Cybercrime has unfortunately become an integral part of our digital lives today. Almost every organization in the world today has reported a data breach or a cyberattack at least once, and this goes to show the ubiquity of these attacks. In this article, we will take a look at some of the best attack surface monitoring tools and their features to help you decide the best fit for your organization.
Here is our list of the best attack surface monitoring tools:
- Intruder – EDITOR’S CHOICE Access this attack surface scanner through a website and launch scans on demand or set up a schedule. Also available in a cheaper version with monthly scans and with options for dynamic application security testing. Access a 14-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL Software solution offered by ManageEngine, assists companies in identifying and remedying vulnerabilities within their devices and network. Start a 30-day free trial.
- Rapid7 InsightVM Advanced vulnerability assessment and mitigation tool that continuously scans your network, discovers vulnerabilities, and automatically remediates them when possible.
- CoalFire Attack Surface Management Continuous attack surface management service identifies, prioritizes, and manages your external-facing assets to reduce the chances of an attack.
- Immuniweb Discovery AI platform enables businesses of all sizes to test and secure their applications, cloud services, devices, and networks from external threats.
- CyCognito Attack Surface Management Scans your attack surface area to identify vulnerabilities and reports the same for quick and easy mitigation.
- UpGuard BreachSight This comprehensive tool not only monitors your attack surface area but also prevents breaches and protects your sensitive information including customers’ data.
Typically, hackers exploit one or more vulnerabilities in an organization to enter its network and commit a crime such as stealing data, locking the critical systems to demand a ransom, exhausting the organization’s digital resources, and more.
The vulnerabilities or the areas that are susceptible to these attacks is called an attack surface. It includes both physical areas such as data centers and digital areas such as unpatched user devices, an unprotected network, and more.
Organizations routinely assess their vulnerabilities and try to address the gaps. This is called attack surface analysis. Many strategies and tools that help with this attack surface analysis and organizations take the information gathered from these tools to understand their current security state and to take further action to mitigate an attack.
Our methodology for selecting the best attack surface monitoring tools
We’ve broken down our analysis for you based on these key criteria:
- Emphasis on tools with advanced vulnerability scanning capabilities, ensuring comprehensive detection of potential threats on the network
