Security is undoubtedly an integral part of every organization, but staying on top of every possible event/trigger that can cause a potential vulnerability is not easy given the huge number of applications and devices used within an organization’s network.
This is where automated tools come in handy, as they help to keep track of the working of applications, possible events and triggers that can increase vulnerability, and more. These tools are often grouped under Security Information and Event Management, or SIEM in short.
Here is our list of the top SIEM Tools:
- ManageEngine EventLog Analyzer – EDITOR’S CHOICE A SIEM tool that gives insights into the potential threats in your network and helps you address them at the earliest. It is a comprehensive tool that provides information about the networks, servers, and applications in your infrastructure. Start a 30-day free trial.
- ManageEngine Log360 – FREE TRIAL This security package includes a SIEM, a file integrity monitor, and a log manager. Runs on Windows Server. Start a 30-day free trial.
- Datadog Security Monitoring Designed to provide greater visibility to your environment from a security standpoint, so you can address the possible vulnerabilities at the earliest. The unified information and tools it provides reduce the chances for security attacks as well.
- RSA NetWitness A security monitoring solution that collects, analyzes, and reports log data from different sources to give a comprehensive idea of the possibility of threats within the organization and to improve compliance with established security standards.
- Logpoint SIEM This package provides a classic log collection and analysis service for security monitoring. Supplemental UEBA and SOAR modules are also available and the tool can be used to centralize the monitoring of multiple sites in one location. Available as a SaaS platform or as downloadable software for Linux.
- Splunk Enterprise System A SIEM solution that helps organizations to quickly detect external and internal threats and respond to them appropriately, so the risks are minimized and the assets are safeguarded.
- LogRhythm NextGen SIEM An advanced platform that detects threats in real-time and gives you the associated context, so you can fix the underlying cause right away. It also promotes collaboration between teams to remediate quickly and efficiently.
- Heimdal Threat Hunting and Action Center This cloud-based platform gathers activity reports from Heimdal products on a site and mines that pool of data for threat indicators. The package also implements automated responses.
- SolarWinds Security Event Manager A simple and powerful SIEM solution that gives the information you need, without the associated complexity and cost. This tool comes loaded with many features that provide the insights you need to understand the security vulnerabilities in your applications and the environment as a whole.
- Securonix An advanced platform for collecting information and analyzing them to identify threats and helping an organization to respond to them right away.
- IBM QRadar Helps teams to accurately detect and prioritize threats across the enterprise, so the existing resource can be used efficiently to mitigate and remediate them. It also helps with planning to ensure that the most critical issues are addressed first.
- FortiSIEM A powerful SIEM and UEBA tool that can improve the overall cybersecurity of an organization and empower it with the information needed to identify and mitigate the existing threats and vulnerabilities.
SIEM is a sub-category within organizational security that collects log and event data generated by the different applications used within the organization. This information is analyzed in real-time to give you insights into the performance of different applications, their vulnerabilities, availability, health, performance, and more.
The Best SIEM Tools
Due to this ability to provide centralized and aggregated information and a detailed analysis of the same, SIEM tools are popularly used by organizations around the world.
This demand has led to the emergence of many tools, so if you’re starting your search for one, it can be an overwhelming experience to navigate through this market to find the one that will best fit your needs.
To ease this process and to help you make an informed decision, in this post, we have gathered the best SIEM tools. Let’s take a detailed look into the features and pricing of each of these tools.
Our methodology for selecting the best SIEM tool:
We rate tools based on the following criteria:
- We prioritize tools that are user-friendly and require minimal setup time, making it easier for organizations to integrate them into their existing infrastructure.
- The ability to monitor a wide range of events and logs from various sources is crucial for effective security incident and event management.
- Tools that provide real-time data analysis and immediate alerts for potential security incidents rank higher in our selection.
- The tool should assist organizations in meeting industry compliance standards and offer robust reporting capabilities for audits and assessments.
- We consider the overall cost of the tool in relation to its features and scalability, ensuring it offers value for different sizes of organizations.
