- Protect Encryption, data tokenization, data masking, hashing, and other techniques are supported to implement the data protection policies.
- Deploy In this step, you can deploy or implement the policies on your premises or cloud infrastructure.
The main job of the platform is to enable businesses to identify sensitive data and control access.
Overview of Comforte Modules
There are different modules in the SaaS package which help provide full protection to sensitive data. Here are the details.
- Data Discovery and Classification Under this module, the system runs a search through all networks, devices, and cloud storage services (comprising structured and unstructured data storage systems) for a data store. On discovering a data location, registration is made in the Comforte data management service for supervision. The procedure does not end here, instead, it continues the search and enables businesses to discover a new location. You can also serve Data Subject Access Requests being a holder of PPI.
- Data Protection Unlike other Data Loss Prevention (DLP) systems, Comforte focuses on each location for protecting data. It follows the approach to trust no one and applies protection to sources rather than examining the passage. It uses Tokenization, Encryption, and Masking techniques to protect sensitive data. Tokenization is ideal for databases whereas the encryption method is best used in file-based systems. If your applications require accurate data for testing, you must invest in the masking technique.
- Security Control Data protection is practiced when you want to protect all the sensitive data whereas, the security controls help determine which technique must be applied when and where most important on which data types. These are also referred to as security policies that are decided based on data privacy standards.
Features of Comforte
- Offers data-centric security
- Supports Tokenization, Encryption, and Masking techniques
- Maintains privacy by protecting data at all times
- Supports individual integrated services
- Compliance with data security regulations
- Offers better visibility into threats and risks
- Faster breach response
- Siloed data protection
- Scalable and fault-tolerant data protection system
- Configuration of protection layers
- Supports algorithm methods
- On-Demand Random Assignment-based Tokenization (ODRA)
- Flexible integration framework
- Offers multi-level data protection
- Allows integration with cybersecurity infrastructures
- Cross-Regulatory Compliance
- Supports a robust ticketing system
- Telephone and email 24×7 support
Why do we recommend it?
Comforte offers a comprehensive, data-centric security approach that is both scalable and fault-tolerant. With features like Tokenization, Encryption, and Masking, it goes beyond traditional Data Loss Prevention (DLP) systems to offer nuanced data protection tailored to different data types and locations.
Who is it recommended for?
Comforte is ideal for businesses that need robust, round-the-clock data protection, particularly those handling sensitive or regulated data such as financial or personal information. Its comprehensive feature set makes it well-suited for organizations that operate in cloud-native and modern DevOps environments and require compliance with various data security regulations.
Pros:
- Comforte helps businesses protect and manage data
- Ensures secure card and financial transactions
- Enables businesses to control and secure data 24×7
- Uses Tokenization, Encryption, and Masking techniques to add data protection
- Helps in data discovery
- Ideal for cloud-native and modern DevOps environments
- It helps avoid lengthy service interruptions
- Enables end-to-end data security strategy for business growth
- Comforte helps minimize business liability
- Reduces implementation costs
- Automates and runs data discovery cycle constantly
- Identifies relevant data and classified AI-driven sensitive data
- Supports adaptable security policies
Cons:
- Data exfiltration device control is not supported by Comforte
- Supports no email scanning
- Content inspection options are not supported for outbound documents
Comforte Pricing
The platform does not reveal the pricing list, instead, it provides access to a demo at first to help businesses discover the cost of the products provided by Comforte, a SaaS platform.
Our methodology for selecting the best Comforte alternatives
We reviewed the market for the best Comforte alternatives and analyzed tools based on the following criteria:
- Automated data discovery services so that you can categorize minor data instances
- Runs audit trails and maintains logs of all events and user access to resources
- Automatically interpret all data privacy standards and requirements
- Detects security threats and anomalies in real time
- Free trial or no-cost assessment options for testing the product
The Best Comforte Alternatives
To protect the company’s data at all times, Comforte follows a unique approach. It believes that preventing exfiltration will not be enough to address the problem of accidental disclosure or inappropriate data usage.