- Selection of tools offering real-time monitoring and alert systems, crucial for immediate identification and response to security issues
- Preference for user-friendly interfaces, allowing for easy navigation and understanding, coupled with robust reporting functionalities
- Consideration of scalability and integration features, ensuring the tool adapts to growing network demands and works well with existing security infrastructure
- Evaluation of cost-effectiveness, including the availability of free trials or versions, and the presence of responsive and knowledgeable customer support
The Best Attack Surface Monitoring Tools
Let’s now jump into a detailed look at the offerings of each of these tools.
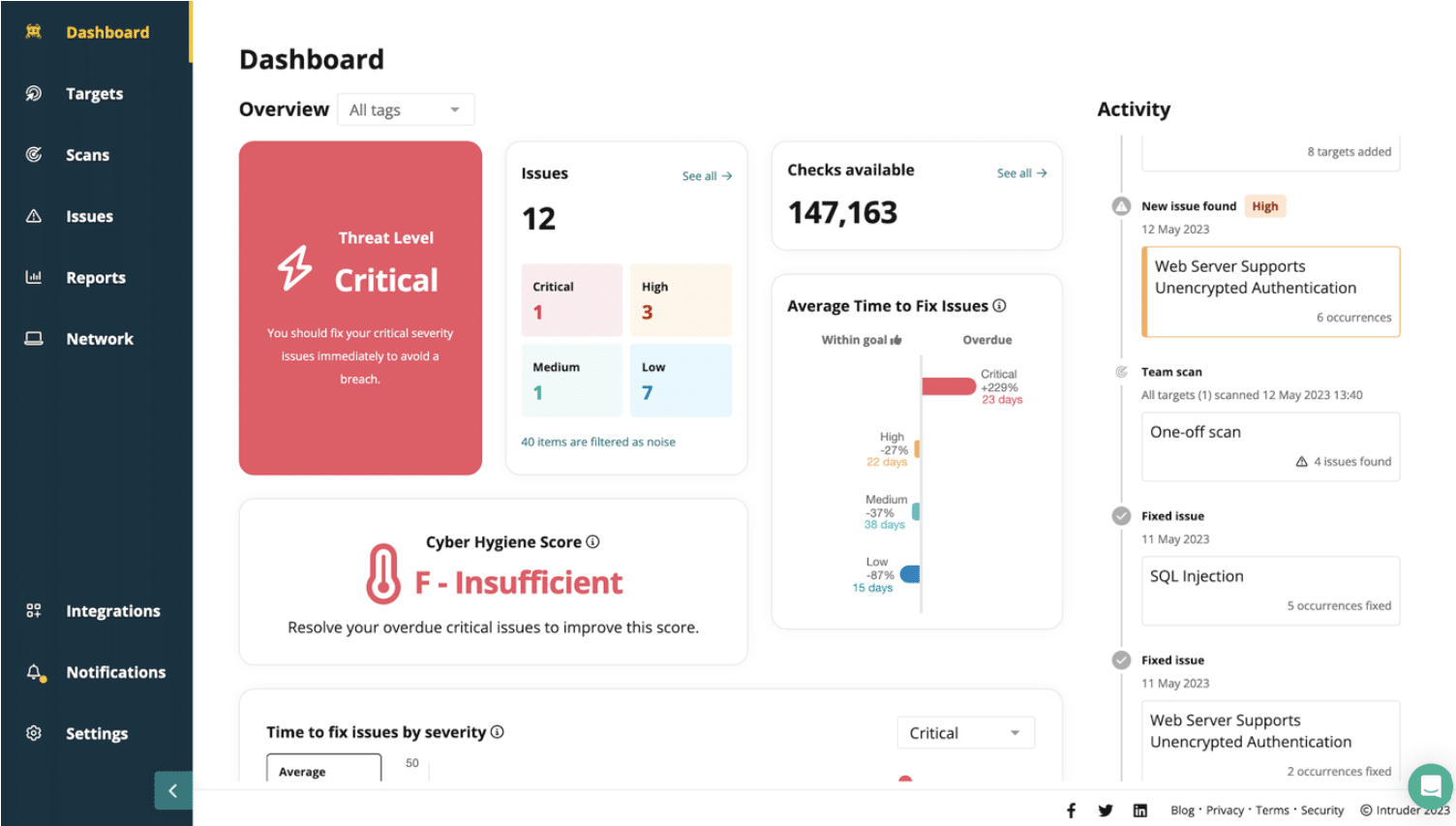
1. Intruder – FREE TRIAL
Intruder is a vulnerability management solution to reduce your attack surface. Intruder kicks off scans when it detects changes in your environment, such as an unintentionally exposed service. It will also run automatic scans for emerging threats, saving you time
Key Features:
- Automated cloud and Emerging Threat Scans
- Developer integrations
- Attack Surface management
- OpenVAS or Tenable
- Scheduled and on-demand scans
- External and internal scanning
Why do we recommend it?
Intruder excels at automated vulnerability management, offering both scheduled and on-demand scans to cover external and internal risks. Its flexibility in scanning options, along with integration capabilities for developers, makes it a robust choice for reducing your attack surface.
The entry-level Essential plan gives you a monthly external scan and unlimited on-demand scans. The two higher plans give unlimited scans and you can decide how frequently you want them to run. Those upper plans also allow on-demand scanning. The company also offers dynamic application security testing (DAST) for web applications and APIs that can be added to any plan.
The external scanner is very easy to access. It doesn’t need any installation; the internal scanner requires agents to be installed on all of your endpoints.
Who is it recommended for?
Intruder is ideal for businesses with dynamic environments that need constant monitoring for vulnerabilities, such as cloud-based services or frequently updated web applications. It’s also suitable for companies looking to integrate vulnerability scanning into their development pipeline.
Pros:
- Choice of monthly scans or unlimited attack surface scans
- On-demand external scanning
- Internal vulnerability scanning option
- Web application and API testing option
- Easy to launch from a website
Cons:
- If you need more capabilities and features, you can upgrade to the higher plans
Download: This service is delivered on a website so you don’t need to download anything to use Intruder’s attack surface scanner. Sign up on the site for a 14-day free trial.