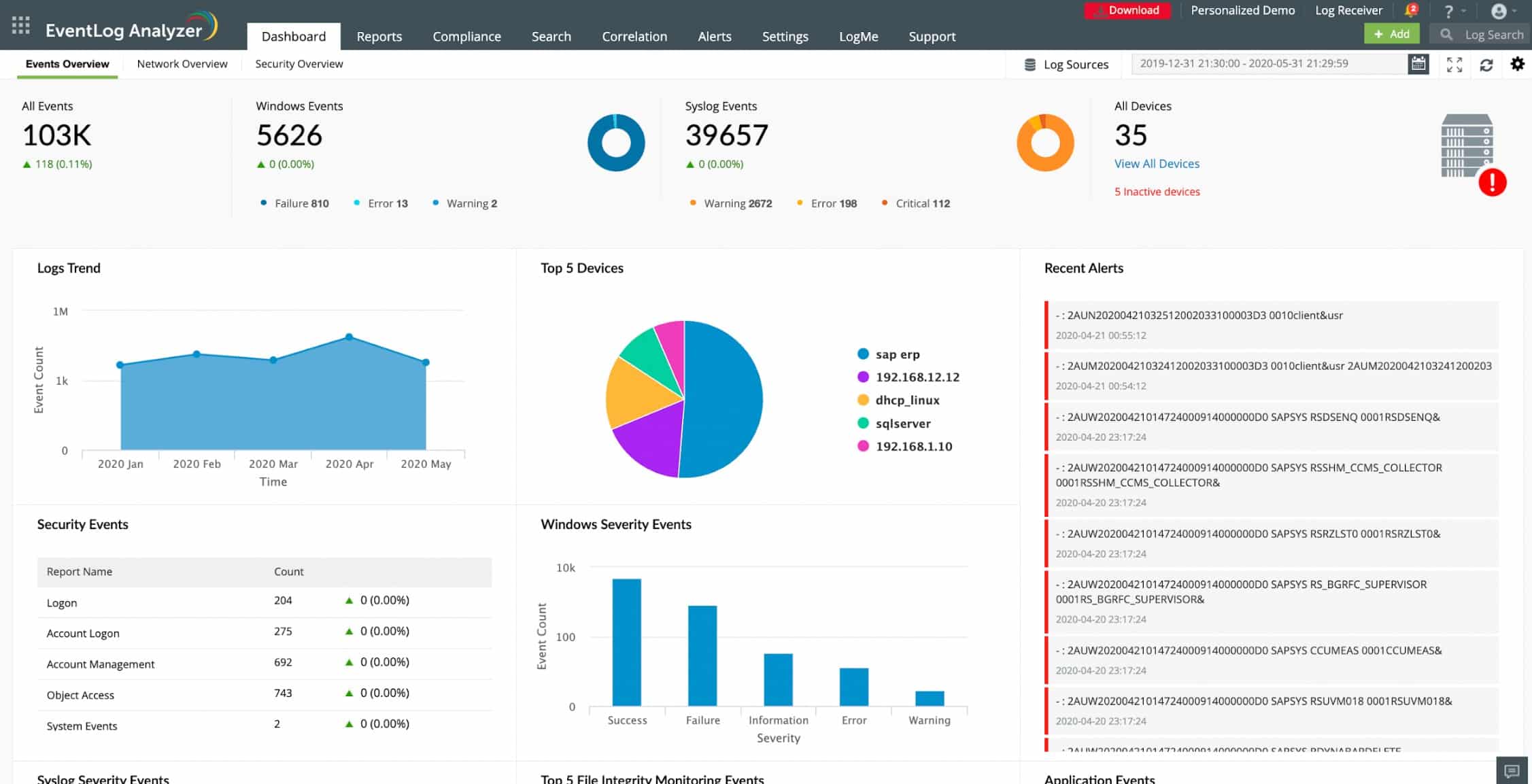
1. ManageEngine EventLog Analyzer – FREE TRIAL
EventLog Analyzer from ManageEngine is a SIEM tool that gives insights into the potential threats to your network and helps you address them at the earliest. It is a comprehensive tool that provides information about the networks, servers, and applications in your infrastructure.
Key Features:
- Automatically analyzes the logs to give you information such as user accesses, unusual activities, anomalies in user behavior, data thefts, security violations, and more
- Supports both agentless and agent-based log collections
- Raises a ticket alert in your system for event rule violation
- Correlates data across different sources to give you a comprehensive view
- Comes with a drag-and-drop builder and a custom rule engine with 30 pre-defined rules
- Offers a single console for viewing all your security-related log data
- Creates compliance reports for meeting different industry standards
- Detects threats from malicious IP addresses
- Collects data from perimeter devices as well
- Archives log data for custom periods
- Provides valuable insights into malicious inbound and outbound traffic
- Comes with augmented threat intelligence
- Processes logs at the speed of 25K logs per second to get quick forensic analysis
- Gives you the information needed to reduce the chances of an attack.
Why do we recommend ManageEngine EventLog Analyzer?
After installing the 30-day free trial of ManageEngine EventLog Analyzer, we were particularly impressed by its ability to automatically analyze logs for anomalies in user behavior and security violations. The tool’s custom rule engine with 30 pre-defined rules also made it easier for us to configure the system to our specific needs.
Who is ManageEngine EventLog Analyzer recommended for?
ManageEngine EventLog Analyzer is a versatile choice for businesses of all sizes, thanks to its tiered pricing plans. Companies in regulated industries will find its compliance reporting particularly helpful. The tool is also ideal for organizations that require quick forensic analysis, as it can process logs at a rate of 25K per second. The support for both agentless and agent-based log collections makes it flexible enough to fit into various IT environments.
Pros:
- Automatic log analysis for security insights.
- Supports agent-based and agentless log collections.
- Effective ticket alert system for event rule violations.
- Fast log processing for quick forensic analysis.
- Augmented threat intelligence for enhanced security.
Cons:
- Complexity of features might overwhelm new users.
EventLog Analyzer comes in three editions, and they are:
- Free ($0) – Supports up to five log sources
- Premium ($595/year) – Supports 1,000 log sources
- Distributed ($2495) – Supports unlimited log sources
You can download a 30-day free trial.