When it comes to Database and Big Data Security, it is hard to find a solution that fits all products. But, Comforte’s data-centric top-notch security with exceptional capabilities changes the scenario.
Using various techniques like tokenization, Format Preserving Encryption, and data masking, businesses can protect data and maintain privacy at all times.
If you are planning to switch to other alternative solutions, let us tell you a few points one must review before finalizing an alternative, such as:
- Automated data discovery service that supports categorizing acute data instances
- Access logging and audit trails
- Support for a free trial or a demo system
- Behavior anomaly detection
- Ability to apply different data protection standards at the same time, and more.
Here are a few alternatives to Comforte that fulfill the above conditions:
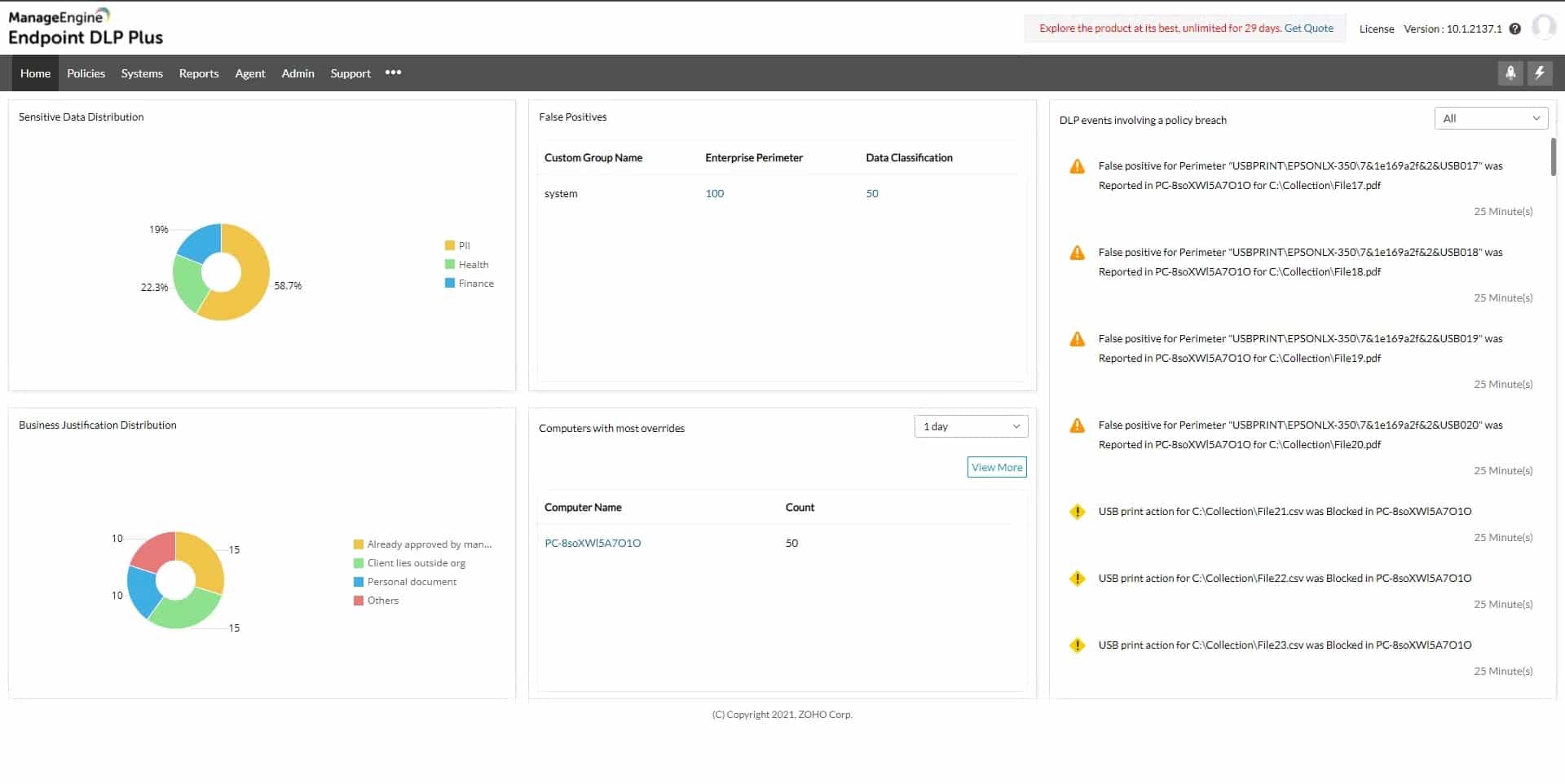
1. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP Plus is a platform designed to safeguard sensitive information on devices, users, and files within a network, and can be applied to both LANs and cloud environments. It utilizes data containerization and intelligent alerting to accurately classify data and minimize false positives, maintaining productivity while maintaining data security.
