Cyber security has become a requirement for businesses of all sizes as malicious actors have become a potential threat to their systems and networking infrastructures containing sensitive and valuable data. For an efficient and robust cyber presence, the strategy makers support different approaches, such as log management, SIEM, intrusion detection, etc.
It is essential for organizations to have a tool or platform that provides visibility into the security of their environment and comprises other security capabilities.
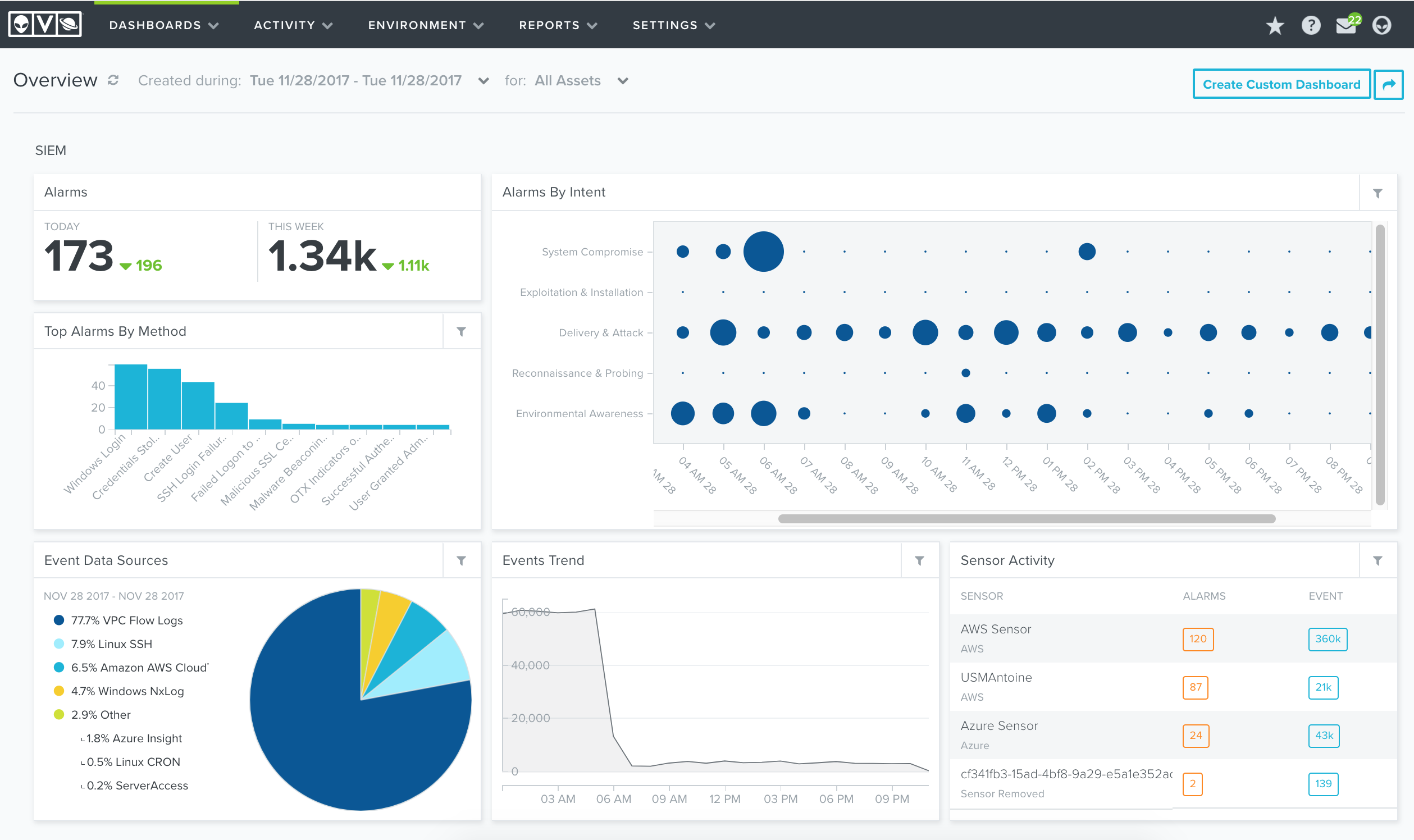
AlienVault Unified Security Management (USM) is a powerful network monitoring platform that combines all these capabilities and helps safeguard digital assets. It merges all essential tools and develops commercial and open-source cybersecurity tools.