EDITOR'S CHOICE
Intruder is our top pick for an attack surface monitoring tool because it provides very attractive options that suit all sizes of businesses. Small businesses on tight budgets can access the Essentials plan that provides external scanning with OpenVAS. Larger businesses that want more frequent scans and an on-demand option can get a Tenable service. Other features of the Intruder.io platform include a Web application tester that can be set up to run continuously as part of a CI/CD pipeline.
Download: Get a 14-day FREE Trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
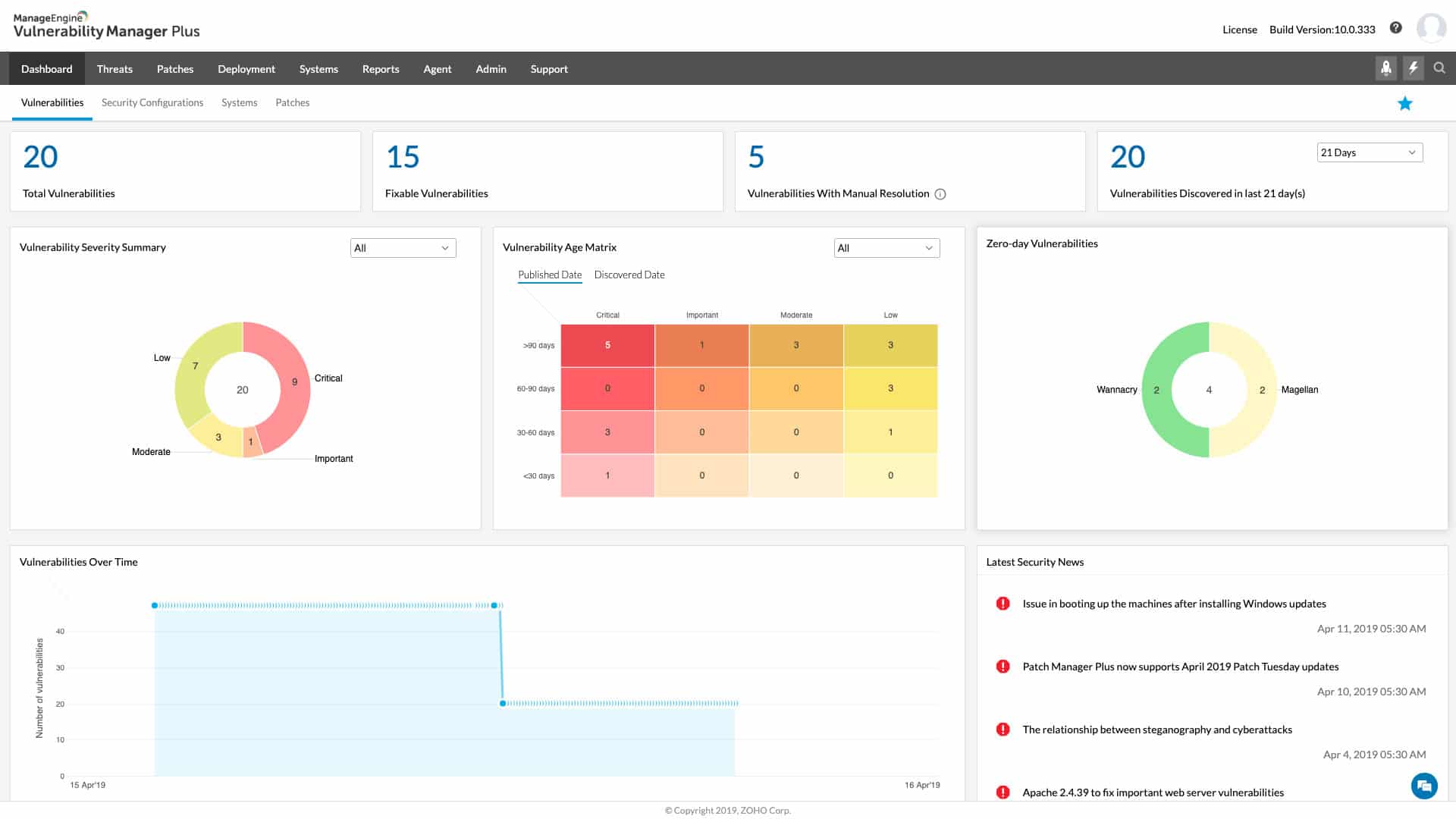
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus uses vulnerability scanning to detect potential vulnerabilities such as insecure configurations or outdated patches and subsequently generates comprehensive reports of its findings.