Key Features:
- End-to-End Encryption Support: Encrypts all sensitive files across the system to prevent data leakage or espionage
- Detailed Backup and Recovery Options: Creates backups for all data in a detailed format and retrieves files when necessary
- Centralized Management: Offers quick setup with full control over data from a single console
- Data Discovery: Automatically runs content analysis to identify all structured and unstructured sensitive data
- Insider Threat Monitoring: Keeps a close watch over user actions and behavior to identify suspicious events and threats
- Device Control: Reduces threat vectors associated with devices by limiting their ability to access or copy sensitive data
- Pre-Defined Templates: Create or use existing pre-defined templates to discover sensitive information
Why do we recommend it?
ManageEngine Endpoint DLP Plus offers a robust set of features including end-to-end encryption, detailed backup and recovery options, and intelligent alerting. Its capability for centralized management and advanced reporting makes it a comprehensive solution for data protection.
The platform also has the capability to automatically detect potentially suspicious user behavior, such as compromised accounts or insider attacks. It is easy to set up and use, even for beginners, with the help of various templates and wizards that enable users to classify sensitive data and implement policies quickly.
Who is it recommended for?
This platform is ideal for organizations that need to secure sensitive data across both LANs and cloud environments. With its user-friendly setup process, it’s suitable for beginners as well as experts in data security, making it a good choice for businesses of all sizes looking for robust data loss prevention solutions.
Pros:
- Encryption: Encrypts almost any portable media and hard drive
- Advanced Reporting: Gain insights with reports on a set schedule as well as run automated audits
- Centralized Management: Allows admins to view their device security from a central place
- Secure Email Collaboration: Only reliable domains are used for data communication
- Intuitive User Interface: User-friendly dashboard with a balance between insights and visuals for efficient administration
Cons:
- Limited Evaluation Option: Demo session is short in comparison to a full-featured trial that would let you check on the tool’s capabilities better
Click here to download your ManageEngine Endpoint DLP Plus 30-day free trial.
EDITOR'S CHOICE
ManageEngine Endpoint DLP Plus is our top pick because it is capable of identifying hijacking attempts and unintentional data leakage in real-time. The robust tool finds files containing all structured and unstructured sensitive data by first scanning every endpoint. After classifying every data element, containerization is used to safeguard every file. Applications that have been designated as trustworthy are the only ones with access to the file. Additionally, the system finds all locations where data is exfiltrated and regulates data flow based on the authorizations given to each user. It even allows admins to closely monitor specific user actions and prevent data theft.
Furthermore, you may quickly build a wide range of endpoint data loss prevention rules with a variety of parameters available. Lightweight agents can be used to remotely distribute these policies, ensuring that security is maintained even while the system is offline.