Here, we will discuss AT&T Cybersecurity (AlienVault), its features, benefits, drawbacks, and pricing plans. Further, we will discuss a few alternatives to the tool that can also help safeguard digital assets.
AT&T Cybersecurity Overview
AlienVault, powered by an AT&T company, is a fully-featured Security Management Software available in two forms USM and OSSIM. AT&T Cybersecurity helps in developing open-source cybersecurity tools with more robust capabilities. These tools enable IT teams to check on the security, including asset discovery, vulnerability management, intrusion detection, and behavioral management.
Key Features
- Asset discovery and inventory
- Supports Behavioral monitoring
- Intrusion detection
- Vulnerability management
- SIEM event correlation
- File Integrity Monitoring
- Real-Time Monitoring
- Web Threat Management
- Prioritization
- Patch Management
- Sensitive Data Identification
- Supports multiple options for the deployment
- Compliance management
- Integrates with third-party ticketing tools like ServiceNow, Jira, etc.
- Product forums for community support
- Security Orchestration and automation
- Unlimited Threat Intelligence
- Mail and phone support
- Knowledge base and product documentation available online
- Data Visualization and analytics dashboards
- Log management
- AWS and Azure cloud monitoring
- Cloud apps security monitoring
Why do we recommend it?
We deployed AlienVault in a sandbox environment to evaluate its multiple functionalities, including its asset discovery and vulnerability management capabilities. The SIEM event correlation and file integrity monitoring features performed exceptionally well, making it a comprehensive choice for security management.
AlienVault Unified Security Management (USM) is an advanced version of AlienVault OSSIM with additional benefits, including log management, threat intelligence, AWS and Azure cloud monitoring, pre-built report templates, etc.
The platform provides security on-premises and to the hybrid cloud by merging all tools in one location. As a result, the centralized platform helps in reducing complexity and deployment times.
It also has support for a crowd-sourced computer-security platform – Open Threat Exchange (OTX). The exchanges enable users to access reliable solutions for detecting threats and incident response.
The tool allows users to scan all log files and generate vulnerability assessment reports for all devices and applications. It is highly compatible with Mac and Windows platforms. Also, users can easily share information related to threat detection on portals to improve the system and its performance.
If you are looking for a credible open-source SIEM tool for your business, invest in AlienVault OSSIM as it supports various functionalities and uses artificial intelligence to help detect hidden threats. You can also look forward to community support via product forums.
It is a highly advantageous tool but also comprises a few drawbacks due to which people look for alternate solutions. Follow the below-listed features, and their pros and cons before switching to the alternatives.
Who is it recommended for?
AlienVault is a suitable solution for businesses that require both on-premises and cloud-based security monitoring. Given its extensive features and compliance management tools, it’s ideal for organizations that must adhere to standards like HIPAA and NIST CSF. It’s particularly beneficial for companies that value community support and real-time threat intelligence updates.
Pros:
- AlienVault is a commercial or open-source SIEM with event collection and correlation features.
- It is an all-in-one platform with essential security capabilities
- Allows contributing and receiving data about malicious hosts in real-time.
- Helps improve security visibility and control.
- Offers compliance services
- Allows centralized threat detection and incident response
- Highly compatible with Mac and Windows environment
- Detects threats across cloud and on-premises infrastructure
- Supports Log management for constant compliance and investigation
- Discover minimal false positives in real-time
- Offers constant threat intelligence updates
- AlienVault provides pre-built compliance reports for HIPAA, NIST CSF, etc.
- Easy to deploy a single platform
- The unified security platform eliminates costs and clutters management of point solutions
- Delivers critical insights
- Supports monitoring of physical IT infrastructures, Microsoft HyperV, Amazon Web Services, etc.
Cons:
- It requires considerable time and effort to set up the tool.