EDITOR'S CHOICE
ManageEngine EventLog Analyzer is our top pick for a SIEM tool because it provides comprehensive log management, real-time monitoring, and advanced threat detection in a highly efficient and cost-effective package. It enables organizations to collect, analyze, and store logs from a variety of sources, including network devices, servers, and applications, ensuring complete visibility into their network security landscape. One of the most important features of EventLog Analyzer is its ability to perform real-time log correlation. It automatically detects security incidents and sends alerts based on predefined rules, allowing security teams to identify and address threats before they can escalate. The tool also supports compliance management, offering built-in reports for standards like GDPR, HIPAA, PCI-DSS, and more. EventLog Analyzer is designed to be user-friendly, with an intuitive interface that allows security teams to easily navigate logs, analyze patterns, and generate detailed reports. The tool supports automated incident response, which helps reduce the time and effort needed to handle security events manually. The tool’s scalability makes it a great fit for businesses of all sizes, providing dependable security features at an affordable price point.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/eventlog/download.html
OS: Windows Server, Linux, and SaaS
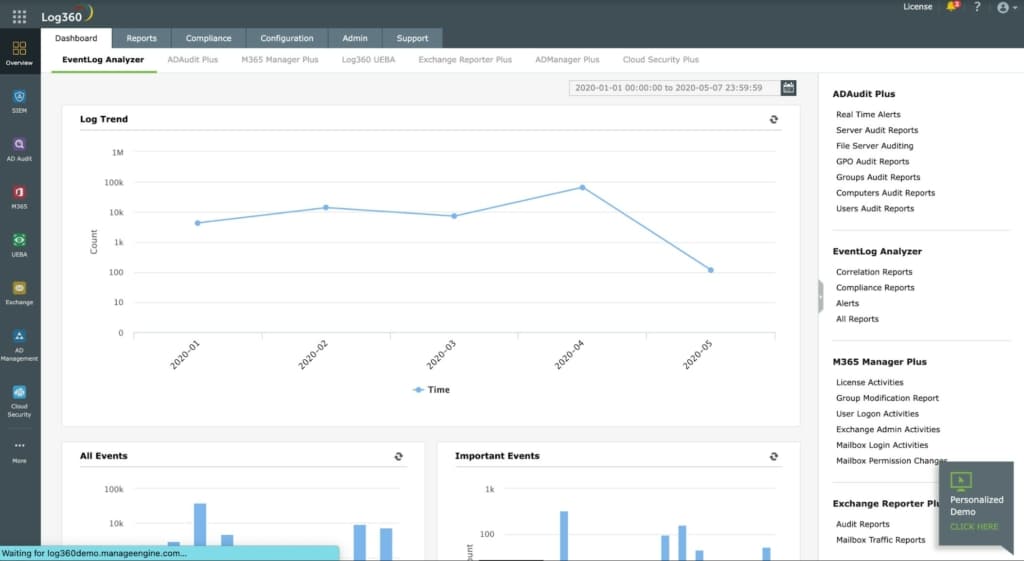
2. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a SIEM system that gets a threat intelligence feed and practices user and entity behavior analytics (UEBA) for anomalous activity detection. The UEBA system is an AI-based machine learning mechanism that establishes a pattern of typical behavior for each user account and device. The SIEM continues to observe activity and adjusts the baseline accordingly to reduce the likelihood of false-positive reporting.
Key Features:
- Runs on Windows Server
- File integrity monitoring
- Log management
- Collects logs from more than 700 software packages
- Gathers Windows Events and Syslog messages
- Extracts activity data from AWS, Azure, and Salesforce cloud platforms
- User and entity behavior analytics for activity baselining
- Anomaly detection for suspicious activity
- Feeds notifications to ManageEngine ServiceDesk Plus, Jira, and Kayoko
- Compliance with PCI DSS, FISMA, HIPAA, SOX, GDPR, and GLBA
- Data viewer with analysis tools
Why do we recommend ManageEngine Log360?
We downloaded and tested ManageEngine Log360’s 30-day free trial and were highly impressed with its UEBA system, an AI-based machine learning mechanism that adjusts behavioral baselines to reduce false positives. The tool’s seamless integration with platforms like AWS, Azure, and Salesforce also adds another layer of efficiency in log management.
Who is ManageEngine Log360 recommended for?
ManageEngine Log360 is best suited for medium to large enterprises that require advanced threat intelligence and behavioral analytics. Its compliance features make it a strong choice for organizations that need to adhere to various standards like PCI DSS, FISMA, HIPAA, SOX, GDPR, and GLBA. Given its wide range of log source compatibility, including more than 700 software packages, it’s an excellent fit for heterogeneous IT environments.
Pros:
- Advanced UEBA for anomalous activity detection.
- Extensive log collection from over 700 software.
- Compliance with multiple industry standards.
- Effective anomaly detection and alert management.
- Efficient user and entity behavior analytics.
Cons:
- Pricing information requires direct contact.
There are two editions of ManageEngine Log360: Free and Professional. You need to get a quote to find out the price. Start a 30-day free trial.