Download: Download 30-Day Free Trial
Official Site: https://www.manageengine.com/endpoint-dlp/
OS: Windows Server
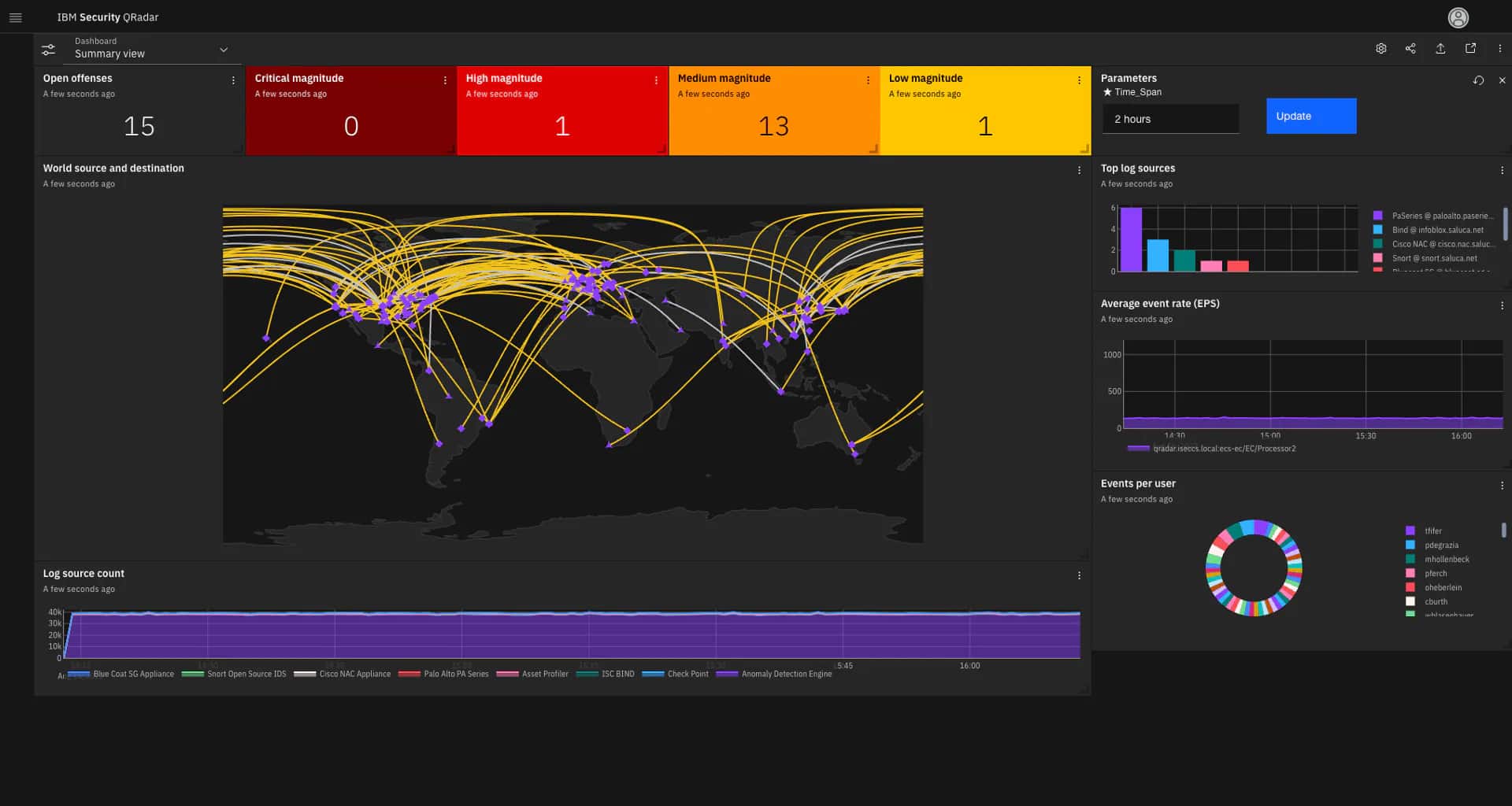
2. IBM Security
IBM Security is one of the best data security and protection solution providers. The platform enables businesses to protect their sensitive information by monitoring and auditing all data activities across multiple environments. It also helps reduce operational complexity and enables enterprises to meet privacy regulations.
Key Features:
- Threat Detection and Response: Offers insights into emerging threats and responds to them early
- Identity and Access Management: Maintains access controls and guards against unwanted access to critical resources
- Data Security: Enforces data protection policies, identifies vulnerabilities, and prioritizes remediation
- Security Information and Event Management: Monitors and analyzes all security events and data in real time to detect threats.