Key Features:
- Comprehensive vulnerability discovery and remediation
- Streamlined remediation with root cause analysis
- Automated scanning and reporting
Why do we recommend it?
ManageEngine Vulnerability Manager Plus provides a comprehensive approach to vulnerability management, covering detection, analysis, and remediation. Its strong reporting capabilities and multi-platform support make it a versatile and effective tool for enhancing network security.
The software also provides asset management, compliance reporting, and patch management capabilities to aid businesses in securing their IT infrastructure. In addition, it offers remediation recommendations, including detailed instructions and connections to relevant resources, to help companies address vulnerabilities identified.
Proactively identifying and addressing security gaps, Vulnerability Manager Plus can enhance the overall security of a business’s network and devices.
Who is it recommended for?
This tool is highly recommended for businesses of all sizes, especially those that operate in mixed OS environments involving Windows, Linux, and Mac. It’s also a great fit for organizations that require robust reporting for compliance purposes and those who are seeking a cost-effective solution, given its free version tailored for small businesses.
Pros:
- Excellent for ongoing scanning and patching throughout the lifespan of any device
- Strong reporting capabilities can demonstrate progress after remediation
- Versatile – can operate on Windows, Linux, and Mac
- The threat intelligence database is regularly updated with the latest threats and vulnerabilities
- Offers a free version, ideal for small businesses
Cons:
- The ManageEngine ecosystem is quite complex, best suited for large-scale organizations
Click here to download your ManageEngine Vulnerability Manager Plus fully functional 30-day free trial.
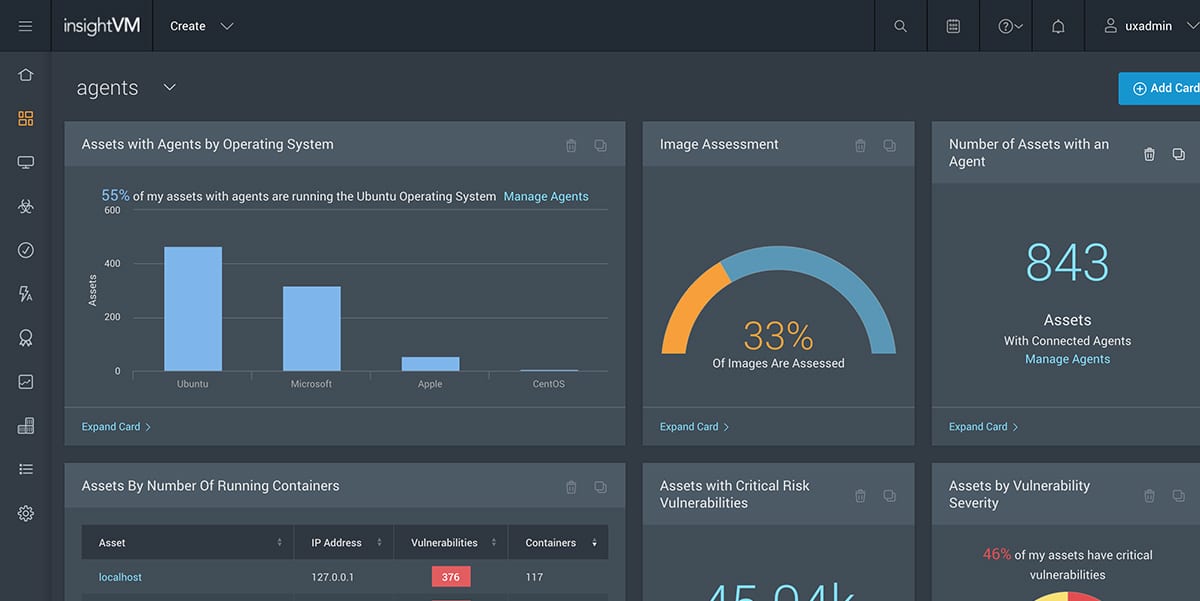
3. Rapid7 InsightVM
InsightVM from Rapid7 is a comprehensive attack surface monitoring tool that continuously scans your attack surface area for possible vulnerabilities and reports the same. Undoubtedly, it provides better risk clarity and even tracks the progress you’ve made in fixing the reported vulnerabilities.