3. Datadog Security Monitoring
Datadog’s Security Monitoring tool is designed to provide greater visibility to your environment from a security standpoint, so you can address the possible vulnerabilities at the earliest. The unified information and tools it provides reduce the chances for security attacks as well.
Key Features:
- Provides end-to-end visibility for dynamic cloud environments
- Easily tracks your compliance levels
- Detects threats in real-time
- Delves deep into your infrastructure metrics and logs to identify threats in real-time
- Provides comprehensive visibility across all layers and systems through a single pane
- Comes with more than 450 integrations to collect data and metrics from all possible applications and stacks
- Has out-of-the-box reporting templates and dashboards
- Gives contextual information to help you to zero in on the problem
- Automatically parses data from your logs into a human-readable form
- Its detection rules feature allows you to detect threats in real-time
- These rules can be modified to suit specific circumstances, so users have complete control over what they do and can use the recommendations from the tool.
Why do we recommend Datadog Security Monitoring?
After testing Datadog Security Monitoring through its 14-day free trial, we found its end-to-end visibility for dynamic cloud environments particularly effective for real-time threat detection. The tool also excels in flexibility, offering more than 450 integrations, which allows for comprehensive data collection across various applications and stacks.
Who is Datadog Security Monitoring recommended for?
Datadog Security Monitoring is ideal for businesses operating in dynamic cloud environments who require real-time threat detection and an extensive range of integration options. Its tiered pricing structure, from a free plan to enterprise-level options, makes it accessible for companies of all sizes. Businesses looking to customize their threat detection rules will also find this tool extremely useful.
Pros:
- End-to-end visibility for dynamic cloud environments.
- Real-time threat detection capabilities.
- Over 450 integrations for comprehensive data collection.
- User-friendly with contextual information provision.
- Customizable detection rules for tailored security.
Cons:
- Pricing may escalate with additional features.
There are three broad plans, and you can customize them to meet your specific requirements. Contact the sales team for such customizations and bulk discounts.
The pricing structure for the three plans are:
- Free – $0
- Pro – $15 per host per month
- Enterprise – $23 per host per month
Click here for a 14-day free trial.
4. RSA NetWitness
RSA NetWitness is a security monitoring solution that collects, analyzes, and reports log data from different sources to give a comprehensive idea of the possibility of threats within the organization and to improve compliance with established security standards.
Key Features:
- Collects log data from all applications and devices
- Provides business context for information from the network and endpoint devices
- Identifies new and unknown threats with real-time data
- Drills down into logs
- Detects and identifies threats using sophisticated rules
- Increases the speed and efficiency through automation
- Integrates multiple risk factors to improve incident response
- Identifies early threat indicators and analyzes their impact
- Continuously monitors and responds to threats on endpoint devices such as laptops and virtual machines
- Enables collaboration to respond to threats
- Provides a unified approach to managing digital risks
Why do we recommend RSA NetWitness?
We tested RSA NetWitness by downloading its free trial and were particularly impressed by its ability to provide business context for log data, significantly enhancing our situational awareness. Its real-time data analysis allowed us to identify new and unknown threats efficiently, making it a robust solution for proactive security monitoring.
Who is RSA NetWitness recommended for?
RSA NetWitness is well-suited for medium to large organizations that require a comprehensive, real-time security monitoring solution. Companies that need to integrate threat data across multiple points in their network, including endpoint devices and applications, will find the tool especially valuable. Additionally, it’s a good fit for organizations looking to improve their incident response through automation and collaboration.
Pros:
- Comprehensive log data collection from various sources.
- Integrates multiple risk factors for incident response.
- Efficient in identifying early threat indicators.
- Enables collaborative response to threats.
- Continuously monitors and responds to endpoint threats.
Cons:
- Cost per throughput may be high for smaller entities.
Pricing is based on throughput, with the lower tiers having more cost/throughput when compared to the higher tiers. It also has a term license that costs $857 per year. The automation and orchestration part is also available on a term license basis that costs $8200 per year. Click here for a free trial.
5. Logpoint SIEM
Logpoint SIEM is a suitable security scanning package for large organizations. This system collects and consolidates log messages from tour endpoints and software packages. The service scans through the standardized messages and identifies threats. The system is able to scan up to one million events per second.
Key Features:
- A log message collector
- Collects logs from more than 25,000 different sources
- Standardizes the format of all incoming messages
- Scan through messages looking for suspicious activity
- Log file management for compliance auditing
- Includes a feed of network activity in its data lake
- Provide advanced threat protection (ATP) against advanced persistent threats (APT)
- Notes suspicious user accounts and IP addresses
- Interfaces with Active Directory to record failed login attempts
- Works through the MITRE ATT&CK matrix
- Compliance reporting for GDPR and HIPAA
- A SOAR service that coordinates the research and remediation capabilities of third-party tools
- A UEBA add on to baseline user behavior and identify anomalous activity
- Automated threat detection, investigation, and response (TDIR) lifecycle
- An endpoint agent, called AgentX, which collects and forwards activity data
- AgentX performs CIS-recommended checks to produce system hardening advice
- A library of pre-written playbooks for automated responses
- Specialized processes for monitoring SAP
- Suitable for use by IT departments and managed security service providers
- Data analysis screens
- Log explorer
- Option to run the systems as a software package for Ubuntu Linux
- SaaS platform option
- Remote site monitoring
Why do we recommend Logpoint SIEM?