- It requires customization, especially in Windows environments
- Supports limited log management options
- Supports limited Application and database monitoring features
AT & T (AlienVault) Benefits
Being a top-notch cybersecurity tool, AlienVault has many benefits, such as threat protection, limitless intelligence through AlienVault USM Labs, and multiple deployment features. Apart from these, there are more benefits associated with AlienVault USM (from AT&T Cybersecurity):
- Unified security platform AlienVault supports the unified approach for detecting threats and incident response. As a result, businesses can save on costs and clutter management of point solutions. It is an all-in-one solution with excellent security capabilities (vulnerability scanning, asset discovery, intrusion detection, behavioral monitoring, SIEM) and advanced features. With the help of its unified approach, businesses can focus more on responding to threats and fixing issues before they launch rather than managing troubles associated with the deployment and handling of various products.
- Offers Unlimited threat intelligence Another advantage of investing in AlienVault USM (from AT&T Cybersecurity) is that the system’s Labs research team enables businesses to access unlimited threat intelligence. The OXT (Open Threat Exchange) information and intelligence together help deliver critical insights to users. With the help of insightful reports, a business can easily respond to security threats.
- Support Multiple deployment options AlienVault USM supports different deployment methods. Further, it helps enterprises in meeting various business requirements. No matter whether the infrastructure is hosted in a data center, in the private or public cloud, or in a hybrid environment, the features of AlienVault USM provide businesses with a proper solution suitable to their operations and requirements. AlienVault USM Anywhere was designed with lightweight software sensors and endpoint agents for collecting log data and other security information. With the help of AlienVault USM Anywhere, a business can also conveniently monitor different platforms, such as Microsoft Azure Cloud, Amazon Web Services, Microsoft HyperV, VMware, and physical IT infrastructures. It supports a secure hosted cloud that collects all data, identifies a threat, and performs security analysis. If your organization requires on-premise management, AlienVault USM Appliance is an ideal solution for your business. The best part about AlienVault USM (from AT&T Cybersecurity) is it supports various application-based features that can be used for scans, collection, and tracking of data from different infrastructures. Collected data is later stored in physical and virtual appliances hosted by the enterprise’s infrastructure.
- Maximizes security investment Organizations that choose AlienVault over other tools get access to a wide range of technologies like endpoint analytics and services, such as threat protection. The tool helps discover threats before they launch which further helps reduce the high volumes of errors and inaccurate alerts. This also benefits businesses to focus on core IT functions rather than just hunting for threats and identifying breaches.
Once you have correctly identified the threat and are aware of how to respond and deal with it, you can save your business from the common struggles. Your experts no longer have to handle the burden all alone.
AT & T (AlienVault) Integrations
View a list of AlienVault integrations offered by the vendor:
- IBM
- Barracuda
- WatchGuard
- Sophos
- Cisco
- Juniper Networks
- Fortinet
- Carbon Black
- Redhat
- Microsoft
- FireEye
Pricing and Plans
AlienVault USM (from AT&T Cybersecurity) is available in different packages – essential, standard, and premium designed for every customer. It does not offer any free plan, but trial and premium subscriptions are available with paid plans.
Get access to Vulnerability assessment, Intrusion detection, Log management, Compliance reports, Incident response, and other features along with 15 days of real-time event search in the Essential package starting at $1075/month.
The Standard Package is best suitable for IT teams who wish to perform deeper security analysis and gain efficiency. Starting at $1695/month, the tool additionally offers Endpoint detection and response, Orchestration with security tools, Dark web monitoring, Integrated ticketing and alerting features, etc., with 30 days of real-time event search.
The Premium Package starts at $2595/month and offers support for higher data volumes, PCI log storage requirements, and enhanced support case response times along with Standard package features. The package is designed to meet specific PCI DSS audit requirements with 90 days of real-time event search.
AlienVault USM (from AT&T Cybersecurity) is great for all businesses. Hence, choose the package as per your business requirement and budget.
Website Link: https://cybersecurity.att.com/
The Best AT&T Cybersecurity Alternatives
No doubt, AlienVault USM (from AT&T Cybersecurity) is a great tool to detect cyberthreats and discover vulnerabilities in real-time. But, you can also go through similar alternatives or competitors to find better results. SIEM technology offers a high-quality solution with advanced analytics and vulnerability assessment features. If you are planning to switch to other SIEM tools, make sure to consider various factors before selecting one for your business.