Key Features:
- Comprehensive Data Gathering InsightVM has lightweight endpoint agents that continuously gather data from all your endpoints, including the devices used by remote workers. It even monitors those endpoints that join the network only occasionally. This continuous and automatic data gathering can alert you when some values indicate a likely attack.
- Intuitive Dashboards InsightVM’s dashboards are easy to read and provide the latest information updated in real-time. This means what you see on the screen is the current state of your network’s security. Also, these dashboards are interactive and you can quickly find the information you want. Further, you can create custom cards and dashboards to meet your requirements.
- Real Risk Prioritization Using advanced AI algorithms, InsightVM can prioritize the identified risks, so you know which ones have to be addressed first. This ranking is based on thousands of critical parameters gathered from different sources. Undoubtedly, it gives a better sense of direction for your organization as your employees know which issues must be addressed right away.
- Integration with Existing Tools InsightVM integrates well with your existing CI/CD tools and public and private container repositories to identify vulnerabilities before they are deployed. In turn, this can help you to secure the containers and their hosts. Further, you can use InsightVM’s RESTful APIs to integrate with your infrastructure and tools for better control and visibility over all that happens within your network.
Why do we recommend it?
Rapid7 InsightVM stands out for its real-time, comprehensive data gathering and intuitive dashboards. Its advanced AI algorithms for risk prioritization ensure that organizations can focus immediately on the most critical vulnerabilities, streamlining the remediation process.
In all, InsightVM is an advanced tool that continuously monitors the attack surface areas to identify vulnerabilities, prioritize them, and send notifications to the concerned team for immediate remediation.
Who is it recommended for?
InsightVM is ideal for enterprises and large organizations with complex IT infrastructures, including a mix of in-office and remote endpoints. Organizations looking for real-time insights, high-level customizability, and seamless integration with existing tools will find it particularly beneficial.
Pros:
- Continuously gathers comprehensive data from all endpoints, enhancing network security monitoring
- Intuitive and real-time updated dashboards for easy and accurate monitoring of network health
- Uses advanced AI for effective risk prioritization, streamlining vulnerability management
Cons:
- Pricing based on asset count may be costly for large networks
- Complex features may pose a learning challenge for new users
The cost depends on the number of assets you choose. For 500 assets, it costs $1.84/asset/month. This goes down as you increase the assets. For example, if you increase to 1,000 assets, the cost goes down to $1.63/asset/month. Click here to get started.
4. CoalFire Attack Surface Management
CoalFire Attack Surface Management is a managed service that continuously monitors your external-facing assets to identify vulnerabilities. In the process, it also offers complete control and visibility into your endpoints and devices.
Key Features:
- Provides a Better Understanding of your Environment CoalFire’s Attack Surface Management (ASM) continuously monitors your network and devices and as a result, provides a better understanding of your environment. In particular, it focuses on the external-facing assets that have a higher chance of facing an attack and reports their critical performance parameters. Such detailed information helps to not just identify attacks but also to stay on top of the changes that happen in your environment.
- Advanced Automation CoalFire’s advanced automation capabilities help you to identify unknown assets, so you can better manage the potential security gaps, and can accordingly prioritize your remediation efforts. You can even set up this tool to perform basic remediation processes when specific events happen.
- Handles Penetration Testing The security team handles penetration testing for cloud providers, small and medium businesses, and large enterprises. Its team of advanced security personnel conduct more than 1,000 penetration tests a year and has been consistently ranked #1 under the U.S. government’s Federal Risk and Authorization Management Program (FedRAMP).