The Logpoint SIEM package is able to manage large volumes of log messages very quickly. A key advantage of the Logpoint system is its library of playbooks that shut down threats quickly. Security orchestration, automation, and response (SOAR) capabilities can interact with third-party security tools providing extra value from the security systems that you already have.
Who is Logpoint SIEM recommended for?
Logpoint SIEM is a good solution for large enterprises. It can also be deployed by managed service providers that offer security services to their clients. The tool has a user and entity behavior analytics (UEBA) add-on that can enhance the user activity tracking services that are included in the core package. The system is able to detect insider threats as well as intruders.
Pros:
- Scan log messages for threats
- Looks for insider threats and account takeovers
- Tracks failed login attempts
- Searches for signs of advanced persistent threats
- Provides utilities for data analysis
Cons:
- No free trial
Prices are given in Euros.
- Requires a minimum order of 100 SIEM nodes at 27 EUR per month each
- UEBA add-on requires a minimum of 250 endpoints at 2.50 EUR per month
- SaaS version starts at 1,580 EUR per month
No trial download is available – get a demo.
6. Splunk Enterprise Security
Splunk Enterprise System is a SIEM solution that helps organizations to quickly detect external and internal threats and respond to them appropriately, so the risks are minimized and the assets are safeguarded.
Key Features:
- Provides visibility into the complete infrastructure
- Ingests data from the logs of systems and applications across cloud and on-premises environments, and analyzes the same to provide meaningful and actionable insights
- Helps to quickly detect malicious threats
- Investigates and correlates activities across multiple environments
- Gives teams the freedom of managing value-add security tasks instead of focusing on hardware management
- Uses alert management and risk scores to present the most relevant threats for your attention
- Comes with customizable dashboards and reports
- Automatically triggers alerts when the values exceed established thresholds
- Offers all the investigative tools needed to provide a quick and efficient response to the emerging threats
- Provides context-driven alerts and automation when needed
- Helps with compliance with security standards
Why do we recommend Splunk Enterprise Security?
After installing the free version of Splunk Enterprise Security, we thoroughly explored its capabilities in our sandbox environment. We were particularly impressed with its alert management and risk scoring features, which prioritized the most relevant threats for immediate attention, significantly streamlining our threat response process.
Who is Splunk Enterprise Security recommended for?
Splunk Enterprise Security is ideal for organizations that require a highly customizable SIEM solution with real-time threat detection and response features. Companies looking for a tool that can seamlessly integrate data from cloud and on-premises environments for comprehensive visibility will find Splunk to be an excellent choice.
Pros:
- Extensive infrastructure visibility.
- Rapid detection of malicious threats.
- Customizable dashboards and reporting tools.
- Context-driven alerts for effective threat response.
- Supports compliance with security standards.
Cons:
- Pricing requires direct inquiry with the sales team.
Contact the sales team for a quote. Click here for a free download.
7. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center is an add-on package for users of Heimdal on-premises cybersecurity tools. This service binds those individual elements into a platform by consolidating activity data that the on-premises units upload to the Heimdal cloud server. The Action Center holds playbooks for automated responses that are triggered by the discovery of a threat.
Key Features:
- Unifies the activities of at least three on-premises Heimdal cybersecurity systems
- Performs threat detection on consolidated activity reports
- Provides risk management through vulnerability scanning and system hardening
- Automated responses implemented through on-premises units
- Requires at least three different Heimdal services to be installed on-premises
- Unifies the activities of on-device Heimdal Net-Generation Anti-Virus installations
- NGAV for Windows, macOS, and Linux
- Interfaces with the mobile device management tool in the NGAV, which watches devices running Android or iOS
- Supports Network Security, Email Security, Patching & Asset Management, and Endpoint Security units
- Provides automated responses, which could involve multiple on-premises packages
- Blocks lateral movement by malware or intruders
- Offers an opportunity to implement user behavior tracking
- Provides an overview of all system activity
- A hybrid cybersecurity tool with elements on-site and on the cloud
Why do we recommend Heimdal Threat Hunting and Action Center?
We accessed Heimdal’s free demo and put its Threat Hunting and Action Center to the test. The platform stood out for its comprehensive threat detection and automated responses, implemented through a unique playbook system. The consolidation of activity data and system hardening capabilities are features we find highly valuable for any cybersecurity setup.
Who is Heimdal Threat Hunting and Action Center recommended for?
This platform is best suited for organizations already invested in Heimdal’s on-premises cybersecurity tools, as it requires at least three different Heimdal services to be installed for optimal performance. The Threat Hunting and Action Center is particularly beneficial for businesses requiring unified cybersecurity activities across multiple vectors—such as Network Security, Email Security, and Endpoint Security. Given its advanced features like user behavior tracking, it’s an excellent fit for medium to large enterprises focused on robust cybersecurity.
Pros:
- Unifies multiple Heimdal cybersecurity systems.
- Automated threat detection and response.