However, we have listed a few alternatives to AlienVault USM (from AT&T Cybersecurity) that can be highly beneficial to your business and performance.
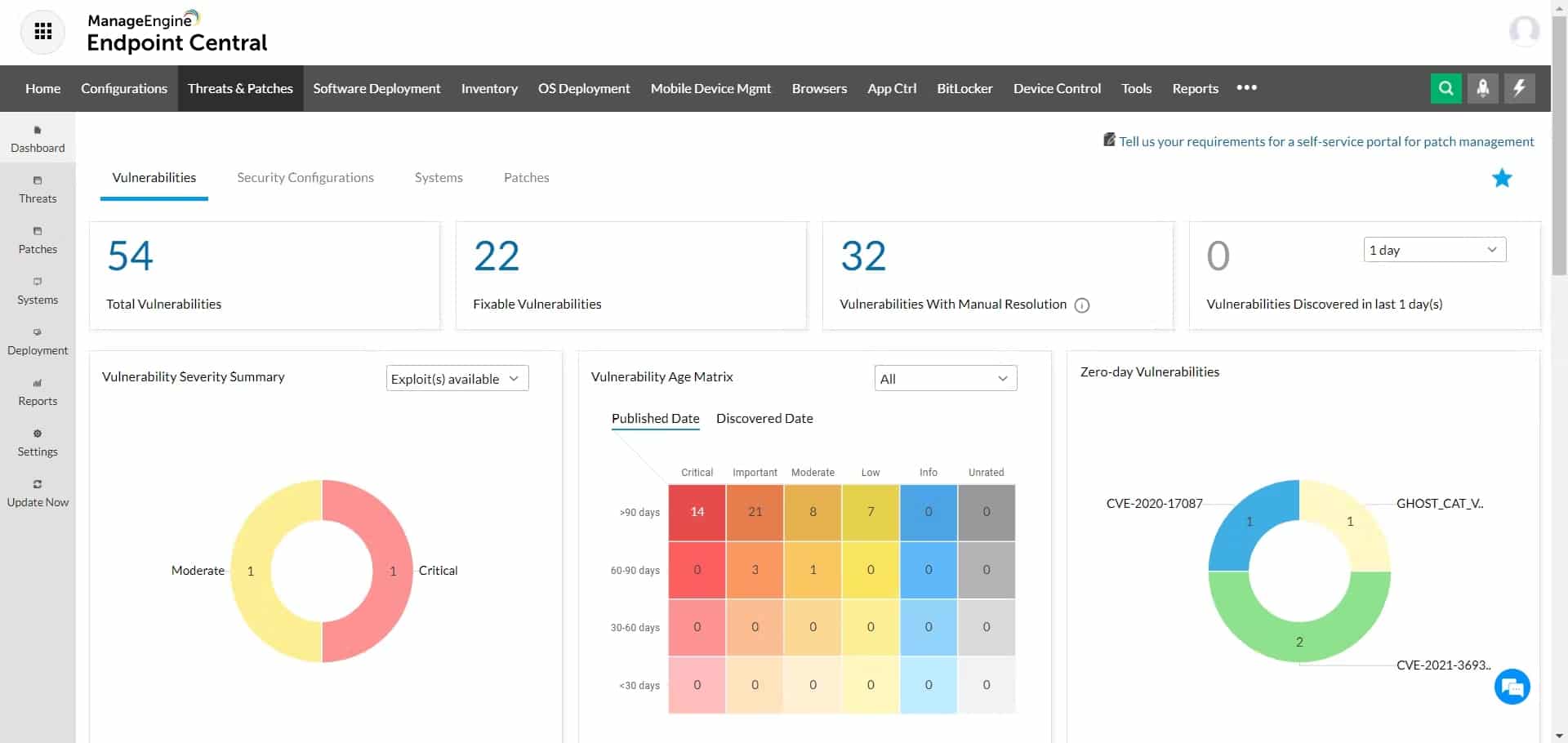
1. ManageEngine Unified Endpoint Management and Security (UEMS) – FREE TRIAL
An organization’s devices can be managed and secured using ManageEngine Unified Endpoint Management and Security (UEMS). IT personnel may efficiently manage and monitor devices, such as laptops, smartphones, and tablets, from a centralized console using UEMS. By allowing administrators to create policies and roll out software upgrades, the platform ensures that all devices are updated and secured.