- Data Encryption: Protects data in transit and rest using tokenization and encryption.
Why do we recommend it?
IBM Security stands out for its comprehensive monitoring and auditing capabilities across various environments, aiding in real-time vulnerability management. It not only helps in compliance with privacy regulations but also provides valuable insights through its reporting features.
Who is it recommended for?
IBM Security is recommended for medium to large enterprises that require extensive visibility into their data activities for security and compliance needs. It’s especially beneficial for businesses that are dealing with complex operational structures and require a robust solution to combat cyber threats effectively.
Pros:
- Comprehensive Protection: Offers defense against a wide range of cyber threats
- Threat Detection and Response: Uses AI-driven cybersecurity solutions to identify and respond to real-time threats
- Regulatory Compliance: Assists in maintaining compliance with industry rules and data privacy laws
- Risk Management: Implements risk-based security controls to reduce exposure to cyber threats
Cons:
- Expensive: in comparison to other tools, IBM security could be a bit costly for some users
With the help of the IBM data security platform, you get greater visibility and generate insightful reports that further help in investigating and remediating cyberthreats. Users can also easily discover and manage data security vulnerabilities in real-time. It also supports Encryption and tokenization techniques. If you are looking for a data security platform similar to Comforte features, go for IBM data security as it offers full visibility and covers the above-listed parameters.
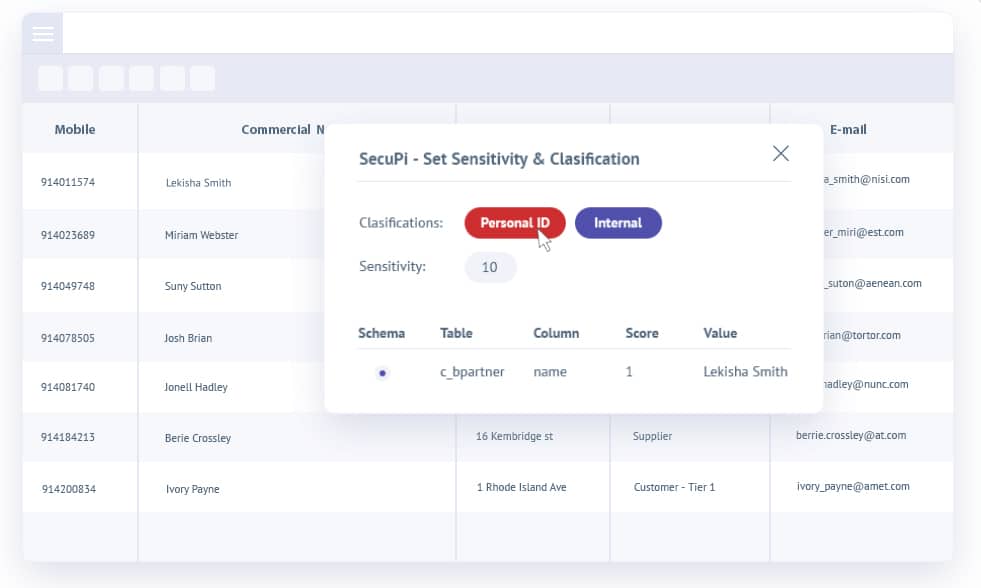
3. SecuPi
SecuPi is another great replacement for Comforte. The tool keeps all your analytics platforms, cloud environments, and applications protected at all times without any development efforts. The tools hardly take more than a day to make production and non-production applications GDPR-ready. It is a centralized solution that protects your systems from insider threats and other cyber attacks. Its features include support for user behavior analytics (UBA), discovery integrations, dynamic data masking, consent controls, monitoring, audits, and more.
Key Features:
- Centralized Platform: Monitors and analyzes all cloud and on-premises application data from a central place
- PCI-DSS Compliance: Uses data-centric security technology to effectively comply with regulatory needs.
- User Behavior Analytics (UBA): Examines user behavior on a network or system within an organization
- Dynamic Data Masking: Keeps critical data safe against unauthorized access by dynamically changing or masking it in real time.