- Enhances risk management with vulnerability scanning.
- Effective for Windows, macOS, Linux, Android, iOS.
- Offers comprehensive system activity overview.
Cons:
- Requires multiple Heimdal services for full functionality.
Heimdal doesn’t publish a price list. Heimdal offers a demo of the Threat Hunting & Action Center instead of a free trial.
8. LogRhythm NextGen SIEM
LogRhythm NextGen SIEM is an advanced platform that detects threats in real-time and gives you the associated context, so you can fix the underlying cause right away. It also promotes collaboration between teams to remediate quickly and efficiently.
Key Features:
- Searches across the log and machine data to give the data you want
- Automates repetitive task and labor-intensive work
- Identifies threats quickly by poring through the logs
- Enhances collaboration to remediate threats
- Eliminates blind spots
- Scales well with your growing business
- Has a modular design that makes it easy to add components when needed
- Centralizes log data and enriches it with contextual information
- Comes with customizable dashboards and reports
- Can be deployed in the cloud or on-premises
- Adds value to your IT operations
- Has prebuilt compliance modules to detect violations
Why do we recommend LogRhythm NextGen SIEM?
After reaching out to the team for a custom trial, we installed LogRhythm NextGen SIEM to scrutinize its features. We found that the tool excels in real-time threat detection and the ability to provide contextual information for immediate remediation. Its automation features were particularly effective in handling repetitive tasks, allowing us to focus on more complex threat scenarios.
Who is LogRhythm NextGen SIEM recommended for?
LogRhythm NextGen SIEM is ideal for businesses of varying sizes, as it scales well and offers both cloud and on-premises deployment options. Organizations aiming to enhance team collaboration in their security operations will find the platform extremely beneficial. Its prebuilt compliance modules also make it a strong candidate for companies needing to meet specific regulatory requirements.
Pros:
- Searches and automates analysis of log data.
- Scales effectively with business growth.
- Centralizes log data with enriched context.
- Modular design for easy component addition.
- Offers prebuilt compliance modules.
Cons:
- No publicly available free trial.
Contact the sales team for more information. At present, there are no publicly available free trials. You can always contact the team for custom trials.
9. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a simple and powerful SIEM solution that gives the information you need, without the associated complexity and cost. This tool comes loaded with many features that provide the insights you need to understand the security vulnerabilities in your applications and the environment as a whole.
Key Features:
- Improves security, monitoring, and troubleshooting
- Actively detects end-user activity
- Simplifies audits with real-time correlations to help you understand the root cause
- Provides immediate threat remediation by allowing you to configure custom rules needed to prevent a breach.
- Detects threats across environments to provide in-depth security
- Tracks all the logon and logoff activities with a centralized events monitor
- Handles all the requirements for compliance risk management
- Continuously monitors applications across environments to assess them for risks
- Gives actionable insights from logs to detect and handle security risks
- Comes with a Botnet detection tool that proactively monitors your systems for bot attacks
- Its centralized log management provides all the data you need in a single view and in the process, gives complete control over the working of your applications
- Meets the compliance requirements of industry standards
- Has multi-event correlation capabilities to detect and prevent cross-site scripting attacks
- Uses cyber threat analysis to protect your environment
- Its database audit tool improves the security and performance of your databases
- Monitors event logs from varied sources to prevent DDoS attacks
- Protects your database from SQL injection attacks
- Detects intrusions right away
- Correlates log patterns to send threat warnings
- Its real-time log analyzer improves threat awareness
- Protects sensitive information from attacks
- Analyzes firewalls and logs to prevent cyberattacks
- Identifies spear phishing attacks
- Implements best practices to detect ransomware attacks
- Simplifies the incident response process
- Monitors user activities and logins to reduce the chances for insider attacks
Why do we recommend SolarWinds Security Event Manager?
After downloading the 30-day free trial, we were highly impressed by SolarWinds Security Event Manager’s extensive features, particularly its capabilities in real-time threat remediation and multi-event correlation. The tool provides an all-in-one dashboard for centralized log management, earning its place at the top of our list.
SolarWinds Security Event Manager is a blend of simplicity and powerful features. Its intuitive interface makes it accessible for teams of all skill levels, while its comprehensive monitoring capabilities ensure no threat goes unnoticed. The tool’s real-time analysis and alerting system provide immediate insights into security incidents, significantly enhancing an organization’s response time. Its robust compliance and reporting features simplify the audit process, making it an ideal choice for organizations needing to adhere to strict industry standards. Finally, the cost-effectiveness and scalability of SolarWinds Security Event Manager make it suitable for both small businesses and large enterprises.
Who is SolarWinds Security Event Manager recommended for?
This SIEM solution is particularly beneficial for IT security professionals and system administrators who need a multi-faceted approach to security. Its real-time log analyzer and database audit tools make it a go-to option for organizations concerned about immediate threat detection and compliance risk management.
Pros:
- Simplifies security monitoring and troubleshooting.
- Actively detects and reports user activities.
- Streamlines audits with real-time correlations.
- Offers immediate threat remediation through custom rules.
- Comprehensive threat detection across environments.