- Multitude of Reports CoalFire has comprehensive reporting and logging capabilities, so you can generate reports quickly for both internal and external auditing and compliance. These reports also help with making key decisions such as capacity planning, optimal use of available resources, budgeting, and more.
Why do we recommend it?
CoalFire Attack Surface Management excels in the continuous monitoring of external-facing assets and advanced automation for vulnerability identification. With its robust penetration testing services, the tool provides an extra layer of security assurance.
Overall, CoalFire is a well-known attack surface monitoring tool that combines penetration testing with automation to provide higher visibility and emerging threats in your environment.
Who is it recommended for?
This tool is recommended for cloud providers, small and medium-sized businesses, as well as large enterprises that require detailed and continuous monitoring of their external assets. Companies that prioritize FedRAMP compliance or have complex external-facing infrastructures will find CoalFire particularly useful.
Pros:
- Comprehensive Asset Discovery: Offers continuous identification of cloud and internet-facing assets, ensuring thorough visibility into an organization’s external attack surface.
- Automated Validation: Automates the verification of security postures, reducing manual effort and enhancing the accuracy of vulnerability assessments.
- Risk-Based Prioritization: By aggregating and prioritizing vulnerabilities and assets, Coalfire’s ASM enables organizations to focus on the most critical risks first.
- Experienced Security Team: Combines ASM platform with a veteran risk assessment team, providing a thorough, risk-based attack surface management solution.
Cons:
- Limited User Reviews: Scarcity of user-generated reviews and ratings for Coalfire’s ASM solution, making it challenging to gauge user satisfaction and real-world performance.
- Potential Complexity: The comprehensive nature of the platform may present a learning curve for new users, potentially requiring additional training and resources for effective implementation.
Contact the sales team for a custom quote. CoalFire doesn’t offer free trials at the time of writing this piece. However, you may contact the company to get answers to your questions and concerns.
5. ImmuniWeb Discovery
ImmuniWeb Discovery leverages Open Source Intelligence (OSINT) and combines it with its AI capabilities to help detect vulnerabilities in attack surface areas. This uses a continuous self-assessment and risk-scoring process to identify threats and gaps as they emerge within your organization.
Key Features:
- Maps and Classifies Threats The highlight of ImmuniWeb Discovery is that it continuously scans the attack surface areas to quickly detect threats. Using this information, it also maps them and even classifies the threats based on their likely impact, so you can mitigate the most critical ones right away. It also classifies threats into on-prem and cloud assets to point your troubleshooting efforts in the right direction.
- Dark Web Monitoring One of the likely impacts of a hacking incident is the availability of your classified information on the dark web. Some hacking incidents may go unnoticed for many weeks or months and will come to light only when your sensitive information is sold on the dark web. To avoid such embarrassments and to help identify attacks quickly, ImmuniWeb continuously monitors the dark web for any information about your company.
- High Visibility ImmuniWeb Discovery provides one of the highest levels of visibilities into your attack surface areas and the potential vulnerabilities hiding there. Its central dashboard provides a snapshot of the status of your vulnerabilities and their causes, access information, compliance, and more. You can also generate reports through this dashboard.
- Comprehensive ImmuniWeb Discovery goes beyond the known vulnerabilities and conflicts as it provides alerts on misconfigured IT assets, abandoned or forgotten assets, and even shadow IT resources. It also scores your vendors and suppliers to prevent any supply chain attacks.
Why do we recommend it?
ImmuniWeb Discovery sets itself apart with its OSINT and AI-driven continuous threat assessment, combined with specialized dark web monitoring. These features provide a robust, real-time snapshot of both existing and emerging vulnerabilities.
In all, ImmuniWeb Discovery is a good choice if you want an overarching view of all your assets and vulnerabilities in a centralized location.
Who is it recommended for?
This tool is best suited for organizations that require advanced threat intelligence and are concerned with data breaches potentially ending up on the dark web. It’s also ideal for companies with a mix of on-prem and cloud assets and those that want to keep tabs on their supply chain’s security posture.