Key Features:
- Centralized device management
- Detailed security controls
- Comprehensive enterprise reporting
Why do we recommend it?
After installing ManageEngine UEMS and administering it across multiple devices, we were particularly pleased with its centralized device management and detailed security controls. Its automatic asset discovery feature simplified inventory management, confirming its utility as one of the top endpoint management solutions.
Who is it recommended for?
ManageEngine Unified Endpoint Management and Security is ideal for MSPs or NOC teams of any size looking for a centralized and scalable solution. Its robust feature set also makes it a compelling choice for organizations that need helpdesk support, thanks to its variety of automated remote administration options.
Pros:
- Excellent monitoring dashboard, great for MSPs or any size NOC teams
- Scalable cloud-based deployment
- Automatic asset discovery makes inventory management easy, even on busy networks
- A wide variety of automated remote administration options make it a solid choice for helpdesk support
Cons:
- The platform can take time to explore all of its features and configuration options fully
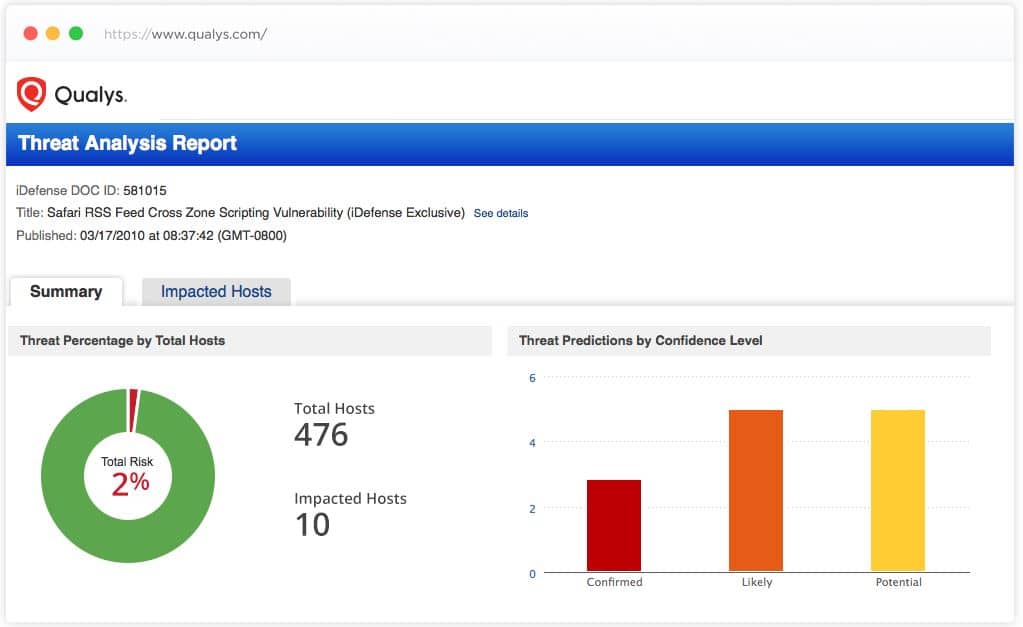
2. Qualys Cloud Platform
Qualys Cloud Platform is one of the alternative solutions and a fully-featured Security Management Software. If you are looking for a tool that will provide end-to-end solutions for your enterprise or small-medium-sized businesses, invest in Qualys. Qualys Cloud Platform provides continuous visibility and excellent solutions for security risk and compliance management. It has sensors that offer constant visibility to all your IT assets. These are centrally managed and available as physical or virtual appliances. The tool comprises cloud agents, remote scanners, Container Sensors, Out-of-Band Sensors, and local scanners to keep an eye on hackers and detect threats in real-time. It also supports Cloud Connectors that help in data collection from other sources and platforms. The SaaS connectors enable businesses to collect information from leading SaaS applications. It also offers integrations with third-party cloud platforms, such as Microsoft Azure, Amazon Web Services, and Google Cloud Platform. By investing in Qualys Cloud Platform, users can automatically collect, analyze security and compliance information, and respond to threats. It also provides real-time alerts on detecting any suspicious activity or new vulnerabilities in the network.