Cons:
- Initial cost can be a barrier for small businesses.
Starts at $2,613 Click here for a fully functional 30-day free trial.
10. Securonix
Securonix’s SIEM is an advanced platform for collecting information and analyzing them to identify threats and helping an organization to respond to them right away.
Key Features:
- Built on big data to provide advanced analytics
- Collects massive data in real-time from different systems and applications
- Uses patented machine learning algorithms to identify advanced threats
- Provides artificial intelligence-based response capabilities
- Gives profound visibility and scalability to your organization’s operations
- Has a cloud-based infrastructure for multi-tenancy
- Decreases the meantime to detect threats
- Comes with intuitive features such as spotter search, response bot, and case management to efficiently identify and track vulnerabilities
- Helps to realize ROI quickly
- Acts as a seamless solution to handle all threats
Why do we recommend Securonix?
After requesting a demo and navigating its interface, we were highly impressed by Securonix’s machine learning algorithms and AI-based response capabilities. These features make it adept at identifying advanced threats in real-time, significantly decreasing the meantime to detect and respond to vulnerabilities.
Who is Securonix recommended for?
Securonix is particularly suited for organizations that handle large volumes of data and require advanced analytics to detect threats. Businesses looking for a cloud-based, scalable solution will find Securonix a perfect fit. It is also ideal for companies wanting to realize a quick ROI, as the platform offers a pricing model based on identities, allowing for cost-effective scaling.
Pros:
- Advanced analytics built on big data.
- Utilizes machine learning for threat identification.
- Provides deep visibility and scalability.
- Features efficient incident identification and tracking.
Cons:
- Pricing based on identities may be complex.
The pricing is based on identities, so you have the flexibility to add the necessary volume and velocity to your plan. Click here to request a demo.
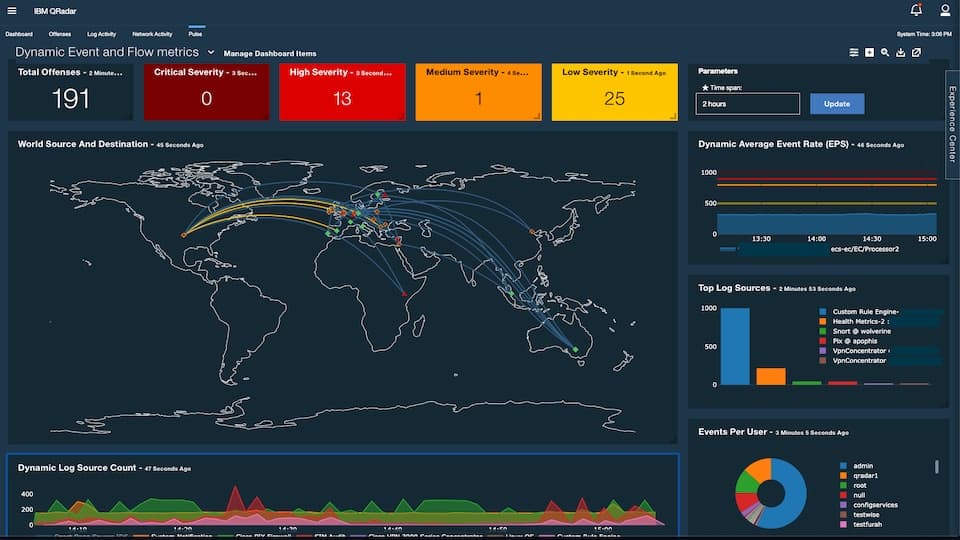
11. IBM QRadar
IBM QRadar helps teams to accurately detect and prioritize threats across the enterprise, so the existing resource can be used efficiently to mitigate and remediate them. It also helps with planning to ensure that the most critical issues are addressed first.
Key Features:
- Accurately detects threats across the entire organization
- Provides intelligent insights that help the teams to respond quickly to a threat
- Consolidates log events and flow data across devices, applications, and endpoints
- Correlates information into unified alerts for better action
- Prioritizes threats so organizations can use their resources efficiently
- Available for cloud-based and on-premises applications
- Eliminates manual tasks
- Comes with out-of-the-box templates for real-time analytics
- Complies with both organizational and industry-specific guidelines and practices
- Automatically parses logs and converts them to a human-readable form
- Integrates with 450+ tools and applications
- Has a flexible architecture
- Highly scalable
Why do we recommend IBM QRadar?
During our 14-day free trial, we put QRadar’s threat detection and prioritization to the test. We were particularly impressed by its ability to consolidate log events and flow data across various devices, applications, and endpoints, facilitating efficient resource allocation for threat remediation.
Who is IBM QRadar recommended for?
IBM QRadar is ideal for enterprise-level organizations that have a complex mix of cloud-based and on-premises applications. Its high scalability and flexibility make it suitable for businesses looking to eliminate manual tasks while adhering to both organizational and industry-specific compliance guidelines. The platform integrates seamlessly with over 450 tools and applications, making it a good fit for organizations that rely on multiple software solutions for security monitoring.
Pros:
- Accurate threat detection across the organization.
- Intelligent insights for rapid threat response.
- Consolidates log and flow data for unified alerts.