- Dynamic Consent Controls: Gives enterprises the ability to dynamically control user consent for data processing.
Why do we recommend it?
SecuPi excels in delivering centralized protection against both insider threats and cyber attacks, and its quick setup time for GDPR readiness is a significant advantage. The platform also offers a robust set of features including dynamic data masking and user behavior analytics.
Who is it recommended for?
SecuPi is ideal for businesses that are in immediate need of meeting compliance standards like GDPR and are looking for a centralized solution that covers monitoring, auditing, and security features. This tool is particularly useful for companies using multiple analytics platforms and cloud environments that need uniform security controls.
Pros:
- User Activity Tracking: Records and tracks every user interaction with sensitive data for analysis
- Scalable and Efficient: Helps fulfill both present and future regulatory and audit needs
- No Code Changes: Offers quick and cost-effective installation without requiring source-code modifications.
- Comprehensive Data Protection: Supports data discovery, classification, encryption, and other features that help secure data at all levels
Cons:
- Demands Expertise: Can be difficult to deploy, and necessitates a high level of system technical expertise.
Address all your compliance requirements and get access to granular user activity visibility along with other controls in a single platform like the SecuPi platform.
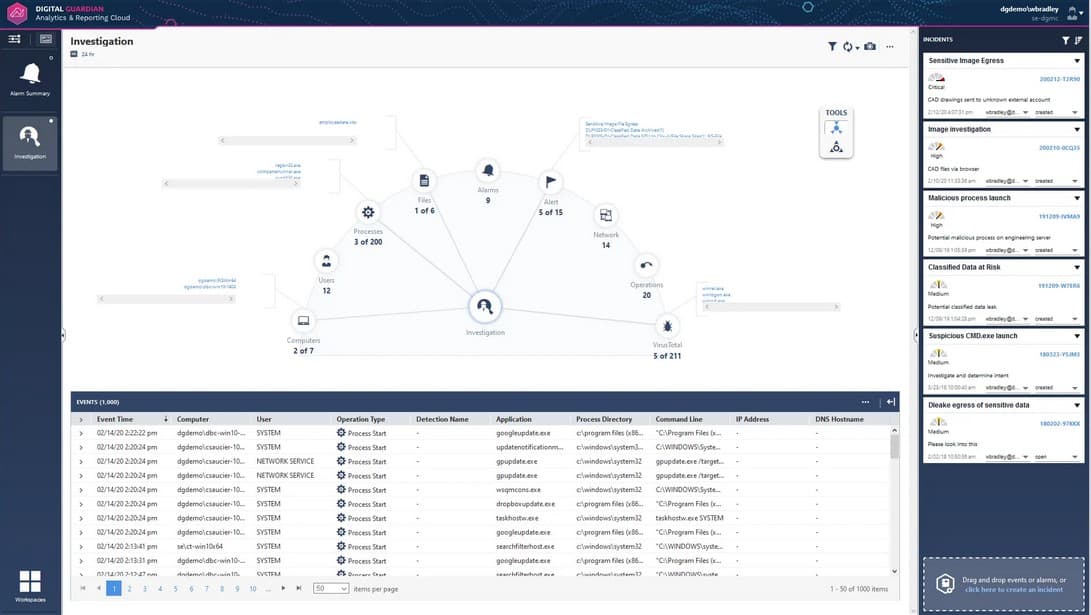
4. Digital Guardian DLP
Digital Guardian DLP is a SaaS platform compatible with Windows, macOS, and Linux platforms. Digital Guardian DLP fits best when it comes to looking for an alternative to Comforte. It supports data discovery and classification modules to protect data discovery and classification. Users can also perform Active Directory audits and work on improving user groups with the help of this excellent tool. It supports no-compromise protection and offers full visibility into your sensitive data.
Key Features:
- Instant Visibility: Allows users to gain clear visibility into the organizational assets and prevent threats
- Data Loss Prevention: Locates, monitors, and protects your sensitive data against serious risks
- Audit Directory: Monitors all the activities that take place within the active directory environment
- Secure Collaboration: Allows users to collaborate and exchange files securely through encryption
Why do we recommend it?