Pros:
- Comprehensive Asset Discovery: Identifies assets across websites, clouds, repositories, and network infrastructures, providing a holistic view of an organization’s digital footprint.
- Zero False-Positive SLA: Offers a Service Level Agreement ensuring zero false positives, which reduces development time and allows unlimited validation of patched vulnerabilities.
- Continuous Monitoring: Automated, non-intrusive scans run continuously, keeping security assessments up-to-date without manual intervention.
- Dark Web Monitoring: Includes monitoring for compromised credentials and data leaks on the Dark Web, enhancing threat intelligence capabilities.
- User-Friendly Interface: Features like single sign-on integration and executive compliance overviews make the platform accessible and easy to navigate.
Cons:
- Manual Tagging Required: Automated tagging of assets is not available, necessitating manual intervention to organize resources.
- Basic Grouping and Filtering: Offers only fundamental features for grouping and filtering resources, which may not meet all users’ needs.
ImmuniWeb Discovery offers four pricing plans and they are:
- Ultimate – $3,995/month, paid annually.
- Corporate Pro – $1,995/month when paid annually and $4,995/month for a monthly subscription.
- Corporate – $995/month, paid annually.
- Express Pro – $499/month, paid annually.
Click here to see a free demo.
6. CyCognito Attack Surface Management
CyCognito is a SaaS platform that automatically monitors your attack surface area to protect your organization from possible risks and vulnerabilities.
Key Features:
- Mitigates the Digital Transformation Risks As more companies move their operations online, managing the security and IT assets can become complex and challenging. This is where CyCognito can come in handy as it monitors the cloud, shadow IT, digital supply chains, and endpoints for possible security gaps and vulnerabilities. It uses both vulnerability scanning and pen testing strategies to ensure that your attack surface area is as small as possible. Also, this tool sends instant alerts in the event of new vulnerabilities or widening of the existing ones.
- Helps Quick Remediation CyCognito not just sends alerts, but also prioritizes the threats based on the likely impact of each security gap. This is sure to help your IT personnel to focus their efforts towards the most critical issues. Further, CyCognito can point you in the right direction, so you can quickly understand the root cause of the problem. Both these measures bring down your remediation effort from months to weeks and even days, thereby reducing the chances of an attack.
- Provides Visibility The dashboard provides a snapshot of your network’s and infrastructure’s state at any time. More importantly, it shows you the risks and vulnerabilities through the lens of an attacker that in turn, can help to avert any major incident.
- Analytics and Trends CyCognito continuously collects data from your attack surface areas and analyzes the same to provide valuable insights and trends. Armed with this information, you can use your resources optimally to thwart an attack.
Why do we recommend it?
CyCognito excels in providing a comprehensive view of your attack surface by monitoring cloud, shadow IT, and digital supply chains. The platform not only alerts you to vulnerabilities but also prioritizes them, aiding in quicker, more focused remediation efforts.
In all, CyCognito discovers risks quickly, accelerates remediation, and enables you to use your resources effectively to protect your organization from any kind of attack.
Who is it recommended for?
CyCognito is particularly useful for organizations undergoing digital transformation who are concerned with managing a complex array of online assets. It’s also an excellent choice for IT teams that value actionable insights for quick remediation, as well as businesses interested in viewing their vulnerabilities from an attacker’s perspective.
Pros:
- Comprehensive Asset Discovery: Autonomously identifies and maps an organization’s entire external attack surface, including unknown and unmanaged assets, providing a thorough understanding of potential exposure.
- Risk-Based Prioritization: Assesses and prioritizes vulnerabilities based on potential business impact, enabling security teams to focus on the most critical risks first.
- Continuous Monitoring: Offers ongoing surveillance of the attack surface, ensuring timely detection of new assets and emerging threats.
- Automated Testing: Simulates real-world attack scenarios to identify exploitable vulnerabilities, enhancing proactive defense strategies.
- User-Friendly Interface: Users appreciate the intuitive design, which simplifies navigation and streamlines the vulnerability management process.
Cons:
- Integration Challenges: Some users have reported difficulties integrating CyCognito with existing security information and event management (SIEM) systems.