- Flexible architecture and scalability.
Cons:
- Flexible payment plans might be confusing.
Offers flexible payment plans to suit your business needs. Contact the sales team for a quote. Click here to start your 14-day free trial.
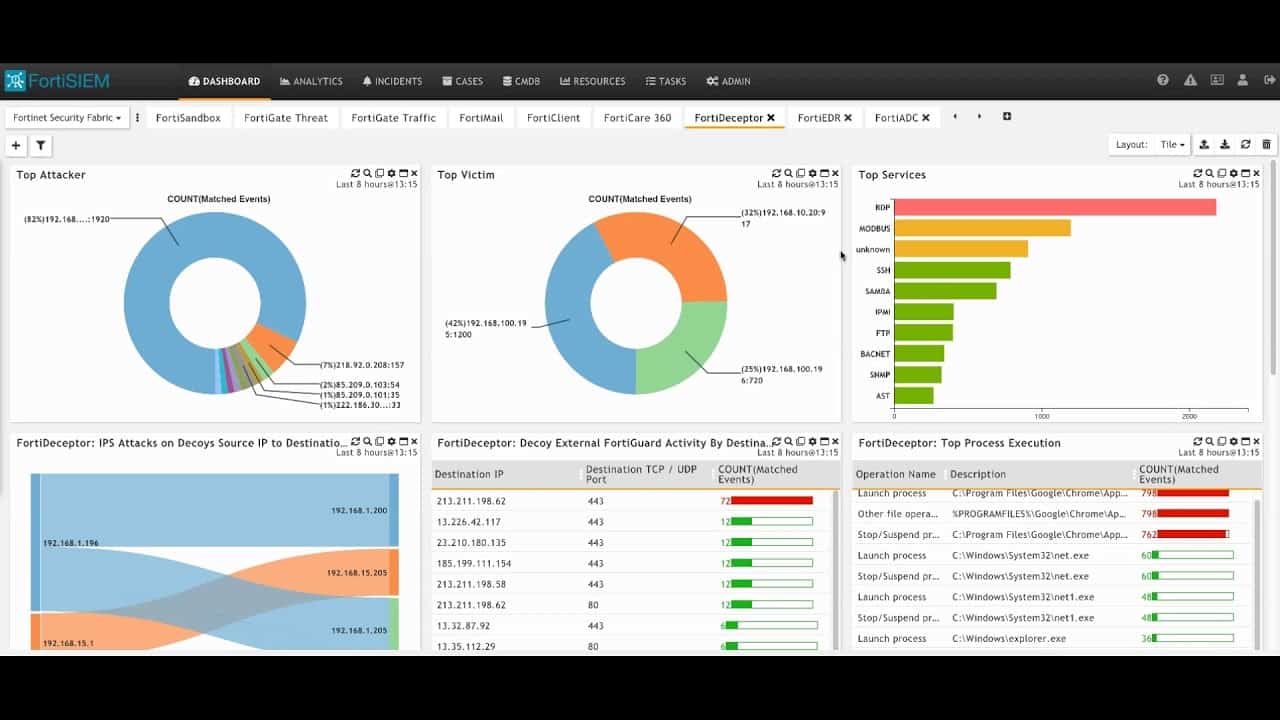
12. FortiSIEM
FortiSIEM is a powerful SIEM and UEBA tool that can improve the overall cybersecurity of an organization and empower it with the information needed to identify and mitigate the existing threats and vulnerabilities.
Key Features:
- Detects unusual user and entity behavior without requiring complex rules
- Identifies internal and external threats with high levels of precision
- Builds a risk score of devices and users
- Provides a centralized view of the performance of different applications
- Comes with out-of-the-box compliance reports
- Continuously updates device context to provide relevant information to the administrators
- Searches events in real-time with no indexing being required
- Integrates with external websites for IP address lookup
- Use both agent-based and agentless data collection, depending on the source
- Works well on both Windows and Linux
Why do we recommend FortiSIEM?
After scheduling a demo to navigate FortiSIEM’s features, we found its ability to continuously update device context remarkably useful. Its real-time event search without requiring indexing also stood out, streamlining the administrative workflow significantly.
Who is FortiSIEM recommended for?
FortiSIEM is suitable for organizations seeking a robust SIEM and UEBA solution offering agent-based and agentless data collection. Its capabilities make it a strong choice for businesses focused on compliance, as it comes with out-of-the-box compliance reports. Additionally, it works well on both Windows and Linux platforms, catering to companies with diverse operating systems.
Pros:
- High precision in identifying internal and external threats.
- Builds comprehensive risk scores for devices and users.
- Provides centralized performance view of applications.
Cons:
- Pricing information not readily available.
Contact customer support for pricing. Click here to schedule a demo.
Conclusion
SIEM tools are necessary for every organization as it collates data from different sources, analyzes them, and presents a concise and context-based summary of existing vulnerabilities and possible threats along with a priority for each. There are many SIEM tools available today and each comes with some unique features, so the choice depends on what you need. The above-mentioned tools can be a good starting point to know what each of them offers, so you can make an informed choice for beefing up your organization’s security.