Digital Guardian DLP provides comprehensive data protection across multiple platforms and offers full visibility into your sensitive data. Its ability to manage detection and response while covering all endpoints, networks, and cloud data sets it apart as a robust alternative to Comforte.
Another plus point of this tool is it manages detection and response. Further, it provides full coverage to all endpoints, networks, and data in the cloud. Digital Guardian DLP also enables businesses to monitor all activities on printers, emails, USB devices, and other channels.
Who is it recommended for?
Digital Guardian DLP is recommended for organizations that need a versatile, platform-agnostic solution for their data protection needs. It’s particularly useful for businesses that require thorough audits, including Active Directory, and those who need to monitor a wide range of data channels like printers, emails, and USB devices.
Pros:
- Cloud Data Security: Offers full visibility and control over your data in the cloud storage
- Cross Platform Coverage: Works well and provides coverage across all major operating systems like Windows, Linux, macOS, and endpoints as well as networks
- USB Tracking: Allows users to monitor USB and other data movement channels like printers and emails
- Comprehensive Remediation and Logging: Comprehensive log tracking and reporting enables trend and event analysis, enabling data protection policies to be adjusted as needed.
Cons:
- Program Conflicts: Not an exception to the rule that DLP software frequently has unfavorable impacts in programs. you may experience severe problems with locking up Microsoft Excel and Outlook.
5. Spirion Sensitive Data Manager
Spirion Sensitive Data Manager is another SaaS platform that protects your healthcare and financial information. Its main goal is to identify and protect PII and different variations applied to sensitive data. When it comes to data discovery and persistent classification, Spirion leads the role and protects data available on-premise or in the cloud. Since its launch in 2006, it has helped many companies and proactively minimized their risks and costs.
Key Features:
- Data Discovery: Discovers all sensitive structured and unstructured data on networks, clouds, and servers and reduces security lapses.
- Automated Data Classification: Reduce risks and increase internal security policies by applying suitable data security controls.
- Customizable Dashboard: Customize and view the financial impacts of cyber risks for better decision making
Why do we recommend it?
Spirion Sensitive Data Manager excels in identifying and protecting Personally Identifiable Information (PII) across various platforms. Its strong focus on data discovery and persistent classification makes it a reliable choice for both on-premise and cloud environments.
It supports data exfiltration channel controls, eliminates false negatives and positives, reduces time to locate ever-expanding big data footprints, etc. Also, one can easily run the tool on different platforms, including Windows, macOS, and Linux.
Who is it recommended for?
This tool is ideal for organizations in the healthcare and finance sectors that handle a large amount of sensitive information. It’s also suitable for companies looking to minimize risks and costs related to data management, especially those that operate on multiple platforms like Windows, macOS, and Linux.
Pros:
- Reduce Data Footprint: Classification helps reduce the footprint of sensitive data
- Sensitive Data Discovery: Eliminates false positives by discovering structured or unstructured data
- Minimizes Risk: Constant data remediation contributes to the proactive reduction of data loss risks and financial damage
Cons:
- Insufficient Direct Data protection: Although sensitive data can be identified, but it demands additional data security methods which could result in redundancy.
- Platform Coverage: Relies on Azure but its protection is limited because it does not have particular data tracking features for Azure or Google Cloud Platform.