- Limited Customization: May offer limited options for customizing reports and dashboards to meet specific organizational needs.
- Learning Curve: New users might experience a learning curve when initially navigating the platform’s features and capabilities.
Contact CyCognito for pricing. There are no free trials at the time of writing this piece, but you can watch a demo video here.
7. UpGuard BreachSight
UpGuard BreachSight is a complete attack surface management platform that goes beyond just preventing data breaches. It also discovers any leaked credentials belonging to your organization and through it protects your customers’ data in the best way possible.
Key Features:
- Uses Security Ratings UpGuard uses a unique algorithm to rank your organization’s current security status. It gathers data across many parameters and assesses them to give you an objective, dynamic, and comprehensive picture. Using this information, you can make appropriate data-driven decisions.
- Custom Notifications UpGuard comes with a bunch of default notifications and also allows you to create and manage custom notifications. Typically, you can set up notifications when your organization’s security score falls below a threshold, a drop in vendors’ scores, the addition of new devices, and more. You can use webhooks, labels, vendor tiers, apps, and emails for managing notifications.
- Continuous Monitoring This platform continuously monitors your attack surface area for any untoward incidents, risks, new domains and IPs, typosquatting, the presence of new vulnerabilities, and more. With such detailed information, your IT team can quickly zero in on the problems and fix them at the earliest.
- Reporting and Insights A highlight of Upguard BreachSight is its reporting capabilities. You can generate reports for the executives, classify the report into subsidiaries and departments, get role-based permissions, create audit logs, and more. Such granular control and visibility reduce the chances of attacks.
- More Integrations UpGuard has a RESTful API using which you can connect to any third-party service or app. It also integrates with Zapier and through it, you can connect to more services.
Why do we recommend it?
UpGuard BreachSight offers a holistic approach to attack surface management by not only identifying vulnerabilities but also detecting leaked credentials. Its unique security rating system and extensive customization options for notifications make it a robust platform for proactive security management.
Overall, this is a complete attack surface management tool that can handle all aspects of vulnerability analysis and threat remediation.
Who is it recommended for?
UpGuard is ideal for organizations looking for a multi-faceted approach to security, including continuous monitoring and detailed reporting. It suits businesses that have complex vendor relationships and require a dynamic, data-driven evaluation of their security posture. Custom notification settings also make it a strong choice for IT teams wanting granular control over alerts.
Pros:
- Comprehensive Risk Management: Offers a holistic view of an organization’s security posture, enabling effective identification and mitigation of vulnerabilities.
- Automated Reporting: Automated reporting features save time during analysis, providing timely insights into security status.
- Continuous Monitoring: Provides ongoing monitoring and real-time alerts, ensuring organizations remain informed about potential security issues.
- User-Friendly Interface: Users appreciate the intuitive design, which simplifies navigation and enhances the overall user experience.
Cons:
- Complexity: Some users find the system’s complexity challenging, potentially requiring substantial effort to manage effectively.
- Pricing Concerns: The pricing model may not scale well with service, posing challenges for organizations with budget constraints.
- Integration Limitations: Users have reported issues with integrating UpGuard BreachSight with other tools, which can hinder seamless workflow processes.
- Feature Gaps: Some users have noted missing features or limited functionality in certain areas, which may affect the platform’s overall utility.
UpGuard BreachSight has four plans, namely,
- Starter – $15,749/year. 50 vendors and three users.
- Professional – $36,749/year. 150 vendors and six users.
- Corporate – $83,999/year. Unlimited vendors and ten users.
- Enterprise – Contact the company for a custom quote.
Click here for a free trial.
Thus, these are some of the best attack surface monitoring tools for you to choose from.
Conclusion
To conclude, attack surface monitoring tools are an essential part of your IT security plan as they continuously monitor the attack surface areas of your organization and send alerts in case of changes or vulnerabilities. Some tools even provide additional information such as security rankings, the root cause of vulnerabilities, security gaps, and other pertinent information that can help with decision-making. All these tools also generate comprehensive reports that can be used for auditing.
We hope this was insightful for you! Make sure to check out our guides too.