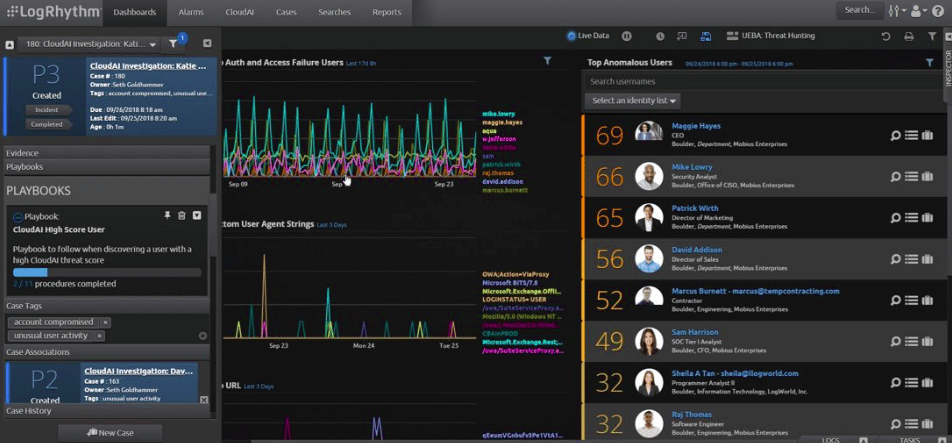
3. LogRhythm NextGen

LogRhythm NextGen is a great tool to mitigate threats and save organizations from future damage or data loss. LogRhythm is a SIEM platform that provides insightful data required for faster remediation of security incidents. It enables users to identify and discover life-threatening cyber attacks before launch.
Why do we recommend it?
We navigated through LogRhythm NextGen’s interface, tested its threat detection features in a sandbox environment, and were fairly impressed. The tool’s continuous correlation with its AI engine allowed for quick and efficient identification of potential cyber threats, validating its strong capabilities in the SIEM sector.
Who is it recommended for?
LogRhythm NextGen is well-suited for organizations that are seeking a SIEM solution to automate repetitive tasks and improve operational efficiency. It’s particularly advantageous for businesses that require a high degree of visibility across various endpoints, networks, and cloud environments, thanks to its customizable dashboards and data normalization features.
The tool hardly takes any time to stop threats, identify, automate and collaborate investigations. With the help of the LogRhythm NextGen SIEM platform, your business can gain full visibility across the environment and remove blind spots from endpoints, networks, and clouds. You can easily spot errors and threats across the environment using the tool. Another advantage of choosing LogRhythm NextGen is you do not have to spend extra time on maintaining, feeding, or caring for the SIEM tool. Instead, the tool makes the analysis and threat detection process easier for IT teams by automating repetitive tasks and labor-intensive work. Further, you can achieve high performance with reduced operating costs using LogRhythm NextGen. Key features of LogRhythm NextGen include continuous correlation with the AI engine, customizable dashboards, cloud or on-premise deployments, data normalization, and access to precise results with structured and unstructured search.
4. Splunk Enterprise Security (ES)
Splunk Enterprise Security (ES) is a security platform with traditional SIEM capabilities and features. With the help of Splunk, businesses can easily combat threats, monitor, scan, visualize, protect and mitigate risk at scale.
Why do we recommend it?
After installing and navigating through Splunk Enterprise Security’s interface, we were impressed by its real-time data analysis capabilities and customizable dashboards. We found it highly effective for quick threat detection and remediation, making it a top contender in the SIEM category.
Who is it recommended for?
Splunk Enterprise Security is particularly useful for medium to large enterprises that require a robust and scalable SIEM solution. It’s also an excellent choice for businesses with complex data environments, as it can collect and analyze big data from multiple sources for comprehensive threat monitoring.