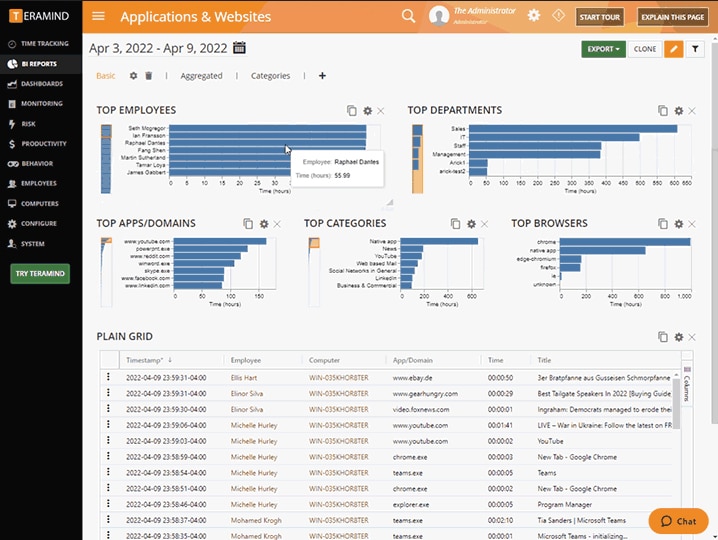
6. Teramind DLP
Teramind DLP is a cloud-based system that provides insider threat protection and secures data at all times. The popular user activity monitoring platform helps detect and prevent the company from fraudulent practices and data misconduct before they occur. It enables the business to investigate the behavior and safeguard data against various malicious and insider threats. It also supports remote employee monitoring, OCR, live and recorded screen caption features, automated alert systems, email monitoring, keystroke logger, file transfer tracking, and more. Its main focus is on employee tracking and supports various modules like productivity logging.
Key Features:
- Remote Desktop Control: Takes remote control of a machine to stop malicious activities and insider threats.
- File Transfer Tracking: Keeps an eye on every file activity for security purposes and compliance
- Live Screen Capture: Allows taking screenshots and video screen recordings to later analyze productivity behaviors.
Why do we recommend it?
Teramind DLP stands out for its comprehensive approach to insider threat protection. With features like live and recorded screen capture, automated alerts, and keystroke logging, it provides an all-around safeguard against various forms of data misconduct and fraudulent activities.
Who is it recommended for?
This tool is particularly useful for businesses that need robust employee monitoring solutions. Whether you are looking to improve productivity, investigate behavior, or secure sensitive data from insider threats, Teramind DLP provides a range of modules tailored to these needs. It’s also suitable for companies with remote workforces.
Pros:
- Insider Threat Protection: Prevents sensitive data from malicious threats originating inside your organization
- Fraud Detection: Identifies fraud activities and prevents data misconduct
- Employee Work Pattern Monitoring: Uses machine learning technology to monitor and investigate threat behavior
Cons:
- Overwhelming for Small Businesses: Wide range of features offered by the tool can be difficult to manage for small businesses
Users can try the 14-day free trial before moving to the premium plans if needed.
Conclusion
No doubt cyberattacks can harm your goodwill and disrupt your business operations leading to heavy losses. To save your business from future damage, it is best to implement data security tools that will help detect security vulnerabilities before they launch. With the help of technologies like encryption and tokenization, you can minimize the risk of attacks. There are various tools and platforms that support these technologies like Comforte.
Comforte is trusted by thousands of customers globally, including some of the largest banks, retailers, and credit card processors. The popular platform helps businesses in managing and protecting third-party data from malicious and insider threats. It includes various products, such as SafePoint, SecurLib/SSL, SecurSSO, JPath, CSL, etc.
Comforte is a cloud-based data security platform that manages your data in different stores on cloud platforms and other places. Businesses of all sizes can invest in Comforte for data protection services. Under Comforte, only the permitted and authorized users get access to use the information. Thus, this practice helps protect your system from any inappropriate use.
Furthermore, there are five stages for data protection; Discover and Classify, Inventory, Policy, Protect, and Deploy. It also supports different modules (Data Discovery and Classification, Data Protection, and Security Control) in the SaaS package, which helps provide full protection to sensitive data. The platform enables businesses to control and secure data, maintains privacy, aids in data discovery, reduces implementation costs, etc. However, there are a few drawbacks too.
If you are looking for alternatives to Comforte, we have listed some of the best tools one can invest in to get similar features and services. ManageEngine Endpoint DLP Plus, IBM data security, Digital Guardian DLP, Spirion Sensitive Data Manager, Teramind DLP, and SecuPi are a few SaaS platforms that also provide similar features and enable businesses to protect data at all times from threats.
Compare the above-listed tools before making any final decision as data protection is vital for every business.