It enables users to analyze all the machine-generated data in real-time. Another advantage of Splunk is it enables businesses to collect big data from multiple sources and perform analysis for quick threat detection and remediation. You can use the tool for performing log management and analysis like other SIEM tools. Further, it allows businesses to store all the collected data or real-time event information as indexers or in a searchable format using Splunk. It has an easy-to-use dashboard with various plugins and customization options that help in generating insightful reports. Get access to faster troubleshooting, automatic discovery of data, team collaboration features, monitoring of business metrics, and more in one platform. One can also save all the searches and tag useful information as per the requirement. Built on an open and scalable data platform, Splunk makes it easier for businesses to manage threat intelligence and protocol intelligence configuration, event processing, deployment requirements, initiate flexible investigations, risk analysis settings, etc.
5. IBM Security QRadar
IBM Security QRadar is another SIEM product that helps in the collection and real-time analysis of security log information. It allows users to collect data from different sources, including the enterprise, network devices, host assets, and multiple operating systems.
Why do we recommend it?
We set up IBM Security QRadar in a sandbox environment and were particularly struck by its purpose-built AI and pre-built playbooks for threat hunting. The event processors streamlined the data collection and analysis, allowing for rapid identification of malicious activities.
Who is it recommended for?
IBM Security QRadar is ideal for organizations seeking an advanced SIEM solution that can handle a variety of data sources and network flows. It’s a strong option for businesses that prioritize real-time analysis and threat hunting, and it’s particularly beneficial for those looking to integrate threat intelligence feeds.
The collected data is then used to analyze the network flow and detect malicious activities. As a result, by using IBM QRadar, you can timely detect and prevent damage. The tool comprises event processors that make the process of collection, storage, and analysis simple and easy to manage. You can deploy it as a SaaS offering on the IBM cloud or as hardware, software, or virtual appliance. The open architecture of QRadar prepares you in advance for future demands and saves time with its purpose-built AI and pre-built playbooks. There are many benefits of investing in IBM Security QRadar, such as improving threat hunting and response by eliminating silos, speeding up alert triage, supporting threat intelligence feeds, and generate insightful reports. Organizations can better analyze and prioritize threats using IBM Security QRadar. If you are looking for an alternative to AT&T Cybersecurity tools, switch to IBM Security QRadar as it is one of the reliable tools that detects and eliminates threats faster compared to other tools.
6. Dynatrace
Dynatrace is an all-in-one AI-powered platform that helps businesses monitor all networks without worrying about their location. It is an easy-to-use comprehensive application monitoring solution trusted by most DevOps.
Why do we recommend it?
We installed Dynatrace and put its AI-powered monitoring capabilities to the test across multiple virtual servers. The tool excelled in offering automatic and intelligent observability, making it one of the standout solutions for infrastructure and application monitoring.
Who is it recommended for?
Dynatrace is particularly beneficial for DevOps teams and enterprises that need to monitor complex, multi-cloud environments. It is also an excellent choice for businesses focusing on digital experience management, as it offers robust features for performance lifecycle management and business analytics.
If you are looking for a tool that enables you to monitor or administer thousands of servers effectively, look no further. Using this SaaS system, companies can track business analytics, monitor application and cloud performance, serverless functions, etc. It is an artificial intelligence (AI) technology-based tool that helps businesses monitor the infrastructure efficiently. Invest in the enterprise-grade monitoring tool for checking the availability of software applications and delivering high performance. Key features of Dynatrace include container and cloud monitoring, digital experience management, performance lifecycle management, business and performance analytics, infrastructure monitoring, and more. Work seamlessly across your full stack and drive better business results using the AI-powered platform. Further, the alternate solution helps simplify cloud complexity and detects threats easily and faster. It supports 600+ technologies and additional features like automatic and intelligent observability, multi-cloud, and technology support.
Conclusion
Many open-source SIEM solutions are available online that can meet your business requirement and provide visibility into the security of your environment, such as AlienVault USM (from AT&T Cybersecurity).
AlienVault USM (from AT&T Cybersecurity) is a popular open-source cybersecurity tool that supports asset discovery, vulnerability management, intrusion detection, and behavioral management. These features enable businesses to detect threats in real-time and incident response.
Available in essential, standard, and premium packages, a few businesses find the tool expensive. Hence, we have listed similar alternatives or competitors to AlienVault USM (from AT&T Cybersecurity). Compare the above-listed tools and then make a final call for your business.